Cyber Security News
Tech Radar
295
Image Credit: Tech Radar
FBI warns Scattered Spider hackers are now going after airlines
- The FBI has warned that the Scattered Spider cybercriminals are now targeting US airlines and transportation, following attacks on UK retailers in the past.
- The group, known for causing system outages and deploying ransomware, consists of financially motivated young adults using phishing and social engineering techniques.
- Two airlines, Hawaiian Airlines and Canada's WestJet, reported cyber incidents in June 2025, potentially linked to Scattered Spider's activities.
- The FBI advises vigilance for anyone in the airline ecosystem, as the group could target direct organizations or breach supply chain third-parties for access.
Read Full Article
17 Likes
TechBullion
1.1k

Image Credit: TechBullion
AI and Security: What’s Coming Next in the 2024 Tech Frontier?
- 2024 is witnessing groundbreaking shifts at the intersection of artificial intelligence (AI) and cybersecurity, with the fusion of predictive AI and security frameworks reshaping how organizations protect digital assets.
- Key advancements in 2024 include the evolution of AI-driven autonomous defense systems, secure multi-agent AI collaboration, AI governance integration for regulatory compliance, and development of quantum-resilient AI encryption.
- The evolution of AI-driven autonomous defense systems marks a shift from reactive to proactive cybersecurity, while protocols for secure collaboration among AI agents are being developed to protect against potential attacks.
- With AI becoming a critical actor in the security landscape, 2024 emphasizes the importance of embedding ethics, governance, and resilience into AI security strategies for forward-thinking organizations.
Read Full Article
20 Likes
Siliconangle
88

Image Credit: Siliconangle
Legit Security launches MCP Server to secure AI-generated code
- Legit Security Ltd. launches Legit MCP Server to bring real-time application security posture management to AI-led software development.
- Legit MCP Server enables AI code assistants like GitHub Copilot to evaluate security, enforce policy guardrails, and drive automatic remediation processes.
- The offering addresses security risks posed by AI-generated code, providing security feedback in natural language to developers without additional learning curve.
- The new feature ensures AI-generated code is scanned, assessed, and remediated in real time, benefiting developers, security teams, and overall organizational quality and compliance.
Read Full Article
5 Likes
Siliconangle
315

Image Credit: Siliconangle
Thales finds enterprises losing ground in race to secure AI and cloud
- Thales SA warns that enterprise security strategies are struggling to keep pace with the complexity of cloud environments and the demands of artificial intelligence.
- The 2025 Thales Cloud Security Study shows that security teams are overwhelmed by operational complexity, fragmented tools, and increased data flow through AI systems in multicloud and SaaS environments.
- Cloud security remains a top priority for enterprises, with AI security investments displacing traditional security spending, and tool sprawl compounding the issue with the average enterprise using 2.1 public cloud providers and 85 SaaS applications.
- The study reveals that the risks are real as stolen credentials and cloud-based assets are top targets for cyberattacks, emphasizing the need for organizations to improve data protection strategies in their digital infrastructure.
Read Full Article
18 Likes
Securityaffairs
16

Image Credit: Securityaffairs
Canada bans Hikvision over national security concerns
- Canada has banned Chinese surveillance firm Hikvision due to national security concerns, ordering the company to cease operations in the country and prohibiting its products from government use.
- The ban includes a national security review under the Investment Canada Act, and Canada is assessing existing properties to ensure no legacy Hikvision products are used going forward.
- Hikvision Canada criticized the ban, calling it baseless and politically motivated, emphasizing that its products comply with Canadian laws and security standards.
- The US and UK have also taken actions against Chinese technology companies in the past due to national security risks, including bans on Hikvision's products.
Read Full Article
1 Like
Dev
316

Image Credit: Dev
Mastering Your Digital Privacy: A Comprehensive Guide to Online Protection
- Digital privacy is crucial in our data-driven society for individuals' protection online.
- It involves controlling personal data access and understanding the difference from data security.
- Threats like breaches, surveillance, identity theft highlight the importance of digital privacy.
- Corporations use diverse data collection practices with ethics and legal considerations.
- Global privacy laws like GDPR impose strict regulations on data processing organizations.
Read Full Article
19 Likes
Tech Radar
135

Image Credit: Tech Radar
Supermarket giant admits 2.2 million people could be hit by worrying data breach - what to do if you're affected
- Ahold Delhaize, a food retail giant, has disclosed a data breach affecting over 2.2 million individuals, with stolen data including sensitive personal information.
- The stolen data includes a range of personal details such as full names, addresses, government ID numbers, and health information.
- A group named INC Ransom has claimed responsibility for the attack, but it remains unclear if customers were specifically targeted.
- Ahold Delhaize is offering free credit monitoring and identity theft protection services to those affected by the breach, with ongoing investigations into the incident.
Read Full Article
8 Likes
TechBullion
304

Image Credit: TechBullion
MUTM Might Be the Real Meme Slayer Of 2025, Outperforming DOGE and PEPE
- In June 2025, meme coins like Dogecoin (DOGE) and Shiba Inu (SHIB) experienced a significant decline in value, leading investors to turn towards utility-based coins for growth.
- Mutuum Finance (MUTM), a decentralized finance protocol, has raised over $11.3 million in its presale with increasing token prices leading up to the listing price of $0.06.
- Analysts predict a potential 29x increase in MUTM token value post-launch, attributing their optimism to the project's utility-based nature and CertiK audit score of 95.
- Mutuum Finance (MUTM) announced a $50,000 Bug Bounty Program in partnership with CertiK to incentivize security experts in identifying and reporting bugs, aiming to ensure platform security.
Read Full Article
18 Likes
Tech Radar
418

Image Credit: Tech Radar
Hawaiian Airlines says it was hit by ‘cybersecurity event’ - but flyers should be safe
- Hawaiian Airlines reported a recent cybersecurity incident that did not impact flights or passenger safety.
- The airline filed an 8-K form with the SEC alerting about the security incident on June 23, 2025.
- Security experts speculate that the attack may have been carried out by Scattered Spider, a hacking collective known for targeting US-based organizations.
- Hawaiian Airlines stated that its flights are operating safely, and the financial impact of the incident is yet to be determined.
Read Full Article
25 Likes
Tech Radar
287

Image Credit: Tech Radar
Hacker pleads guilty to breaching company networks to pitch his own services
- Nicholas Michael Kloster, a man from Kansas, pleaded guilty to hacking multiple organizations, including a health club, nonprofit, and former employer, to promote his own cybersecurity services.
- Kloster accessed the organizations' systems using various methods, such as breaching a restricted area at a gym and using a boot disk to bypass authentication into a nonprofit's systems.
- He offered consulting services to prevent future cyberattacks after claiming responsibility for the breaches and stole credit card data to buy hacking tools.
- Kloster faces potential consequences of up to five years in federal prison without parole, a fine of up to $250,000, supervised release, and restitution. The FBI's involvement suggests serious punishment.
Read Full Article
17 Likes
Securityaffairs
211
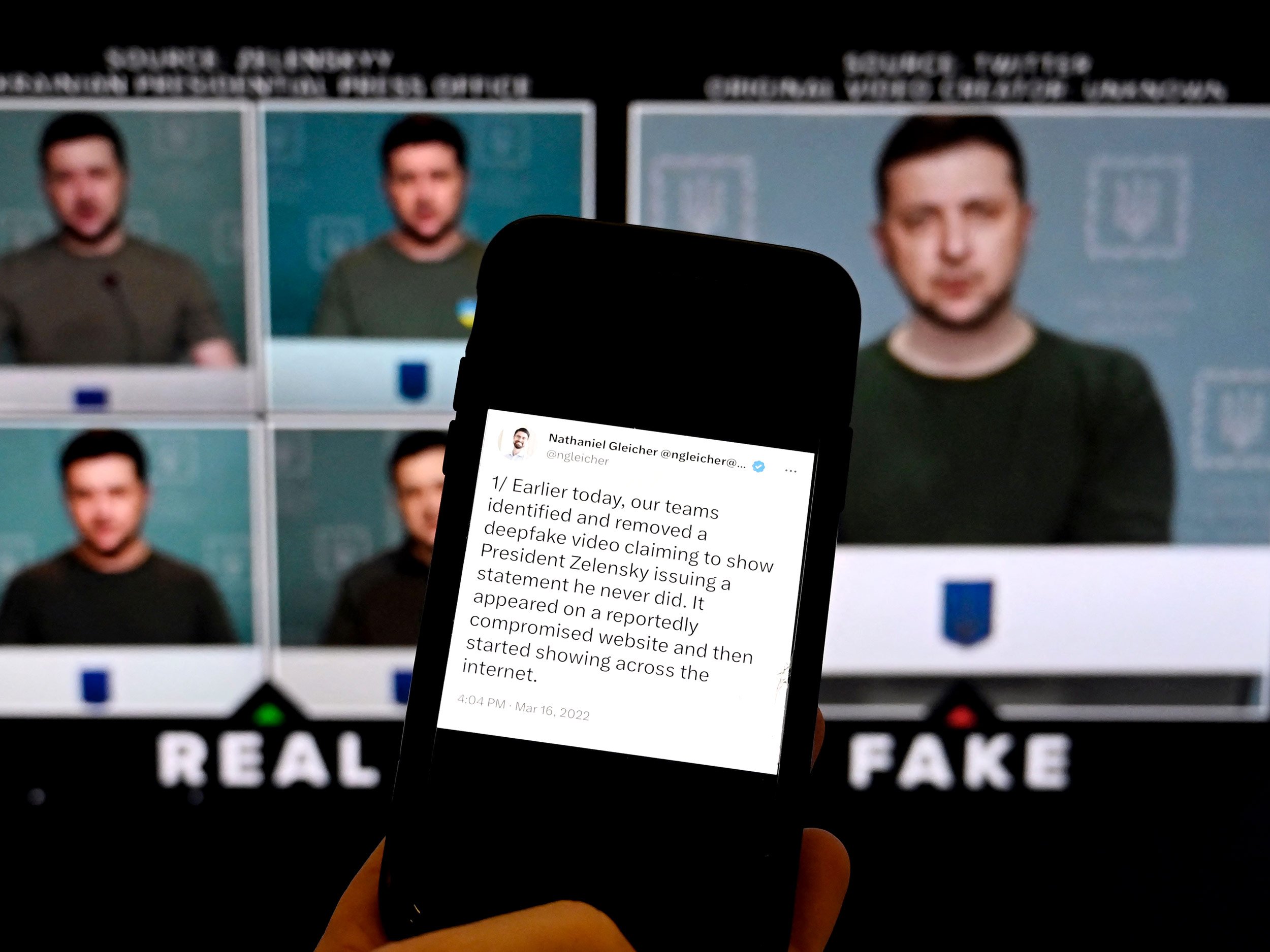
Image Credit: Securityaffairs
Denmark moves to protect personal identity from deepfakes with new copyright law
- Denmark plans to amend its copyright law to give individuals rights over their body, face, and voice to combat AI-generated deepfakes, believed to be the first law of its kind in Europe.
- The proposed law aims to protect individuals from being exploited by generative AI by allowing them to copyright their identity, with support from around 90% of MPs.
- The new law in Denmark will ban realistic AI-generated imitations of artists' performances without consent, with compensation for victims, excluding parody and satire.
- Denmark's Culture Minister emphasized the importance of protecting everyone's right to their own body, voice, and facial features, and plans to push similar initiatives across the EU.
Read Full Article
12 Likes
The Verge
291

Image Credit: The Verge
Hundreds of Brother printer models have an unpatchable security flaw
- Hundreds of Brother printer models have been found to have serious security flaws allowing attackers to remotely access devices still using default passwords.
- Eight new vulnerabilities were discovered in 689 Brother printers by security company Rapid7, with one flaw that cannot be fixed by patching the firmware.
- Brother has recommended users to change the default admin password via the device’s Web-Based Management menu for affected models.
- While most flaws can be fixed through firmware updates, the most critical flaw, CVE-2024-51978, will be addressed in future printer versions due to manufacturing changes.
Read Full Article
17 Likes
TechJuice
384

Image Credit: TechJuice
Germany Israel Cyber Dome: A Risky Bet or Europe’s Cyber Savior?
- Germany and Israel have launched a bold initiative called the Germany-Israel cyber dome to combat rising cyber threats in Europe.
- The project involves a joint German-Israeli cyber research center to enhance collaboration between the two nations' intelligence and security services.
- The cyber dome is part of Germany's broader defense plans as it seeks to strengthen its capabilities in the face of evolving security challenges.
- The initiative symbolizes a strategic bet that a combined cyber force can mitigate cyber risks, but its effectiveness and long-term impact remain uncertain.
Read Full Article
23 Likes
TechJuice
80

Image Credit: TechJuice
Cybercrime Gang in Multan Busted for WhatsApp Scams and JazzCash Fraud
- The National Cyber Crime Investigation Agency (NCCIA) dismantled a cybercrime gang in Multan accused of WhatsApp scams and JazzCash fraud.
- Six individuals were arrested in a targeted operation in Multan's Dunyapur area for allegedly defrauding people both domestically and internationally.
- The gang operated by creating fake WhatsApp accounts, using false identities on Facebook, and exploiting platforms like JazzCash for fraudulent activities.
- Legal proceedings are in progress against the arrested suspects, and efforts are being made to investigate the misuse of JazzCash by reaching out to the platform for an official comment.
Read Full Article
4 Likes
TechJuice
333

Image Credit: TechJuice
Cybercrime Gang in Multan Busted for WhatsApp Scams and Payment Transfer Fraud
- The National Cyber Crime Investigation Agency (NCCIA) has dismantled a cybercrime gang in Multan accused of orchestrating WhatsApp scams and payment transfer fraud.
- The operation led to the arrest of six individuals and seizure of six mobile phones suspected to hold key evidence of the gang’s activities.
- The gang operated by luring victims through fake WhatsApp accounts and false identities on Facebook to obtain personal information and cash transfers.
- A FIR has been lodged against the suspects, and legal proceedings are in progress. The agency is also seeking comments from payment platforms affected by the fraud.
Read Full Article
20 Likes
For uninterrupted reading, download the app