Cyber Security News
Securityaffairs
291

Image Credit: Securityaffairs
Ahold Delhaize data breach affected over 2.2 Million individuals
- A ransomware attack on Ahold Delhaize led to a data breach affecting over 2.2 million individuals.
- The breach impacted various US subsidiaries of Ahold Delhaize, exposing personal information such as contact details, financial data, health information, and employment records.
- The company is offering the affected individuals two years of free credit monitoring and identity protection.
- In April 2025, the Inc Ransom group claimed responsibility for the cyberattack, stating that internal data was likely stolen and posted on their leak site.
Read Full Article
17 Likes
TechBullion
236

Image Credit: TechBullion
The Essential Role of Construction Site Security for Contractors and Developers
- Construction site security is crucial for protecting valuable equipment, materials, and personnel from theft, vandalism, and accidents.
- The UK construction industry incurs over £800 million annually in theft-related costs, emphasizing the vulnerability of construction sites.
- Investing in adequate construction site security helps reduce risks like delays, increased costs, and damage to a company's reputation.
- Security measures for construction sites include manned guarding, mobile patrols, CCTV monitoring, and tailored security solutions from professional security providers like All Time Security.
Read Full Article
14 Likes
VoIP
259

Image Credit: VoIP
Telefónica and Wiz Partner to Boost Multi-Cloud Security
- Telefónica Tech partners with Wiz to enhance multi-cloud security for organizations in Spain.
- Wiz’s comprehensive Cloud-Native Application Protection Platform (CNAPP) will be integrated into Telefónica Tech's portfolio, offering advanced security features such as incident detection and continuous monitoring.
- The collaboration aims to simplify security management in multi-cloud environments by providing complete visibility, identifying risks, and enabling preventative measures against threats.
- The partnership intends to facilitate organizations' transition to multi-cloud systems by optimizing security measures and protection against cyber threats, with Wiz's established presence in Fortune 100 companies.
Read Full Article
15 Likes
Medium
23

Tried Learning Data Science in 30 Days — Here’s What Actually Worked"
- The individual tried learning data science in 30 days through YouTube tutorials and free courses, but found the random approach led to burnout.
- They discovered the importance of following a structured learning path, focusing on Python basics, statistics, data visualization, and simple machine learning.
- Building a mini project analyzing COVID data using pandas and Seaborn helped in understanding concepts better through practical application.
- Key takeaways included daily focused learning, hands-on projects, following one structured roadmap, and tracking progress, emphasizing the need to avoid jumping between multiple courses and obsessing over tools.
Read Full Article
1 Like
TechJuice
338

Image Credit: TechJuice
GIFTEDCROOK Evolves Into Full-Blown Cyber-Espionage Weapon
- GIFTEDCROOK, a once mild browser data thief, has transformed into a potent cyber-espionage tool, transcending mere password theft.
- Upgraded versions of GIFTEDCROOK (1.2 and 1.3) now target sensitive files like PDFs and spreadsheets, filtering documents based on date and size.
- The malware infiltrates systems via emails posing as military documents, leveraging Excel macros to gather data discreetly and utilizes Telegram bots for exfiltration.
- With enhanced features like file scanning, encryption, and data exfiltration mechanisms, GIFTEDCROOK has escalated to a serious threat for high-level intel in defense and critical sectors.
Read Full Article
20 Likes
Dev
67

Image Credit: Dev
Mastering Input Filtering in PHP: A Guide to `filter_input` Techniques
- PHP's filter_input function simplifies input validation and sanitization in web development to prevent security vulnerabilities.
- Basic syntax of filter_input: filter_input(int $type, string $variable_name, int $filter = FILTER_DEFAULT, array|int $options = 0);
- Common filtering techniques include validating email input, sanitizing strings, validating integers, filtering URLs, using filter flags, and sanitizing and validating arrays.
- Pros of filter_input: built-in, easy to use, reduces manual validation; Cons: limited flexibility compared to custom validation libraries. Consider using libraries like Laravel Validator or Symfony’s Validator Component for complex validation.
Read Full Article
4 Likes
Securityaffairs
268
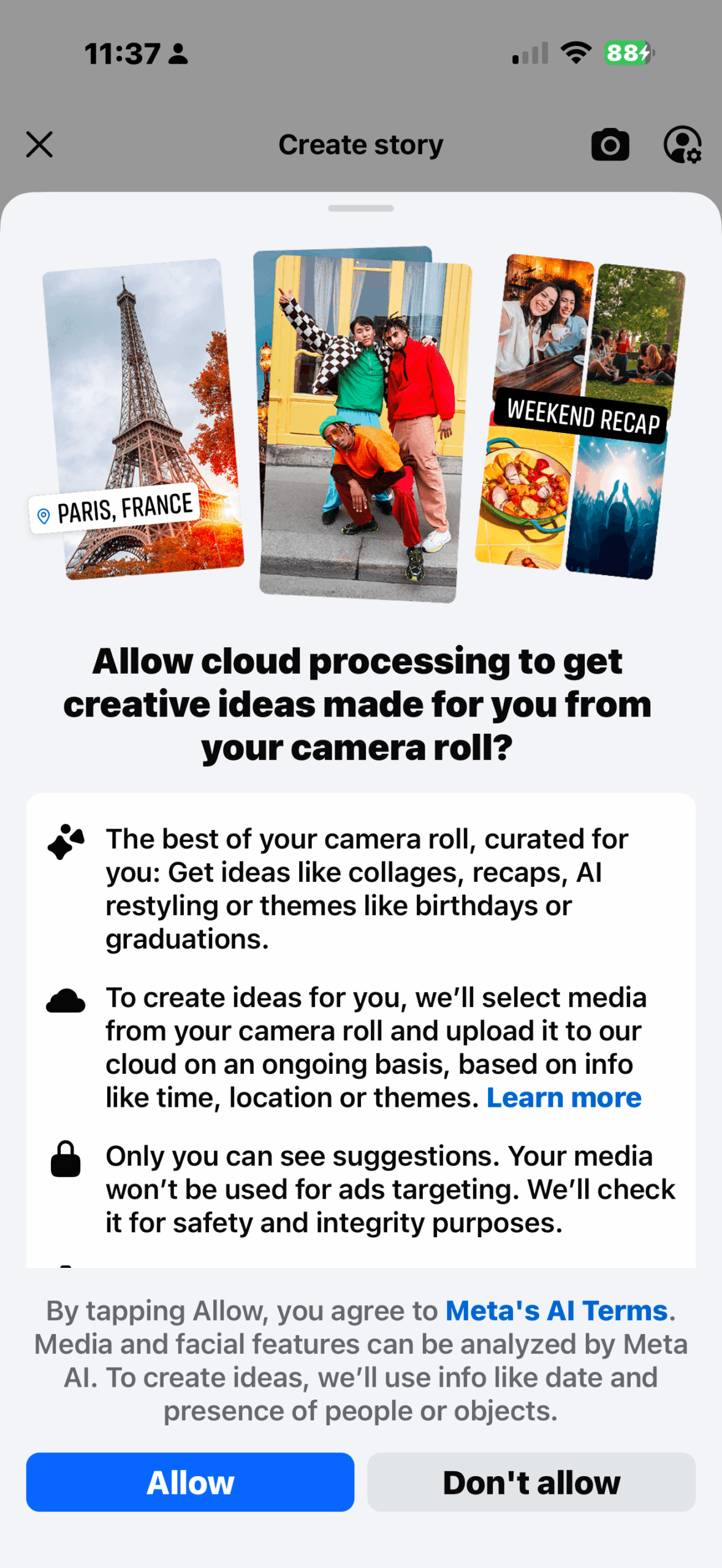
Image Credit: Securityaffairs
Facebook wants access to your camera roll for AI photo edits
- Facebook is asking users to enable 'cloud processing' to access photos from their phones, even those not uploaded.
- By opting into 'cloud processing,' Facebook can continuously upload media to its servers to generate creative suggestions using details like time, location, and theme.
- The new feature poses privacy concerns as users may unwittingly allow Meta to use their media for AI model training without clear consent.
- Meta states that AI-generated photo suggestions are private, not used for ads, and can be turned off at any time; the feature will initially be available only for users in Canada and the US.
Read Full Article
15 Likes
Gritdaily
25

Image Credit: Gritdaily
The Founders Betting Everything on Fixing Encryption Before AI and Quantum Break It
- Entrokey Labs, co-founded by Patrick Hearn and Eric Dresdale, aims to revolutionize cybersecurity by addressing the vulnerability of encryption keys due to lack of entropy.
- They have developed an AI-driven platform that generates high-entropy cryptographic keys using cosmic data, offering a software-only solution to enhance security.
- Entrokey's approach enables organizations to achieve post-quantum resilience without major infrastructure changes, integrating seamlessly with existing systems like OpenSSL and Keycloak.
- The founders emphasize the importance of adapting encryption to combat evolving threats posed by AI and quantum computing, advocating for smarter, flexible software solutions.
Read Full Article
1 Like
Pymnts
25

Image Credit: Pymnts
Scattered Spider Hackers Reportedly Targeting Airline Industry
- The FBI has warned about cyberattacks from the hacking group Scattered Spider targeting the air travel industry.
- Google’s Mandiant and Palo Alto Networks' Unit 42 also reported similar cyberattacks by Scattered Spider on the aviation sector.
- Scattered Spider, known for tactics like social engineering and phishing, has been behind major cyberattacks, including the MGM Casinos data breach and a recent attack on Marks & Spencer.
- The FBI stated that large corporations, their third-party IT providers, and anyone in the airline ecosystem could be at risk of cyberattacks by Scattered Spider.
Read Full Article
1 Like
VentureBeat
72

Image Credit: VentureBeat
Identity theft hits 1.1M reports — and authentication fatigue is only getting worse
- Authentication methods are varied - from 2FA to SSO to WebAuthn, causing confusion.
- Customers demand seamless yet secure experiences amidst rising identity theft reports.
- Businesses must balance security measures with user convenience to prevent customer alienation.
- Future of authentication lies in continuous signals and AI-driven risk-based processes.
Read Full Article
4 Likes
Securityaffairs
190

Image Credit: Securityaffairs
Security Affairs newsletter Round 530 by Pierluigi Paganini – INTERNATIONAL EDITION
- FBI warns of Scattered Spider targeting the airline sector
- China-nexus hackers hijack SOHO devices for espionage
- Critical ISE flaws in Cisco fixed
- Various cyberattacks and data breaches reported worldwide
Read Full Article
11 Likes
The Fintech Times
135

Image Credit: The Fintech Times
Checkout.com: To Thrive and Combat Against Growing Fraud, Firms Must Invest in Education
- Checkout.com has extended its partnership with the Merchant Risk Council to combat digital fraud complexities and payment risk.
- Research shows a significant impact of fraud on the global population, with both consumers and firms experiencing an increase in fraudulent activities.
- The partnership aims to invest in educational programs like Payments Essentials and Fraud Essentials to equip professionals with skills in fraud prevention and secure payment infrastructures.
- Checkout.com advocates for education as a key strategy to prevent fraud and has appointed representatives to the Merchant Risk Council's regional advisory boards to enhance fraud prevention practices.
Read Full Article
8 Likes
Tech Radar
33

Image Credit: Tech Radar
China-backed "LapDogs" hackers hijacked hundreds of devices in an outlandish intel campaign aimed at US and Asian targets
- A cyber espionage operation called LapDogs, reportedly linked to China-aligned threat actors, targeted devices in multiple countries including the US, Japan, South Korea, Taiwan, and Hong Kong.
- The operation involved hijacking SOHO routers and IoT devices, turning them into Operational Relay Boxes (ORBs) for extended surveillance.
- The hackers used a custom backdoor named ShortLeash to gain root-level access and remain undetected in compromised devices, with some devices acting as gateways to infiltrate internal networks.
- SecurityScorecard highlighted LapDogs' strategic and geo-targeted approach, emphasizing the challenge in detecting the malware due to the spoofing of legitimate security certificates.
Read Full Article
2 Likes
TechBullion
180

Image Credit: TechBullion
Improve Productivity with Outsourced IT Support Services
- Outsourced IT Support boosts productivity and efficiency for businesses of all sizes.
- It offers cost-effective solutions, proactive monitoring, and access to a full expert team.
- Managed IT Services prevent issues, freeing internal staff to focus on core tasks.
- Outsourcing IT keeps systems updated, secure, and scalable to support business growth.
- Investing in IT support ensures smoother operations, less downtime, and enhanced cybersecurity.
Read Full Article
8 Likes
Medium
99

What Is JA3? The Silent Fingerprint Behind Every HTTPS Connection
- JA3 is a method to create a unique fingerprint of how a client behaves at the TLS level by encoding raw data and hashing it using MD5.
- It is useful for bot and malware detection, application fingerprinting, and fraud analytics by distinguishing TLS handshakes and behaviors.
- JA3 serializes fields into a comma-separated string and produces a unique hash representing the client's TLS negotiation process.
- Cloudflare WAF uses JA3 to protect sensitive API endpoints with multiple filters.
Read Full Article
5 Likes
For uninterrupted reading, download the app