Cyber Security News
Kaspersky
362

Image Credit: Kaspersky
57 suspicious Chrome extensions with millions of installs | Kaspersky official blog
- Cybersecurity researchers found 57 suspicious extensions in the Chrome Web Store with over six million users.
- The extensions had alarming permissions that didn’t match their descriptions and were hidden from searches.
- Browser extensions can pose security risks and compromise privacy, even if downloaded from official stores.
- The suspicious extensions requested broad permissions, such as access to cookies, potentially allowing for data theft.
- These extensions could track user actions, change search engines, inject scripts, and activate advanced tracking.
- An investigation started with one extension, Fire Shield Extension Protection, which led to the discovery of more suspicious plugins.
- Most of these extensions claimed to block ads or improve search results, but lacked the necessary code to do so.
- The plugins were linked to a suspicious domain and shared common traits, suggesting they belong to the same family of spyware.
- Users are advised to check for and delete suspicious extensions, download only necessary ones, and use reliable security software.
- The extensions appeared to be part of a spyware or data-stealing program family, emphasizing the importance of cautious extension usage.
Read Full Article
21 Likes
Dev
40

Image Credit: Dev
TryHackMe: HTTP in Detail
- TryHackMe's HTTP in Detail room offers a beginner-friendly walkthrough of the HyperText Transfer Protocol (HTTP) and HTTPS, covering key concepts like methods, status codes, headers, cookies, and more.
- The room provides hands-on exercises to explain web communication, data transmission between clients and servers, making it ideal for beginners in web security or networking.
- Tasks in the room include defining HTTP(S), understanding requests and responses, learning HTTP methods like GET, POST, PUT, DELETE, interpreting status codes like 201, 404, 503, 401, exploring headers like User-Agent, Content-Type, Host, and working with cookies.
- The room also involves practical tasks such as making GET, PUT, POST, and DELETE requests to specific pages, along with questions on protocols like TCP/IP and systems like Samba.
Read Full Article
2 Likes
Tech Radar
163
Image Credit: Tech Radar
Chinese hackers use Google Calendar in stealthy new attack
- Chinese state-sponsored hackers known as APT41 have been using Google Calendar in their recent attacks to serve as part of the C2 infrastructure.
- Google’s Threat Intelligence Group dismantled the setup abusing Google Calendar and made changes to prevent future attacks.
- The attack, called ToughProgress, involves phishing emails with malicious .ZIP archives, fake PDFs, and fake JPGs that hide malware.
- To tackle the threat, Google developed custom detection signatures, identified affected companies, and took down associated Workspace accounts and calendar entries.
Read Full Article
9 Likes
Securityaffairs
99
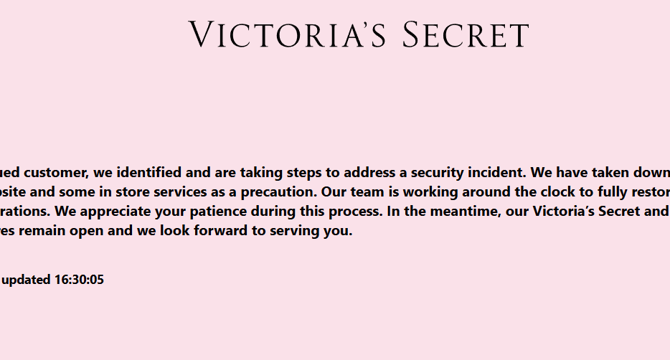
Image Credit: Securityaffairs
Victoria’s Secret ‘s website offline following a cyberattack
- Victoria's Secret took its website offline after a cyberattack that impacted customer care and distribution center operations.
- The company's CEO mentioned that recovery from the cyberattack will take some time as the incident affected email access for some staff.
- After the security incident, Victoria's Secret shares dropped by 6.9%, and the company did not disclose technical details about the attack.
- Recent data breaches in major brands like Dior and Adidas, along with UK retailers facing cyberattacks, indicate a rising threat against retailers globally.
Read Full Article
5 Likes
Pymnts
353

Image Credit: Pymnts
Exodus Selects Worldpay’s Card Payment Capabilities for Cryptocurrency Purchases
- Exodus has partnered with Worldpay to offer card payment capabilities for purchasing cryptocurrencies directly within Exodus' self-custodial crypto wallet.
- The new service, XO Pay, allows customers to buy and sell cryptocurrencies without using third-party exchanges.
- Worldpay's native card payments integrated into the platform enhance and simplify the buying experience for customers.
- Exodus is utilizing Worldpay's fraud detection and prevention solution, FraudSight, to ensure the security of transactions.
Read Full Article
21 Likes
Pymnts
448

Image Credit: Pymnts
Victoria’s Secret Shutters Website Over Security Incident
- Victoria’s Secret's website was shut down due to a security incident, with no details on the nature or start date of the incident disclosed.
- High-profile cyber attacks have been affecting companies recently, with breaches reported at Adidas, Snowflake, and other major organizations.
- Increased reliance on third-party providers in various business operations has raised concerns about cybersecurity vulnerabilities.
- Data breaches involving third parties have doubled from 15% to 30% in recent years, leading to more breach-related lawsuits and financial concerns for companies.
Read Full Article
26 Likes
TechCrunch
231

Image Credit: TechCrunch
A decade in, bootstrapped Thinkst Canary reaches $20M in ARR without VC funding
- Cybersecurity company Thinkst is celebrating its 10th anniversary of launching Canary, their flagship product designed to catch hackers in action.
- With a focus on customer needs over rapid growth, Thinkst has reached $20 million in annual recurring revenue without any external funding.
- Founder Haroon Meer attributes their success to fulfilling promises, resulting in a 60% retention rate of their first-year customers.
- Canary, launched in 2015, acts as an early warning system on networks, alerting companies when hackers breach their systems.
- Canary Tokens, another offering, helps users detect unauthorized access by placing bait in secure locations for monitoring.
- Thinkst's canaries are hard to deploy incorrectly, as they effectively catch attackers whether they blend in or stand out.
- The company relies on word of mouth and organic sales growth, with customers confirming the effectiveness of their products.
- Despite not seeking venture capital, Thinkst believes in running a business that remains attractive for investment or acquisition.
- Founder Haroon Meer envisions every company having multiple canaries, emphasizing the quality and value of their product over immediate revenue growth.
- With a current revenue of $20 million, Thinkst sees further growth potential and emphasizes providing a good product at a fair price.
Read Full Article
13 Likes
Tech Radar
181

Image Credit: Tech Radar
A key Microsoft OneDrive feature has a worrying security flaw which could expose user data
- A security flaw has been found in Microsoft's OneDrive File Picker by researchers, allowing threat actors potential access to cloud archives.
- The flaw is due to excessive permissions requested by File Picker, including read access to the entire drive, caused by the lack of fine-grained OAuth permissions.
- The Oasis Research Team highlighted the consequence of this flaw, potentially leading to customer data leakage and non-compliance with regulations.
- Microsoft has acknowledged the issue regarding the security flaw but has not issued a fix yet.
Read Full Article
10 Likes
Tech Radar
244
Image Credit: Tech Radar
Thousands of Asus routers hacked to create a major botnet planting damaging malware
- Thousands of ASUS routers have been hacked to create a major botnet by threat actors exploiting security vulnerabilities.
- The hackers gained initial access by exploiting poorly secured routers using brute force and authentication bypass methods.
- They abused a known command injection flaw (CVE-2023-39780) to establish persistent access and create a botnet.
- The attackers can maintain long-term access without dropping malware traces, with the number of compromised devices steadily increasing.
Read Full Article
14 Likes
Silicon
240
Image Credit: Silicon
The Disruption Layer: Conversations from the Edge of Change: Head-to-Head
- The key challenge of digital transformation involves aligning strategy, systems, and people at the edge of change, rather than focusing solely on technology.
- Moving from legacy systems to agile, digital ecosystems faces barriers such as poor framing for business models and legacy mindsets.
- Assessing legacy infrastructure for modernization involves evaluating alignment with the business's ambition and vision for transformation.
- AI tools have accelerated reinvention efforts in assisting system changes, implementation guidance, and shaping customer experiences.
- Digital reinvention should not just be a technology upgrade but also a cultural and strategic shift within the business.
- Insurers may need to undergo numerous micro-pivots in their transformation journey to become more adaptive and responsive.
- Success in digital transformation can be measured through operational changes such as customer sentiment, Net Promoter Scores, and product adaptability.
- Adaptivity is crucial for insurers to thrive amid continuous technological disruptions and changing customer expectations.
- Innovation acceleration and adaptability to changing competitive landscapes will define organizations that thrive amid ongoing technological disruptions.
- Insurers need to shift to customer-centric models, adapt rapidly to evolving risks and demographics, and create new propositions to meet modern needs.
Read Full Article
14 Likes
Tech Radar
54

Image Credit: Tech Radar
Victoria’s Secret laid bare after security incident takes down systems
- Victoria's Secret confirmed a cyberattack, leading to the shutdown of its websites and some in-store services.
- No one has claimed responsibility yet for the security incident, and details about the attack remain scarce.
- Victoria's Secret triggered incident response protocols and engaged third-party experts to investigate and restore operations securely.
- With the company's systems offline for at least three days, speculation suggests ransomware as a possible cause, but no confirmation has been made.
Read Full Article
3 Likes
Entrepreneurshiplife
226

Image Credit: Entrepreneurshiplife
Why Cybersecurity Should Be a Top Priority for Every Business and Public Infrastructure
- In today’s interconnected world, digital systems' reliance has increased significantly across all sectors, making cybersecurity vital to prevent attacks.
- Cyberattacks pose a serious threat to essential services and sensitive data, impacting financial and operational stability.
- Critical systems such as power grids and transportation networks require strong cybersecurity measures to prevent disruptions and maintain services.
- Modern systems are vulnerable to cyber threats due to complexities, outdated security measures, and integration of new technologies.
- Cyberattacks have far-reaching economic consequences, leading to financial losses, legal liabilities, and disruptions in various industries.
- Public safety is closely linked to the integrity of critical infrastructure, emphasizing the importance of cybersecurity in ensuring day-to-day operations and citizen well-being.
- Governments worldwide have implemented regulations to enforce cybersecurity practices and hold organizations accountable for data protection.
- AI and automation play a growing role in enhancing cybersecurity by enabling real-time threat detection, response, and continuous network monitoring.
- Organizations need to understand vulnerabilities, comply with regulations, invest in advanced security solutions, and promote a security-conscious culture to mitigate cyber risks effectively.
- Investing in robust cybersecurity strategies is crucial to protecting critical infrastructure, ensuring operational stability, and mitigating the escalating cyber threats of today.
Read Full Article
13 Likes
Dev
185

Image Credit: Dev
Cybersecurity Tips for Users
- Using weak and common passwords makes you an easy target for hackers. Use a password manager and create unique, complex passwords for better security.
- Enable Two-Factor Authentication (2FA) on all your accounts to add an extra layer of security and prevent unauthorized access.
- Be cautious of clicking on suspicious links, as they could lead to phishing scams and compromise your data. Always verify the sender before clicking.
- Avoid using public Wi-Fi without a VPN to protect your sensitive information from potential hackers who may exploit vulnerabilities in public networks.
Read Full Article
11 Likes
TechDigest
206

Image Credit: TechDigest
Victoria’s Secret shuts down US website following ‘security incident’
- Victoria’s Secret has suspended most of its US website and in-store services due to a security incident, with its UK website unaffected.
- The company is working to fully restore operations and has engaged third-party experts to address the situation.
- The incident impacted the company's stock, with shares closing down by approximately 7% on Wednesday.
- This incident adds to a recent spree of cyberattacks targeting retailers, with companies like Marks & Spencer and the Co-op also facing disruptions.
Read Full Article
12 Likes
TechDigest
86

Image Credit: TechDigest
UK consumers at ‘serious risk of fraud’ following leak of 800 million cookies
- Nearly 800 million internet cookies of UK consumers leaked online, posing a significant fraud risk.
- Global cookie leaks surge from 54 billion to 94 billion, with UK ranking 27th out of 253 countries.
- Cookies can contain sensitive personal data and when stolen, can be used by cybercriminals to impersonate users and gain unauthorized access to accounts.
- NordVPN report highlights Google searches as most significant source of cookie leaks, emphasizing the importance of consumer vigilance and cybersecurity measures.
Read Full Article
5 Likes
For uninterrupted reading, download the app