Cyber Security News
Medium
74
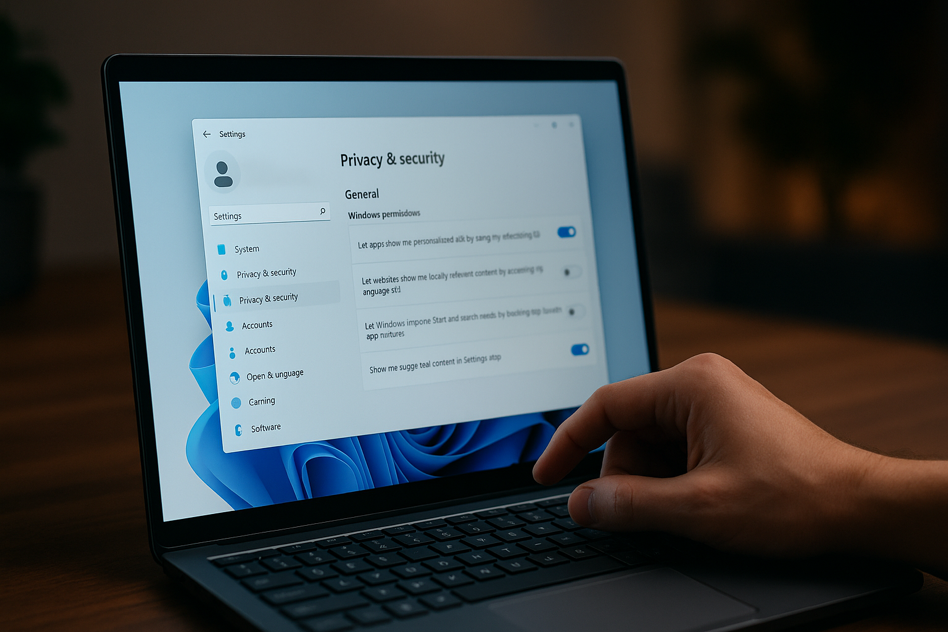
Image Credit: Medium
Want More Privacy on Windows 11? Here Are 6 Features I Always Disable
- Windows 11 offers several features that can compromise user privacy.
- Steps to enhance privacy on Windows 11 include disabling the Advertising ID to prevent personalized ads.
- Users can limit diagnostic data sharing with Microsoft and disable location services when not needed.
- Controlling app permissions, avoiding syncing data with a Microsoft account, and disabling Activity History can further enhance privacy on Windows 11.
Read Full Article
4 Likes
Medium
173
Image Credit: Medium
Zama’s Fully Homomorphic Encryption: Redefining Privacy in Crypto
- Zama, an open-source cryptography company, focuses on making FHE practical for blockchain and AI.
- Fully Homomorphic Encryption (FHE) allows calculations on encrypted data without revealing information.
- Zama's FHE enables privacy-preserving decentralized applications, revolutionizing the crypto industry.
- Its speed improvement makes FHE viable for real-world blockchain applications like payments.
- Zama's FHE balances privacy and transparency, offering solutions for confidential transactions in Web3.
Read Full Article
10 Likes
Dev
351

Image Credit: Dev
Zeroize: The Tiny and Memory-Safe Rust Crate
- Zeroize is a Rust crate designed to securely and efficiently zero out memory containing sensitive data like passwords and cryptographic keys.
- The crate helps address the threat of sensitive data lingering in memory even after it's no longer needed, which could leave it vulnerable to exposure in certain attacks.
- Zeroize allows users to explicitly clear memory when sensitive data is no longer required, providing a way to take control over memory security.
- Users can easily implement Zeroize in their Rust code to automate the process of securely clearing sensitive data, adding minimal overhead to the final binary.
Read Full Article
21 Likes
Tech Radar
243

Image Credit: Tech Radar
Security breach reveals Catwatchful spyware is snooping on thousands of phones - here's how to stay safe
- A security researcher uncovered a major data breach involving Catwatchful, an Android spyware app posing as a child monitoring tool.
- The breach exposed a user database with plaintext passwords and email addresses, impacting over 62,000 users and compromising phone data of 26,000 victims.
- The dodgy developer behind Catwatchful was identified due to reusing an email address, leading to the exposure of the spyware's operation outside the Play Store.
- Google has taken steps to warn users about the app, despite it not being available on the Play Store, advising the use of security measures like antivirus software and malware removal tools.
Read Full Article
14 Likes
Tech Radar
70

Image Credit: Tech Radar
The AI-powered future of ransomware is coming soon - here's what we need to look out for
- The future of ransomware threats is evolving with the use of Generative Artificial Intelligence (GenAI) by hackers to improve their coding processes.
- Kaspersky's Global Research and Analysis Team (GReAT) analyzed the new ransomware group FunkSec and found it using AI to generate code in its encryptors and tools.
- AI-powered attacks are on the rise, making AI-powered defenses essential in combating evolving threats. Companies like CrowdStrike, SentinelOne, and Microsoft are leveraging AI and machine learning for enhanced security.
- Kaspersky recommends enabling ransomware protection for endpoints, keeping systems updated, and focusing on detecting lateral movements and data exfiltration for improved defense against ransomware threats.
Read Full Article
4 Likes
Securityaffairs
12

Image Credit: Securityaffairs
Europol shuts down Archetyp Market, longest-running dark web drug marketplace
- Europol, in collaboration with German authorities, has shut down Archetyp Market, the longest-running dark web drug marketplace.
- The operation spanned six countries and resulted in the arrest of the market's administrator in Spain, along with targeted actions against top vendors in Sweden.
- Archetyp Market operated for over five years, attracting over 600,000 users globally and facilitating drug transactions totaling at least EUR 250 million.
- The takedown was part of a significant international effort involving around 300 officers and led to the seizure of assets worth €7.8 million, delivering a blow to anonymous drug trafficking on the dark web.
Read Full Article
Like
Medium
399

Image Credit: Medium
Tor over VPN vs. VPN over Tor — Which Actually Protects You Better?
- Tor over VPN involves connecting to a VPN server first, then routing encrypted traffic through the Tor Network.
- Drawbacks of Tor over VPN include unencrypted traffic leaving Tor exit nodes and dependence on VPN reliability.
- VPN over Tor encrypts data when it enters and exits Tor nodes before reaching the Internet, providing better anonymity.
- VPN over Tor is suitable for maximum anonymity, hiding VPN usage, and controlling VPN endpoint.
Read Full Article
23 Likes
Global Fintech Series
405

Image Credit: Global Fintech Series
How SSI Empowers Users to Own and Control Their Digital Identity?
- Identity in the digital realm is critical, but often controlled by third parties.
- Self-Sovereign Identity (SSI) enables users to manage and share their digital credentials.
- SSI decentralizes identity, offers privacy, security, and enhances user control and portability.
Read Full Article
24 Likes
Wired
384

Image Credit: Wired
The Promise and Peril of Digital Security in the Age of Dictatorship
- In El Salvador, LGBTQ+ activists face increased authoritarianism under Bukele's regime.
- Activists, like Rodríguez, receive digital security training amidst threats and violent crackdowns.
- Organizations document hate crimes, navigating challenges to protect victims' data from government scrutiny.
- Government implements laws for cyber control, raising concerns about privacy and freedom of speech.
- The struggle for justice and protection of data persists amid escalating political control.
Read Full Article
23 Likes
Tech Radar
78

Image Credit: Tech Radar
Cisco warns of a serious security flaw in comms platform - and that it needs patching immediately
- Cisco has discovered hardcoded login credentials with root access in its Unified Communications Manager, requiring immediate patching.
- The security flaw, tracked as CVE-2025-20309 with a severity score of 10/10, affects different releases of the Unified CM software.
- Affected versions, ranging from 15.0.1.13010-1 to 15.0.1.13017-1, have no workarounds, and the only solution is to upgrade to version 15SU3 released in July 2025.
- No evidence of abuse has been reported, and hardcoded credentials represent a common cause of system infiltrations in software applications.
Read Full Article
4 Likes
Pymnts
182

Image Credit: Pymnts
Payment Hubs Rescue Banks From $100 Million Digital Payments Chaos
- FinTechs and digital-first challengers have raised consumer expectations for frictionless transactions.
- Traditional banks are facing pressure due to complex and siloed payment systems, leading to inefficiencies.
- Businesses lose an average of $98.5 million annually due to disruptions in money movement, citing cyber threats, fraud, and regulatory complexities as main contributors.
- Payment hubs provide unified platforms that streamline payment processing, offering faster transactions and enhanced security and compliance.
Read Full Article
10 Likes
Securityaffairs
20

Image Credit: Securityaffairs
Kelly Benefits data breach has impacted 550,000 people, and the situation continues to worsen as the investigation progresses
- A data breach at Kelly Benefits has impacted 550,000 people, with the number of affected individuals growing as the investigation continues.
- Benefits and payroll solutions firm Kelly Benefits confirmed the breach, revealing that more individuals were affected than originally believed.
- The breach, which occurred in December 2024, exposed sensitive personal data like names, SSNs, medical, and financial data.
- The latest update from the company disclosed that over 553,660 individuals were impacted, and affected individuals are being offered free credit monitoring and identity protection services.
Read Full Article
1 Like
Dev
161

Image Credit: Dev
How to Avoid False Positives in SafeLine WAF with Custom Rules
- When using a WAF like SafeLine, false positives can occur due to default rules not aligning with application behavior.
- Resolving false positives involves configuring custom rules in SafeLine WAF, such as whitelists to allow specific traffic or blacklists to block malicious patterns.
- Common methods for custom rule configuration in SafeLine include partial path match, exact path match, prefix match, and regex match.
- Testing custom rules in SafeLine can be optimized by avoiding browser caching and understanding the matching logic for effective protection.
Read Full Article
9 Likes
Silicon
240
Image Credit: Silicon
Qantas Confirms Customer Data Stolen By Hackers
- Australian airline Qantas experienced a cyber-attack compromising customer data of about 6 million individuals.
- The breach affected a third-party platform used by Qantas' customer contact centre, including customer names, email addresses, and phone numbers.
- No payment card details or login credentials were compromised in the attack, and Qantas has taken steps to secure its systems.
- The incident possibly linked to the hacking group Scattered Spider, known for targeting various sectors including airlines, using social-engineering methods for gaining unauthorized access.
Read Full Article
14 Likes
Semiengineering
91
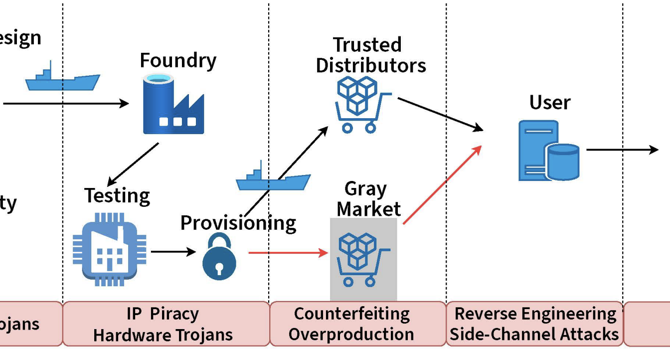
Image Credit: Semiengineering
Framework To Analyze Threats To The Semiconductor Supply Chain (NIST, U. of Maryland)
- Researchers at NIST and University of Maryland published a technical paper on analyzing threats in the semiconductor supply chain.
- The framework introduces a metric to quantify threats from collusion of adversaries at different supply chain stages, aiming to guide security efforts and optimize hardware security costs.
- Two case studies demonstrate real-life applications of the framework in the paper.
- Titled 'Analyzing Collusion Threats in the Semiconductor Supply Chain,' the paper provides insights into security challenges in the semiconductor industry.
Read Full Article
5 Likes
For uninterrupted reading, download the app