Cyber Security News
Medium
251

The Future of Cybersecurity: AI-Powered Detection of Malware and Phishing
- Malware and phishing are major cyber threats targeting individuals and organizations, aiming to steal data or manipulate users into revealing sensitive information.
- Attackers are using advanced techniques like polymorphic malware and social engineering, challenging traditional detection systems.
- AI, particularly when using machine learning and NLP, enhances cybersecurity by quickly analyzing data for anomalies, detecting phishing links, and learning from new threats.
- While AI presents significant advantages in detecting and responding to cyber threats, integrating it with human expertise and robust security policies will be crucial for staying ahead in cybersecurity.
Read Full Article
15 Likes
Hackaday
268
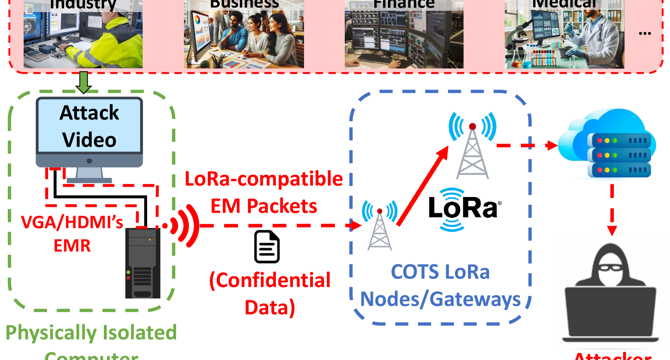
Image Credit: Hackaday
Video Cable Becomes Transmitter with TEMPEST-LoRa
- Researchers have developed TEMPEST-LoRa, a method to encode LoRa data into video files for transmission.
- By using a specially-constructed video file, information can be broadcasted via LoRa using a video cable and graphics card as the transmitter.
- The technique requires a display resolution of 1080×1920@60Hz, and the video must play fullscreen, allowing transmission even when the display is off.
- The maximum transmission distance achieved was 81.7m at 21.6 kbps, and the code is available on GitHub for academic use.
Read Full Article
16 Likes
Medium
272

Image Credit: Medium
Learn about AI-Related Risks and AI Risk Management
- AI-related risks encompass disruptive outcomes and negative impacts associated with AI technologies.
- Sources of AI risks include ethical aspects like fairness and reliability, and technical aspects.
- AI risk management involves applying techniques like risk avoidance, mitigation, transfer, and acceptance.
- Existing frameworks for AI risk management need further development to address evolving technologies.
Read Full Article
16 Likes
Dev
195

Image Credit: Dev
The Rise of AI-Generated Phishing Websites: How Hackers Are Weaponizing Generative Tools
- Phishing attacks have evolved with the use of generative AI tools to create fake websites and URLs quickly and at scale.
- AI-powered phishing sites hosted on legitimate infrastructure make traditional detection challenging for defenders.
- Real-world impacts include cloned credential sites, deepfake-enhanced attacks, and homograph domain spoofing.
- AI amplifies the phishing threat by enabling fast and personalized attacks, emphasizing the need for proactive defense measures.
Read Full Article
11 Likes
Medium
142

Image Credit: Medium
How I Ended Up in Cybersecurity (And How You Can Too)
- The author's journey into cybersecurity began with creative coding, developing an 8-bit game using Python and Pygame.
- Driven by curiosity, the author transitioned from coding to cybersecurity with a hacker mindset of exploring the limits of systems.
- The author emphasizes the importance of hands-on experience in cybersecurity, recommending guided labs, learning core tools, building a portfolio, and engaging with the community.
- While certifications like Certified Penetration Testing Specialist (CPTS) can be beneficial, the author highlights that they are just checkpoints in the cybersecurity journey.
Read Full Article
8 Likes
Mjtsai
309

Common Vulnerabilities and Exposures (CVE) Funding
- DHS did not renew funding for MITRE's 25-year-old Common Vulnerabilities and Exposures (CVE) program, leading to a potential shutdown on April 16.
- Curl and Postgresql have faced issues with bogus CVEs, leading to wasted time addressing them, and the Linux kernel generates many CVEs, diminishing their value.
- The CVE Foundation has been established to ensure the long-term viability, stability, and independence of the CVE Program.
- U.S. government reversed the decision to discontinue funding for the CVE program, providing another 11 months of funding, while the EU has developed its own alternative called the EUVD.
Read Full Article
18 Likes
Dev
130

Image Credit: Dev
Security news weekly round-up - 4th July 2025
- Actively exploited vulnerability allows full server takeover and hardware destruction.
- New flaw in IDEs enables malicious extensions to bypass verified status.
- Hackers use PDFs to impersonate known brands in phishing campaigns, risking data theft.
- NimDoor macOS malware revives itself, posing persistent threat to users and networks.
- Vercel's AI tool abused by cybercriminals to create fake login pages at scale.
Read Full Article
7 Likes
Securityaffairs
53

Image Credit: Securityaffairs
Critical Sudo bugs expose major Linux distros to local Root exploits
- Critical Sudo bugs have been discovered that allow local users to gain root access on Linux systems.
- The vulnerabilities, named CVE-2025-32462 and CVE-2025-32463, affect major Linux distributions.
- CVE-2025-32462 allows executing commands on unintended machines, while CVE-2025-32463 lets local users obtain root access through user-controlled directories.
- The Stratascale Cyber Research Unit found the vulnerabilities, with a fix limiting the --host option and deprecating the chroot feature in Sudo.
Read Full Article
3 Likes
Medium
48
Image Credit: Medium
Your Data and Where It Lives
- Uploading a photo or posting content online leads to a complex system of data tracking, storage, and surveillance.
- Deleted data may remain in backups for months, and manual clearing of activity logs is required to prevent data retention.
- Instances like the Cambridge Analytica scandal illustrate the extent of data harvesting and misuse by companies like Meta.
- Data privacy concerns extend to brands selling data, surveillance by agencies like ICE, and the persistence of ghost data on reset devices.
Read Full Article
2 Likes
Dev
277

Image Credit: Dev
SSIS Tip: How to Check the Project or Package Protection Level
- Understanding and configuring the ProtectionLevel setting in SSIS is essential for maintaining security throughout the ETL process.
- To check the ProtectionLevel setting in SSIS:
- 1. Open your SSIS project in SQL Server Data Tools (SSDT) or SQL Server Management Studio (SSMS).
- 2. Right-click the project (or an individual package) and select Properties.
- 3. In the Properties window, locate the ProtectionLevel option, which determines how sensitive information is stored and secured.
- Common ProtectionLevel options include DontSaveSensitive, EncryptSensitiveWithUserKey, EncryptSensitiveWithPassword, EncryptAllWithPassword, EncryptAllWithUserKey, and ServerStorage.
- Best practices include using DontSaveSensitive for automated pipelines, EncryptSensitiveWithPassword for sharing packages between developers, and avoiding EncryptSensitiveWithUserKey for portability.
- For a detailed tutorial with screenshots and additional tips, refer to the full guide linked in the article.
Read Full Article
16 Likes
Tech Radar
285

Image Credit: Tech Radar
Hunting for early Prime Day deals? Beware, scammers have set up thousands of fake Amazon sites - here's what to look out for
- Hackers have set up thousands of fake websites posing as Amazon to steal login credentials and trick people into fraudulent purchases ahead of Prime Day.
- NordVPN's Threat Protection Pro team observed over 120,000 malicious websites mimicking Amazon, including 92,000 phishing sites, 21,000 malware sites, and 11,000 fake goods sites in the past two months.
- Consumers are advised to be cautious during Major shopping events like Prime Day as cybercriminals exploit shoppers' excitement for limited-time deals, making them more susceptible to cyber scams.
- Events such as Amazon Prime Day, Black Friday, and Cyber Monday are prime targets for cybercriminals, with a surge in malicious activities observed, including a significant rise in tricking people into making unauthorized payments.
Read Full Article
17 Likes
Tech Radar
355

Image Credit: Tech Radar
Hundreds of Android apps band together in massive scam campaign targeting millions - here's what we know
- A major ad fraud campaign involving hundreds of Android apps has been dismantled by security researchers.
- The campaign, known as IconAds, displayed ads without proper context or user consent and hid app icons on devices to avoid removal.
- The apps were removed from the Google Play Store after generating 1.2 billion bid requests daily at its peak.
- Although the malicious apps have been taken down, researchers anticipate new apps with similar fraudulent tactics to surface in the future.
Read Full Article
21 Likes
Tech Radar
134

Image Credit: Tech Radar
Venture capital giant IdeaLab confirms breach, says private data was stolen in attack
- IdeaLab, a technology startup incubator, confirmed a data breach where cybercriminals accessed its network and stole sensitive information.
- The breach affected current and former employees, support service contractors, and their dependents, with stolen data including names and 'variable data'.
- The ransomware group, Hunters International, claimed responsibility for the attack and published decryption keys for all victims, with the leaked archive containing 137,000 files.
- IdeaLab is offering affected individuals complimentary identity theft protection services and credit monitoring, while security experts speculate about the motives behind Hunters International's disbanding.
Read Full Article
8 Likes
Socprime
380

Image Credit: Socprime
CVE-2025-5777 Detection: A New Critical Vulnerability Dubbed “CitrixBleed 2” in NetScaler ADC Faces Exploitation Risk
- Critical security issue in NetScaler ADC, CVE-2025-5777, poses exploitation risk after being exploited.
- Vulnerability allows memory overflow, control flow alteration, potential DoS conditions; resembles CitrixBleed.
- CitrixBleed 2's exploitation involves data compromise, session token leakage, posing serious risks.
- Detection tools, rules, and AI are available to identify and mitigate CVE-2025-5777 risks.
Read Full Article
22 Likes
Medium
155
Image Credit: Medium
What Spotify Taught Me About Strategy, AI, and User Experience
- Spotify faces challenges such as providing bad recommendations and relying heavily on ads and subscriptions for revenue.
- Issues with user experience include buggy playback, repetitive songs, and unwanted podcasts.
- Proposed solutions include using smarter machine learning, dynamic pricing, and improving system stability.
- Recommendations also involve redesigning Spotify's user flow, leveraging ML engines like Vertex AI, and moving towards a retrieval and re-ranking approach.
Read Full Article
9 Likes
For uninterrupted reading, download the app