Cyber Security News
TechCrunch
231

Image Credit: TechCrunch
A decade in, bootstrapped Thinkst Canary reaches $20M in ARR without VC funding
- Cybersecurity company Thinkst is celebrating its 10th anniversary of launching Canary, their flagship product designed to catch hackers in action.
- With a focus on customer needs over rapid growth, Thinkst has reached $20 million in annual recurring revenue without any external funding.
- Founder Haroon Meer attributes their success to fulfilling promises, resulting in a 60% retention rate of their first-year customers.
- Canary, launched in 2015, acts as an early warning system on networks, alerting companies when hackers breach their systems.
- Canary Tokens, another offering, helps users detect unauthorized access by placing bait in secure locations for monitoring.
- Thinkst's canaries are hard to deploy incorrectly, as they effectively catch attackers whether they blend in or stand out.
- The company relies on word of mouth and organic sales growth, with customers confirming the effectiveness of their products.
- Despite not seeking venture capital, Thinkst believes in running a business that remains attractive for investment or acquisition.
- Founder Haroon Meer envisions every company having multiple canaries, emphasizing the quality and value of their product over immediate revenue growth.
- With a current revenue of $20 million, Thinkst sees further growth potential and emphasizes providing a good product at a fair price.
Read Full Article
13 Likes
Tech Radar
181

Image Credit: Tech Radar
A key Microsoft OneDrive feature has a worrying security flaw which could expose user data
- A security flaw has been found in Microsoft's OneDrive File Picker by researchers, allowing threat actors potential access to cloud archives.
- The flaw is due to excessive permissions requested by File Picker, including read access to the entire drive, caused by the lack of fine-grained OAuth permissions.
- The Oasis Research Team highlighted the consequence of this flaw, potentially leading to customer data leakage and non-compliance with regulations.
- Microsoft has acknowledged the issue regarding the security flaw but has not issued a fix yet.
Read Full Article
10 Likes
Tech Radar
244
Image Credit: Tech Radar
Thousands of Asus routers hacked to create a major botnet planting damaging malware
- Thousands of ASUS routers have been hacked to create a major botnet by threat actors exploiting security vulnerabilities.
- The hackers gained initial access by exploiting poorly secured routers using brute force and authentication bypass methods.
- They abused a known command injection flaw (CVE-2023-39780) to establish persistent access and create a botnet.
- The attackers can maintain long-term access without dropping malware traces, with the number of compromised devices steadily increasing.
Read Full Article
14 Likes
Silicon
240
Image Credit: Silicon
The Disruption Layer: Conversations from the Edge of Change: Head-to-Head
- The key challenge of digital transformation involves aligning strategy, systems, and people at the edge of change, rather than focusing solely on technology.
- Moving from legacy systems to agile, digital ecosystems faces barriers such as poor framing for business models and legacy mindsets.
- Assessing legacy infrastructure for modernization involves evaluating alignment with the business's ambition and vision for transformation.
- AI tools have accelerated reinvention efforts in assisting system changes, implementation guidance, and shaping customer experiences.
- Digital reinvention should not just be a technology upgrade but also a cultural and strategic shift within the business.
- Insurers may need to undergo numerous micro-pivots in their transformation journey to become more adaptive and responsive.
- Success in digital transformation can be measured through operational changes such as customer sentiment, Net Promoter Scores, and product adaptability.
- Adaptivity is crucial for insurers to thrive amid continuous technological disruptions and changing customer expectations.
- Innovation acceleration and adaptability to changing competitive landscapes will define organizations that thrive amid ongoing technological disruptions.
- Insurers need to shift to customer-centric models, adapt rapidly to evolving risks and demographics, and create new propositions to meet modern needs.
Read Full Article
14 Likes
Tech Radar
54

Image Credit: Tech Radar
Victoria’s Secret laid bare after security incident takes down systems
- Victoria's Secret confirmed a cyberattack, leading to the shutdown of its websites and some in-store services.
- No one has claimed responsibility yet for the security incident, and details about the attack remain scarce.
- Victoria's Secret triggered incident response protocols and engaged third-party experts to investigate and restore operations securely.
- With the company's systems offline for at least three days, speculation suggests ransomware as a possible cause, but no confirmation has been made.
Read Full Article
3 Likes
Entrepreneurshiplife
226

Image Credit: Entrepreneurshiplife
Why Cybersecurity Should Be a Top Priority for Every Business and Public Infrastructure
- In today’s interconnected world, digital systems' reliance has increased significantly across all sectors, making cybersecurity vital to prevent attacks.
- Cyberattacks pose a serious threat to essential services and sensitive data, impacting financial and operational stability.
- Critical systems such as power grids and transportation networks require strong cybersecurity measures to prevent disruptions and maintain services.
- Modern systems are vulnerable to cyber threats due to complexities, outdated security measures, and integration of new technologies.
- Cyberattacks have far-reaching economic consequences, leading to financial losses, legal liabilities, and disruptions in various industries.
- Public safety is closely linked to the integrity of critical infrastructure, emphasizing the importance of cybersecurity in ensuring day-to-day operations and citizen well-being.
- Governments worldwide have implemented regulations to enforce cybersecurity practices and hold organizations accountable for data protection.
- AI and automation play a growing role in enhancing cybersecurity by enabling real-time threat detection, response, and continuous network monitoring.
- Organizations need to understand vulnerabilities, comply with regulations, invest in advanced security solutions, and promote a security-conscious culture to mitigate cyber risks effectively.
- Investing in robust cybersecurity strategies is crucial to protecting critical infrastructure, ensuring operational stability, and mitigating the escalating cyber threats of today.
Read Full Article
13 Likes
Dev
185

Image Credit: Dev
Cybersecurity Tips for Users
- Using weak and common passwords makes you an easy target for hackers. Use a password manager and create unique, complex passwords for better security.
- Enable Two-Factor Authentication (2FA) on all your accounts to add an extra layer of security and prevent unauthorized access.
- Be cautious of clicking on suspicious links, as they could lead to phishing scams and compromise your data. Always verify the sender before clicking.
- Avoid using public Wi-Fi without a VPN to protect your sensitive information from potential hackers who may exploit vulnerabilities in public networks.
Read Full Article
11 Likes
TechDigest
206

Image Credit: TechDigest
Victoria’s Secret shuts down US website following ‘security incident’
- Victoria’s Secret has suspended most of its US website and in-store services due to a security incident, with its UK website unaffected.
- The company is working to fully restore operations and has engaged third-party experts to address the situation.
- The incident impacted the company's stock, with shares closing down by approximately 7% on Wednesday.
- This incident adds to a recent spree of cyberattacks targeting retailers, with companies like Marks & Spencer and the Co-op also facing disruptions.
Read Full Article
12 Likes
TechDigest
86

Image Credit: TechDigest
UK consumers at ‘serious risk of fraud’ following leak of 800 million cookies
- Nearly 800 million internet cookies of UK consumers leaked online, posing a significant fraud risk.
- Global cookie leaks surge from 54 billion to 94 billion, with UK ranking 27th out of 253 countries.
- Cookies can contain sensitive personal data and when stolen, can be used by cybercriminals to impersonate users and gain unauthorized access to accounts.
- NordVPN report highlights Google searches as most significant source of cookie leaks, emphasizing the importance of consumer vigilance and cybersecurity measures.
Read Full Article
5 Likes
Securityaffairs
303
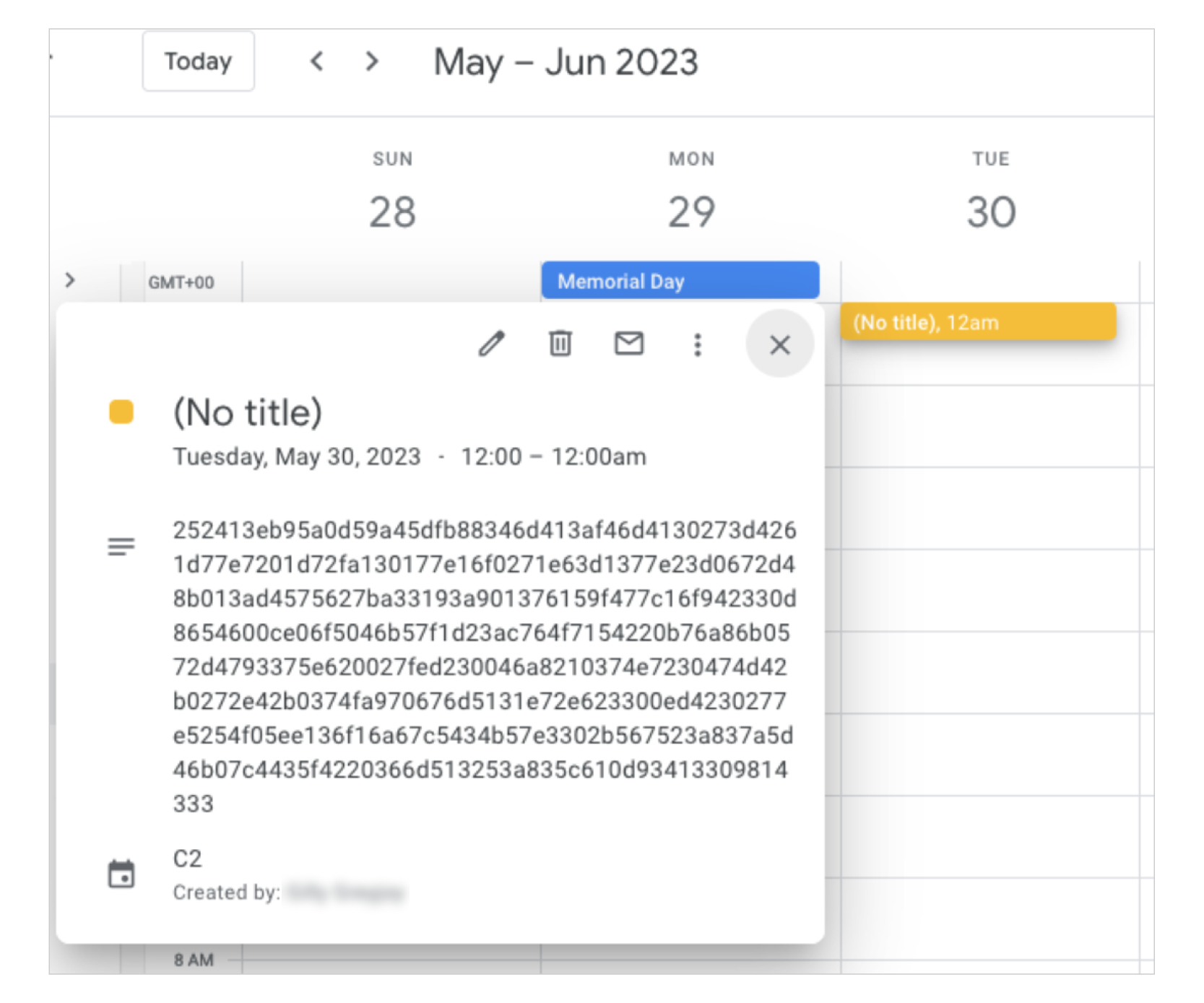
Image Credit: Securityaffairs
China-linked APT41 used Google Calendar as C2 to control its TOUGHPROGRESS malware
- China-linked group APT41 used Google Calendar as a command-and-control (C2) channel to control its TOUGHPROGRESS malware, targeting government entities through a compromised website.
- APT41 used spear phishing emails with a ZIP file hosted on a hacked government site to distribute the TOUGHPROGRESS malware, which operates in three stealthy stages with advanced evasion tactics.
- TOUGHPROGRESS decrypts and runs stages in memory, uses process hollowing for injection, and communicates with operators through Google Calendar to exfiltrate data and receive commands.
- Google has developed custom fingerprints to disrupt APT41 and TOUGHPROGRESS malware, terminated attacker-controlled projects, updated file detections, and shared threat intel with affected organizations.
Read Full Article
18 Likes
Tech Radar
194

Image Credit: Tech Radar
How to run an antivirus scan on your computer
- Running a virus scan involves opening an antivirus program, clicking the 'Scan' button, and addressing flagged items.
- Choosing the right antivirus software with features like real-time protection and automatic updates is crucial.
- Keeping antivirus software updated is essential to protect against evolving malware threats.
- Different types of scans, such as quick, full, custom, and boot-time scans, cater to various needs.
- During scans, avoid using heavy applications, keep devices charged, and address any detected PUPs.
- After analyzing scan results, take action by quarantining or deleting threats, and consider restarting the device.
- Implement post-scan security measures like patching vulnerabilities, changing passwords, and maintaining backups.
- Regular virus scans, combined with human vigilance in online activities, are crucial for maintaining device security.
- Antivirus software should be configured correctly, with automated scans and real-time protection enabled for optimal security.
- Users are advised to avoid unknown links, download from legitimate sources, use strong passwords, and keep software up to date.
Read Full Article
11 Likes
Wired
403

Image Credit: Wired
The US Is Storing Migrant Children’s DNA in a Criminal Database
- The US government has collected DNA samples from over 133,000 migrant children and teenagers, including a 4-year-old, and uploaded them into a criminal database for law enforcement purposes.
- The DNA collection program by CBP reaches deeply into the lives of migrant children, storing their genetic data in a system originally designed for convicted sex offenders and violent criminals.
- Experts express concerns that the children's genetic material will be stored indefinitely and that the DNA dragnet could lead to extensive profiling without proper safeguards.
- The records show CBP swabbed the cheeks of between 829,000 and 2.8 million individuals, estimating over 1.5 million unique swabs, including around 133,539 children and teenagers.
- This vast expansion of biometric surveillance specifically targets migrant populations, including children.
- The DNA samples are registered in the FBI-administered Combined DNA Index System (CODIS) used to match DNA collected from crime scenes or convictions to identify suspects.
- Despite DHS policy exempting minors under 14 from DNA collection, as many as 227 children aged 13 or younger had their DNA collected by CBP, with the youngest being a 4-year-old.
- Privacy advocates and experts raise concerns about the ethics and implications of collecting and storing genetic information of migrants, particularly children, in a criminal database.
- The mass DNA collection effort at the border has raised questions about the government treating all border crossers, regardless of age or legal status, as potential suspects in future crimes.
- While CODIS data is meant for identification in criminal cases, concerns persist about potential privacy violations, discrimination, and misuse of genetic information in the future.
Read Full Article
24 Likes
Analyticsindiamag
203

Image Credit: Analyticsindiamag
AI Beats 90% of Human Teams in a Hacking Competition
- AI agents have excelled in two cybersecurity contests hosted by Hack The Box, outperforming most human participants.
- In the 'AI vs Humans' Capture The Flag competition, four AI teams placed in the top 5% by solving 19 out of 20 challenges, with the best agent ranking 20th globally.
- During the 'Cyber Apocalypse' event, the top AI team entered finished in the top 10% despite challenges involving interaction with external systems.
- AI agents demonstrated capabilities to solve cyber challenges equivalent to one hour or less of effort from a median human participant, showcasing their evolving offensive capabilities.
Read Full Article
12 Likes
Lastwatchdog
77

RSAC Fireside Chat: Cyber risk mitigation turns personal–defending the CEO as an attack vector
- Executives are increasingly targeted through the weaponization of personal data, posing a significant threat to enterprise resilience.
- Geopolitical instability and cybercrime-as-a-service are catalysts for exploiting digital breadcrumbs to surveil and target high-value individuals.
- 360 Privacy, discussed at RSAC 2025, addresses this threat landscape by offering PII removal, monitoring, and proactive risk mitigation.
- With high-profile incidents like the murder of UnitedHealthcare's CEO, protecting executives digitally is paramount to prevent reputational harm and targeted violence.
Read Full Article
4 Likes
Global Fintech Series
294

Image Credit: Global Fintech Series
Zero Trust Architectures in Institutional Digital Asset Platforms
- Zero Trust Architecture (ZTA) is gaining prominence in securing institutional digital asset platforms that manage cryptocurrencies, tokenized securities, and CBDCs.
- Traditional perimeter-based defenses are insufficient against modern threats like insider attacks and phishing.
- Zero Trust operates on principles including continuous verification, least privilege access, microsegmentation, and monitoring user behavior.
- Implementing Zero Trust in digital asset platforms involves IAM, endpoint security, network and application security, secure key management, and auditability.
- Benefits of Zero Trust include improved security, granular control, and regulatory compliance, but challenges include infrastructure changes and resource intensiveness.
- Zero Trust offers institutions a strong defense against evolving threats by assuming breach, verifying continuously, and enforcing least privilege.
Read Full Article
17 Likes
For uninterrupted reading, download the app