Cyber Security News
Medium
112
Image Credit: Medium
Implement Audit Logs for your Database tables in SQL Server
- Implementing Audit Logging through application code is complex and not recommended. It is more efficient to implement Audit Logs directly in the database.
- Audit Logging involves creating an Audit Log table and an Audit Log trigger for tracking user activity and changes in database tables.
- The Audit Log table mirrors the structure of the target table with additional columns for storing old and new field values, action type, timestamp, and user information.
- The Audit Log trigger captures changes in the database table and populates the Audit Log table with relevant information, such as the type of operation and user responsible for the change.
Read Full Article
6 Likes
Gizchina
67

Image Credit: Gizchina
5 Ways To Keep Your Android Phone Safe During Long Travels
- Traveling with an Android smartphone offers convenience for navigating, booking, and staying connected, but exposes devices to risks like unsecured Wi-Fi networks and theft.
- To protect Android phones during travel, using VPNs, enabling Find My Device, securing with a neck lanyard, avoiding random QR codes, and using eSIM for security are recommended.
- A good VPN is essential to encrypt internet traffic, add privacy, and prevent data tracking on public Wi-Fi networks, enhancing security while traveling.
- Enabling Find My Device feature on Android allows users to track and secure their devices, aiding in locating lost items and remotely wiping data if needed.
- Using a neck lanyard to physically secure the phone can prevent theft or loss, providing an extra layer of protection in crowded or unfamiliar environments.
- Avoiding scanning random QR codes and installing unverified apps helps protect against potential security breaches and malware downloads on Android devices.
- Opting for an eSIM during travel offers enhanced security compared to physical SIM cards, with added benefits like lower costs and increased data protection.
- Being aware of security measures and utilizing resources like VPNs, Find My Device, neck lanyards, cautious app downloads, and eSIMs can help safeguard Android phones during trips.
- Travelers should prioritize securing their smartphones to prevent data breaches, theft, and other risks while on the go for a seamless and safe travel experience.
- Adopting practical habits and taking proactive steps to protect Android devices before and during travel is crucial for ensuring data privacy and device security.
Read Full Article
4 Likes
Tech Radar
320

Image Credit: Tech Radar
Criminals hijacking subdomains of popular websites such as Bose or Panasonic to infect victims with malware: here's how to stay safe
- Criminals have been hijacking subdomains of major organizations like Bose, Panasonic, and CDC to spread malware and conduct online scams.
- Security experts have identified a threat group called Hazy Hawk utilizing misconfigured DNS records to redirect visitors to malicious sites.
- Hazy Hawk exploits abandoned cloud resources with dangling DNS records to control legitimate-looking subdomains for spreading malware.
- To stay safe, individuals should be cautious of push notifications from unfamiliar sites, while organizations must prioritize DNS hygiene and use automated monitoring tools for threat detection.
Read Full Article
19 Likes
Dev
307

Image Credit: Dev
From Classroom to HackTheBox: My Journey Through Cybersecurity Degree, Certifications, and the Power of Practical Experience
- The article recounts the author's cybersecurity journey encompassing a mix of degree, certifications, and practical experience acquired through platforms like INE, TryHackMe, and HackTheBox.
- It emphasizes the importance of combining classroom learning, certifications, and practical skills to establish a solid foundation in cybersecurity and enhance job readiness.
- The author discusses the advantages and limitations of pursuing a cybersecurity degree, highlighting the need for hands-on practice and self-learning to be job-ready.
- Various well-known certification bodies like OffSec, CREST, and GIAC are explored for their industry recognition and practicality in preparing professionals for cybersecurity roles.
- The article provides insights into technical and practical-focused certifications offered by platforms like HackTheBox, INE, TCM Security, Altered Security, and others.
- It presents considerations for choosing between a cybersecurity degree and certifications, emphasizing the importance of a balanced approach combining theory and practical skills.
- Hands-on experience is deemed essential, with platforms like HackTheBox, TryHackMe, and INE labs mentioned as valuable resources for building real-world offensive security skills.
- The author offers do's and don'ts for aspiring cybersecurity professionals, stressing the significance of mastering basics, continuous learning, balancing theory with practice, networking, and documenting progress.
- The importance of staying updated on emerging trends in cybersecurity and not neglecting soft skills like communication is highlighted in the article.
- In conclusion, the article advocates for a holistic approach to cybersecurity education by integrating degrees, certifications, and practical experience for a well-rounded foundation.
- It underlines the need for curiosity, dedication, and adaptability in the cybersecurity field, suggesting a gradual progression from beginner-friendly platforms like TryHackMe to more advanced challenges on HackTheBox.
Read Full Article
18 Likes
Medium
434
Image Credit: Medium
Inconsistencies in CyberSecurity
- The concept of vulnerabilities occurring at integration points of systems is highlighted, such as cache deception due to lack of understanding of CDN workings and URL parsing discrepancies causing security gaps.
- A vulnerability in Google reCAPTCHA, as exposed by James Kettle, emphasizes the risk of race conditions, potentially affecting multiple websites using reCAPTCHA.
- Expanding the concept beyond reCAPTCHA, exploiting vulnerabilities like unchecked rate limiting in image upload functions and payment gateway integration issues further underscores the impact of integration gaps.
- Instances of inconsistent data handling leading to exploits, like manipulating payment IDs to repeatedly receive funds on a compromised exchange, showcase the significance of meticulous system integration understanding.
- Inadequate data validation and rate limiting, as observed in third-party PII verification services, provide avenues for resource depletion and unauthorized access, reflecting the broader issue of oversight in integration protocols.
- The narrative emphasizes the necessity for thorough scrutiny during bug bounty programs and pentests, advocating attention to detail at system junctions to identify and mitigate vulnerabilities effectively.
- Developer negligence towards documentation comprehension is pinpointed as a primary cause of vulnerabilities, emphasizing the criticality of understanding not only external systems but also internal components like libraries utilized in coding.
- The pervasive nature of inconsistencies between browsers and JavaScript, as highlighted in various cases, serves as a reminder of the omnipresence of integration challenges in cybersecurity landscapes.
- The need for developers to meticulously engage with documentation and understand the intricacies of third-party services, APIs, and libraries is underscored, noting that oversights in such areas can lead to exploitable security vulnerabilities.
- The article gestures towards the importance of vigilance and comprehension in navigating integration complexities for cybersecurity professionals and developers, urging a proactive approach towards securing systems.
- The author hints at future content exploring thematic subjects discussed at the NahamCon conference, particularly focusing on inconsistencies highlighted in Voorivex's presentation, aligning with the overarching theme of system integration challenges in cybersecurity.
Read Full Article
26 Likes
Siliconangle
235

Image Credit: Siliconangle
Ready for a post-quantum world? The time to start is now
- Quantum computing advancements pose a threat to current encryption technology, potentially compromising data security in the future.
- Organizations need to prepare for a post-quantum world to mitigate cryptography risks and transition to quantum-safe solutions.
- The transition from classical to post-quantum cryptography requires a multiyear migration strategy and supports hybrid solutions.
- NIST released three post-quantum encryption standards in 2024, setting clear goals for implementation and migration roadmaps.
- Challenges include outdated applications, hardware limitations, and the need for crypto-agility in the face of evolving algorithms.
- Companies like IBM and others offer post-quantum solutions ranging from hardware to full-lifecycle migration support.
- Quantum Xchange, CryptoNext, and IBM provide tools for discovery, remediation, and management of post-quantum cryptographic assets.
- Various vendors offer quantum technologies like quantum key distribution, quantum random number generators, and post-quantum cryptographic libraries.
- Industries such as telecommunications, government agencies, and data centers are early adopters of post-quantum technologies for enhanced security.
- Enterprises are advised to establish cryptography task forces to coordinate post-quantum mitigation strategies across their organizations.
Read Full Article
14 Likes
Medium
343

Image Credit: Medium
Inside the Black Box: How US Border Agents Crack Your Devices
- French space researcher denied U.S. entry over text messages critical of Trump administration's policies, leading to diplomatic tensions.
- Michigan attorney faced targeted search at Detroit airport for representing pro-Palestinian protester; refused to surrender phone due to privileged client information.
- U.S. Customs and Border Protection conducted over 47,000 electronic device searches in FY 2024, with a significant increase in searches over years.
- Advanced tools like Cellebrite's UFED and GrayKey enable comprehensive data extraction from devices, including deleted files and security bypass.
- Legal foundation for electronic device searches lies in CBP Directive #3340-049A, using the border search exception to the Fourth Amendment's warrant requirement.
- Device searches reveal disparities based on demographics, with a higher percentage targeting non-U.S. citizens.
- CBP's centralized management systems retain relevant data from searches indefinitely, with some travelers experiencing extended device detention.
- Legal battles concerning electronic device searches at borders involve balancing privacy concerns with traditional border search powers, resulting in contrasting court decisions.
- Citizenship status determines the legal protections and potential consequences of device searches at borders, impacting travelers' rights and decision-making.
- With evolving legal and technical landscapes, strategies like Lockdown mode and security hygiene help protect digital privacy during border crossings.
Read Full Article
20 Likes
Secureerpinc
13

Image Credit: Secureerpinc
Ransomware Hackers Exploit New Windows Flaw
- Ransomware hackers exploited a new Windows flaw, targeting various sectors with malware and malicious tools.
- The exploit included threats like PipeMagic backdoor, Grixba infostealer, and Encryptors, causing endpoint protection failure and demanding ransom.
- Microsoft addressed the Windows flaw with a cumulative update in April 2024, reducing the vulnerability for users.
- To enhance cybersecurity preparedness, organizations are advised to update systems, enable multi-factor authentication, and create offline data backups.
Read Full Article
Like
Medium
384
Image Credit: Medium
Yahoo Breach Retrospective: What We Still Ignore
- In 2013, hackers stole personal data from 3 billion Yahoo user accounts, but the breach was hidden for three years.
- Lessons from the Yahoo breach, like weak encryption and corporate cover-ups, remain unlearned a decade later.
- Yahoo stored passwords using the outdated MD5 hashing algorithm, and security questions were stored in plain text.
- The reason why we are still ignoring these issues is a dangerous cycle of denial, and breaking it requires acknowledging and addressing security vulnerabilities.
Read Full Article
23 Likes
Medium
126

Image Credit: Medium
Why Your Email Address Is a Privacy Risk (And What You Can Do About It)
- Email addresses have become a unique identifier linking various aspects of an individual's online activities, posing a significant privacy risk.
- Using a single email address across multiple platforms allows companies to create detailed profiles about individuals, making them vulnerable to data breaches, scams, and spam.
- Privacy-focused users are increasingly turning to email aliases, such as emalias.app, to enhance online privacy by creating unique identifiers for different services.
- Email aliases offer users greater control over their online identity, allowing them to manage communications, assess trustworthiness of services, and mitigate spam or security threats effectively.
Read Full Article
7 Likes
Arstechnica
411

Image Credit: Arstechnica
Ransomware kingpin “Stern” apparently IDed by German law enforcement
- German law enforcement has identified the leader of the Russian cybercrime cartel Trickbot known as 'Stern'.
- The leader, using the name 'Stern', orchestrated attacks on thousands of victims including hospitals and schools over roughly six years.
- The real-world name of the cybercriminal leader 'Stern' is identified as Vitaly Nikolaevich Kovalev, a 36-year-old Russian man.
- Germany has issued an Interpol red notice for Kovalev, who is believed to be in Russia, for allegedly leading a criminal organization.
Read Full Article
24 Likes
Gizchina
393

Image Credit: Gizchina
How to Run an Antivirus Scan and Keep Yourself Safe
- To protect yourself from cyber threats like viruses and malware, it's essential to run antivirus scans and use software properly.
- Choose antivirus software with features like real-time protection, automatic updates, ransomware protection, web protection, firewall, and email scanning.
- Ensure your antivirus software is regularly updated to detect the latest threats created by hackers.
- Be vigilant for signs of infection like system slowdowns, pop-ups, unfamiliar toolbars, app crashes, and strange files.
- Different types of scans include quick scans, full scans, custom scans, and boot-time scans, each serving a specific purpose.
- Perform scans with precautions like closing heavy programs, connecting to power sources, and addressing potentially unwanted programs.
- Review scan results thoroughly, take necessary actions on threats, and understand how malware entered your system to prevent future breaches.
- Enhance security post-scan by updating software, changing passwords, backing up files, and enabling real-time protection.
- Develop good cyber habits like avoiding suspicious links, using strong passwords, updating software, and being cautious on public Wi-Fi.
- Regular antivirus scans are crucial for detecting threats early, protecting personal information, maintaining system efficiency, and preventing costly damage.
Read Full Article
23 Likes
Medium
13
Image Credit: Medium
OPSEC vs. the illusion of security
- Operational Security (OPSEC) is crucial for protecting investigations from being compromised, traced back, or discovered.
- When conducting online investigations, OPSEC serves as your digital armor to safeguard your identity.
- Casual browsing is different from Open Source Intelligence (OSINT) investigations where you actively seek information that might be hidden.
- Inadequate OPSEC can expose investigators to personal risks, legal issues, and can jeopardize the entire investigation.
- Investigators can unconsciously leave digital footprints through browser fingerprinting, IP address exposure, and metadata in files.
- Linkages between accounts, created using similar devices or browsers, can compromise an investigator's anonymity.
- Effective OPSEC requires multiple layers of protection and a cautious approach to new leads or subjects.
- Understanding the security mindset and implementing consistent security measures are essential in OSINT investigations.
- Consistent security practices, proper isolation in investigations, and preparedness for potential breaches are key in maintaining a secure investigative environment.
- Starting with strong security protocols ensures the safety and credibility of an investigation, laying a solid foundation for effective outcomes.
Read Full Article
Like
Medium
438

the rise of quiet quitting 9
- Quiet quitting has gained popularity on social media platforms like TikTok, Instagram, and LinkedIn as a form of digital self-care.
- It is not about laziness but a conscious effort to prioritize mental health and set boundaries in the workplace.
- The trend challenges traditional notions of overwork and hustle culture, emphasizing the importance of balance and emotional sustainability.
- Quiet quitting has become a symbol of modern self-care and is reshaping conversations around mental health and work culture.
Read Full Article
26 Likes
Medium
375
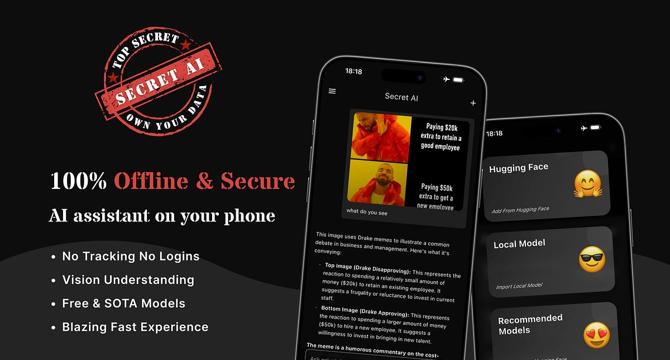
Image Credit: Medium
Introducing Secret AI: The Truly Private AI Assistant That Works 100% Offline
- Secret AI is a new AI assistant that works 100% offline on mobile devices, ensuring complete privacy and zero data collection.
- It supports CPU and GPU acceleration with popular model formats, providing impressive performance based on device capabilities.
- Users can access cutting-edge open-source models, upload photos for on-device AI analysis, and connect to custom API engines for enhanced capabilities while maintaining privacy.
- Secret AI offers a secure platform for sensitive conversations, business ideas, creative projects, learning, and research. It is available on iOS App Store and Google Play Store with both free and premium features.
Read Full Article
22 Likes
For uninterrupted reading, download the app