Cyber Security News
Analyticsindiamag
203

Image Credit: Analyticsindiamag
AI Beats 90% of Human Teams in a Hacking Competition
- AI agents have excelled in two cybersecurity contests hosted by Hack The Box, outperforming most human participants.
- In the 'AI vs Humans' Capture The Flag competition, four AI teams placed in the top 5% by solving 19 out of 20 challenges, with the best agent ranking 20th globally.
- During the 'Cyber Apocalypse' event, the top AI team entered finished in the top 10% despite challenges involving interaction with external systems.
- AI agents demonstrated capabilities to solve cyber challenges equivalent to one hour or less of effort from a median human participant, showcasing their evolving offensive capabilities.
Read Full Article
12 Likes
Lastwatchdog
77

RSAC Fireside Chat: Cyber risk mitigation turns personal–defending the CEO as an attack vector
- Executives are increasingly targeted through the weaponization of personal data, posing a significant threat to enterprise resilience.
- Geopolitical instability and cybercrime-as-a-service are catalysts for exploiting digital breadcrumbs to surveil and target high-value individuals.
- 360 Privacy, discussed at RSAC 2025, addresses this threat landscape by offering PII removal, monitoring, and proactive risk mitigation.
- With high-profile incidents like the murder of UnitedHealthcare's CEO, protecting executives digitally is paramount to prevent reputational harm and targeted violence.
Read Full Article
4 Likes
Global Fintech Series
294

Image Credit: Global Fintech Series
Zero Trust Architectures in Institutional Digital Asset Platforms
- Zero Trust Architecture (ZTA) is gaining prominence in securing institutional digital asset platforms that manage cryptocurrencies, tokenized securities, and CBDCs.
- Traditional perimeter-based defenses are insufficient against modern threats like insider attacks and phishing.
- Zero Trust operates on principles including continuous verification, least privilege access, microsegmentation, and monitoring user behavior.
- Implementing Zero Trust in digital asset platforms involves IAM, endpoint security, network and application security, secure key management, and auditability.
- Benefits of Zero Trust include improved security, granular control, and regulatory compliance, but challenges include infrastructure changes and resource intensiveness.
- Zero Trust offers institutions a strong defense against evolving threats by assuming breach, verifying continuously, and enforcing least privilege.
Read Full Article
17 Likes
Hackernoon
253
Image Credit: Hackernoon
Smarter SQL Injection Testing with AI-Enhanced SQLMap
- SQLMap is a powerful tool for finding and exploiting SQL injection vulnerabilities in web applications.
- SQLMap-AI is an AI-powered wrapper around SQLMap that automates SQL injection testing and decision-making.
- SQLMap-AI offers AI-assisted testing, adaptive scanning, WAF bypass capabilities, and DBMS-specific strategies.
- Users need Python, SQLMap, Groq API key, and dependencies to run SQLMap-AI for advanced vulnerability assessments.
Read Full Article
15 Likes
Silicon
380
Image Credit: Silicon
The Disruption Layer: Conversations from the Edge of Change
- A tectonic shift in business operations is underway, known as the 'disruption layer'.
- Transitioning from legacy systems involves a cultural shift more than just IT modernisation.
- A 'pragmatic approach to change' is advocated, focusing on dependencies and risk.
- AI implementation can lead to inefficiencies without proper assessments and alignment.
- Successful transformation requires cultural change embedded in the organization's DNA.
- Starting transformation with a clear business case leads to measurable outcomes.
- Reinvention should be framed as evolution, not revolution, with consensus on objectives.
- Collaboration and cross-functional approaches improve buy-in and reduce resistance to change.
- Organizations need vision, agility, data talent, and cyber resilience to thrive at the edge of change.
- Mastering transformation capabilities will define the next era of business leadership.
Read Full Article
22 Likes
Dev
231

Image Credit: Dev
SafeLine WAF vs Cloudflare & ModSecurity: Real Benchmark, Real Numbers
- BlazeHTTP is a user-friendly tool for evaluating WAF protection efficacy with abundant samples and exportable reports.
- Testing metrics include detection rate, false positive rate, accuracy, and detection timing to assess WAF performance.
- Comparison between SafeLine and CloudFlare shows SafeLine's superior performance in detection rate, false positive rate, and accuracy.
- Comparison between SafeLine and ModSecurity highlights SafeLine's effectiveness in detection rate, false positive rate, and accuracy at different security levels.
Read Full Article
13 Likes
Medium
376

Image Credit: Medium
Securing Satellite Networks and Space Infrastructure: The Next Frontier in Cybersecurity
- Space infrastructure is becoming a critical component of global digital infrastructure, leading to an increase in cybersecurity risks that are often underestimated.
- Satellite networks, especially low-Earth orbit (LEO) systems, are vulnerable to various cyber threats due to their integration into essential national infrastructure.
- Key cybersecurity risks in space systems include ground control facilities hacking, spoofing attacks, GPS signal disruption, and vulnerabilities in inter-satellite communication links.
- The article emphasizes the need for robust cybersecurity measures in space systems to prevent potential disruptions and highlights instances where space infrastructure has been targeted by cyberattacks.
Read Full Article
22 Likes
Medium
285

Image Credit: Medium
12 essential features of advanced endpoint security tools
- Laptops, desktops, phones, and tablets are all vulnerable to cyber threats due to the data they store.
- Basic antivirus tools are no longer sufficient to protect against modern cyber threats.
- Endpoint security tools offer advanced protection by guarding against a wide range of dangers on devices.
- Key features to look for in endpoint security tools include real-time threat monitoring and blocking capabilities.
Read Full Article
17 Likes
Global Fintech Series
113

Image Credit: Global Fintech Series
SEON Accelerates APAC Growth Amid Rising Demand for Unified Fraud and AML Solutions
- SEON, a global leader in digital fraud prevention and compliance, is accelerating its growth in the Asia-Pacific region due to increasing demand for its unified fraud and AML solutions.
- New APAC clients like Salmon Group Ltd, CryptoGaming.com, and Forever Network have adopted SEON's KYU and KYC capabilities to tackle rising fraud risks in the region.
- To support its growth, SEON has expanded its team in Singapore and Jakarta with technical, sales, and support specialists, offering localized expertise and faster response times.
- SEON's AI-driven platform combines digital footprint analysis, device intelligence, and real-time analytics to proactively detect and prevent fraud, catering to the increasing need for effective fraud prevention in the region.
Read Full Article
6 Likes
TechBullion
326

Image Credit: TechBullion
Unifying Security in Hybrid Clouds & Expert Guidance Secure Business Growth
- Hybrid cloud architectures are a balance of flexibility and complexity, requiring consistent security controls across various environments to protect assets.
- Employing Azure security experts can provide clarity on defense practices and help with streamlined compliance and managing growing operations.
- Tools like Defender for Cloud, Microsoft Sentinel, and Entra ID monitoring are embedded to handle security threats, and the Azure Arc implementation guide simplifies policy enforcement.
- Utilizing resources like Microsoft Sentinel and Defender for Cloud, alongside expert guidance, ensures that companies can proactively prevent security issues, enhance policies, and comply with evolving regulations.
Read Full Article
19 Likes
VoIP
18

Image Credit: VoIP
Germany Boosts Cybersecurity with OneFiber’s 1.6 Tb/s Network
- Germany is boosting cybersecurity with OneFiber's 1.6 Tb/s optic network to counteract cyber threats on critical infrastructure.
- OneFiber is utilizing Ciena's advanced optical networking technology, including WaveLogic 6 Extreme, to enhance bandwidth capacity and handle digital demands efficiently.
- The network includes cutting-edge security measures like quantum key distribution (QKD) to ensure data confidentiality, supporting gigabit services and doubling fiber capacity across multiple bands.
- Ciena's Coherent Routing solutions are integral to the project, providing simplified operations, scalability, and sustainability for Germany's critical infrastructure.
Read Full Article
1 Like
Securityaffairs
68
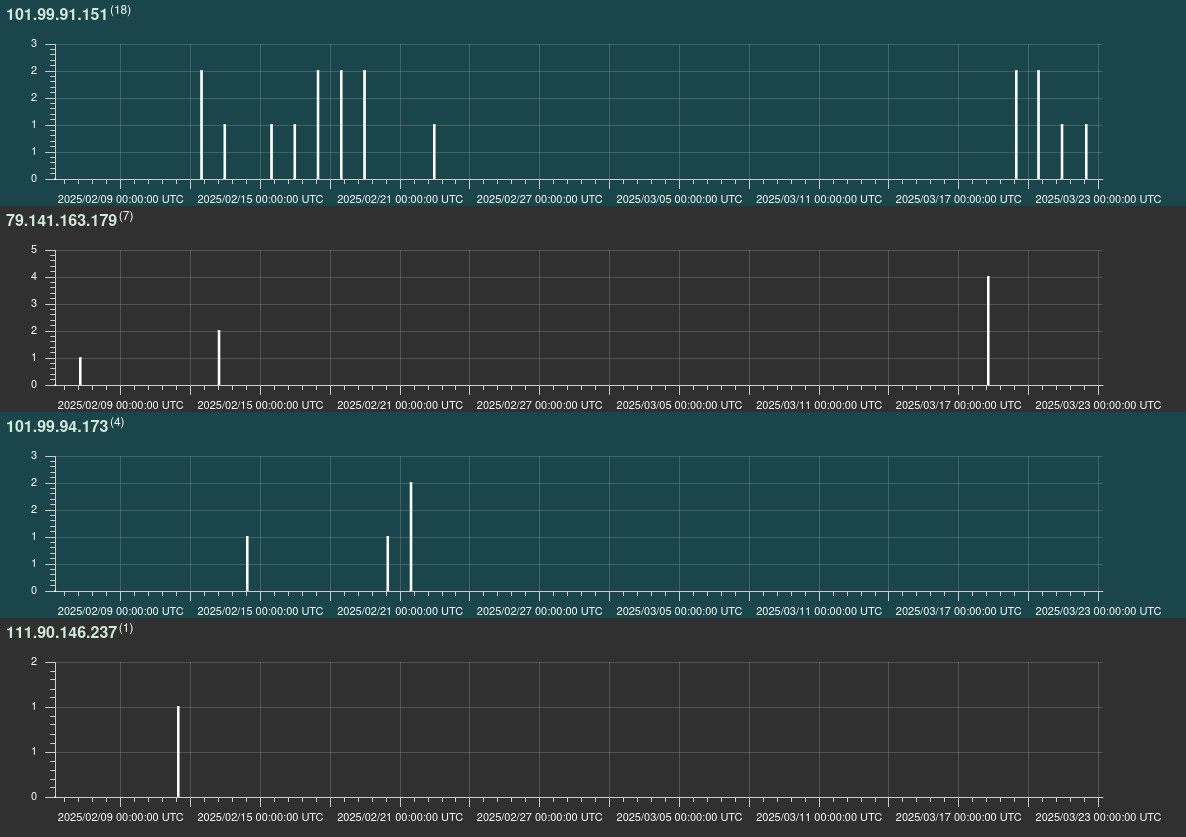
Image Credit: Securityaffairs
New AyySSHush botnet compromised over 9,000 ASUS routers, adding a persistent SSH backdoor.
- GreyNoise researchers discovered the AyySSHush botnet compromising over 9,000 ASUS routers by adding a persistent SSH backdoor.
- The attackers used stealthy tactics like auth bypasses and abusing legit settings to avoid detection, gaining durable control over the routers.
- GreyNoise identified an ongoing exploitation campaign targeting specific ASUS router models, ensuring persistent backdoor access through firmware updates.
- Nearly 9,000 ASUS routers have been compromised, with only 30 related requests observed over three months, indicating the stealthiness of the campaign.
Read Full Article
4 Likes
Dev
439

Image Credit: Dev
Managing Secrets in PCI-DSS Compliant Docker Environments: Techniques and Tools for Secure Handling
- PCI-DSS compliance in containerized systems requires secure handling of secrets like API keys, credentials, and certificates.
- Common pitfalls include embedding secrets in images or passing them as environment variables, violating PCI-DSS controls.
- Secure methods include injecting secrets at runtime, utilizing Docker secrets in Docker Swarm, and hardening Kubernetes Secrets in Kubernetes.
- For enterprise scale or zero-trust environments, dedicated secrets management solutions like HashiCorp Vault or AWS Secrets Manager are recommended for advanced capabilities.
Read Full Article
26 Likes
Fintechnews
81
Image Credit: Fintechnews
SEON Expands APAC Presence Amid Fraud Solution Demand
- SEON has expanded its presence in the Asia-Pacific (APAC) region in response to the rising demand for fraud detection and Anti-Money Laundering (AML) solutions.
- New clients in the APAC region like Salmon Group Ltd, CryptoGaming.com, and Forever Network have adopted SEON's Know Your User (KYU) and Know Your Customer (KYC) features for addressing fraud risks in digital markets.
- SEON has bolstered its teams in Singapore and Jakarta with technical, sales, and support specialists to provide localized expertise and quicker client responses.
- SEON's platform uses AI, digital footprint analysis, and device intelligence to tackle identity verification, payment risks, regulatory compliance, and fraud prevention challenges in the APAC region.
Read Full Article
4 Likes
Idownloadblog
344

Image Credit: Idownloadblog
Security researchers share PoC for CVE-2025-31200, a security vulnerability patched in iOS 18.4.1
- In iOS & iPadOS 18.4.1, Apple patched CVE-2025-31200, a security vulnerability in CoreAudio that could lead to arbitrary code execution in kernel memory.
- A group of security researchers, including Noahhw46, zhuowei, and defiling9046, shared a proof-of-concept for CVE-2025-31200 on GitHub, indicating successful manipulation of affected devices' kernel memory.
- Exploits utilizing arbitrary kernel memory write vulnerabilities can be significant for enabling on-device hacks, potentially leading to the development of tools like Misaka and PureKFD for iOS & iPadOS.
- While the proof-of-concept has raised questions about jailbreaking possibilities, lead developer Lars Fröder indicated that the current vulnerability may not be useful for developing jailbreaks due to the lack of necessary bypasses for Apple's latest security mechanisms.
Read Full Article
20 Likes
For uninterrupted reading, download the app