Cyber Security News
Securityaffairs
381
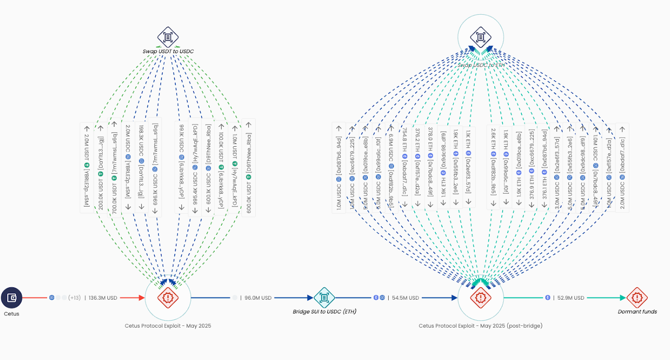
Image Credit: Securityaffairs
Crooks stole over $200 million from crypto exchange Cetus Protocol
- Cetus Protocol suffered a $223 million crypto theft and is willing to drop legal action if the stolen funds are returned.
- The platform was paused as the investigation confirmed the cyber heist last week.
- $162 million of the compromised funds have been successfully paused, and recovery efforts are underway with the Sui Foundation.
- The hack was due to a vulnerable package but has since been fixed, with the company offering a $5 million bounty for tips to identify the attacker.
Read Full Article
22 Likes
Dev
113

Image Credit: Dev
What Is a WAF? A Beginner’s Guide to Web App Firewalls
- A WAF, or Web Application Firewall, acts as a security filter between users and web applications, blocking malicious requests in real time before reaching the backend.
- A typical WAF can block common web attacks, detect bots, rate-limit requests, log suspicious traffic, and apply custom rules to safeguard APIs.
- WAFs work as reverse proxies, inspecting every request and response to match against security rules, including signature-based detection and heuristic analysis.
- It is crucial to use a WAF, especially for publicly accessible apps, as an additional layer of protection against exploits, despite following security guidelines and writing secure code.
Read Full Article
6 Likes
Medium
340

Image Credit: Medium
About Google is a leading
- Networking faced challenges in ensuring data security despite robust security measures.
- To address these challenges, Networking enhanced authentication and privacy measures with Google's security experts.
- They implemented advanced protocols like multi-factor authentication and zero-trust security models.
- By integrating Google's enterprise-level security solutions, Networking significantly improved its security posture.
Read Full Article
20 Likes
Dev
68

Image Credit: Dev
Data Security & Authorization: The Dual Pillars of a Robust Database System
- Data Security and Authorization are crucial components of a robust Database Management System (DBMS).
- Authentication verifies the identity of users accessing the database through methods like usernames and passwords, biometric scanners, or token-based systems.
- Authorization specifies the actions an authenticated user can perform within the database based on their role and responsibilities.
- By combining authentication and authorization, a comprehensive security framework is established to protect data integrity, confidentiality, and availability in a database system.
Read Full Article
4 Likes
Dev
386

Image Credit: Dev
Exploring customLogger: Smart, Customizable Logging in Payload CMS
- Payload CMS is a developer-centric, customizable, and API-driven content management system based on Node.js and TypeScript.
- Key features of Payload include TypeScript-first structure, modern admin interface, built-in security, and hooks/plugins support.
- The payload-auditor plugin in Payload CMS offers precise audit capabilities for all operations on collections, ensuring transparency and reliability in logging.
- Custom logging is crucial for tracking user activities and data changes in CMS, providing customization, transparency, security, and analytics benefits.
- The customLogger feature in the payload-auditor plugin allows developers to customize logging behavior at different levels, enhancing logging flexibility and precision.
- CustomLogger supports multi-level customization, including operation-level, hook-level, global hooks level, and global level, with defined execution priority.
- The customLogger function structure includes inputs like hook arguments and log fields and requires returning a specific output, allowing for detailed logging customization.
- Best practices for utilizing customLogger include keeping log structure simple, avoiding storing sensitive data, and using async operations for external data processing.
- Utilizing customLogger in Payload CMS projects enhances logging accuracy, enables specific change tracking, and helps in faster debugging and security monitoring.
- CustomLogger in payload-auditor can be instrumental in building a reliable logging infrastructure, enhancing audit capabilities, and serving as a critical component in security strategies.
Read Full Article
23 Likes
Dev
204

Image Credit: Dev
Office 365 E5 for Enterprises: The All-in-One Platform for Secure Communication, Analytics, and Compliance
- Microsoft Office 365 E5 is a comprehensive and secure solution that offers advanced productivity, security, and compliance tools for enterprises.
- It includes advanced office applications, Microsoft Teams integration with Phone System, advanced security features, compliance tools, and Power BI Pro integration.
- Key benefits of Office 365 E5 include enhanced productivity, end-to-end security, improved compliance, business intelligence at scale, and lower IT overhead.
- Target users for Office 365 E5 are enterprises with advanced security needs, highly regulated organizations, businesses requiring enterprise voice solutions, and data-driven organizations.
Read Full Article
12 Likes
Medium
131

File inclusion vulnerabilities in common programming languages with examples
- Attacker's goal is to alter a variable in functions like include or require to inject malicious code from a remote source.
- To prevent File Inclusion vulnerabilities in PHP, validate all user input before using it in the application.
- Using a whitelist of accepted parameters or predefined switch/case statements is recommended to prevent such vulnerabilities.
- JavaServer Pages (JPS) can include files for execution at runtime, which can lead to remote code execution on a vulnerable server.
Read Full Article
7 Likes
Medium
195

The Threat You Can’t Scan For: Why I Built Veriduct
- The article discusses the development of a data protection system called Veriduct, created in response to the increasing threat of ransomware and data breaches.
- Veriduct focuses on storing instructions for rebuilding files, instead of the files themselves, using a method called semantic annihilation to destroy file structures without deleting the files.
- The project was driven by the need for more efficient and secure backups, aiming to separate data from meaning to enhance privacy and data protection.
- Veriduct operates by stripping file structures and splitting data into chunks stored in a database, requiring a keymap for reconstruction, effectively making the data unrecognizable without the key.
- The system, open-source and built on semantic annihilation, challenges traditional encryption methods, ensuring data protection by rendering files uninterpretable without the key.
- Veriduct's approach involves stripping file headers and metadata, storing decontextualized data chunks, and using a keymap for reassembly, providing a new layer of defense against data breaches and surveillance.
- The article highlights the struggle to get recognition for Veriduct, despite reaching out to privacy experts and security firms for collaboration and validation.
- Veriduct aims to disrupt the current data protection paradigm by emphasizing semantic destruction as the primary defense mechanism, going beyond traditional encryption methods.
- The system has implications beyond anti-ransomware measures, including enabling secure messaging systems like KlyptM, which prioritizes user-defined privacy and data protection.
- Veriduct challenges the existing digital security landscape by offering a novel approach to safeguarding data privacy and ensuring data remains incomprehensible without the keymap.
- The article emphasizes the importance of exploring alternative data protection models like Veriduct to address evolving threats and the limitations of conventional encryption methods.
Read Full Article
11 Likes
Medium
299
Image Credit: Medium
Doctrine in the Shadows: How Cyber Adversaries Are Rewriting the Rules of War
- The article discusses how cyber adversaries are reshaping the rules of war by targeting digital infrastructure, leading to potential network disruptions and paralysis.
- Cyber weapons operate stealthily, and attacks on critical systems can result in cascading outages, blurring the line between reconnaissance and sabotage.
- The scenario presented in the article highlights a digital crisis unfolding without warning sirens, causing chaos in power grids, finance, healthcare, and transportation systems.
- Federal agencies struggle to coordinate responses without a unified cyber defense strategy, showcasing the need for rapid adaptation in the face of evolving threats.
- The doctrine of strategic shaping by adversaries like China and Russia focuses on weakening America's digital infrastructure through cyber operations rather than traditional military means.
- The article emphasizes the need to transition from deterrence by dominance to resilience by design to effectively counter evolving cyber threats.
- The concept of a Digital Iron Dome is proposed as a solution, involving advanced technologies and collective defense strategies to protect critical digital assets and infrastructure.
- The article also discusses the convergence of cyber and outer space domains, highlighting the vulnerability of satellite systems to digital attacks.
- Deterrence in cyber warfare is seen as challenging due to the ambiguity of attributions, emphasizing the importance of resilience and collective deterrence strategies.
- The need for democratizing defense efforts, incorporating all sectors into national defense fabric, and fostering a cultural shift towards proactive cybersecurity measures is underscored.
Read Full Article
18 Likes
Tech Radar
95

Image Credit: Tech Radar
This dangerous new phishing scam spoofs a top Google program to try and hack Facebook accounts
- A new phishing campaign is exploiting Google AppSheets' workflow automation to send emails spoofing Facebook and harvesting login credentials.
- The attackers are able to bypass email protection mechanisms and send phishing emails directly to inboxes using a legitimate Google service.
- The phishing emails impersonate Facebook and attempt to trick individuals into providing login credentials and 2FA codes through a fake appeal process.
- The attackers use unique email IDs and a landing page hosted on Vercel to deceive victims and obtain session tokens for persistent access even after password changes.
Read Full Article
5 Likes
Medium
218

Image Credit: Medium
How to Safely Meet People From Online In Person
- Meeting people from online in person can be dangerous, thus it is crucial to take safety precautions.
- Never disclose personal information such as address, workplace/school, phone number, passwords, or financial details to strangers online.
- Before meeting someone, research their online presence, avoid private or unfamiliar meeting locations, and inform a trusted person or bring a friend along.
- During the meeting, ensure safety by meeting in public places, staying sober and aware, securing your drink, and knowing emergency exits for a quick escape if necessary.
Read Full Article
13 Likes
Securityaffairs
231
Image Credit: Securityaffairs
Marlboro-Chesterfield Pathology data breach impacted 235,911 individuals
- SafePay ransomware attacked Marlboro-Chesterfield Pathology, compromising personal data of 235,000 individuals.
- The breach occurred on January 16, 2025, leading to the unauthorized access of internal systems.
- Stolen information included names, addresses, birth dates, medical treatment details, and health insurance data.
- Marlboro-Chesterfield Pathology notified the US Department of Health and Human Services about the breach affecting 235,911 people.
Read Full Article
13 Likes
Medium
245

Image Credit: Medium
How are the feeds of Facebook, YouTube, and Instagram tailored to the user?
- Social media apps like Facebook, Twitter, and YouTube tailor feeds based on algorithms sorting posts by relevancy instead of publish time.
- This customization includes prioritizing posts from close friends and family, and recommending videos based on past viewing history.
- While the use of algorithms in social media feeds generally enhances user experience, it's crucial to be cautious about online sharing as everything posted is permanent.
- Users can adjust settings on platforms like Facebook, YouTube, Twitter, and Instagram to control the content they see and mitigate the influence of algorithms.
Read Full Article
14 Likes
Medium
49

Image Credit: Medium
What Online Games are Safe for My Child?
- It is essential to be cautious about allowing children to play online games due to potential exposure to inappropriate content.
- Minecraft is a recommended cross-platform game that is both educational and entertaining for children, promoting creativity, problem-solving, and teamwork.
- Websites like PBS Kids, National Geographic Kids, and FunBrain offer safe and engaging online games for kids, catering to different age groups with educational content.
- These websites provide various activities that help children learn about subjects like animals, geography, and more, in a secure online environment.
Read Full Article
3 Likes
Tech Radar
49
Image Credit: Tech Radar
TikTok fans beware - experts warn dangerous malware spread by AI fake videos
- Hackers are using AI-generated videos on TikTok to trick users into downloading infostealing malware, as warned by cybersecurity researchers Trend Micro.
- The videos demonstrate fake methods to activate premium features in software like Windows, Microsoft Office, Spotify, and CapCut, spreading malicious scripts through PowerShell commands.
- The malware campaign leverages TikTok's algorithm to increase visibility, with one video reaching half a million views, promoting the deployment of Vidar and StealC infostealers.
- Unlike past methods where malware links were shared in descriptions, this campaign delivers malware through videos, bypassing traditional security measures and posing a significant threat to users.
Read Full Article
3 Likes
For uninterrupted reading, download the app