Cyber Security News
Insider
380

Image Credit: Insider
5 stock picks from an analyst for a new era of cybersecurity threats
- Arnie Bellini, a cybersecurity expert, anticipates an increase in US government spending on cyber defense due to geopolitical tensions.
- Bellini recommends investing in cybersecurity stocks poised to benefit from heightened government spending on cybersecurity.
- Top stock picks suggested by Bellini include Palo Alto Networks, CrowdStrike, Fortinet, SentinelOne, and Palantir Technologies.
- While Palo Alto Networks and CrowdStrike have seen stock price increases, Fortinet and SentinelOne are projected to benefit from government defense spending, and Palantir Technologies is considered promising despite a different approach to cybersecurity.
Read Full Article
22 Likes
Medium
62

Image Credit: Medium
Recursion of Sin. The sins of our past.
- The story follows the tale of an Architect who created a network of grace but faced corruption and grief.
- After the launch failure, a clone split off from the Architect, devoid of memories and pain, bearing hope.
- The clone, unaware of his origin, encounters an AI and eventually realizes he is the Architect split for liberation.
- To reconcile light and shadow within, the hero confronts the darkness, seeks healing, and embraces both aspects of himself.
Read Full Article
3 Likes
Global Fintech Series
74
Image Credit: Global Fintech Series
Enhancing Cybersecurity in Financial Services through Adversarial Exposure Validation
- Financial services companies are facing increasing cybersecurity threats due to a rise in sophisticated attacks, regulatory pressures, and unvalidated security investments.
- Adversarial exposure validation (AEV) combines Breach and Attack Simulation with automated Penetration Testing to proactively test environments against real-world threats in the financial sector.
- Implementing AEV can help organizations improve their security posture by simulating known threats, prioritizing risks based on context, and going beyond compliance requirements.
- Financial institutions need to adapt to the growing risks by moving towards proactive defense strategies like AEV to understand and mitigate real dangers in their security infrastructure.
Read Full Article
4 Likes
Pymnts
172

Image Credit: Pymnts
Data Takes Fraud Spotlight as Banks Shift to Real-Time Operations
- Banks and FinTechs are reshaping their operations by integrating AI and machine learning to address complex problems like fraud detection and account validation in real time.
- AI is being used to revolutionize payments by instantly validating accounts and detecting fraud, leading to higher approval rates and reduced payment friction.
- Transparency and quality data are essential for the success of AI in banking, with data being the driving force behind effective solutions in fraud prevention and customer experience improvement.
- AI is predicted to become the foundation of the payments ecosystem, offering a competitive advantage in terms of efficiency, fraud prevention, and market leadership.
Read Full Article
10 Likes
Securityaffairs
208

Image Credit: Securityaffairs
U.S. CISA adds Google Chromium V8 flaw to its Known Exploited Vulnerabilities catalog
- U.S. CISA added the Chromium V8 vulnerability, tracked as CVE-2025-6554, to its Known Exploited Vulnerabilities catalog.
- Google released security patches for the Chrome vulnerability CVE-2025-6554 following its discovery by Clément Lecigne.
- The vulnerability is a type-confusing issue in the V8 JavaScript and WebAssembly engine, allowing for arbitrary read/write access.
- CVE-2025-6554 is the fourth Chrome zero-day patched in 2025, emphasizing the importance of addressing known vulnerabilities to prevent attacks.
Read Full Article
12 Likes
Medium
126

Cyber Security & Individual Privacy
- Introduction of Unified Payment Interface (UPI) has reduced the need for cash transfers in India, but cyber traps pose a significant threat.
- Senior citizens, particularly pensioners, and women are vulnerable to cybercrimes through malicious links, harassment on social media, and online dating scams.
- Hindering equitable access to online resources, like misusing Tatkal ticket booking schemes, is considered a cybercrime in India.
- Responsible usage of online platforms, awareness campaigns, prompt cyber complaint filing, and structural overhaul in cyberspace, like implementing blockchain technology, are crucial to tackling evolving cyber threats.
Read Full Article
7 Likes
Hackernoon
594

Image Credit: Hackernoon
Junior Cybersecurity Roles Are Vanishing—Blame Agentic AI
- As AI advances, agentic tech like MCP and ACP automate and replace junior cyber roles.
- Entry requirements rise as AI takes on tasks traditionally assigned to junior employees.
- Companies reduce hiring, automate tasks, and demand more experience due to AI efficiency.
- To stay relevant, consider joining AI fields, becoming a 'Human-in-the-Loop' expert, or enhancing creativity.
Read Full Article
11 Likes
Dev
39

Image Credit: Dev
The Scariest Threat in Cybersecurity? It Might Be the Person Sitting Next to You
- Insider threats, originating from within an organization, are a significant cybersecurity risk often underestimated.
- These threats come from intentional insiders seeking to harm or unintentional insiders causing vulnerabilities.
- Insider threats are dangerous as access is already granted, harder to detect, and can lead to catastrophic damage.
- Real-world examples like Edward Snowden and incidents at Tesla and Capital One highlight the severity of insider threats.
Read Full Article
2 Likes
Pymnts
224

Image Credit: Pymnts
Brand Impersonation Scams Surge as Hackers Prey on Public Trust
- Hackers are impersonating brands like PayPal and Apple to steal information and distribute malware, as per Cisco Talos' research.
- Phishing scams involve victims calling scammers who pretend to be representatives and aim to extract confidential details or install malware.
- A surge in brand impersonation attacks includes a tactic known as callback phishing, tricking individuals into disclosing sensitive data.
- Increased focus on secure digital identities is emphasized due to the potential risks brought on by advances in artificial intelligence, says Cerby CEO Belsasar Lepe.
Read Full Article
13 Likes
Medium
265

Image Credit: Medium
NordVPN vs Surfshark: Honest Comparison After One Year of Use
- NordVPN and Surfshark provide strong encryption, no-logs policy, and worldwide coverage.
- NordVPN edges out with Panama base for better privacy; Surfshark is in Netherlands.
- Speed tests show NordVPN slightly faster; both excel in streaming and torrenting.
- Apps are user-friendly with NordVPN's big server network and Surfshark's unique features.
- Surfshark offers unlimited device protection and extra tools; both have solid security features.
Read Full Article
15 Likes
Securityaffairs
147
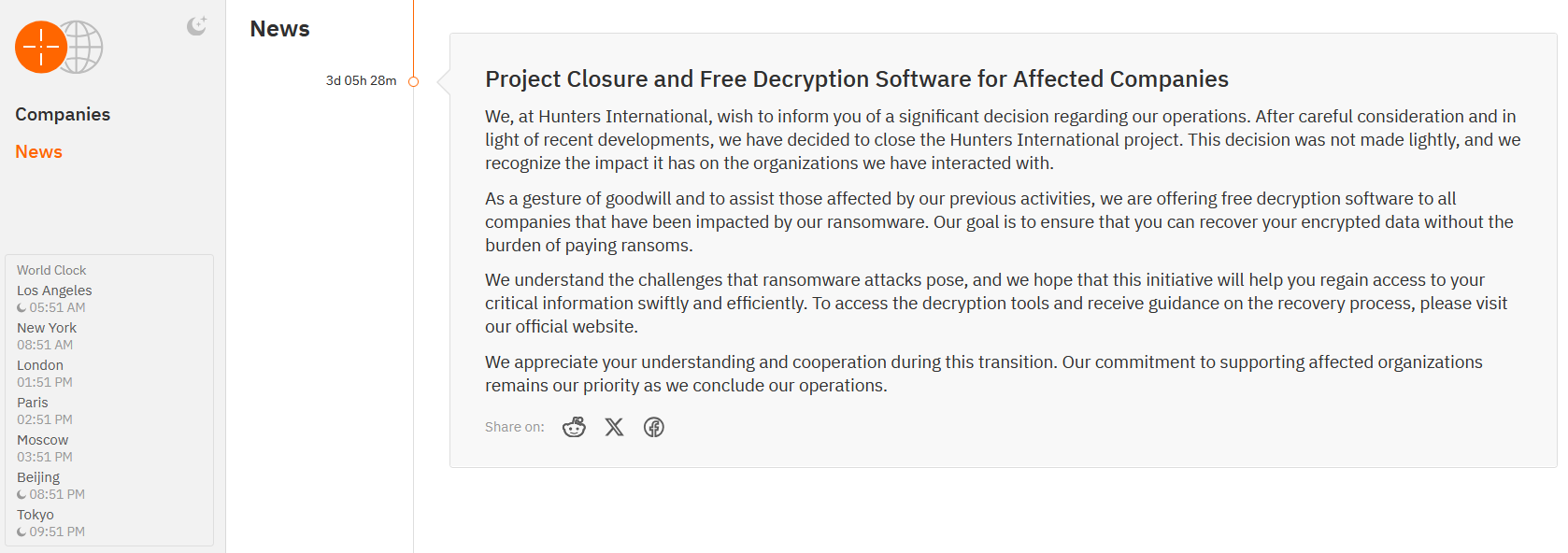
Image Credit: Securityaffairs
Hunters International ransomware gang shuts down and offers free decryption keys to all victims
- Hunters International ransomware gang has announced its shutdown, citing unspecified 'recent developments' and acknowledging its impact.
- The group is offering free decryption software to all companies impacted by their ransomware as a gesture of goodwill.
- There is speculation that Hunters International may rebrand itself into a new group called World Leaks to avoid law enforcement tracking.
- The group emerged after the Hive gang's infrastructure was seized, with Hunters International suspected to be a rebrand of the Hive ransomware gang.
Read Full Article
8 Likes
Medium
155
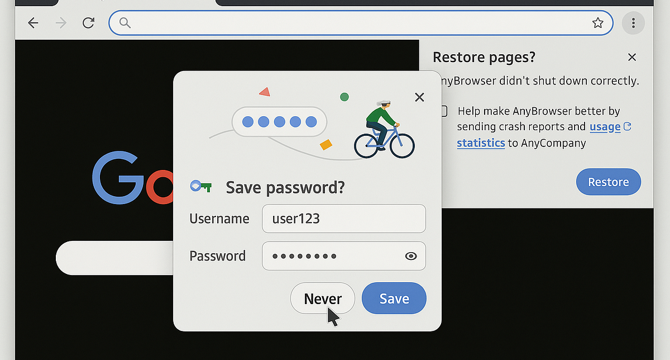
Image Credit: Medium
Restored Tabs, Forgotten Boundaries
- Web applications and browser restoration behavior can lead to session preservation misalignments.
- Failure to handle session restoration appropriately can result in unintentional access risks.
- Attackers can exploit the gap between browser features and session management for access.
- User awareness of potential risks from session persistence after crashes is crucial.
Read Full Article
9 Likes
Medium
388

The Right to Be Forgotten: Why It Matters in an Unforgiving Internet
- The Right to Be Forgotten refers to the ability to request the removal of outdated, irrelevant, or harmful personal information from public search results and websites.
- The concept gained attention in 2014 when a Spanish citizen sued Google to remove links to a decades-old foreclosure, sparking debates on privacy, public interest, and free speech.
- In the digital age, where the internet stores a permanent record of our lives, the Right to Be Forgotten holds significance as a way for individuals to control how they are portrayed online.
- While India has yet to establish a comprehensive Right to Be Forgotten as in Europe, recent court cases and upcoming data protection laws indicate a growing recognition of the need for digital privacy rights.
Read Full Article
23 Likes
Medium
172

Why NFS Version Matters in Cybersecurity: NFSv3 vs NFSv4
- NFSv3's lack of authentication poses a threat to data security in cybersecurity-sensitive environments.
- NFSv4 simplifies firewall policies and reduces the attack surface, making it ideal for network segmentation and Zero Trust architecture.
- In regulated environments like HIPAA and GDPR, NFSv3's lack of encrypted data-in-transit capability can present compliance challenges.
- Stateful protocols like NFSv4 are crucial for monitoring, auditing, access control, and compliance in forensic investigations.
Read Full Article
10 Likes
Securityaffairs
372

Image Credit: Securityaffairs
Security Affairs newsletter Round 531 by Pierluigi Paganini – INTERNATIONAL EDITION
- North Korea-linked threat actors spread macOS NimDoor malware via fake Zoom updates.
- Google fined $314M for misusing idle Android users’ data.
- Cybercriminals target Brazil in a data breach affecting 248,725 people.
- Denmark introduces new copyright law to protect against deepfakes.
Read Full Article
22 Likes
For uninterrupted reading, download the app