Cyber Security News
Socprime
399
Image Credit: Socprime
AI-Generated Carbon Black Detection Rule for DarkCrystal RAT Campaign
- Uncoder AI processes threat reports like CERT-UA#14045 on DarkCrystal RAT and generates Carbon Black-compatible detection logic.
- Detection logic includes capturing process names, MD5 file hashes, URLs, and destination IPs associated with the DarkCrystal campaign.
- Uncoder AI simplifies the process of writing detection rules for Carbon Black by auto-aggregating threat intelligence and generating production-ready rules.
- The operational value includes accelerated IOC-to-rule pipeline, high-fidelity threat matching, improved C2 discovery, and making threat intel actionable in Carbon Black.
Read Full Article
24 Likes
TechCrunch
254

Image Credit: TechCrunch
Data broker giant LexisNexis says breach exposed personal information of over 364,000 people
- LexisNexis Risk Solutions, a data broker, disclosed a breach affecting over 364,000 people, dating back to December 25, 2024.
- The hacker obtained consumers' sensitive personal data, such as names, dates of birth, phone numbers, addresses, Social Security numbers, and driver's license numbers.
- Data brokers like LexisNexis profit from collecting and selling access to large amounts of Americans' personal and financial data for various purposes.
- The Trump administration recently scrapped a plan that aimed to restrict data brokers from selling Americans' personal information, despite calls by privacy advocates.
Read Full Article
15 Likes
Securityaffairs
322
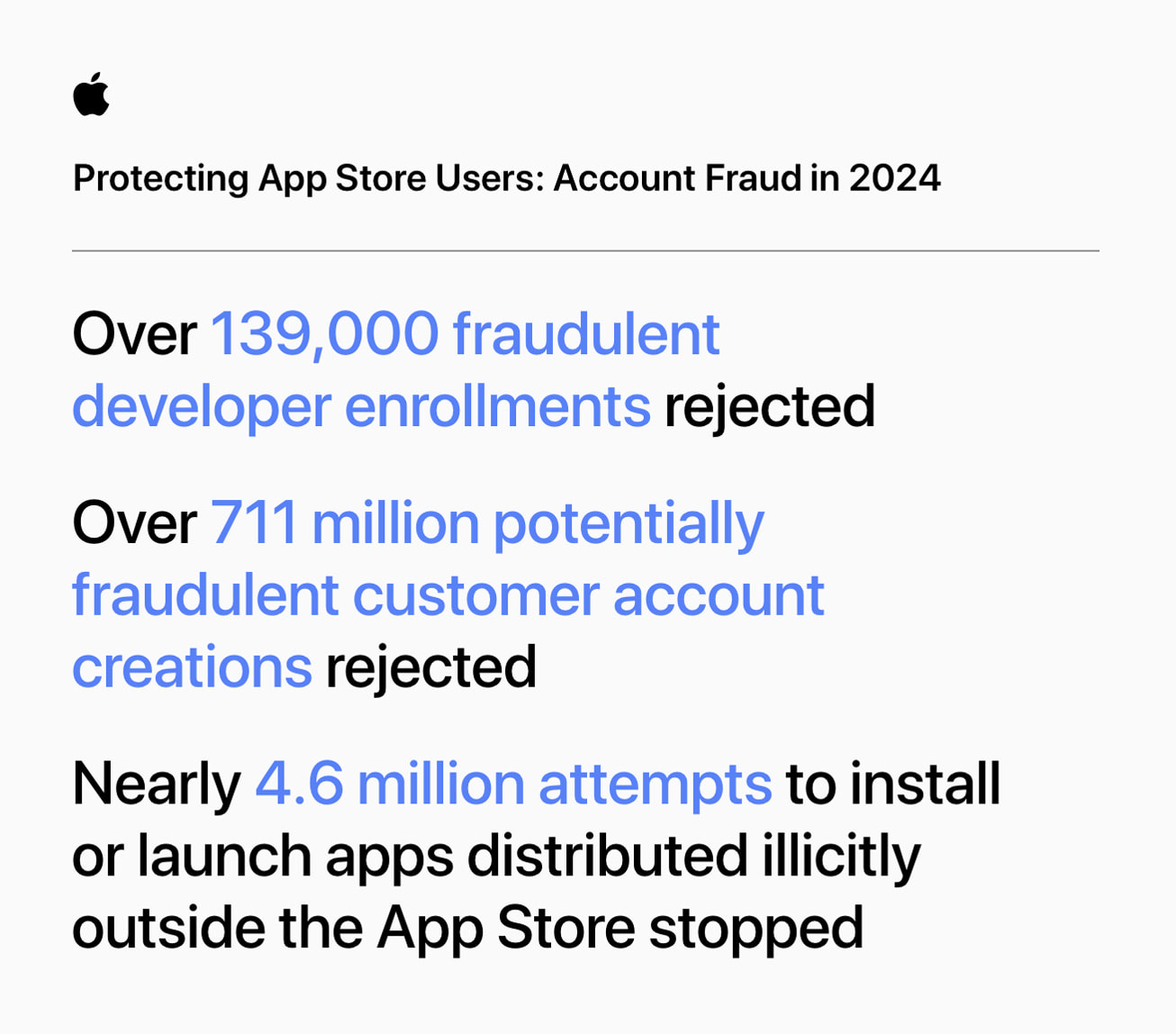
Image Credit: Securityaffairs
App Store Security: Apple stops $2B in fraud in 2024 alone, $9B over 5 years
- Apple has blocked over $9 billion in fraud in the past five years, with $2 billion blocked in 2024 alone, preventing various scams on the App Store.
- The App Store has become a trusted platform with over 813 million weekly visits, focusing on user security and developer success.
- In 2024, Apple took down thousands of fraudulent developer accounts, fake customer accounts, and unauthorized apps, demonstrating its commitment to the users' safety.
- Apple's App Review team reviewed over 7.7 million submissions in 2024, rejecting 1.9 million for violating standards, and maintaining a strong focus on privacy and security.
Read Full Article
19 Likes
Tech Radar
172

Image Credit: Tech Radar
Most of CISA’s senior leaders are leaving the agency
- Many of CISA's senior leaders are reportedly leaving the agency by the end of May 2025, leading to concerns about the agency's future performance.
- The organization is currently undergoing its third workforce reduction this year.
- The sudden exodus in senior leadership includes leaders from five of CISA's six operational divisions and six of its 10 regional offices.
- Employees express anxiety and reservations about the agency's future with the significant departures of senior leadership causing uncertainty.
Read Full Article
10 Likes
Siliconangle
77
Image Credit: Siliconangle
Chainguard enhances container efficiency with new multilayer image upgrade
- Chainguard Inc. has introduced multilayer container images with intelligent rebuilds to enhance container efficiency and accelerate pull times.
- The new multilayer approach divides container images into intelligent layers, allowing for faster downloads and less redundant data transfer during updates.
- Chainguard's engineering team developed a 'per-origin' strategy to split images into layers, resulting in a 70% reduction in unique layer data size and a significant decrease in bytes transferred during pulls of updated images.
- The company claims that the new multilayer images will provide faster pull times, increased bandwidth, and storage efficiency for developers, without altering their workflows.
Read Full Article
4 Likes
Dev
367

Image Credit: Dev
The Trojan Horse Job Offer - How a Hacked LinkedIn Profile & Stolen Project Delivered Malware
- A hacked LinkedIn account led to a job offer for a Web3 role, with malware delivered through a GitHub repo with Node.js backend.
- The malware aimed to scan for sensitive data, steal clipboard content, and install a remote shell backdoor.
- The recruiter claimed their account was hacked later, emphasizing the need to verify all sources.
- The LinkedIn profile appeared legitimate, gradually building trust before sharing the malicious GitHub repository.
- The repository contained a React frontend and a Node.js backend with obfuscated malware in bootstrap.js.
- The malware fetched and executed code from a remote server, with capabilities like file scanning, data theft, and installing backdoors.
- The attackers used stolen concepts to add credibility to the scam, promoting a fake project akin to a real one.
- The experience highlights the importance of isolating unknown code, scrutinizing dynamic code execution, and trusting instincts.
- Developers are advised to use virtual machines, verify sources thoroughly, and have emergency protocols in case of suspected compromise.
- This incident serves as a reminder to stay cautious in the face of sophisticated malware attempts leveraging seemingly trustworthy platforms.
Read Full Article
22 Likes
Siliconangle
127

Image Credit: Siliconangle
Delinea report finds 69% of firms hit by ransomware last year
- 69% of organizations faced ransomware breaches last year with recovery time stretching to two weeks, according to a report by Delinea Inc.
- U.S. breach rates climbed from 53% in 2023 to 71% in 2024, with over a quarter of firms targeted multiple times by ransomware.
- Fewer U.S. firms paid ransoms in 2024 (57%) compared to 2023 (76%), but payment does not guarantee success in retrieving all data.
- Only 18% of victims fully restored operations within 24 hours, while three-quarters took up to two weeks to recover fully, indicating the operational disruptions post-ransomware attacks.
Read Full Article
7 Likes
Siliconangle
213

Image Credit: Siliconangle
Oasis Security warns of excessive OneDrive File Picker permissions exposing entire drives
- A report by Oasis Security Ltd. highlights critical security issues in Microsoft's OneDrive File Picker, exposing users' entire content to third-party web apps.
- The flaws stem from excessive permissions granted through OAuth protocols, allowing access to all OneDrive content instead of specific files.
- The lack of fine-grained scopes in the OneDrive File Picker creates a risk of unauthorized access to sensitive content, affecting hundreds of apps and potentially millions of users.
- Security experts recommend enforcing admin consent policies, reviewing app registrations for high-risk scopes, and using token protection measures to mitigate the security risks associated with overpermissioning in OneDrive File Picker.
Read Full Article
12 Likes
Siliconangle
54

Image Credit: Siliconangle
Cisco introduces Duo Identity and Access Management to enhance identity protection in the AI era
- Cisco introduces Duo Identity and Access Management as a new security solution to combat identity-based attacks in the artificial intelligence era.
- Duo IAM offers a security-first approach with multifactor authentication and a new user directory to manage user identities and access to resources securely.
- The solution integrates with existing third-party identity systems, introduces advanced phishing protection features like Complete Passwordless authentication, and enhances security with Proximity Verification.
- Duo IAM also integrates with Cisco Identity Intelligence to monitor identity risks in real time, automate response actions, and neutralize emerging threats swiftly.
Read Full Article
3 Likes
Medium
176

Image Credit: Medium
AI-Enhanced Phishing Emails: The New Frontier in Cybersecurity Threats
- Phishing emails are evolving with the use of AI, making them highly convincing and personalized.
- AI-generated spear-phishing emails have a success rate of 54%, surpassing generic phishing campaigns.
- AI-powered phishing simulations demonstrate how cybercriminals can automate interactions and create context-aware responses, lowering the barrier for attacks.
- Awareness and vigilance are critical to combatting AI-driven phishing threats in cybersecurity.
Read Full Article
10 Likes
TechBullion
22

Image Credit: TechBullion
The Cost of a Click: Understanding the True Impact of Phishing and How to Spot It
- Phishing is a common threat that can have serious consequences, impacting not just individuals but entire companies.
- Phishing relies on human manipulation, tricking individuals through various tactics like trust, curiosity, and urgency.
- Advancements in Artificial Intelligence have made phishing attacks more sophisticated, requiring individuals to be extra vigilant.
- Getting educated and certified in cybersecurity, like with CompTIA Security+, can empower individuals to protect themselves and contribute to the global fight against cyber threats.
Read Full Article
1 Like
Siliconangle
27

Image Credit: Siliconangle
Snyk launches AI Trust Platform to address security in AI-driven software development
- Snyk launches AI Trust Platform to address security in AI-driven software development.
- The Snyk AI Trust Platform aims to secure and govern software development in the AI era, empowering organizations to accelerate AI-driven innovation while mitigating business risks.
- The platform introduces features like Snyk Assist, an AI-powered chat interface for guidance, Snyk Agent for automating fixes, Snyk Guard for real-time governance, and the Snyk AI Readiness Framework.
- Additionally, Snyk Labs focuses on AI Security Posture Management, while Snyk Studio enables tech partners to build secure AI-native applications, highlighting the Model Context Protocol server for secure AI model integrations.
Read Full Article
1 Like
TechBullion
108

Image Credit: TechBullion
Digital Privacy Laws Every Fintech CEO Must Know
- By 2025, the average cost of a data breach is projected to rise to $5.00 million, with 95% of breaches motivated by financial gain.
- New privacy laws are emerging rapidly, with eight state privacy laws to take effect in 2025, each with unique requirements and penalties.
- Compliance is crucial for fintech CEOs not only to avoid fines but to build trust, gain a competitive edge, and protect the bottom line.
- GDPR compliance is essential even for fintech companies outside Europe if they cater to EU consumers; explicit consent and data handling norms are key.
- In the U.S., state laws like CCPA and new regulations from states such as New Jersey pose compliance challenges for fintech companies operating across state lines.
- Fintech companies need to navigate federal regulations like the Gramm-Leach-Bliley Act (GLBA) in addition to state laws, increasing the complexity of compliance.
- Asia's fintech markets are growing, and privacy regulations like India's Digital Personal Data Protection Act (DPDPA) and Korea's data rules impact the industry.
- Data breach costs are high globally, with the banking sector facing average losses of $10.93 million per breach; smaller fintech firms are not immune to financial impacts.
- Privacy concerns can harm customer trust, delay product launches, disrupt operations, and lead to legal challenges including lawsuits and regulatory penalties.
- Fintech CEOs can enhance compliance by adopting Privacy by Design principles, mapping data flows, implementing technical safeguards, using clear consent mechanisms, and leveraging AI for compliance monitoring.
Read Full Article
6 Likes
Tech Radar
22

Image Credit: Tech Radar
Adidas confirms customer data stolen in worrying cyberattack
- Adidas confirms suffering major cyberattack.
- Customer data included in the breach, primarily contact information of customers who contacted the Adidas help desk.
- Latest cyberattack on a retail giant in a series of attacks; customers warned to be vigilant about identity theft and fraud.
- 2025 saw a number of high-profile cyberattacks on retailers, including luxury department store Harrods, Marks and Spencer, Co-op, and fashion brand Dior.
Read Full Article
1 Like
The Register
426

Image Credit: The Register
The cost of compromise: Why password attacks are still winning in 2025
- Passwords continue to be the main digital access mechanism despite advancements in passkeys and biometric authentication, leading to security vulnerabilities.
- Verizon's 2025 Data Breach Investigations Report highlights that 38% of attacks involve credential abuse or phishing due to the prevalence of weak passwords.
- Common password mistakes include using easily guessable passwords like '123456' and 'password', leaving systems vulnerable to attacks.
- Even following password complexity guidelines may not be enough to deter attackers, as seen with the prevalence of stolen passwords meeting standard requirements.
- Attempts to outsmart attackers by introducing innovative password generation ideas, like using three random words, are still susceptible to phishing and database theft.
- Password reuse across multiple accounts poses a significant risk, highlighting the importance of employing password managers to enhance security.
- Specops Password Policy offers continuous password compromise scanning and customization options, enhancing Active Directory users' password management and enforcement.
- Tools like Specops can help organizations prevent password reuse, enforce stronger password policies, and thwart common password vulnerabilities like incremental numbers.
- Customizable password requirements for different user groups, such as finance teams or privileged access users, improve overall security posture and support compliance efforts.
- Enhanced password security measures, including blocking weak passwords and enforcing unique phrases, are crucial for organizations to stay ahead of evolving cyber threats.
Read Full Article
25 Likes
For uninterrupted reading, download the app