Cyber Security News
Tech Radar
356

Image Credit: Tech Radar
Hundreds of Android apps band together in massive scam campaign targeting millions - here's what we know
- A major ad fraud campaign involving hundreds of Android apps has been dismantled by security researchers.
- The campaign, known as IconAds, displayed ads without proper context or user consent and hid app icons on devices to avoid removal.
- The apps were removed from the Google Play Store after generating 1.2 billion bid requests daily at its peak.
- Although the malicious apps have been taken down, researchers anticipate new apps with similar fraudulent tactics to surface in the future.
Read Full Article
21 Likes
Tech Radar
135

Image Credit: Tech Radar
Venture capital giant IdeaLab confirms breach, says private data was stolen in attack
- IdeaLab, a technology startup incubator, confirmed a data breach where cybercriminals accessed its network and stole sensitive information.
- The breach affected current and former employees, support service contractors, and their dependents, with stolen data including names and 'variable data'.
- The ransomware group, Hunters International, claimed responsibility for the attack and published decryption keys for all victims, with the leaked archive containing 137,000 files.
- IdeaLab is offering affected individuals complimentary identity theft protection services and credit monitoring, while security experts speculate about the motives behind Hunters International's disbanding.
Read Full Article
8 Likes
Socprime
381

Image Credit: Socprime
CVE-2025-5777 Detection: A New Critical Vulnerability Dubbed “CitrixBleed 2” in NetScaler ADC Faces Exploitation Risk
- Critical security issue in NetScaler ADC, CVE-2025-5777, poses exploitation risk after being exploited.
- Vulnerability allows memory overflow, control flow alteration, potential DoS conditions; resembles CitrixBleed.
- CitrixBleed 2's exploitation involves data compromise, session token leakage, posing serious risks.
- Detection tools, rules, and AI are available to identify and mitigate CVE-2025-5777 risks.
Read Full Article
22 Likes
Medium
155
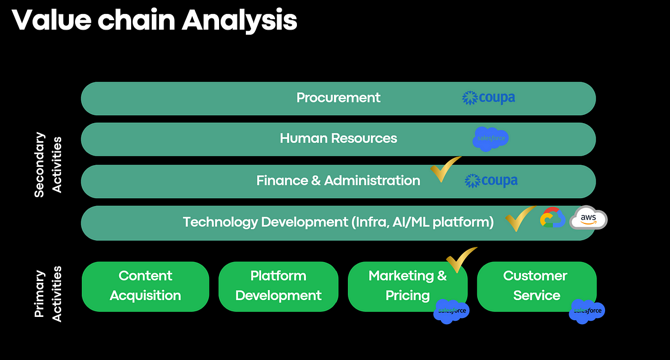
Image Credit: Medium
What Spotify Taught Me About Strategy, AI, and User Experience
- Spotify faces challenges such as providing bad recommendations and relying heavily on ads and subscriptions for revenue.
- Issues with user experience include buggy playback, repetitive songs, and unwanted podcasts.
- Proposed solutions include using smarter machine learning, dynamic pricing, and improving system stability.
- Recommendations also involve redesigning Spotify's user flow, leveraging ML engines like Vertex AI, and moving towards a retrieval and re-ranking approach.
Read Full Article
9 Likes
Global Fintech Series
291

Image Credit: Global Fintech Series
FinSei Ltd Partners with FinHub.cloud to Accelerate Next-Generation Payment Solutions Across the UK and Europe
- FinSei Ltd, a fintech company, partners with FinHub.cloud to enhance payment solutions in the UK and Europe.
- The partnership aims to improve scalability, security, and operational efficiency for FinSei.
- FinSei offers e-wallets, card issuing, international transfers, and alternative payments, focusing on underserved markets and cross-border transactions.
- The collaboration with FinHub.cloud will boost transaction speed, strengthen security, accelerate product rollouts, and enhance regulatory compliance for FinSei.
Read Full Article
17 Likes
Cheapsslshop
291

Image Credit: Cheapsslshop
TLS Certificate Lifetimes Drop to 47 Days: What You Need to Know
- The CA/Browser Forum, supported by Apple, Google, and Mozilla, passed a proposal to reduce the maximum lifespan of TLS certificates starting in March 2026.
- The certificate validity will be gradually reduced to just 47 days by 2029 to enhance internet security and mitigate risks associated with expired or stolen certificates.
- This change poses challenges for website owners and IT teams, requiring them to adapt to shorter certificate lifetimes and prepare for the upcoming security update.
- The shift aims to improve online security by preventing misuse of outdated or compromised certificates, with significant changes planned for TLS certificate validity periods.
Read Full Article
17 Likes
Global Fintech Series
262

Image Credit: Global Fintech Series
Why Fintech’s True AI Revolution Starts with Getting the Basics Right?
- FinTech's AI narrative depicts a future with virtual assistants revolutionizing money interactions.
- However, the true AI revolution lies in perfecting fundamental operations over futuristic dreams.
- AI optimization enhances fintech processes, emphasizing the need for strong data governance.
- Fintech's real magic lies in AI as an optimizer refining existing processes.
Read Full Article
15 Likes
Tech Radar
295

Image Credit: Tech Radar
Experts warn this top GenAI tool is being used to build phishing websites
- Okta warns that the GenAI tool v0.dev is being exploited to create phishing sites hosted on Vercel infrastructure to appear legitimate.
- The AI tools are generating false URLs, posing a risk to unsuspecting users and providing a lower technical barrier for cybercrime.
- Phishing sites created using v0.dev are mimicking authentic company logos and hosted on Vercel to enhance credibility, with popular targets including Microsoft 365 and fake crypto sites.
- Experts recommend implementing multi-factor authentication and updating cybersecurity training programs to combat the rising threat of AI-generated phishing attacks.
Read Full Article
17 Likes
Dev
254

Image Credit: Dev
MCP 2025-06-18 Spec Update: Security, Structured Output & Elicitation
- MCP 2025-06-18 Spec Update enhances security with OAuth 2.0 Resource Server classification.
- Structured JSON tool output supported, along with elicitation for user input mid-session.
- New Security Considerations, PKCE protection, and token audience validation for MCP servers.
- Added Security Best Practices with concrete countermeasures and structured output schema support.
- Resource links in tool results, protocol version enforcement, and JSON-RPC batching removed.
Read Full Article
15 Likes
Tech Radar
303

Image Credit: Tech Radar
French government hit by Chinese hackers exploiting Ivanti security flaws
- Chinese state-sponsored threat actors exploited three zero-day vulnerabilities in Ivanti CSA solutions to access French government agencies and other commercial entities such as telcos, finance, and transportation organizations.
- The attackers abused the vulnerabilities to steal login credentials and establish persistence on target endpoints, using techniques like deploying PHP web shells and installing kernel modules acting as a rootkit.
- The attacks were attributed to a group named Houken, known for exploiting vulnerabilities in SAP NetWeaver previously, and sold the gained access to French government devices, believed to be targeting valuable intelligence and sensitive data.
- The French National Agency for the Security of Information Systems (ANSSI) confirmed the breaches, linking the attacks to Chinese state-sponsored actors, while noting the group Houken had targeted various sectors beyond Western entities.
Read Full Article
18 Likes
Neuways
369

Image Credit: Neuways
AI deepfakes: Denmark introduces law to protect citizens
- Denmark introduces pioneering legislation to protect citizens from AI-generated deepfakes.
- The law gives individuals control over their face, voice, and identity rights.
- Deepfake technology poses threats like fraud, reputation attacks, and social manipulation.
- UK businesses may face legal obligations to safeguard against deepfake risks.
Read Full Article
22 Likes
Pymnts
156

Image Credit: Pymnts
Nonbanks Lead Expansion Into Real-Time Payments
- Real-time payments are becoming the new standard for fast, efficient, and convenient transactions, revolutionizing money movement globally.
- Nonbank entities are increasingly joining the real-time payments space, indicating a shift towards broader adoption and innovation in faster payment systems.
- Retail giant Walmart is venturing into real-time payments with a new pay-by-bank option, aiming to streamline transactions and avoid costly interchange fees.
- The expansion of real-time payment systems globally creates opportunities for nonbank players like Walmart to enhance customer service and drive mainstream adoption of instant payments.
Read Full Article
9 Likes
Dev
307

Image Credit: Dev
Hardening Docker Deployments with SafeLine WAF Integration
- Docker is commonly used for deploying lightweight applications, but lacks security and performance tuning by default.
- Guide covers how to install and optimize Docker on CentOS, secure containers using SafeLine WAF, and optimize Docker settings.
- SafeLine WAF is a free Web Application Firewall that protects against various attacks - install process and securing steps included.
- Optimizing Docker, adding SafeLine WAF, and configuring settings helps improve security and performance for Docker deployments.
Read Full Article
18 Likes
Securityaffairs
332

Image Credit: Securityaffairs
A flaw in Catwatchful spyware exposed logins of +62,000 users
- A flaw in the Catwatchful Android spyware exposed the full user database, leaking email addresses and plaintext passwords of over 62,000 users, including customers and the admin.
- Catwatchful, a spyware posing as a child monitoring app, is used for non-consensual surveillance, enabling access to victims' private data and real-time phone content.
- The spyware's database exposed around 62,000 accounts and data from 26,000 victims, primarily in Mexico, Colombia, India, and other Latin American countries, with the administrator's identity also revealed.
- Security researcher Eric Daigle found a SQL injection flaw in Catwatchful, leading to the exposure of plaintext logins and passwords, which prompted actions from Google's Safe Browsing and the Firebase team but the database remained online.
Read Full Article
20 Likes
Global Fintech Series
275

Image Credit: Global Fintech Series
The Open Platform Is First Unicorn in Web3 Ecosystem in Telegram at $1Billion Valuation
- The Open Platform in Telegram has become the first unicorn in the TON-based ecosystem with a $1 billion valuation after completing its Series A funding round led by Ribbit Capital and Pantera Capital.
- The raised $28.5 million in an extended Series A funding round, bringing the total funding secured by The Open Platform to over $70 million, showcasing investor confidence in its ability to drive blockchain ecosystem growth in Telegram.
- The investment will support the geographic expansion of TOP's portfolio companies across the U.S., EU, and other regions, focusing on regulatory licensing, compliance infrastructure, and security enhancements.
- The Open Platform aims to leverage TON Blockchain in conjunction with Telegram's global reach to onboard a billion users to crypto, offering various products and apps to drive mainstream adoption of blockchain technology.
Read Full Article
16 Likes
For uninterrupted reading, download the app