Cyber Security News
Medium
294

Image Credit: Medium
Advanced Persistent Threat Simulation for Global Critical Assets
- Advanced Persistent Threats (APTs) are sophisticated, state-sponsored groups targeting critical global assets like government infrastructure and financial systems.
- An article discusses simulating APTs in a controlled lab environment to understand the Tactics, Techniques, and Procedures (TTPs) of threat actors like APT29, Hafnium, and Lazarus.
- The simulation involves using tools like CALDERA by MITRE for framework, OpenCTI and MISP for threat intelligence, and Atomic Red Team for APT emulation among others.
- By implementing an APT Simulation Lab, organizations can proactively train defenders, validate controls, and gain strategic visibility against dangerous threat actors to enhance cybersecurity measures.
Read Full Article
17 Likes
Dev
85

Image Credit: Dev
How to Stay Safe from Cyber Attacks: Tips Anyone Can Follow
- Cyber attacks are increasingly targeting everyday internet users, emphasizing the importance of cybersecurity readiness for all.
- Simple steps to stay safe online include using strong and unique passwords, enabling two-factor authentication, keeping software updated, and avoiding public Wi-Fi for sensitive activities.
- Additional measures involve being cautious of phishing attacks, protecting devices with antivirus software, regularly backing up data, and securing home networks with advanced encryption.
- Educating family or team members about cybersecurity, choosing the right cybersecurity partner, and staying informed and compliant with cybersecurity laws are all crucial for maintaining online safety.
Read Full Article
5 Likes
Dev
194

Image Credit: Dev
Cybersecurity for Beginners: How to Get Started in 2025
- Cybersecurity is about protecting devices, data, and networks from digital attacks like malware and phishing.
- In 2025, cybersecurity is crucial as everything is connected online, making basic cybersecurity skills essential for individuals and businesses.
- Steps to start in cybersecurity include learning basics, choosing a learning path, setting up a practice lab, following cybersecurity frameworks, staying updated, and understanding OT security.
- Beginner tips for success in cybersecurity include using free resources, practicing daily, joining online communities, and documenting your learning.
Read Full Article
11 Likes
Medium
122

Image Credit: Medium
Top Dangers of the Internet
- Cyberbullying is a major risk for children online, with bullies potentially being known individuals or strangers. Parents should educate children on seeking help if they experience cyberbullying.
- Online predators exploit children via social media, aiming to establish relationships for harmful purposes. Setting social media accounts to private and educating kids on online risks are crucial preventive measures.
- Emphasize the importance of keeping social media profiles private and refraining from posting sensitive information that could be exploited by malicious individuals to harm your child.
- Children are vulnerable to online scams that appear too good to be true, such as promises of freebies or cash prizes. Teach kids to be cautious of such offers and never click on suspicious links to avoid potential risks and virus infections.
Read Full Article
7 Likes
Medium
434

Image Credit: Medium
Your Role in Combating Internet Crimes Against Children
- Over 5,600 law enforcement officers and child care advocates specializing in Internet Crimes Against Children attended a conference focused on combating online child exploitation.
- Tech companies like TikTok, Google, Snap, Meta, Dropbox, and Yahoo hosted sessions to guide law enforcement on obtaining evidence to prosecute criminals by cooperating with platforms.
- The National Center for Missing and Exploited Children received over 30,000 CyberTips in a single state alone, showing the magnitude of child crimes and the need for increased resources.
- Urgent actions required include providing support to organizations like Savvy Cyber Kids, as funding constraints hinder law enforcement efforts to combat child sexual predators effectively.
Read Full Article
26 Likes
Medium
126

Image Credit: Medium
How to Foster Community in the Virtual Classroom
- Remote learning and online classrooms remain important options even though not as necessary as last year.
- Parents of K-12 students receiving only in-person instruction are more satisfied than those whose children are learning online.
- Fostering an online community in the virtual classroom is crucial for ensuring quality education and student support.
- Building a sense of support, respect, and confidence among students in their Internet proficiency is essential for the future.
Read Full Article
7 Likes
Dev
443

Image Credit: Dev
Security news weekly round-up - 30th May 2025
- AI developer assistant in GitLab has been found vulnerable to malicious code injection, emphasizing the need for developers to carefully verify code generated by such AI tools.
- Attackers are exploiting trust in NPM packages to steal data by collecting internal and external network identifiers for follow-up attacks.
- Employees searching for payroll portals on Google are being tricked into sending paychecks to hackers through deceptive websites and phishing pages.
- A campaign using fake Docusign emails aims to harvest personal information, prompting organizations to enhance phishing awareness programs to prevent falling victim to such scams.
- Cybercriminals are spreading Venom RAT and stealing crypto wallets by cloning an antivirus site to distribute malware under the guise of security software downloads.
- OneDrive's misconfiguration granting web apps full read access to all files raises concerns over data security and the need for users to be cautious of authorizing SaaS plug-ins.
Read Full Article
26 Likes
Securityaffairs
63

Image Credit: Securityaffairs
Meta stopped covert operations from Iran, China, and Romania spreading propaganda
- Meta stopped covert operations from Iran, China, and Romania targeting social media platforms with propaganda.
- Three influence operations disrupted by Meta using fake accounts on Facebook, Instagram, and more.
- Accounts removed linked to China-based network targeting Myanmar, Taiwan, and Japan.
- Meta also removed accounts tied to Iran-based network targeting Azeri-speaking users and accounts linked to a Romania-based network.
Read Full Article
3 Likes
Medium
239
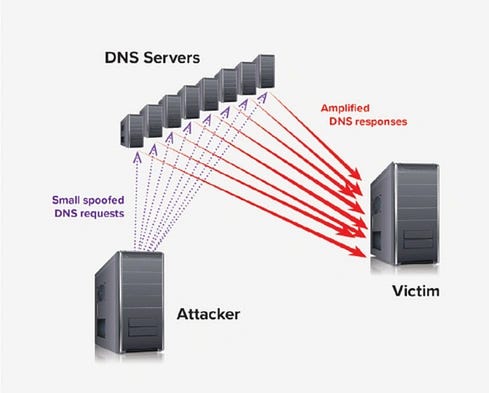
Image Credit: Medium
DNS Cache Poisoning: The Invisible Hacker in the Network
- DNS Cache Poisoning, also known as DNS Spoofing, poses a threat by manipulating trust and redirecting users to malicious servers.
- DNS serves as the internet's phonebook, translating domain names to IP addresses and caching responses for efficiency.
- DNS Cache Poisoning involves injecting false DNS records to reroute users to fake sites.
- Attackers exploit vulnerabilities in the DNS caching mechanism to execute poisoning attacks.
- Key concepts involved include guessing transaction IDs, predictable source ports, and race conditions.
- Attack tools like dsniff, Ettercap, and dnsspoof are commonly used for DNS poisoning.
- Real-world incidents in Iran and China have showcased the impact of DNS spoofing on redirecting users and censoring content.
- Defense mechanisms against DNS Cache Poisoning include DNSSEC, randomizing source ports, encrypted DNS protocols, and hardened recursive resolvers.
- The future of DNS security faces challenges despite advancements like DNSSEC and encrypted protocols, highlighting the need for vigilance and defense strategies.
- DNS Cache Poisoning underscores the importance of understanding and combating this threat to safeguard online identities and data.
Read Full Article
14 Likes
Dev
371

Image Credit: Dev
The Hacker’s New Assistant: How AI is supercharging Cyber crime In 2025
- Generative AI and big language models are increasingly being used by cyber criminals in 2025 to automate attacks tailored to their targets.
- AI technologies like generative AI are employed by hackers for social engineering through fake profiles, deep fakes, and phishing campaigns.
- Cyber attacks in 2025 involve AI-generated texts, images, and videos impersonating high-profile individuals to deceive targets.
- Traditional cybersecurity training is deemed inadequate in combating AI-powered cyber threats, urging for more practical approaches and immediate action.
- Protecting against AI-powered cyber attacks in 2025 involves utilizing biometrics, limiting access, and leveraging AI for anomaly detection.
- Human vigilance remains crucial in combating cyber threats, emphasizing regular employee training, and utilizing multi-factor authentication.
- The legal and ethical implications of AI-generated threats pose challenges, especially concerning privacy and accountability.
- Businesses must adapt their cybersecurity measures to address the evolving landscape of cyber threats intertwined with AI advancements.
- As AI technology progresses, legal frameworks, rights, and responsibilities need to evolve to address the increasing risks posed by AI-generated threats.
- The intersection of AI and cybercrime demands a thorough reevaluation of security measures, privacy concerns, and ethical considerations to mitigate potential risks effectively.
Read Full Article
22 Likes
Tech Radar
90

Image Credit: Tech Radar
Devious new ClickFix malware variant targets macOS, Android, and iOS using browser-based redirections
- ClickFix malware variant now targets macOS, Android, and iOS after evolving from a Windows-only attack
- Attack involves browser-based redirections starting from a compromised website, leading users to a fake URL shortener and a download page
- On macOS, the attack triggers a terminal command to execute a malicious script, while on Android and iOS, it leads to a drive-by attack without requiring user interaction
- Antivirus programs have already flagged the malicious payload, showing the expanding reach of attackers across different operating systems
Read Full Article
5 Likes
Medium
162

Image Credit: Medium
Northern California Children’s Therapy Center Data Breach: What Parents and Families Need to Know
- On March 16, 2025, unauthorized individuals exploited a vulnerability in NCCTC’s cloud-based file management system, gaining access to personal information stored on their platform. Quick action was taken to secure systems and resolve the issue by March 19, 2025.
- The breach at Northern California Children’s Therapy Center exposed sensitive data including Referring Provider Information, Child Information, Parent and Caregiver Information, and Family and Provider Concerns, putting individuals at risk of identity theft and privacy violations.
- Implications of children's healthcare information being compromised extend beyond typical data breaches, as children are particularly vulnerable to long-term identity theft schemes due to their inability to monitor credit reports independently.
- Healthcare organizations serving pediatric populations must balance accessible care coordination with robust cybersecurity measures to protect sensitive information. Legal rights and options may be available for affected individuals under state and federal privacy laws such as HIPAA.
Read Full Article
9 Likes
Wired
194

Image Credit: Wired
A Hacker May Have Deepfaked Trump’s Chief of Staff in a Phishing Campaign
- German authorities identified the Trickbot ransomware gang leader as Vitaly Nikolayevich Kovalev, a Russian man at large in his home country. CBP collected DNA from 133,000 migrant children for a national criminal database. Wired also reported on a far-right MMA tournament linked to an American neo-Nazi group and offered privacy tips and a guide on protecting oneself from surveillance and hacking.
- The FBI is investigating a phishing campaign that impersonated Susie Wiles, Trump's chief of staff, targeting high-profile individuals with fraudulent messages and calls. This attack may have involved deepfake technology, faking Wiles' voice. Security experts criticise the security awareness and advice using vetted tools to mitigate such risks.
- An Iranian man pleaded guilty in the Baltimore ransomware attack case, revealing his involvement in the Robbinhood ransomware campaign. Russian nuclear blueprints were exposed in a document leak, posing a significant security threat. License plate recognition cameras were used in the search for a woman suspected of having a self-administered abortion, raising privacy concerns.
- Funnull Technology and its CEO were sanctioned by the US Treasury for involvement in investment scams linked to $200 million in reported losses. The company facilitated numerous schemes abusing major cloud services. Wired also covers other tech news and advancements in AI.
Read Full Article
11 Likes
Tech Radar
81

Image Credit: Tech Radar
Billions of stolen cookies are still for sale on the internet - here's how to stay safe
- Research from NordVPN has uncovered the presence of 94 billion stolen cookies on the dark web, with only a small percentage still active.
- Notably, most of these stolen cookies are inactive, but some malware like CryptBot remains effective with 83.4% of its stolen cookies still active.
- The stolen cookies pose a serious risk to users, as they can be exploited to hijack live sessions, take over accounts, bypass security measures, and access sensitive information.
- This highlights the importance of staying vigilant online and taking measures to protect personal information and security.
Read Full Article
4 Likes
Dev
348
Image Credit: Dev
Build Your Unshakeable AWS Cloud Security Career: The Practical Roadmap Employers Crave
- Cloud security skills gap widening, AWS expertise in demand.
- Actionable roadmap provided to build AWS Cloud Security career.
- Key areas covered: Foundational AWS Proficiency, IAM Mastery, Hands-On Experience, Validation & Portfolio Building.
- Emphasis on practical application, certifications, hands-on projects, and networking with industry professionals.
Read Full Article
20 Likes
For uninterrupted reading, download the app