Cyber Security News
TechDigest
393

Image Credit: TechDigest
Britain to unleash army of cyber hackers to take on Putin
- Britain is investing over £1 billion in artificial intelligence and a dedicated hacking attack team to enhance defensive and offensive cyber capabilities.
- The newly established Cyber and Electromagnetic Command will lead the enhanced offensive cyber operations to confront hostile states, primarily Russia, with a focus on faster decision-making on the battlefield.
- Defence Secretary John Healey confirmed Britain's intent to conduct offensive hacks and emphasized the urgency due to increasing cyberattacks faced by the Ministry of Defence from hostile states like Russia, China, Iran, and North Korea.
- The investment will bring a Digital Targeting Web, known as a 'kill web,' into action by 2027 and aims to ensure faster connectivity and information sharing among military forces for quicker responses in cyber warfare.
Read Full Article
23 Likes
Securityaffairs
176
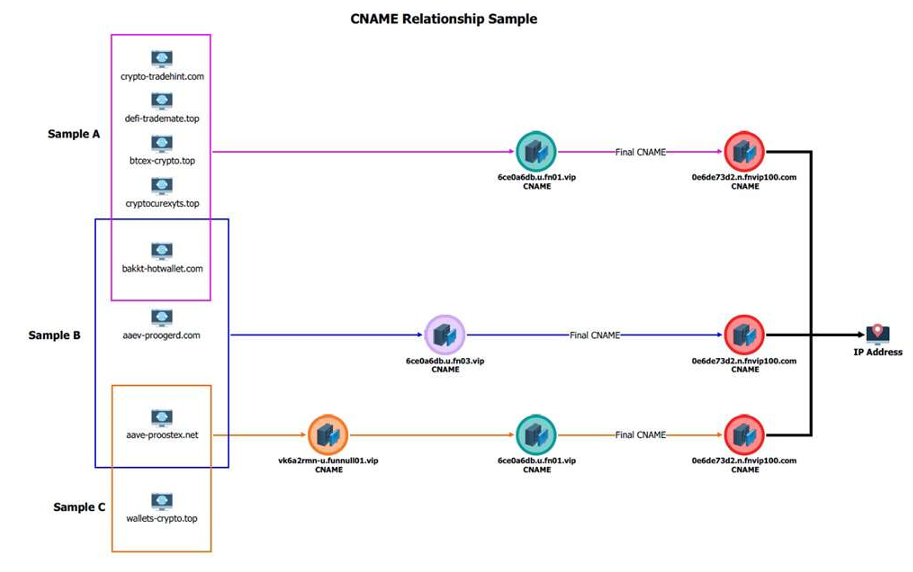
Image Credit: Securityaffairs
US Treasury sanctioned the firm Funnull Technology as major cyber scam facilitator
- The U.S. Treasury sanctioned Funnull Technology and Liu Lizhi for facilitating romance scams leading to significant losses in cryptocurrency fraud.
- Funnull Technology Inc. aided in cyber scams by providing infrastructure for fake platforms, resulting in over $200 million in losses for U.S. victims.
- Romance scams involve scammers building fake romantic relationships to exploit victims for financial gain by manipulating them into sending money or sensitive information.
- The FBI issued a FLASH alert highlighting indicators of compromise associated with Funnull's malicious cyber activities, including patterns of IP address activity and domain migrations.
Read Full Article
10 Likes
Medium
594

Image Credit: Medium
AI in Cyber Security Course in Delhi, India (2025)
- Craw Security offers a comprehensive AI in Cyber Security course in Delhi (2025) focused on using AI tools for enhancing digital protection.
- The course covers effective AI technologies in cybersecurity, making Craw Security a preferred institute in Delhi for cyber security training.
- The career outlook in AI and Cybersecurity is promising in 2025, with opportunities in government sectors, defense, finance, tech companies, and MNCs.
- The AI in Cyber Security Course fees at Craw Security are budget-friendly, including easy EMI options and discounts for students and professionals.
Read Full Article
19 Likes
Tech Radar
72
Image Credit: Tech Radar
Microsoft Authenticator begins password autofill phase out this week - so export now, or you could lose them forever
- Microsoft Authenticator is phasing out password autofill capabilities, which will end in July 2025.
- Users are advised to export their saved passwords or switch to using Microsoft Edge for autofill functionality.
- Timeline: New passwords cannot be saved in Authenticator from June 2025, autofill stops in July 2025, and saved passwords become inaccessible in August 2025.
- Passwords are synced with Microsoft Account and can be accessed through Edge after Authenticator's autofill function is deprecated.
Read Full Article
4 Likes
Lastwatchdog
321

RSAC Fireside Chat: Human and machine identity risks are converging — and they’re finally visible
- Non-human service accounts have become a significant liability in enterprise security, outnumbering humans by 30 to 1, particularly in cloud environments.
- Anetac has developed a streaming telemetry model to address the visibility and risks associated with service accounts, identifying issues like over-permissioned credentials and dormant accounts.
- Anetac's new product, Human Link Pro, aims to bridge the gap between non-human and human credential risks by focusing on the Joiner, Mover, Leaver lifecycle and identifying persistent exposure points in identity management.
- The platform has revealed cases of active credentials for employees who left up to 18 years ago, emphasizing the importance of continuous telemetry to enhance visibility of identity-related risks.
Read Full Article
19 Likes
Global Fintech Series
407

Image Credit: Global Fintech Series
How FinTechs Are Using AI for Smarter AML Surveillance
- AI is revolutionizing AML surveillance by providing more efficient and intelligent detection mechanisms to combat financial crime.
- AI-driven analytics allow for the identification of hidden patterns, real-time detection of suspicious behaviors, and streamlined compliance efforts.
- FinTechs are leading the transformation by integrating AI into their AML strategies to enhance risk assessment and fraud detection.
- AI shifts AML surveillance from rule-based to dynamic approaches, enabling real-time analysis, risk assessment, and prioritization of high-risk cases.
- AI minimizes false positives, anticipates risks with predictive analytics, automates compliance processes, and evolves to counter evolving financial crimes.
- Challenges for small financial institutions in adopting AI for AML include high costs, lack of expertise, data availability issues, regulatory complexities, and legacy system integration challenges.
- Strategies to overcome AI adoption barriers include industry partnerships, cloud-based solutions, upskilling the workforce, phased implementation, and exploring pre-configured AI solutions.
- AI is enhancing financial institutions' ability to prevent financial crimes by reducing false positives, automating compliance tasks, and leveraging predictive analytics.
- The integration of AI and human expertise is crucial for a resilient and trustworthy AML ecosystem, ensuring ethical oversight and accurate interpretation of financial behaviors.
- The future of AML surveillance lies in information sharing, regulatory advancements, and further developments in AI-driven technologies.
Read Full Article
24 Likes
Tech Radar
199
Image Credit: Tech Radar
ConnectWise hit by nation-state cyberattack, some ScreenConnect customer systems affected
- ConnectWise experienced a cyberattack believed to be from a nation-state actor, impacting a small number of ScreenConnect customers.
- ConnectWise triggered its incident response plan, engaged with Mandiant for investigation, and implemented enhanced monitoring and security measures.
- The exact details of the attack, including the threat actor involved and the scope of impact, remain undisclosed.
- ConnectWise had previously patched security flaws in 2024 that were exploited by cybercriminals and nation-state actors, with a high severity vulnerability fixed in ScreenConnect versions.
Read Full Article
11 Likes
Securityaffairs
221

Image Credit: Securityaffairs
ConnectWise suffered a cyberattack carried out by a sophisticated nation state actor
- ConnectWise detected suspicious activity linked to a nation-state actor, impacting a small number of its ScreenConnect customers.
- ConnectWise confirmed the cyberattack and launched an investigation with cybersecurity firm Mandiant, patching the flaw in ScreenConnect and implementing enhanced security measures.
- The breach possibly occurred in August 2024 and went unnoticed until May 2025. The ScreenConnect flaw (CVE-2025-3935) may have allowed remote code execution via stolen machine keys.
- Threat actors exploited ScreenConnect vulnerabilities (CVE-2024-1709 and CVE-2024-1708) in early 2024, with Black Basta and Bl00dy ransomware groups actively exploiting the flaws.
Read Full Article
13 Likes
TechJuice
108

Image Credit: TechJuice
GriffithRAT: New Malware Threatens Fintech and Trading Platforms
- Global security firm Kaspersky has discovered a new malware strain called GriffithRAT, posing a serious threat to the fintech sector.
- GriffithRAT is actively targeting fintech companies, online trading platforms, and betting services in countries like the UAE, Egypt, Türkiye, and South Africa.
- The malware spreads through messaging platforms, installs covertly, and grants hackers remote access to steal data, including login credentials, keystrokes, and screenshots.
- Experts urge businesses in the financial industry to enhance cybersecurity measures, including refraining from downloading unsolicited files, updating antivirus software, and educating employees on cyber threats.
Read Full Article
6 Likes
The Register
421
Image Credit: The Register
Infosecurity Europe 2025 drives cybersecurity priorities amid growing global risks
- Infosecurity Europe 2025 celebrates its 30th anniversary with the theme 'Building a Safer Cyber World' at ExCeL London from 3-5 June.
- The event will feature nine content theatres, over 200 hours of sessions, and nearly 250 speakers addressing critical challenges and emerging threats with more than 13,000 professionals attending.
- Keynote speakers include Professor Brian Cox and Rory Stewart, discussing topics ranging from science rebuilding trust to geopolitics and cyberconflict.
- New features for 2025 include SANS Masterclasses focusing on Cloud Security and Security Culture, an AI & cloud security stage, and engaging sessions with industry practitioners and policymakers.
Read Full Article
25 Likes
Dev
135

Image Credit: Dev
Which Authentication Method Would You Choose for Your Website in 2025?
- Authentication methods in the digital world are evolving constantly to enhance security and user experience.
- Options like social login with Google, Facebook, or Apple offer convenience but raise concerns about control and reliance on third parties.
- Multi-Factor Authentication (MFA) provides enhanced security through multiple layers but may introduce friction in the login process.
- Single Sign-On (SSO) streamlines access across multiple services, catering to scalability but may be perceived as complex for smaller websites.
Read Full Article
8 Likes
Medium
181

Image Credit: Medium
The Daily Tech Digest: 30 May 2025
- The field of Artificial Intelligence and Machine Learning has seen significant advancements and integration into various sectors, showcasing AI's maturity and impact.
- Notable developments include Google DeepMind's MedGemma for medical text and image comprehension, DeepSeek's efficient R1 AI model, and Sora in Azure OpenAI by Microsoft Azure.
- Perplexity's data generation tool expands AI utility beyond text to structured data formats, and Hugging Face unveils humanoid robots, signaling a move into physical AI.
- VS Code introduces auto-approval for tools, enhancing developer workflows. Ethical considerations, cybersecurity vulnerabilities, and policy impacts are critical in AI and tech.
- Recent warnings about OneDrive cloud access vulnerability, State Department reorganization, and foreign student visa crackdown raise concerns about data security and civil liberties.
- Counterterrorism sanctions, RealPage AI law ban, and corporate decisions affecting the tech industry prompt scrutiny and discussions on regulatory oversight and consumer protection.
- In consumer tech, Grammarly secures substantial funding, Delaware AG evaluates OpenAI restructuring, and Angular v20 and .NET Aspire enhancements drive innovation.
- AWS Amplify, Zune creator's role at Amazon, and CSS if() function in Chrome 137 reflect technological evolution and strategic market shifts in the tech sector.
- Instagram's content format expansion and Tesla's secretive robotaxi service raise questions about user experiences and regulatory challenges in tech advancements.
- In the realm of startups, DeepSeek's R1 AI model and Perplexity's data generation tool offer efficiency and innovation, while GitLab Duo Chat and .NET developments streamline development processes.
Read Full Article
10 Likes
Tech Radar
40
Image Credit: Tech Radar
Over a million critical severity records exposed in Q1 2025 alone - make sure you're not at risk
- Norton's Gen Threat Report for Q1 2025 shows a surge in data stealing threats and over 1.19 million records breached, including plaintext passwords.
- Breach events increased by 36% year-on-year with a rise in identity protection incident notifications and potential fraud alerts.
- Financial threats profited significantly in Q1, particularly through AI-powered deepfake and cryptocurrency scams, with one campaign yielding $3.8 million for scammers.
- Cybercriminals are utilizing advanced technologies like AI and deepfakes to exploit trust, as per the Gen Q1/2025 Threat Report by Norton.
Read Full Article
2 Likes
Cryptonews
249

SEC Commissioner Hester Peirce Tells Crypto Investors to ‘Be an Adult’, Clarifies Securities Transactions
- Hester Peirce, head of SEC's Crypto Taskforce, advised crypto investors to handle their losses like adults at the Bitcoin 2025 conference in Las Vegas.
- Peirce emphasized the need for consistency in the crypto community regarding government intervention, stating that profits and losses are part of the game.
- She highlighted that the securities status of a crypto transaction depends more on the specific deal details rather than the digital assets involved.
- Peirce expects the number of crypto assets considered securities to increase with the tokenization of real-world assets like stocks and bonds.
Read Full Article
14 Likes
The Register
366

Image Credit: The Register
Security outfit SentinelOne's services back online after lengthy outage
- Security services vendor SentinelOne experienced a major outage on Thursday, impacting commercial customer consoles.
- Despite the outage, SentinelOne assures customers that their endpoints are still protected, but managed response services are affected.
- The outage lasted for at least six hours and has been attributed to a cloudy problem, possibly related to services hosted in AWS.
- SentinelOne restored services at 7:41PM UTC on Thursday, stating that early analysis suggests it was not a security incident.
Read Full Article
21 Likes
For uninterrupted reading, download the app