Cyber Security News
Medium
318
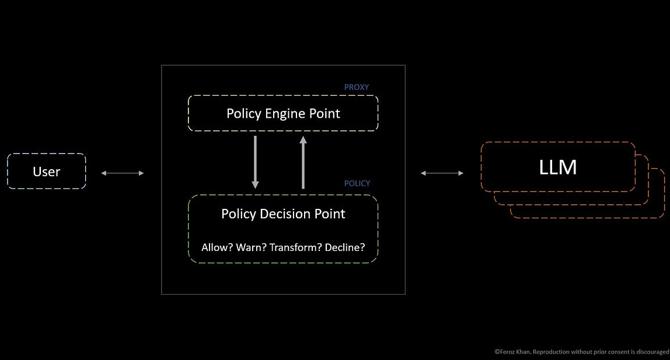
Image Credit: Medium
Building Safer LLMs: How Proxy-Based Policy Engines Stop Prompt Injection
- Proxy-based policy engines provide a robust way to protect Language Model Models (LLMs) from threats by inserting a proxy between users and the model.
- Defenses live in the proxy, removing the need to fine-tune every new LLM model version for security risks, and enabling centralized management of multiple models.
- LlamaGuard and PromptGuard are LLM-based classifiers for filtering input/output to detect attacks, while open-source proxy tools like Usage Panda can monitor and control LLM traffic.
- Relying on a proxy-based layer with a policy engine enhances LLM security, ensuring they behave reliably and safely without changing base models.
Read Full Article
19 Likes
Dev
327

Image Credit: Dev
Internet Authentication Service for CyberSecurity
- Internet Authentication Service (IAS) is a network service by Microsoft that offers centralized authentication, authorization, and accounting for user access to network resources.
- IAS implements the RADIUS protocol, enabling organizations to manage user accounts and permissions centrally, enhancing security by allowing only authorized users to access sensitive information.
- IAS can take different forms, including RADIUS, TACACS+, and LDAP, catering to various organizational needs such as remote user authentication and detailed user permission controls.
- The key features of IAS include authentication, authorization, and accounting, ensuring secure user access to resources and tracking user activity for compliance purposes.
Read Full Article
19 Likes
Fintechnews
381

Image Credit: Fintechnews
Beyond KYC: How Technology is Transforming the Fraud Prevention Game
- Digital wallets and cryptocurrencies are prime targets for fraud, as per SEON's report.
- Traditional fraud prevention methods struggle to keep up with evolving tactics.
- Organizations shift focus to proactive strategies, prioritizing real-transaction monitoring and digital footprint analysis.
- Device intelligence offers additional defense layer to detect fraudulent activities in online transactions.
- Adoption of advanced technologies enhances security, reduces fraud rates, and boosts customer experiences.
Read Full Article
22 Likes
The Fintech Times
406

Image Credit: The Fintech Times
Banks Roll Out Confirmation of Payee Across Australia to Crack Down on Scams
- Banks in Australia are officially rolling out Confirmation of Payee, a name-matching service to protect customers from scams.
- Investing around $100 million in the technology, banks aim to keep consumers' money safe through the Scam-Safe Accord initiative.
- Confirmation of Payee helps reduce scams by verifying name, BSB, and account number details before payments are made, giving customers more control and confidence.
- Australia's banking sector is leading in customer protection against scams with the implementation of Confirmation of Payee, contributing to the reduction of scam losses and enhancing customer safeguards.
Read Full Article
24 Likes
Dev
174

Image Credit: Dev
SSH Over Tor: Cool, Practical, or Just Tinfoil Hats?
- Suricata is being explored further in a robotics project to monitor network interactions for security and system behavior during development and deployment.
- With modern robots having multiple network interfaces, monitoring network traffic is crucial, and Suricata offers deep packet inspection capabilities.
- Suricata operates in IDS mode, providing intrusion detection through deep packet inspection and configurable rules for generating alerts.
- A custom Python script can distill Suricata logs, grouping entries for better analysis, revealing traffic patterns and potential intrusion attempts.
Read Full Article
10 Likes
Medium
107

Image Credit: Medium
Yuzu Keys: Your Gateway to Nintendo Switch Gaming on PC
- Understanding Yuzu keys is crucial for gamers looking to play Nintendo Switch games on PC through emulation.
- Yuzu keys act as a decryption password for the emulator to read encrypted Switch game files, enabling gameplay.
- Obtaining Yuzu keys legally involves extracting them from your own Nintendo Switch using tools like Lockpick_RCM, avoiding risky downloads from unknown sources.
- Setting up Yuzu keys correctly allows gamers to enhance gameplay experience with features like improved visuals, higher frame rates, backup saves, and more.
Read Full Article
6 Likes
Ars Technica
382

Image Credit: Ars Technica
AT&T rolls out Wireless Account Lock protection to curb the SIM-swap scourge
- AT&T is rolling out a protection called Wireless Account Lock to prevent unauthorized changes to mobile accounts in an effort to combat SIM swapping, a form of account hijacking.
- SIM swapping, or port-out fraud, has been a longstanding issue that has affected wireless carriers and their customers. Scammers use this technique to swap out SIM cards, gaining access to accounts and potentially stealing funds, as seen in a case involving cryptocurrency theft.
- The new Wireless Account Lock feature aims to prevent SIM-swap scams by restricting changes to SIM cards until the lock is deactivated. This protection is available in the myAT&T mobile app settings.
- AT&T's Wireless Account Lock follows similar protection services introduced by T-Mobile and Verizon. The move comes amid increasing efforts to combat unauthorized SIM swaps, with the Federal Communications Commission implementing rules to make such scams harder to execute.
Read Full Article
22 Likes
Securityaffairs
261

Image Credit: Securityaffairs
Cisco removed the backdoor account from its Unified Communications Manager
- Cisco addressed a static SSH credentials vulnerability in its Unified Communications Manager, tracked as CVE-2025-20309.
- The vulnerability allowed remote attackers to log in using hardcoded root credentials, granting full root privileges without authentication.
- Cisco removed the backdoor account from its Unified Communications Manager to mitigate the issue.
- Admins are advised to upgrade to fixed software releases to prevent exploitation of the vulnerability, with no workarounds available.
Read Full Article
15 Likes
Tech Radar
294

Image Credit: Tech Radar
Security experts flag another worrying issue with Anthropic AI systems - here's what they found
- Security experts discovered a critical-severity vulnerability in Anthropic's Model Context Protocol (MCP) Inspector project, allowing potential remote code execution attacks against host devices.
- The flaw in the Inspector tool could have been exploited by hackers to steal data, deploy malware, and move laterally within networks.
- To exploit the vulnerability, attackers needed to exploit a decades-old browser bug alongside the flaw in Inspector.
- Anthropic addressed the flaw, tracked as CVE-2025-49596, in mid-June 2025 by issuing a patch to version 0.14.1, adding a session token and origin validation as preventive measures.
Read Full Article
17 Likes
TechBullion
157

Image Credit: TechBullion
Beyond Basic Chat: Getting To The Bottom Of Cloud Messaging’s Security Edge
- Cloud messaging has evolved beyond basic chat, emphasizing the importance of security in modern communication.
- Modern cloud messaging platforms focus on user authentication, data protection, API security, compliance, proactive defense, and device-level security.
- Interoperability and standardization are crucial for ensuring secure and unified communication across different platforms.
Read Full Article
9 Likes
Wired
332

Image Credit: Wired
A Group of Young Cybercriminals Poses the ‘Most Imminent Threat’ of Cyberattacks Right Now
- Recent cyberattacks on UK, US, and Canada caused by financially motivated cybercriminals.
- The group, Scattered Spider, targets companies with expertise in backend systems and social engineering.
- Group members deploy ransomware or extortion attacks after gaining system access.
- Law enforcement pressure in 2024 temporarily slowed down the group, but recent attacks resumed.
Read Full Article
20 Likes
Infoblox
58

Image Credit: Infoblox
Why Allowlisting Alone Is Not Sufficient to Protect Cloud Workloads
- Allowlisting outbound destinations has operational challenges in dynamic cloud environments.
- Trusted services can be compromised, leading to data exfiltration or C2 channel abuse.
- Limitations like DNS tunneling and misconfigurations expose vulnerabilities of allowlisting alone.
Read Full Article
3 Likes
Tech Radar
83

Image Credit: Tech Radar
Google has patched another urgent security flaw in Chrome - so update now or be at risk
- Google's TAG team discovered and patched a high-severity bug in Chrome's V8 engine, identified as CVE-2025-6554, that allowed threat actors to execute arbitrary code on endpoints.
- The bug was actively exploited in the wild, posing risks of data theft, token exfiltration, and malware deployment.
- Google released patches for Windows, macOS, and Linux versions on June 26, urging users to update to safeguard their systems.
- The exploit was discovered by Google's Threat Analysis Group (TAG), indicating potential abuse by nation-state threat actors in targeted attacks.
Read Full Article
5 Likes
Tech Radar
0

Image Credit: Tech Radar
Insurance group Kelly Benefits says over half a million people now affected in major data breach - here's what we know
- Insurance group Kelly Benefits suffered a data breach affecting over half a million customers.
- Sensitive information such as full names, Social Security numbers, and financial data was compromised.
- Victims are being offered free credit monitoring and identity theft protection services.
- Kelly Benefits urges customers to remain vigilant against potential phishing attacks and fraud.
Read Full Article
Like
Medium
124

Image Credit: Medium
Zama and FHE: The Future of Private and Secure Blockchains Has Arrived
- Zama is utilizing Fully Homomorphic Encryption (FHE) to enable smart contracts to be executed on encrypted data, ensuring privacy and security.
- FHE allows computations to be performed on encrypted data, keeping the actual data hidden from nodes, making it a game-changer for Web3 by maintaining data confidentiality.
- Zama's Confidential Blockchain Protocol enables fully private smart contracts, where inputs and outputs remain encrypted throughout the execution, offering enhanced privacy compared to traditional blockchains.
- Zama and FHE are introducing a new era for Web3 by prioritizing privacy as a foundational design element, allowing for various applications like private voting, secure transactions, and confidential health apps without exposing sensitive data.
Read Full Article
7 Likes
For uninterrupted reading, download the app