Cyber Security News
Siliconangle
433

Image Credit: Siliconangle
Cyolo updates privileged access platform with tools to monitor unmanaged vendor connections
- Cyolo updates its Cyolo PRO platform with new capabilities to enhance visibility, security, and operational agility in industrial and cyber-physical environments.
- The update includes Third-Party VPN Control feature for enforcing access policies over vendor-managed VPNs without changes to existing infrastructure.
- Cyolo addresses the challenge of governing external VPNs and access gateways used by third-party vendors, reducing risks and providing policy enforcement.
- The new update also introduces features like Instant Collaboration Link for secure external participant invitations and Secure Remote Assistance for secure technical support.
- Cyolo PRO now includes Asset Access Hub for unified asset management and role-based access assignment in complex environments.
- The company aims to make OT and CPS access more agile, secure, and seamless for administrators and end users, without disrupting vendor workflows.
- Co-founder Almog Apirion emphasizes the importance of managing third-party vendor access securely in industrial operations and critical infrastructure.
- Cyolo, a venture capital-backed startup, has raised $85.2 million in funding over four rounds from investors like National Grid Partners Inc. and others.
Read Full Article
26 Likes
Siliconangle
433
Image Credit: Siliconangle
Operant AI expands Gatekeeper platform with MCP Gateway for AI runtime security
- Operant AI Inc. expands its Gatekeeper platform with MCP Gateway for AI runtime security.
- MCP Gateway is designed to secure Model Context Protocol applications by offering real-time discovery, detection, and defense for all layers of the MCP stack.
- MCP is an open-source framework facilitating communication between AI agents and tools during runtime for enhanced workflows.
- Operant AI addresses security challenges arising from the widespread adoption of MCP in enterprise environments.
- MCP Gateway provides security, governance, and visibility to ensure secure operation of AI systems.
- It helps organizations manage AI agents securely throughout the lifecycle, from development to deployment.
- Key features of MCP Gateway include MCP Discovery for real-time cataloging, MCP Detections for threat detection, and MCP Defense for real-time protection.
- MCP Discovery catalogs tools and agents across local and cloud environments to enhance visibility and expose access patterns.
- MCP Detections offer advanced threat detection for sensitive data leaks, agentic AI threats, and vulnerabilities in MCP servers.
- MCP Defense enforces trust zones, blocks unverified tools, and prevents data leaks through flow controls and redaction.
- Operant collaborates with MCP vendors and AI tool providers through an ecosystem partnership program to enhance security in the MCP landscape.
- MCP Gateway is now part of Operant's AI Gatekeeper platform with integration support for existing MCP servers and AI agent deployments.
Read Full Article
26 Likes
Tech Radar
190

Image Credit: Tech Radar
Your least-favorite browser finally added a proper password manager, and it could be a massive game-changer for secure business credential sharing
- Microsoft Edge has introduced a new secure password deployment feature for Business users.
- The tool is available for Microsoft 365 Business Premium, E3, and E5 subscription options.
- It prevents passwords from being shared incorrectly and allows for secure credential sharing within organizations.
- Users can autofill passwords on authorized websites but cannot view, edit, delete, or export them.
- Passwords stored in the tool are encrypted using Microsoft Information Protection SDK.
- Admins can apply granular configurations for users or user groups through the Microsoft 365 admin center.
- The tool helps in aligning with Zero Trust principles and compliance requirements.
Read Full Article
11 Likes
Cheapsslshop
269
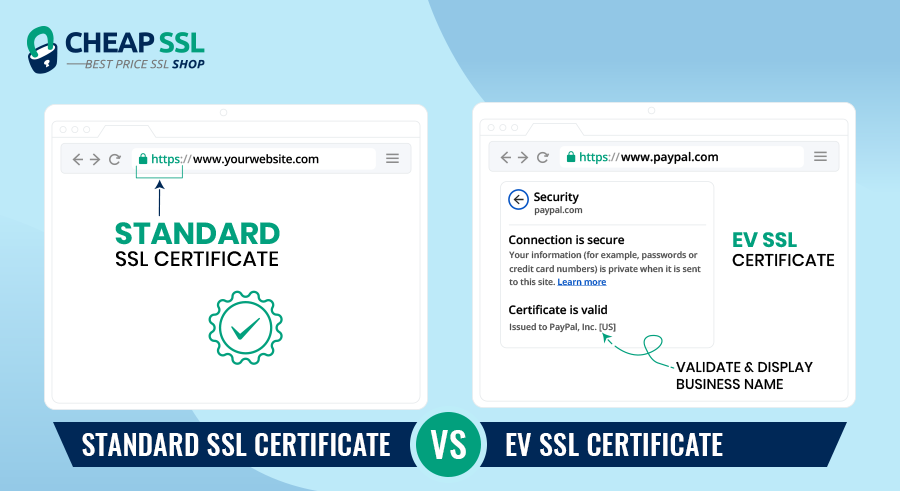
Image Credit: Cheapsslshop
Standard SSL vs EV SSL: Which SSL Certificate Should You Get?
- SSL is essential for website security, browser trust, and user confidence.
- SSL certificates are necessary as the digital landscape advances.
- Choice between types of SSL certificates like Standard SSL vs EV SSL is vital for site owners.
- Two commonly compared SSL certificates are Standard SSL and EV SSL.
- Difference in validation levels makes choosing the right SSL crucial.
- While both encrypt data, they vary in verifying the website's identity.
- Choosing between DV SSL and EV SSL depends on several factors.
- This guide helps in understanding the distinctions and selecting the suitable certificate.
- Standard SSL authenticates domain ownership and ensures a secure connection.
- It is issued by a trusted Certificate Authority to protect data from interception and tampering.
- Understanding the differences between EV and standard SSL certificates is essential for decision-making.
- EV SSL certificates offer extended validation, providing higher trust and credibility.
- EV SSL is beneficial for increasing user trust and reassuring website legitimacy.
- Consider factors like trust level, budget, and user perception when choosing between SSL options.
- Deciding the appropriate SSL certificate type is crucial for website security and user trust.
- Selecting the right SSL certificate enhances data protection and improves website credibility.
Read Full Article
16 Likes
Dev
291

Image Credit: Dev
Your Network Might Already Be Compromised If You Are Still Using 2022 Security Playbooks
- Network security is becoming increasingly crucial in 2025 as AI-powered attacks outpace legacy defenses.
- Zero Trust is now considered the minimum standard for security.
- Cloud misconfigurations remain a top cause of breaches.
- Deepfakes and AI-generated phishing attacks are becoming more sophisticated.
- Regulatory frameworks like the EU's AI Act are influencing compliance requirements.
- The traditional network perimeter has vanished, with networks now spanning across various endpoints, cloud services, remote teams, and third-party tools.
- Developers need to be more cognizant of network security as their involvement in code that interacts with sensitive data or third-party APIs exposes them to security risks.
- AI, automation, and visibility are integral for defenders to combat automated and scaled attacks effectively.
- A free webinar is available to delve deeper into these network security challenges.
Read Full Article
17 Likes
TechBullion
300

Image Credit: TechBullion
Breaking News: Only 17% of Organizations Can Actually Stop AI Data Leaks, Kiteworks Survey Reveals
- A survey by Kiteworks reveals that only 17% of organizations have technical controls in place to prevent AI data leaks.
- 27% of organizations admit that over 30% of the data fed into AI tools is private or confidential.
- The survey highlights a significant gap between AI adoption speed and security readiness, posing a potential data breach crisis.
- Kiteworks executives discuss the challenges of traditional security approaches with AI, emphasizing the need for technical protection over hope-based strategies.
- Organizations are blind to the risks of data exposure through AI ingestion, with 44% operating without visibility over their sensitive data.
- Legal firms face challenges leveraging AI efficiency while maintaining confidentiality, exemplifying the struggle in implementing effective AI security measures.
- Prevention at the point of entry is highlighted as the most effective strategy to mitigate AI data leaks, as organizations focus on output monitoring rather than input controls.
- Many organizations are overwhelmed by rapid regulatory changes regarding AI data flows, underestimating the potential consequences of non-compliance.
- The survey points out a fundamental failure in technology adoption across industries, with organizations equally vulnerable to AI-related attacks and breaches.
- Successful AI adoption requires a balance between innovation and security, with technical controls playing a critical role in enabling safe experimentation and protection.
Read Full Article
18 Likes
Socprime
0

Image Credit: Socprime
CVE-2025-4123 Vulnerability: “The Grafana Ghost” Zero-Day Enables Malicious Account Hijacking
- A zero-day vulnerability (CVE-2025-4123) in Grafana, a popular analytics platform, allows malicious account hijacking.
- Despite a fix being available, over 46,500 instances of Grafana remain vulnerable to exploitation.
- Reports highlight the increasing vulnerabilities in open-source software, with 86% of analyzed applications containing vulnerable components.
- To combat security threats, the SOC Prime Platform offers real-time threat intelligence and detection tools for proactive defense.
- The CVE-2025-4123 vulnerability affects a significant percentage of Grafana instances, exposing them to account takeover risks.
- The flaw, named 'The Grafana Ghost,' enables attackers to execute arbitrary code and seize control of user accounts.
- Exploiting this vulnerability can lead to loss of visibility into key systems and operational data compromise.
- Mitigation measures include updating to patched Grafana versions to reduce the risk of exploits.
- Organizations with exposed instances of CVE-2025-4123 must implement proactive defense strategies to thwart potential attacks.
- The SOC Prime Platform offers advanced AI-driven solutions to help organizations act swiftly in the face of evolving cyber threats.
Read Full Article
Like
Securityaffairs
185
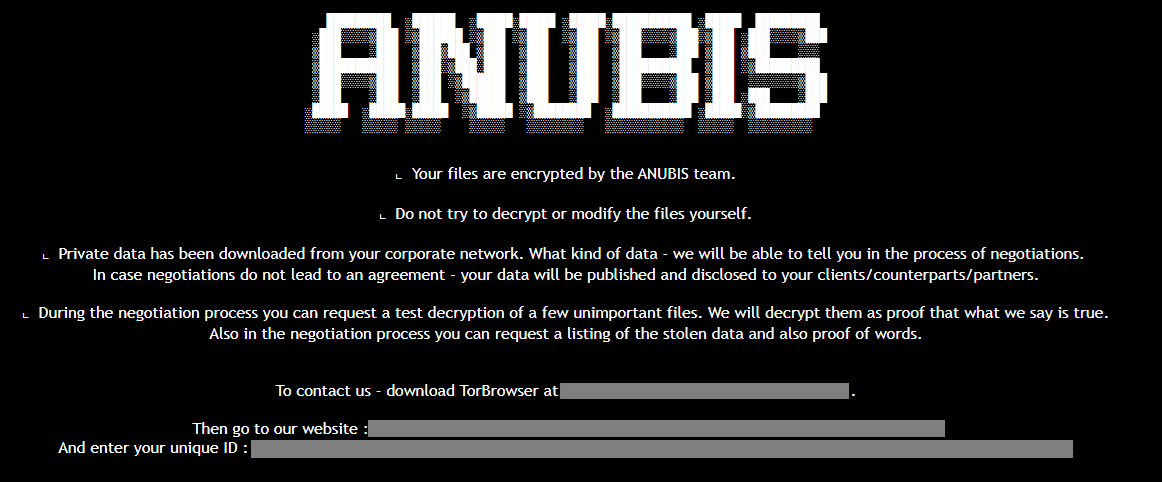
Image Credit: Securityaffairs
New Anubis RaaS includes a wiper module
- Anubis RaaS now includes a wiper module, permanently deleting files and preventing recovery even after ransom payment.
- Active since December 2024, Anubis launched an affiliate program in February 2025, breaching organizations in various sectors like healthcare and construction.
- It combines file encryption with a rare 'wipe mode,' erasing data effectively, as per a report by Trend Micro.
- Anubis evolved from an earlier variant called Sphinx, offering multiple monetization paths, including data theft and access resale.
- The ransomware operates with the ECIES encryption scheme and uses double extortion tactics, threatening to leak data if ransom demands are not met.
- Upon activation of the wiper mode, files are left with a 0 KB size, indicating complete erasure.
- Anubis supports various commands for privilege escalation, directory exclusion, and targeted encryption, ensuring successful data encryption.
- The ransomware's use of dual-threat capabilities and flexible affiliate programs represents a significant evolution in cyberthreat landscape, maximizing revenue potential and victim pressure.
- Trend Micro released a list of indicators of compromise (IoCs) related to the Anubis threat.
Read Full Article
11 Likes
Tech Radar
424

Image Credit: Tech Radar
Worrying attack sees 10,000 records allegedly belonging to VirtualMacOSX leaked - here's what we know
- Thousands of records from VirtualMacOSX users, including sensitive information like banking data, have been leaked on a hacking forum.
- Security researchers discovered a thread on a mainstream internet hacking forum offering a database allegedly from VirtualMacOSX.com for free.
- The leaked database includes personal details such as user IDs, full names, email addresses, passwords, bank details, and support tickets.
- The database contains 176,000 lines across three separate .txt files with significant personal and financial information.
- Safety Detectives conducted a superficial analysis of a 34-line sample from the database, indicating its authenticity.
- It is advised that users reset their passwords, monitor bank accounts for suspicious activities, and beware of potential phishing attempts.
Read Full Article
25 Likes
TechBullion
402

Image Credit: TechBullion
How Business IT Solutions Support Data Security
- In today’s digital world, protecting business data is crucial for survival, with cyber threats and data breaches on the rise.
- Business IT Solutions play a vital role in safeguarding information, preventing threats, and ensuring long-term digital resilience.
- These solutions encompass services like IT support, network security, cloud computing, backup, and disaster recovery.
- IT Support Companies offer technical expertise, strategic insights, system monitoring, security protocols, and employee training to enhance data security.
- Business IT Solutions actively protect data through endpoint protection, encryption, cloud security, network monitoring, compliance management, and disaster recovery planning.
- They assist in complying with regulations like GDPR, HIPAA, and PCI-DSS, minimizing legal risks and fines.
- Business IT Solutions focus on proactive security measures, scalability, employee training, and swift response to incidents for comprehensive data protection.
- The importance of having secure backups, quick recovery protocols, and involving employees in strengthening internal defenses is highlighted.
- Overall, Business IT Solutions are essential for staying ahead of cyber threats, ensuring compliance, and maintaining data security in a constantly evolving digital landscape.
- They serve as digital security partners, offering ongoing support and protection against increasingly sophisticated cyber threats.
Read Full Article
24 Likes
Eletimes
101

Image Credit: Eletimes
Infineon expands government ID portfolio with SECORA ID V2 and eID-OS for enhanced flexibility and faster time-to-market
- Infineon Technologies AG introduces two new solutions, SECORA ID V2 and eID-OS, to meet the increasing demand for electronic identification (eID) documents globally.
- These solutions provide flexibility for selecting project-specific requirements, reducing development time, and expediting deployment for local security printers and card manufacturers.
- SECORA ID V2, the successor to SECORA ID V1, offers improved security features and transaction speeds up to 80% faster, based on Java Card 3.1 standard supporting biometric match-on-card functions.
- Infineon's SECORA ID V2 supports a wide range of applets, Visa, Mastercard, and Calypso payment tools, with Common Criteria EAL6+ certification and EMVCo approval.
- Infineon eID-OS integrates TEGRION security controller with a native operating system, offering a performance-optimized solution targeting CC EAL 5+ eMRTD certification, reducing maintenance costs.
- eID-OS features fast and secured transactions with a powerful CPU, advanced cryptography accelerators, and Integrity Guard 32 security architecture, ensuring transaction times of less than 0.5 seconds.
- The solution provides simplified implementation, personalization, and administration, with low total cost of ownership and reduced carbon footprint due to Infineon's coil-on-module package.
- Infineon's eID-OS saves space and enables thinner electronic data pages, ideal for modern eID projects requiring an additional security layer.
Read Full Article
6 Likes
Global Fintech Series
366

Image Credit: Global Fintech Series
The End of AI’s Wild West: How New Regulations Will Reshape Financial Services in 2025
- AI has been a significant driver of innovation in financial services, but the unregulated adoption is coming to an end.
- Global governments are working on legal frameworks to ensure transparency and accountability in AI systems.
- The EU AI Act is the first comprehensive regulation, influencing AI regulations worldwide.
- Financial firms operating in the EU must comply with the AI Act or face hefty fines.
- In the U.S., state-level regulations on AI are emerging, with California leading in various AI-related legislation.
- Federal guidelines by NIST are shaping responsible AI development.
- Financial institutions must prepare for compliance with international and domestic AI regulations.
- Employee training and customer transparency regarding AI regulations are essential.
- Firms need to align with global standards like the EU AI Act to ensure compliance while leveraging AI-driven financial services.
- Early action in adopting transparent and responsible AI practices will give firms a competitive advantage.
Read Full Article
22 Likes
Wired
229

Image Credit: Wired
6 Tools for Tracking the Trump Administration’s Attacks on Civil Liberties
- The article discusses various tools that track the Trump administration's attacks on civil liberties.
- These tools aim to document changes in federal government funding, workforce, policy, immigration deportations, ICE flights, and regulatory changes.
- Examples include The Impact Map, United States Disappeared Tracker, ICE Flight Tracking, Regulatory Changes Tracker, and Trump Administration Litigation Trackers.
- The article also highlights the tracking of far-right groups targeting Pride Month events.
- The tools monitor mass deportations by ICE, ICE Air deportation flights, regulatory changes, and litigation challenging administration initiatives.
- The article emphasizes the need for documenting and analyzing governmental actions impacting civil rights.
- Overall, the tools provide crucial resources for understanding the implications of the federal activities reshaping the US.
Read Full Article
13 Likes
Wired
22

Image Credit: Wired
The WIRED Guide to Protecting Yourself From Government Surveillance
- The article discusses ways to protect against government surveillance under the Trump administration, including the use of encrypted communications like Signal and the importance of encryption for data security.
- It highlights the need for individuals in at-risk groups to upgrade their data security measures, especially considering the vast surveillance machinery at play.
- Various recommendations are provided, such as using end-to-end encrypted messengers like Signal, WhatsApp, and Apple’s iMessage for secure communication.
- The article emphasizes the significance of encrypted devices, recommending full disk encryption for smartphones and laptops to prevent unauthorized access.
- Cloud storage concerns are addressed, stressing the importance of end-to-end encrypted backups to maintain data privacy and security.
- Tips on maintaining online anonymity using tools like the Tor Browser and VPNs are shared to protect internet browsing habits and location data.
- Financial privacy measures are discussed, advocating for cash transactions over digital payments to avoid financial surveillance.
- The article also touches on the use of burner phones for anonymity and cautions against their limitations in maintaining long-term privacy.
- Lastly, it acknowledges the challenges of controlling one's digital past and the risk of past data compromises affecting privacy.
- Overall, the article offers comprehensive advice on enhancing personal privacy protections and resisting surveillance through various technological means.
Read Full Article
1 Like
Wired
322

Image Credit: Wired
Why We Made a Guide to Winning a Fight
- WIRED has created a guide on winning a fight, providing strategies for different types of battles.
- The guide covers physical and non-physical fights, such as protests against government policies and online trolling.
- It emphasizes the importance of picking battles wisely and understanding how to effectively win them.
- Nonviolent protests involving over 3.5% of a population have been successful in driving change, according to Harvard's Erica Chenoweth.
- WIRED's package includes stories on topics like the Tesla Takedown, gender-affirming care, and digital security in the current political climate.
- Advice on fighting and out-trolling trolls is provided, along with insights from experts in various fields.
- The guide encourages readers to fight for their beliefs but in a non-violent manner, promoting activism and change in society.
Read Full Article
19 Likes
For uninterrupted reading, download the app