Cyber Security News
VentureBeat
94

Image Credit: VentureBeat
Google quietly launches AI Edge Gallery, letting Android phones run AI without the cloud
- Google has quietly launched the AI Edge Gallery, an experimental Android app that allows users to run AI models directly on their smartphones without internet connection.
- AI Edge Gallery enables tasks like image analysis, text generation, and coding assistance while ensuring data processing remains local.
- The app, available through GitHub, aims to democratize AI access and address privacy concerns related to cloud-based AI services.
- Built on Google’s LiteRT and MediaPipe frameworks, the app supports various machine learning frameworks and is optimized for mobile devices.
- The Gemma 3 model in the app offers efficient language processing and quick response times for tasks such as text generation and image analysis.
- AI Chat, Ask Image, and Prompt Lab are core capabilities of the app, allowing users to perform a variety of tasks offline.
- The on-device processing approach enhances data privacy and compliance with regulations, particularly in sensitive industries like healthcare and finance.
- However, the shift to on-device processing raises new security concerns, requiring organizations to focus on protecting devices and AI models.
- Google's platform approach with AI Edge Gallery differs from competitors, focusing on infrastructure rather than proprietary features.
- While the app faces limitations such as performance variations and installation complexities, it represents a significant shift in AI deployment towards edge computing and privacy-focused strategies.
Read Full Article
5 Likes
Hackernoon
406

Image Credit: Hackernoon
INE Alert: $16.6 Billion In Cyber Losses Underscore Critical Need For Advanced Security Training
- INE Security emphasizes the urgent need for technical cybersecurity professionals to combat cyber threats after record losses of $16.6 billion in 2024 were reported by the FBI.
- Organizations face complex technical challenges such as ransomware evolution, post-compromise detection, and cryptocurrency attacks, requiring specialized skills in threat detection, response, and forensics.
- INE Security offers advanced training programs focusing on threat detection labs, incident response, forensics training, threat hunting methodologies, and industry-specific attack simulations to address the escalating cybersecurity threats.
- The value of skilled security professionals in proactive threat hunting and rapid response capabilities is highlighted, with INE Security providing tailored enterprise training solutions to help organizations enhance their security measures.
Read Full Article
24 Likes
Mcafee
207

Image Credit: Mcafee
How to Protect Your Crypto After the Coinbase Breach
- Coinbase recently experienced a data breach impacting nearly 70,000 users due to insider wrongdoing.
- Sensitive personal information was exposed, leading to potential follow-on attacks and identity theft risks.
- Compromised data includes personal identifiers, financial information, identity documents, and account activity.
- Coinbase refused to pay a $20 million ransom demanded by the attackers and set up a reward fund for their capture.
- The company notified affected users, enhanced defenses, and is collaborating with law enforcement agencies.
- Coinbase users are advised to enable strong two-factor authentication and be cautious of imposters.
- McAfee offers additional safeguards like Scam Detector, reducing digital footprint, and Identity Monitoring.
- Protective measures against identity theft include Transaction Monitoring, Credit Monitoring, and Security Freeze.
- The breach underscores the importance of personal security measures in the digital realm to prevent scams and identity theft.
Read Full Article
12 Likes
Tech Radar
297

Image Credit: Tech Radar
That's a new one: Iranian hackers pretend to be a modelling agency to try and steal user details
- Iranian hackers attempted to steal user details by pretending to be a German modelling agency, as reported by Palo Alto Networks’ Unit 42.
- The malicious website spoofed a legitimate modelling agency website, using obfuscated JavaScript to capture visitor information like browser details and IP addresses.
- The goal of the attack was likely selective targeting based on device and network-specific data collected from visitors.
- Unit 42 speculates that the Iranian threat actors involved could be associated with groups like Agent Serpens or APT35 for potential future attacks involving malware or credential theft.
Read Full Article
17 Likes
Macdailynews
225

Image Credit: Macdailynews
Apple TV is privacy advocates’ go-to streaming device
- Apple TV boxes stand out in terms of privacy protection by avoiding automatic content recognition tracking unlike competitors like Roku, Amazon Fire TV, and Google TV.
- During setup, users of Apple TV have the option to disable features like Siri, location tracking, and analytics data sharing, providing better control over their privacy settings.
- Apple's business model does not rely on selling targeted ads, which leads to less data harvesting and monetization compared to other tech companies, earning them more trust in handling user data according to RJ Cross from PIRG.
- Apple TV is favored by privacy-conscious users for its strong privacy protections, making it a go-to streaming device for those who prioritize safeguarding their personal data.
Read Full Article
13 Likes
TechBullion
279

Image Credit: TechBullion
How aosu Surveillance Cameras Help Prevent Crime in Your Neighborhood
- Neighborhood safety has become a growing concern due to crimes like theft and vandalism.
- Traditional security measures are no longer sufficient to provide adequate protection.
- aosu surveillance cameras offer advanced technology to prevent crime and enhance security in residential neighborhoods.
- These cameras provide real-time monitoring, deterrence, and interaction, making them a versatile and cost-effective security solution.
Read Full Article
16 Likes
TechCrunch
347

Image Credit: TechCrunch
NSO Group asks judge for new trial, calling $167 million in damages ‘outrageous’
- NSO Group is seeking a new trial or reduction in the $167 million damages it was ordered to pay to WhatsApp by filing a motion in court.
- NSO Group's lawyers argue that the punitive damages awarded are 'outrageous' and 'unlawful,' exceeding lawful punitive damages by many orders of magnitude.
- WhatsApp vows to continue fighting the case despite NSO Group's attempts to avoid accountability and seek impunity.
- NSO Group claims that the damages awarded exceed its financial capacity to pay and reflect an improper desire to punish the company.
Read Full Article
20 Likes
Tech Radar
248

Image Credit: Tech Radar
Security flaw in vBulletin forum software exploited by hackers
- A critical security vulnerability in vBulletin, a popular forum software, is being actively exploited in the wild.
- Security researcher Ryan Dewhurst has observed exploitation attempts for the vulnerability, which can lead to remote code execution.
- The vulnerability, with severity scores of 10/10 and 9.0/10, affects vBulletin versions 5.0.0 through 5.7.5 and 6.0.0 through 6.0.3, potentially allowing RCE capabilities.
- Although patches have been released, many sites remain at risk due to delayed patching by administrators of vBulletin forums.
Read Full Article
14 Likes
IEEE Spectrum
315

Image Credit: IEEE Spectrum
Disaster Awaits if We Don’t Secure IoT Now
- In 2015, Ukraine experienced widespread power outages due to a Russian cyberattack on critical infrastructure, signaling a decade of cyber threats on crucial systems. Attacks on infrastructures like a Kansas nuclear plant and the New York City subway have escalated concerns.
- The proliferation of IoT devices, especially Industrial IoT (IIoT) devices, poses a significant risk as the number of connected devices continues to grow exponentially. The potential impact of cyberattacks on IoT devices can extend beyond the devices themselves to cause physical-world damage to entire communities.
- Security for IoT devices is often overlooked due to their limited need for human interaction and non-sensitive information storage. However, cyberattacks on IoT devices can have severe consequences, highlighting the need for proactive security measures.
- To enhance the security of IoT devices, two key strategies are emphasized: basic cybersecurity hygiene and defense in depth. Basic cybersecurity practices include avoiding default passwords, regular software updates, and validating software integrity.
- The U.S. Government's Software Bill of Materials (SBOM) aims to provide transparency in software supply chains, aiding in identifying and addressing vulnerabilities in IoT device software. Having accurate SBOMs can enhance cybersecurity for both device suppliers and users.
- Defense in depth, a less known but crucial approach, focuses on layered security measures involving protection, detection, and remediation. Implementing a layered security model helps safeguard IoT devices against complex vulnerabilities and ensures resilience against cyberthreats.
- A vital component of IoT security is establishing a Root of Trust (RoT) to protect the device's firmware and ensure its integrity. RoT mechanisms, including hardware-based RoTs and secure boot processes, play a key role in safeguarding IoT devices from malicious attacks.
- Remote Attestation, facilitated by hardware components like the Trusted Platform Module (TPM), enhances the security of IoT devices by collecting and reporting evidence of device integrity during startup. This process helps validate the trustworthiness of IoT devices through cryptographic signatures.
- In case of anomalies, remediation actions for IoT devices may involve resetting the device, refreshing software, or utilizing authenticated watchdog timers to ensure device health. Practices like power-cycling and leveraging trusted components aid in mitigating security breaches and ensuring device resilience.
- As IoT cybersecurity measures evolve and become more accessible, both device designers and system integrators need to prioritize implementing robust security mechanisms to protect against cyber threats. The incorporation of high-security mechanisms and reliable software stacks enhances the overall security posture of IoT devices.
Read Full Article
19 Likes
Tech Radar
388

Image Credit: Tech Radar
Key Linux systems may have security flaws which allow password theft
- Two information disclosure vulnerabilities were discovered in Apport and core-dump handler, affecting Ubuntu, Fedora, and Red Hat.
- The vulnerabilities, CVE-2025-5054 and CVE-2025-4598, are race condition bugs that allow threat actors to access sensitive information.
- Mitigations are available for the vulnerabilities, advising users to secure core dumps, implement strict PID validation, and enforce restrictions on accessing SUID/SGID core files.
- Qualys developed proof-of-concept for both vulnerabilities and system administrators are urged to take necessary security measures.
Read Full Article
23 Likes
Microsoft
320

Image Credit: Microsoft
GitHub Secret Protection and GitHub Code Security for Azure DevOps
- GitHub has launched standalone security products, GitHub Secret Protection and GitHub Code Security for Azure DevOps, following changes to GitHub Advanced Security.
- GitHub Secret Protection for Azure DevOps is available for $19 per active committer per month, offering push protection, secret scanning alerts, and security overview.
- GitHub Code Security for Azure DevOps is available for $30 per active committer per month, offering dependency alerts, CodeQL scanning, security findings for third-party tools, and security overview.
- Customers can start using Secret Protection and Code Security plans as soon as it's available in their organization, with no disruption to the current Advanced Security experience for existing customers.
Read Full Article
19 Likes
Securityaffairs
85
Image Credit: Securityaffairs
Police took down several popular counter-antivirus (CAV) services, including AvCheck
- On May 27, 2025, authorities seized crypting service sites (including AvCheck, Cryptor, and Crypt.guru) used by cybercriminals to test malware evasion capabilities.
- An international law enforcement operation, spearheaded by the U.S. Department of Justice, dismantled an online cybercrime syndicate providing encryption services to help malware evade detection.
- The operation, named Endgame, involved global efforts from U.S., Dutch, Finnish, and other national police forces to shut down malware services. The seized domains offered counter-antivirus tools for cybercriminals.
- CAV services like AVCheck enable cybercriminals to test their malware against antivirus programs discreetly, allowing them to gain unauthorized access to computer systems undetected. Undercover agents confirmed the services were linked to ransomware groups behind attacks in the U.S. and abroad.
Read Full Article
5 Likes
Siliconangle
157

Image Credit: Siliconangle
Sysdig detects AI-assisted malware exploiting Open WebUI misconfigurations
- Sysdig's Threat Research Team discovered a malware campaign that exploited misconfigured instances of Open WebUI to deploy malicious, AI-generated payloads targeting Linux and Windows systems.
- The attacker uploaded a malicious Python script through Open WebUI's plugin system, using obfuscation techniques, indicative of AI-generated code.
- The malware targeted crypto mining on Linux systems and included components for credential theft, sandbox evasion, and hardware discovery on Windows systems.
- Sysdig's runtime threat detection was able to identify the threat in real-time, utilizing YARA rules, behavioral detections, and threat intelligence to detect the suspicious activity.
Read Full Article
9 Likes
Tech Radar
189

Image Credit: Tech Radar
US banks don't want to have to reveal when they've been hacked
- US banks are resisting a recent SEC ruling that mandates the disclosure of cyber attacks, citing added strain and complexity to their operations.
- The rule requires public companies to disclose cyber incidents, including impact and scope, within a short timeframe, potentially before internal investigations are completed.
- Banks argue that the additional disclosure obligations could escalate pressure during ransomware attacks and be leveraged by attackers for extortion.
- In response, the banking group has lobbied for extensions to data protection and cybersecurity requirements, while Australia has implemented a similar rule mandating ransomware payment disclosures within 72 hours for organizations above a certain turnover.
Read Full Article
11 Likes
Medium
234
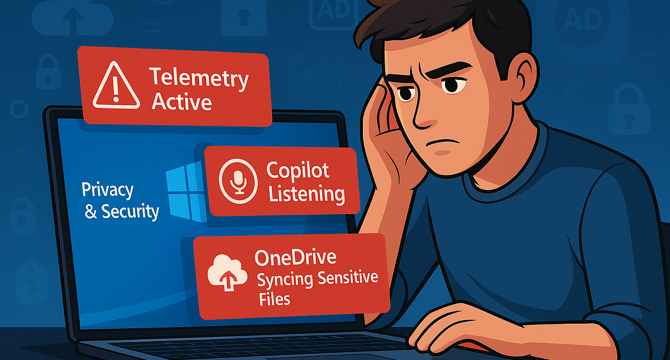
Image Credit: Medium
These 4 Windows Settings Are a Privacy Disaster — Turn Them Off Now
- Windows 11 collects user data through telemetry, which can be disabled in Settings > Privacy & security > Diagnostics & feedback.
- OneDrive in Windows syncs files by default, posing security risks. Users can consider using Proton Drive or setting up a private cloud with Raspberry Pi.
- Windows Recall feature takes screenshots of every user activity, raising privacy concerns. It's important to disable it in Privacy settings.
- Microsoft's Copilot AI assistant on Windows may compromise user data privacy. Users are advised to disable it to have more control over their data.
Read Full Article
14 Likes
For uninterrupted reading, download the app