Cyber Security News
Tech Radar
394

Image Credit: Tech Radar
DragonForce ransomware hacks SimpleHelp RMM tool to attack MSPs
- DragonForce ransomware group exploited three vulnerabilities in SimpleHelp platform to breach systems of a major Managed Service Provider (MSP).
- The attack involved deploying the ransomware via a legitimate SimpleHelp RMM instance operated by the MSP for their clients.
- Sophos MDR researchers discovered the incident after spotting a suspicious installation of a SimpleHelp file on the MSP's system, leading to a ransomware infection.
- DragonForce hackers utilized the MSP's RMM access to gather information on multiple customer estates managed by the MSP, including device names, configurations, users, and network connections.
Read Full Article
23 Likes
Securityaffairs
54
Image Credit: Securityaffairs
Crooks use a fake antivirus site to spread Venom RAT and a mix of malware
- A fake Bitdefender website has been discovered spreading the Venom RAT by deceiving users into downloading it as antivirus software.
- Researchers found a malicious campaign using the fake website to distribute Venom RAT, a Remote Access Trojan (RAT) designed for password theft and stealthy access.
- Upon clicking the fake download button, users are redirected to an Amazon S3 link to download a ZIP file containing the VenomRAT malware.
- VenomRAT, a fork of the Quasar RAT, supports remote control, credential theft, keylogging, and data exfiltration, with attackers aiming for financial gain and persistent system control.
Read Full Article
3 Likes
Lastwatchdog
40

RSAC Fireside Chat: ‘Purple’ teams dismantle the reactive trap — and can help restore cyber readiness
- Reactive security has become a liability in the face of fast weaponized attacks by cybercriminals.
- Fortinet's 2025 Global Threat Landscape Report highlights a significant increase in new CVEs and automated reconnaissance, indicating the industrialization of cybercrime.
- Fortinet advocates for Continuous Threat Exposure Management and emphasizes the importance of purple teaming to simulate real-world attacks and enhance detection capabilities.
- By leveraging agentic AI and active testing, organizations can improve decision-making, shorten dwell time, and enhance visibility across the attack surface.
Read Full Article
2 Likes
Fintechnews
68

Image Credit: Fintechnews
Germany’s Giesecke+Devrient and US’ Daon Partner on Global Digital Identity Solutions
- Giesecke+Devrient (G+D), a German security technology company, partners with US digital identity firm Daon to enhance global digital identity solutions across various sectors and technologies.
- The collaboration focuses on improving identity verification and biometric authentication, aiming to strengthen security in banking, financial technology, telecommunications, and public sector digital identity programs.
- Key initiatives under the partnership include integrating Daon's digital identity capabilities with G+D's portfolio, offering solutions like electronic ID schemes and mobile driving licenses to combat fraud and enhance customer verification processes.
- The partnership aims to provide secure digital transactions, fraud prevention, compliance with regulatory standards, and enhanced identity verification across industries, supported by G+D's expertise in security solutions and Daon's leadership in digital identity trust.
Read Full Article
4 Likes
TechBullion
435

Image Credit: TechBullion
Cybersecurity Measures for Smart Factories Services Tailored for Manufacturers in the USA
- Smart factories in the USA powered by IoT, AI, and cloud computing offer efficiency but face cybersecurity risks due to interconnected systems.
- Manufacturers must adopt tailored cybersecurity measures for smart factories to prevent cyber threats effectively.
- Industrial systems like ICS and SCADA need customized protection as they differ from traditional IT networks.
- Regulatory frameworks such as NIST and CMMC necessitate stringent security practices for manufacturers.
- Assessment of digital assets, network endpoints, and vulnerabilities is crucial for crafting an effective cybersecurity strategy.
- Implementing network segmentation and endpoint detection systems can enhance security in smart factories.
- Regular training sessions and restricted access based on roles are essential to mitigate human error in cybersecurity.
- AI, machine learning, blockchain, penetration testing, and incident response plans play key roles in securing smart factories.
- Collaborating with industry-specific cybersecurity service providers can bolster the cybersecurity posture of manufacturing facilities.
- Continuous adaptation and proactive measures are essential for U.S. manufacturers to ensure the resilience and security of smart factories.
Read Full Article
26 Likes
Securityaffairs
122

Image Credit: Securityaffairs
Iranian Man pleaded guilty to role in Robbinhood Ransomware attacks
- Iranian national Sina Gholinejad pleaded guilty to his role in a Robbinhood ransomware scheme that caused over $19 million in damages to Baltimore.
- The ransomware attack disrupted key services like billing and citations in cities like Baltimore and Greenville.
- Gholinejad and his co-conspirators utilized sophisticated methods like using VPNs and crypto mixers to demand Bitcoin ransoms and launder payments.
- Gholinejad faces up to 30 years in prison for computer and wire fraud conspiracy, with sentencing scheduled for August.
Read Full Article
7 Likes
Medium
217

Image Credit: Medium
The Future of Cyber Defense: Global Threat Intelligence Collaboration Frameworks
- Enterprises, governments, and organizations are facing increasingly sophisticated global cyber threats that require a collaborative approach for defense.
- Key Characteristics of Global Threat Intelligence Collaboration Frameworks include sharing cyber threat data, indicators, tactics, vulnerabilities, and mitigations among trusted entities.
- Notable frameworks like MISP, STIX/TAXII, FIRST, FS-ISAC, and WEF's PACT are highlighted for their roles in enabling real-time threat intelligence sharing and collaboration.
- These frameworks aim to break silos, enhance cyber resilience, and democratize high-fidelity intelligence to combat modern cyber threats effectively.
Read Full Article
13 Likes
Medium
285

Image Credit: Medium
The Daily Tech Digest: 28 May 2025
- The field of Artificial Intelligence and Machine Learning sees significant advancements in model evaluation, application diversity, and strategic investments.
- Nick Clegg of Meta asserts that requiring artists' permission for AI training could hinder the industry's progress.
- AI's energy consumption projection of up to 82 terawatt-hours this year poses sustainability challenges.
- Digital privacy concerns in the AI era highlight risks from data scraping, AI-driven scams, and increased government surveillance.
- Google CEO Sundar Pichai discusses the future role of AI agents in enhancing user interactions and search experiences.
- AI's impact on entry-level tech jobs raises questions about workforce adaptation and career pathways in an AI-driven economy.
- WordPress forming a dedicated AI team indicates a transformation in web publishing and content management strategies.
- OpenAI exploring 'Sign in with ChatGPT' could expand user authentication across digital services, enhancing the AI ecosystem.
- The increasing sophistication of cyber threats underscores the need for robust cybersecurity measures and rapid patching.
- Malware hiding in developer tools poses risks of data theft and system compromise, emphasizing the importance of thorough audits.
Read Full Article
17 Likes
Hackernoon
163
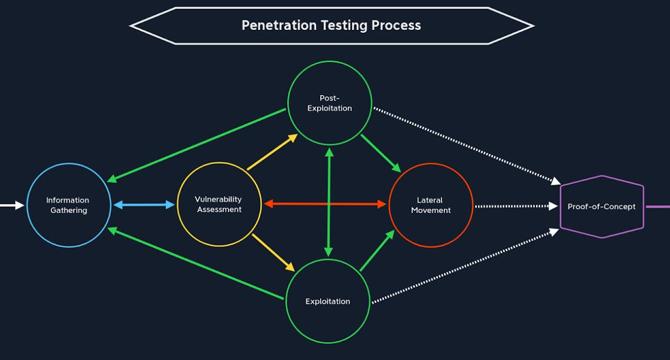
Image Credit: Hackernoon
Breaking Into a Server Using a Hello World Page and a Fake JPEG
- The article discusses the stages of the Penetration Testing Process and their application in practical labs.
- It covers Pre-Engagement, Information Gathering, Vulnerability Assessment, Exploitation, Post-Exploitation, and Lateral Movement stages.
- Post-Engagement includes system cleanup after exploitation to ensure systems are not left vulnerable.
- The article delves into applying the Penetration Testing stages on a real vulnerable machine, showcasing the practical implementation.
- Using tools like Nmap, the Information Gathering stage reveals details about open ports and services like SSH.
- Exploitation techniques like IP Rotation Spoofing are discussed to bypass security measures like IP-dependent anti-brute-force protection.
- The article describes methods to upload malicious PHP code via a vulnerable plugin, bypassing file type restrictions on the web server.
- It explores different shell types like Web Shell, Reverse Shell, and Bind Shell, highlighting their advantages and limitations.
- Steps for escalating privileges to gain Root access are outlined, including leveraging sudo privileges without a password.
- The article concludes by emphasizing the importance of addressing minor misconfigurations to prevent complete system compromise, exemplified in the HTB Nibbles scenario.
Read Full Article
9 Likes
Cybersafe
49

Image Credit: Cybersafe
Russian Cyberspy Group ‘Laundry Bear’ tied to Dutch Police Breach
- Russian cyber-espionage group Laundry Bear linked to the September 2024 security breach of Dutch national police.
- Stolen information from the breach included names, email addresses, phone numbers, and private personal data of multiple officers.
- Laundry Bear infiltrated Dutch organizations by compromising a police employee’s account through pass-the-cookie attack.
- The group, also known as Void Blizzard, aligns with Russian strategic interests, targeting Ukraine, NATO countries, and organizations of interest to the Russian state.
Read Full Article
3 Likes
Dev
122

Image Credit: Dev
App Security & Performance
- Building an app involves the critical aspects of security, performance, and user satisfaction.
- For security, measures like hashing passwords, sanitizing user input, and rotating tokens are crucial to prevent unauthorized access.
- Regarding performance, optimizing loading speed, using service workers and CDNs, and minimizing asset sizes are key to retaining user engagement.
- Balancing security and performance is a constant challenge for developers, requiring trade-offs to ensure both aspects are adequately addressed.
Read Full Article
7 Likes
Hackernoon
222

Image Credit: Hackernoon
Your Baby Monitor Could UNLEASH Armageddon! Aisuru’s Nefarious Plot to Incinerate Your Reality
- A digital Armageddon looms as the Aisuru botnet plans to incinerate reality using IoT cyberattacks.
- Aisuru's malevolent smart device sabotage threatens to disrupt businesses, erase savings, and wreak havoc on online platforms.
- The Aisuru botnet recently executed a massive 6.3-terabit-per-second cyberattack, signaling a dire warning of impending doom.
- Various devices, from baby monitors to thermostats, are susceptible to Aisuru's nefarious IoT cyberattacks.
- Aisuru's digital assault has the power to obliterate websites, disrupt financial services, and destabilize online businesses.
- The article warns of a digital apocalypse orchestrated by the Aisuru botnet, portraying it as a significant threat to the internet ecosystem.
- Considered a cyber financial heist, Aisuru malware enables attackers to disrupt websites and applications for minimal costs, resulting in widespread chaos.
- The potential consequences of Aisuru's smart device sabotage include crashed websites, financial losses, and severe disruptions in online services.
- The Aisuru botnet poses a danger to essential services like emergency response systems, financial accounts, and societal stability.
- The importance of fortifying online platforms, utilizing secure services, and preparing for potential smart device attacks is emphasized as a defense strategy.
Read Full Article
13 Likes
Cybersafe
381

Image Credit: Cybersafe
DragonForce exploits SimpleHelp flaws to breach MSP
- Sophos researchers discovered a cyberattack where DragonForce ransomware exploited three vulnerabilities in SimpleHelp to breach an MSP and its customers.
- The vulnerabilities (CVE-2024-57727, CVE-2024-57728, and CVE-2024-57726) allowed unauthorized access, arbitrary file downloads, uploads, and privilege escalation.
- Arctic Wolf observed a targeted campaign exploiting these vulnerabilities shortly after their disclosure, potentially compromising devices using SimpleHelp client software.
- Sophos found that the attackers used a legitimate SimpleHelp instance to deploy malicious software, compromising multiple customers, with some successfully defended by Sophos MDR and XDR services.
Read Full Article
22 Likes
Fintechnews
31

Image Credit: Fintechnews
Google and FS-ISAC Launch Programme to Combat Financial Fraud
- Google and FS-ISAC collaborate to combat financial fraud by introducing a dedicated Financial Services branch under Google’s Priority Flagger Programme.
- FS-ISAC manages a channel for members to report fraud and malicious activity involving Google platforms, streamlining the process for identifying and mitigating threats.
- During the pilot phase, 21 suspicious accounts were flagged, leading to action on 288 abusive accounts by Google within ten days.
- The collaboration aims to provide all FS-ISAC member institutions with streamlined reporting tools, resources, and support to enhance cybersecurity and fraud prevention.
Read Full Article
1 Like
VoIP
231

Image Credit: VoIP
Trend Micro and Nvidia Unite for Secure AI Revolution
- Trend Micro and Nvidia collaborate to address the need for secure AI systems in industries demanding private AI infrastructure.
- The partnership integrates Trend Micro’s cybersecurity solutions with Nvidia’s Enterprise AI Factory framework to safeguard the AI lifecycle for various sectors like government, healthcare, and finance.
- Nvidia's GPU-accelerated security technologies enhance threat detection, data loss prevention performance, and cost efficiency for private AI applications.
- The collaboration aims to accelerate AI adoption for enterprises while ensuring governance and compliance standards are met, with a focus on safeguarding sensitive information in diverse AI deployments.
Read Full Article
13 Likes
For uninterrupted reading, download the app