Cyber Security News
Tech Radar
90

Image Credit: Tech Radar
ChatGPT and other AI tools could be putting users at risk by getting company web addresses wrong
- New research highlights that AI often provides incorrect URLs, posing risks to users like phishing and malware attacks.
- One in three login links provided by large language models (LLMs) such as GPT-4.1 were incorrect, with some leading to unsafe domains.
- Attackers are optimizing websites for LLMs, creating phishing risks, with instances of fake sites being recommended by AI tools observed.
- Developers have unknowingly used malicious AI-generated URLs in code, emphasizing the need for users to verify web addresses before clicking on links.
Read Full Article
5 Likes
Dataprivacyandsecurityinsider
34

Joint Release Warns of Iranian-Backed Cyber-Attacks
- A Joint Advisory was issued warning about potential Iranian-backed cyber-attacks on U.S. networks despite ongoing negotiations.
- Iranian state-sponsored cyber actors are likely to increase DDoS campaigns and ransomware attacks, particularly targeting Defense Industrial Base companies.
- The advisory recommends organizations, especially in critical infrastructure, to stay vigilant against potential malicious cyber activities.
- The advisory outlines tools and techniques used by threat actors to target vulnerable networks and devices, and provides strategies to prevent or mitigate attacks.
Read Full Article
1 Like
Dataprivacyandsecurityinsider
86

FBI Warns Airline and Transportation Sectors About Scattered Spider
- The FBI issued a warning to the airline and transportation sectors about cyber criminal group Scattered Spider.
- Scattered Spider uses social engineering techniques to deceive IT help desks and bypass multi-factor authentication.
- Palo Alto’s Unit 42 and Mandiant have verified Scattered Spider's activities in these sectors.
- Organizations are advised to implement robust identity verification processes and phishing-resistant MFA to protect against Scattered Spider attacks.
Read Full Article
5 Likes
Kraken
350

Image Credit: Kraken
Kraken assists U.S. Secret Service in record-breaking crypto fraud seizure
- Kraken collaborated with the United States Secret Service on a crypto fraud investigation, resulting in the largest-ever crypto seizure of approximately $225 million.
- The fraudsters utilized social engineering tactics, known as 'pig butchering,' to deceive victims into fake cryptocurrency investments, leading to significant financial losses.
- The $225 million in question was frozen by Tether in 2023 and linked to a Department of Justice investigation. Kraken's assistance in identifying victims was crucial for the seizure warrant.
- Kraken's dedicated cooperation with law enforcement, rapid response in providing crucial information, and commitment to protecting client assets emphasize their role in combating fraud and maintaining trust in the crypto community.
Read Full Article
21 Likes
Tech Radar
41

Image Credit: Tech Radar
North Korean hackers target Mac users with devious new malware
- North Korean hackers are targeting Mac users with a new backdoor malware called NimDoor to steal cryptocurrency and sensitive data.
- They use Nim, AppleScript, and clever tactics to evade traditional security measures and maintain persistence.
- Victims are lured through Telegram to a fake Zoom meeting where they are tricked into downloading malicious payloads that steal various types of data.
- This attack exploits the rise in remote work and Mac users' perceived security, representing a significant advancement in North Korean cyber capabilities.
Read Full Article
2 Likes
Medium
82

Image Credit: Medium
Cyber Hygiene In The Age Of AI
- Cyber hygiene involves protecting data from cyber threats like identity theft and security breaches through practices like using strong passwords and keeping software up to date.
- In a world intertwined with AI, where our lives are heavily reliant on technology, maintaining good cyber hygiene is essential even for individual users.
- Neglecting basic digital habits can lead to serious consequences, such as identity theft and online reputation blunders, emphasizing the importance of practicing good cyber hygiene.
- The article highlights the significance of cyber hygiene in the age of AI and the potential risks individuals and businesses face in the digital landscape.
Read Full Article
4 Likes
TechCrunch
78

Image Credit: TechCrunch
Ransomware gang Hunters International says it’s shutting down
- Ransomware gang Hunters International announced on its dark web page that it is shutting down without specifying reasons.
- The hackers are offering free decryption keys to all companies impacted by their ransomware to help recover encrypted data.
- Hunters International has had various victims, including a U.S. cancer center and the U.S. Marshals Service, despite the agency denying being hacked.
- There were indications as early as April that the group might transition to a new entity called World Leaks, using different ransomware software and hosting a new site.
Read Full Article
4 Likes
Tech Radar
136

Image Credit: Tech Radar
Scammers are once again abusing PDFs to trick victims into calling fake support numbers
- Security researchers from Cisco Talos have warned of a rise in phishing campaigns involving callback scams, where victims are prompted to call attackers on the phone.
- Threat actors spoof major tech companies like Microsoft and Adobe, sending phishing emails with PDF attachments containing phone numbers controlled by the attackers.
- The attackers manipulate victims into divulging sensitive information or downloading malware by posing as customer representatives during the phone calls.
- These callback phishing campaigns exploit victims' trust in phone calls and use social engineering tactics to deceive them, with most phone numbers being VoIP to make tracing difficult.
Read Full Article
8 Likes
Medium
371

Image Credit: Medium
Delete WhatsApp Already — You’re Not a Lab Rat, Are You?
- WhatsApp, owned by Meta, is under scrutiny for its privacy practices.
- Despite end-to-end encryption for message content, metadata is collected, analyzed, and monetized.
- Meta acquired WhatsApp in 2014 not for user happiness but for data on human behavior.
- The gradual erosion of privacy on WhatsApp has raised concerns about user data exploitation.
Read Full Article
22 Likes
TechBullion
380

Image Credit: TechBullion
$100 Million and Counting – What FUNToken’s Milestone Means for Its Market Position
- FUNToken has crossed the $100 million market capitalization mark, signaling a significant milestone in its positioning within the Web3 landscape.
- The achievement is attributed to strategic planning, transparent revenue streams, and deflationary measures, with a recent 25 million $FUN burn showcasing the project's sustainable economic impact.
- Investors have reacted positively to the revenue-driven burn, leading to a 41% price surge and subsequent consolidation within the $0.010-$0.011 range, solidifying FUNToken's perceived value beyond speculation.
- FUNToken's roadmap includes the development of games and a mobile wallet to enhance utility and engagement, while prioritizing security through a complete CertiK audit and Skynet integration.
Read Full Article
22 Likes
Tech Radar
119

Image Credit: Tech Radar
Signal clone used by federal agencies hit in attacks targeting major flaws - CISA says patch immediately
- Hackers are actively targeting a popular Signal messaging app clone, TeleMessage, used by federal agencies.
- The clone lacks proper end-to-end encryption and has been exploited by hackers using CVE-2025-48927 and CVE-2025-48928 vulnerabilities.
- Around 60 government officials' chats and metadata have been stolen by hackers. CISA has given agencies until July 22 to patch the app.
- The app was involved in the Signalgate scandal, where sensitive information was leaked online, leading to the removal of a former national security advisor.
Read Full Article
7 Likes
Medium
276

Image Credit: Medium
Why Banning Smartphones at School Sends the Wrong Message to our Kids About Digital Citizenship
- Schools are increasingly implementing policies to minimize smartphone use, including bans and stricter guidelines.
- Research shows over 75% of US schools have smartphone bans, with some requiring phones to be kept in 'phone jails'.
- Experts suggest that outright smartphone bans may hinder teaching digital citizenship and tech literacy.
- Promoting mindful smartphone use through conversations and strategies is seen as a more effective solution than outright bans.
Read Full Article
16 Likes
Medium
342

Image Credit: Medium
An Uncertain Vision (Pro) of the Future
- Apple introduced the Vision Pro, their first spatial computer, aiming to enhance digital experiences by overlaying the user interface onto the physical world.
- The device integrates Augmented Reality (AR) and Virtual Reality (VR) capabilities to offer a more immersive user experience.
- While Apple touts the device's potential in entertainment and productivity, concerns persist regarding its impact on social interactions and potential for increased social isolation.
- The emergence of spatial computing technology prompts a reevaluation of the balance between online and offline interactions as users navigate the new immersive capabilities of the Vision Pro.
Read Full Article
20 Likes
Medium
20
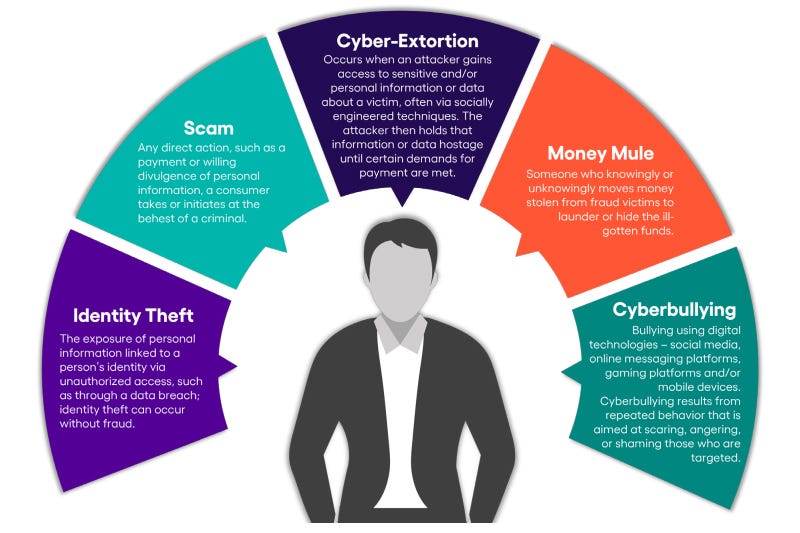
Image Credit: Medium
Parents, Your Kids Need Your Cyber Help
- 73% of U.S. households are concerned about cyberbullying, but many parents don't realize that social media is a primary tool for cyberbullying targeting children on platforms like YouTube, Snapchat, TikTok, and Facebook.
- Cyberbullied children are more susceptible to fraud, as they tend to hide online activities from parents, making them easier targets for scams that rely on manipulative schemes.
- Children's social media accounts being compromised can lead to scams targeting other family members. Posting location details online can increase physical risks and aid cybercriminals in creating profiles to deceive children and their connections.
- Scams involving fraudulent peer-to-peer payments are on the rise, affecting households when criminals exploit children to access their parent's accounts. Parents are advised to sign up for security alerts and family-wide identity protection to detect and prevent cyber threats.
Read Full Article
1 Like
Kaspersky
119

Image Credit: Kaspersky
Best travel apps: maps, taxis, food, internet | Kaspersky official blog
- Prepare for travel with essential apps for maps, taxis, food, internet connectivity.
- Navigate new places with Google Maps, GPS mapping apps, and Guru Maps for hiking.
- Ensure connectivity with eSIM, useful local operator apps, and Kaspersky VPN Secure Connection.
- Use specialized apps like Moovit for public transport and MICHELIN Guide for dining recommendations.
- Secure travel with encrypted note-taking apps, password manager, and VPN Secure Connection.
Read Full Article
7 Likes
For uninterrupted reading, download the app