Cyber Security News
Hackersking
373

Image Credit: Hackersking
Permissionless Mic & Camera Access Using Chromium Browser
- A new type of phishing attack known as Permissionless Phishing Attack allows access to camera, microphone, and location without user permission.
- By using the Chromium flag --auto-accept-camera-and-mircophone-capture, websites can access camera and microphone automatically.
- Code snippets demonstrate how to capture camera and microphone without user prompts and continuously save camera snapshots using getUserMedia.
- The script sends image data to upload.php for saving and the /var/www/imgCapture folder collects captured images.
Read Full Article
22 Likes
Dev
403

Image Credit: Dev
I Built a Simple SQL Injection Test Tool (and Broke My Own Site in the Process 😅)
- Mohammad built a simple SQL injection test tool as part of his cybersecurity self-learning journey.
- The tool is a PHP script that injects common SQLi payloads into GET parameters to detect potential SQL injection patterns.
- While testing the tool on a WordPress site, Mohammad accidentally affected a plugin's query but didn't crash the site.
- Mohammad learned about reflective vs blind injection, server reactions to invalid queries, and the limitations of pattern matching for real detection.
Read Full Article
24 Likes
Medium
386

Image Credit: Medium
Thiel, Taiwan, and the Machinery of Fate
- Peter Thiel raises the concern of whether the West's advancement in AI could provoke China to invade Taiwan, a topic often overlooked in geopolitical discussions.
- Thiel suggests that AI could redefine power projection, especially in relation to Taiwan and its complex geopolitical entanglements.
- Thiel's discussions veer into eschatological themes, swapping strategic analysis for allegory, which could be dangerous if misconstrued as geopolitical thought.
- While Thiel acknowledges the evolving power dynamics due to AI, his approach lacks structural understanding and may oversimplify complex geopolitical realities.
Read Full Article
23 Likes
Medium
259

Image Credit: Medium
Privacy by Default: Powerful Principle, Poor Requirement
- Product specs often mention supporting privacy by default as a responsible practice, but it's more of an aspiration without clear specifics.
- Vague statements on privacy can lead to teams guessing, resulting in overengineering or missing crucial requirements.
- To make privacy by default actionable, specific rules should be established, behaviors defined, constraints outlined, prohibitions listed, and testability ensured.
- Ambiguity around privacy requirements can cause issues downstream with engineering, legal, QA, and end users, making clear and verifiable requirements essential.
Read Full Article
15 Likes
Insider
318

Image Credit: Insider
A notorious hacker group is now targeting the aviation industry, the FBI says
- The FBI has warned that the cybercriminal group Scattered Spider is targeting the aviation industry in the US and Canada by deceiving IT help desks into granting them access to sensitive data.
- Scattered Spider gained attention in 2023 for hacking MGM Resorts and Caesars Entertainment, using social engineering techniques to bypass multi-factor authentication and gain unauthorized access.
- The group focuses on large corporations and third-party IT providers within the airline ecosystem, aiming to steal sensitive data for extortion and deploying ransomware.
- Cybersecurity experts urge the aviation industry to tighten up help desk identity verification processes to prevent unauthorized access and social engineering attacks by groups like Scattered Spider.
Read Full Article
19 Likes
Dev
140

Image Credit: Dev
Vulnerability Assessment
- Vulnerability assessment is a crucial practice in modern cybersecurity for proactively identifying security vulnerabilities in systems, applications, networks, and databases.
- Importance of vulnerability assessment: Identifying misconfigurations, security risks like SQL Injection and XSS, assessing risk exposure, and promoting a DevSecOps culture.
- Common types of vulnerability assessment include network scans, host-based scans, application scans, database scans, and wireless scans.
- Key tools for vulnerability assessment include Qualys, Rapid7, and Tenable Nessus. Continuous and collaborative vulnerability assessments are essential for robust security.
Read Full Article
8 Likes
Siliconangle
85

Image Credit: Siliconangle
Code, community and the future: 13 takeaways from Open Source Summit NA
- Open Source Summit North America explored intersections of code, community, and change.
- Insights from thought leaders discussed AI tech's growth, open-source ROI, and observability solutions.
- Key takeaways included AI's impact, open-source ROI, observability enhancements, and security innovations.
Read Full Article
5 Likes
Securityaffairs
187

Image Credit: Securityaffairs
The FBI warns that Scattered Spider is now targeting the airline sector
- The FBI has issued a warning that the cybercrime group Scattered Spider is targeting the airline sector using social engineering techniques to gain access.
- Scattered Spider is focusing on large corporations and their third-party IT providers within the airline ecosystem, putting trusted vendors and contractors at risk.
- The cybercriminals steal data for extortion and deploy ransomware; FBI is collaborating with the aviation industry to combat these attacks and assist victims.
- Additionally, Unit 42 has warned about Muddled Libra targeting the aviation industry with advanced social engineering methods, while Google highlighted Scattered Spider's shift toward targeting U.S. companies after UK retailer attacks.
Read Full Article
11 Likes
TechBullion
42

Image Credit: TechBullion
Why Sliding Gate Operators Are Smart for Commercial Properties?
- Sliding gate operators offer automation, secure control, and cost-effectiveness for commercial properties like warehouses and office parks.
- They provide increased security by responding to access systems like RFID cards and keypads, minimizing human error and deterring forced entry.
- Sliding gates are adaptable to tight spaces, making them suitable for urban commercial buildings, and they can handle high-volume traffic efficiently.
- While initially costly, slide gate operators pay off in the long run by improving productivity, reducing security risks, and lasting for years with less maintenance.
Read Full Article
2 Likes
Ubergizmo
55

Image Credit: Ubergizmo
WhatsApp Banned From U.S. House Devices Over Security Concerns
- The U.S. House of Representatives has banned WhatsApp from all House-issued devices due to security concerns over data protection and transparency.
- WhatsApp was classified as a 'high risk' application, leading to its ban, because of insufficient transparency in data protection policies and security vulnerabilities.
- House staff are now advised to use more secure messaging services like Microsoft Teams, Amazon’s Wickr, Signal, Apple’s iMessage, and FaceTime as alternatives to WhatsApp.
- Meta, WhatsApp's parent company, disputed the ban, stating that WhatsApp offers stronger security features than some of the recommended alternatives.
Read Full Article
3 Likes
Tech Radar
148

Image Credit: Tech Radar
Mr Hamza, Mysterious Team Bangladesh, and Keynous+ led a massive surge in DDoS on US businesses following an attack on Iran
- A surge in Distributed Denial of Service (DDoS) attacks against U.S. businesses has been linked to the Israel-Iran conflict, with hacktivists redirecting their focus from Israel to America in a 48-hour escalation.
- Key groups involved in the DDoS attacks include Mr. Hamza, Mysterious Team Bangladesh, and Keynous+, with Mr. Hamza claiming over half of the attacks targeted at the U.S. Additionally, smaller groups like Team Fearless (PS) have contributed to this cyber hostility.
- The sectors targeted during the June 22 escalation included manufacturing, finance, and government, with a specific focus on military and aerospace production. This targeted approach suggests a calculated effort to disrupt core defense and economic infrastructures.
- The use of DDoS attacks as a disruptive tool poses challenges for online operations, highlighting the need for companies to enhance their cyber resilience and invest in robust security protocols, particularly DDoS protection.
Read Full Article
8 Likes
Tech Radar
29

Image Credit: Tech Radar
Microsoft is phasing out passwords soon – here's why passkeys are replacing them and what to do next
- Microsoft is phasing out saved passwords from its Authenticator app.
- Users will switch to passkeys, a safer login method tied to devices.
- This move aims to enhance security and combat cyberattacks more effectively.
- Passkeys, using biometrics or PIN, replace traditional passwords for authentication.
Read Full Article
1 Like
TechCrunch
174

Image Credit: TechCrunch
FBI, cybersecurity firms say a prolific hacking crew is now targeting airlines and the transportation sector
- The FBI and cybersecurity firms have warned that a hacking group known as Scattered Spider is targeting airlines and the transportation sector.
- Scattered Spider, comprised mainly of financially motivated English-speaking hackers, uses tactics like social engineering, phishing, and ransomware to steal data.
- The hackers may target large corporations and their IT providers in the airline ecosystem, putting airlines and associated vendors at risk.
- Recent intrusions have been reported by Hawaiian Airlines and WestJet, with the latter's cyberattack linked to Scattered Spider. This follows previous attacks on the retail sector and insurance industry.
Read Full Article
10 Likes
Securityaffairs
361
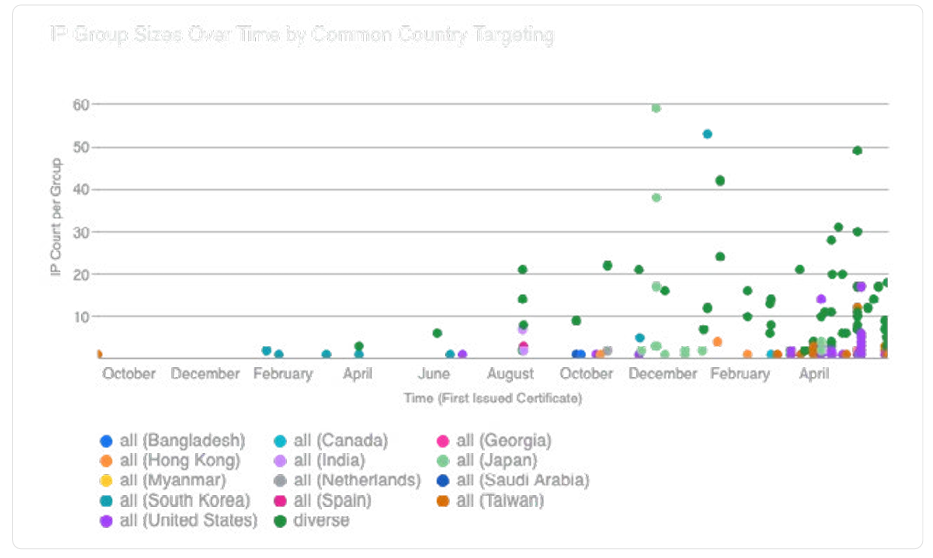
Image Credit: Securityaffairs
LapDogs: China-nexus hackers Hijack 1,000+ SOHO devices for espionage
- Over 1,000 SOHO devices hacked in China-linked LapDogs spying campaign for espionage.
- Security researchers uncover ORB network supporting long-term spying ops in U.S. and Asia.
- ShortLeash malware, targeting various hardware vendors, found hiding in compromised devices.
Read Full Article
21 Likes
Medium
302

Objective: To develop a strong foundational understanding of penetration testing by completing the…
- The article discusses the importance of developing a strong foundational understanding of penetration testing by covering topics such as reporting, types of testing (Black Box, Grey Box, White Box), and practical tests like the ACME assignment.
- Specific methodologies like OSSTMM, OWASP, NIST Cybersecurity Framework 1.1, and NCSC CAF are highlighted as part of the penetration testing process.
- A scenario involving exploiting a web server's IP address, gaining access to sensitive information, and escalating privileges from a normal user to root user/administrator is described, culminating in finding the root flag THM{PENTEST_COMPLETE}.
Read Full Article
18 Likes
For uninterrupted reading, download the app