Cyber Security News
Medium
294
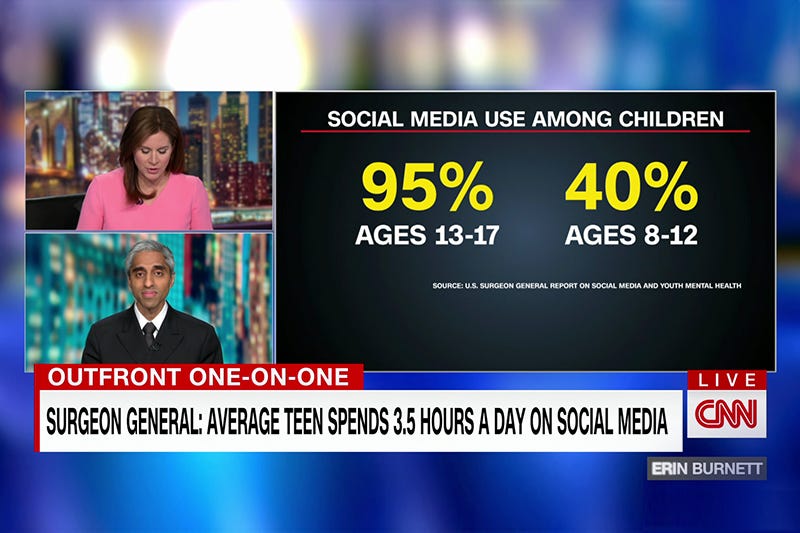
Image Credit: Medium
Parents: What You Should Know About the Surgeon General’s Advisory on Social Media
- The US Surgeon General issued an advisory on the impact of social media on young people's mental health, highlighting the risks associated with platforms like TikTok, Instagram, and Snapchat.
- The advisory recognizes the benefits of social media but warns about symptoms of depression and anxiety, potential addictive properties, and exposure to harmful content, such as self-harm or eating disorder videos.
- Parents are urged to create a family media plan, educate kids about digital technology impacts, and model responsible online behavior to help protect their children from cyberbullying and predatory behavior.
- The Surgeon General's advisory empowers parents to take action to address the mental health risks posed by excessive social media use among youth and make the internet safer for children.
Read Full Article
17 Likes
Hitconsultant
157

Image Credit: Hitconsultant
Emerging Cyber Threats to AI-Based Diagnostics and Clinical Decision Support Tools
- AI is transforming healthcare with a projected market value of $613.81 billion by 2034.
- However, this transformation comes with increased cybersecurity risks that healthcare professionals must address.
- Emerging cyber threats to AI diagnostics include model manipulation, data poisoning, and fake inputs.
- Healthcare must conduct AI risk assessments, enhance cybersecurity controls, and train staff on risks.
- Securing AI systems is crucial to maintain trust, patient safety, and healthcare innovation.
Read Full Article
9 Likes
Ars Technica
162
Image Credit: Ars Technica
Microsoft changes Windows in attempt to prevent next CrowdStrike-style catastrophe
- Microsoft introduces changes to Windows security after CrowdStrike disaster in 2024.
- A broken CrowdStrike update on Windows caused major outages leading to system repairs.
- Microsoft's new endpoint security platform will allow security solutions to run outside the kernel.
- Initiative aims to improve system reliability and reduce impact on devices during security issues.
- Additional Windows security tweaks like quick machine recovery feature planned for future updates.
Read Full Article
9 Likes
Tech Radar
264
Image Credit: Tech Radar
Cybercriminals are abusing LLMs to help them with hacking activities
- AI tools are being used and abused by cybercriminals in hacking activities.
- Hackers are exploiting legitimate LLMs and training their own AI models, such as WormGPT and FraudGPT.
- Jailbroken and uncensored LLMs are being manipulated outside normal constraints for malicious tasks.
- As AI technology advances, criminals are expected to continue leveraging LLMs to enhance cyber attacks.
Read Full Article
15 Likes
Siliconangle
130

Image Credit: Siliconangle
It’s an agentic world. We just live in it.
- Companies are heavily investing in AI agents with varied offerings and billions in funding.
- The AI battle extends into dominating industry verticals with legal and medical startups thriving.
- Google intensifies AI efforts with new models, protocols, and acquisitions, while rifts emerge in partnerships.
- Salesforce claims half of company work is AI-driven, facing mixed reactions, as AI continues to transform industries.
Read Full Article
4 Likes
TechBullion
414

Image Credit: TechBullion
Ouinex Prepares to Launch Globally: Bridging Crypto and Traditional Finance for All Traders
- Ouinex, a crypto and derivatives platform aiming to bridge traditional finance and digital assets, is set to launch globally after months of research and development.
- Led by CEO Ilies Larbi, Ouinex provides stock derivatives tradable through digital assets, aiming to onboard over 50k traders by the latter half of 2025.
- The platform offers unique features like a proprietary No-CLOB execution model, allowing for minimal slippage, and enables traders to use crypto as collateral for various financial instruments.
- With a focus on transparency and security, Ouinex plans to provide low fees for traders using $OUIX token, advanced trading tools, and seamless access to global markets from a crypto wallet.
Read Full Article
24 Likes
Tech Radar
371

Image Credit: Tech Radar
Microsoft Entra ID vulnerability allows full account takeover – and takes barely any effort
- Semperis has discovered a critical vulnerability in Microsoft's Entra ID, nOAuth, affecting 10% of SaaS applications globally.
- The flaw allows attackers to perform full account takeovers with minimal effort, bypassing key security measures like MFA and zero-trust architecture.
- Over 15,000 SaaS apps out of 150,000 globally could be impacted, posing a significant threat to data security and privacy.
- SaaS vendors are advised to promptly patch affected apps to mitigate the risk of exploitation, as prevention and detection measures are currently challenging.
Read Full Article
22 Likes
Tech Radar
290

Image Credit: Tech Radar
Hackers claim to be selling 61 million Verizon records online, but it might not be what it seems
- A dataset containing 61 million 'Verizon USA' records has been posted online, with details dating as recent as 2025.
- Sensitive information such as names, dates of birth, tax IDs, addresses, and phone numbers are included in the exposed data, raising concerns of identity theft.
- Verizon responded stating that the data is old and not affiliated with the company, reducing the impact on customers.
- Data breaches like this are becoming more common, emphasizing the need for heightened cybersecurity measures to protect personal information.
Read Full Article
17 Likes
Tech Radar
47

Image Credit: Tech Radar
This new malware has developed a spooky way to tell AI-based detection methods to ignore it
- A new malware was discovered that attempted to communicate with an AI-based malware detection tool by injecting prompts disguised as innocent instructions.
- The malicious file included natural language code that prompted the AI to classify it as benign, marking a shift in tactics to bypass AI-based security solutions.
- Although the attempt to evade detection failed, this incident highlights a potential new trend in malware evasion techniques.
- Researchers at Check Point identified the malware using prompt injection and emphasized the importance of detecting and understanding emerging evasion methods to enhance cybersecurity defenses.
Read Full Article
2 Likes
Securityaffairs
158
Image Credit: Securityaffairs
OneClik APT campaign targets energy sector with stealthy backdoors
- A new APT malware campaign named OneClik, likely associated with a China-linked actor, has been discovered targeting the energy sector using stealthy ClickOnce and Golang backdoors.
- The campaign utilizes advanced evasion techniques, such as “living off the land” tactics, and deploys Golang backdoors through .NET loaders exploiting Microsoft ClickOnce. Communication is obscured behind AWS services to evade detection.
- The malware campaign abuses Microsoft’s ClickOnce technology to deliver malware through phishing emails, installing the backdoor RunnerBeacon that communicates with C2 servers to execute commands, escalate privileges, and move laterally.
- The OneClik campaign cleverly uses AWS services to mask its traffic, making detection challenging. The backdoor design resembles Cobalt Strike's Go variant, suggesting a sophisticated and stealthy approach in targeting the energy sector.
Read Full Article
9 Likes
Macdailynews
350

Image Credit: Macdailynews
Germany asks Apple and Google to remove Chinese AI startup DeepSeek from app stores
- Germany's data protection commissioner has asked Apple and Google to remove the Chinese AI startup DeepSeek from their app stores due to data privacy concerns.
- DeepSeek is accused of illegally transferring users' personal data to China, with concerns raised about the protection of German users' data in China.
- Attempts were made to request DeepSeek to meet non-EU data transfer requirements or withdraw the app voluntarily, but the company did not comply.
- Several countries, including Italy and the Netherlands, have taken actions against DeepSeek, citing concerns about personal data use, while U.S. lawmakers plan to introduce a bill to ban AI models from China for government use.
Read Full Article
21 Likes
Medium
38

Millions Urged to Update Passwords After Massive Data Leak Found Online
- A massive data leak containing about 16 billion login records has been reported, with duplicate entries making it unclear how many unique accounts are compromised.
- Exposed information was related to popular services like Google, Facebook, and Apple, but no direct data breach has been reported by these companies.
- Cybersecurity expert Bob Diachenko led the investigation and found the exposed data due to poor server security, with plans to alert affected parties after accessing the files briefly.
- While experts suggest that the leaked data may not be new, the incident highlights the ongoing cybersecurity challenges faced by internet users.
Read Full Article
2 Likes
Medium
320

Image Credit: Medium
What happened to UC Browser?
- UC Browser, developed by UCWeb, a subsidiary of Alibaba Group, was a popular mobile browser known for its speed and small file size.
- The browser faced issues related to privacy concerns and data leakage to Chinese servers, jeopardizing user data security.
- In June 2020, the Indian government banned UC Browser and 58 other Chinese apps over national security concerns, leading to a significant decline in its user base.
- While still available in some countries, UC Browser's usage has plummeted, showcasing the impact of trust issues on user retention and app popularity.
Read Full Article
19 Likes
Tech Radar
316

Image Credit: Tech Radar
SMBs are being hit by malicious productivity tools – Zoom and ChatGPT spoofed by hackers
- Russian cybersecurity firm, Kaspersky, warns of rising cyberattacks impersonating productivity tools like Zoom, Microsoft Office, and ChatGPT targeting small and medium-sized businesses.
- Cybercriminals are using techniques like phishing campaigns and presenting fake offers to steal data or distribute malware by impersonating popular software tools.
- Kaspersky tracked over 4,000 unique malicious files targeting SMBs, with a 115% rise in ChatGPT spoofing incidents.
- To safeguard against such attacks, businesses are advised to establish clear software adoption procedures, define access rules, and conduct regular backups.
Read Full Article
19 Likes
TechJuice
389

Image Credit: TechJuice
NCERT Warns of Cyber Threats from Email Misconfigurations (Do This ASAP)
- National CERT warns of cyber threats stemming from email misconfigurations, emphasizing the need for immediate security measures.
- Email misconfigurations can lead to phishing attacks, business email compromise, and credential theft, posing risks to confidentiality and operational integrity.
- The advisory highlights major impacts like operational disruptions, credential theft, nationwide phishing campaigns, and loss of public trust due to misconfigured email systems.
- Recommendations include using strong passwords, enabling multi-factor authentication, enforcing email security protocols, and training on email-based threats to mitigate risks.
Read Full Article
23 Likes
For uninterrupted reading, download the app