Cyber Security News
Dev
217

Image Credit: Dev
How to Crack Password-Protected ZIP Files Using John the Ripper on Kali Linux
- Learn how to crack password-protected ZIP files using John the Ripper on Kali Linux in a cybersecurity project.
- John the Ripper is a powerful tool for password cracking and security audits, supporting various hash types and file formats.
- ZIP files are chosen for this project due to their beginner-friendly nature and compatibility with John the Ripper.
- Project setup involves creating a password-protected ZIP file and using Kali Linux with RDP access.
- Steps include creating the ZIP file, starting Kali Linux, finding the IP address, connecting via RDP, transferring the file, and using John the Ripper.
- After setting up, extracting the hash from the ZIP file, saving it to a text file, and cracking the password with John the Ripper is done.
- John the Ripper successfully cracked the ZIP file password, emphasizing the importance of strong passwords in cybersecurity.
Read Full Article
13 Likes
Socprime
137

Image Credit: Socprime
From Sigma to SentinelOne: Detecting Password Access via Notepad with Uncoder AI
- The Sigma rule targets unauthorized credential access or suspicious behavior on Windows systems by detecting Notepad opening files with names suggesting password storage.
- The rule looks for process creation events with parent process explorer.exe, child process notepad.exe, and command line containing strings like password*.txt, password*.csv, etc.
- Tagged under MITRE technique T1083 (File and Directory Discovery) and uses process_creation telemetry from Windows.
- Uncoder AI automatically translates the detection logic into SentinelOne Event Query syntax, enabling efficient threat hunting or real-time alerting.
- This translation includes mapping parent/child process relationships, command line pattern matching, and supports wildcards and multiple extensions.
- Automatically parsing Sigma YAML-based rules, Uncoder AI maps fields and logic into SentinelOne's query structure while preserving semantic intent.
- This innovation allows security teams to deploy powerful behavioral detections in SentinelOne without manual scripting.
- The capability offers rapid Sigma rule reuse, detection of unauthorized credential access, reduced engineering overhead, and better visibility into file access patterns involving sensitive keywords.
- Uncoder AI transforms abstract detections into actionable endpoint queries, facilitating proactive threat hunting in SentinelOne.
Read Full Article
8 Likes
Socprime
395

Image Credit: Socprime
Convert Sigma DNS Rules to Cortex XSIAM with Uncoder AI
- Uncoder AI can convert Sigma DNS rules to Cortex XSIAM syntax, aiding in detecting malicious DNS queries related to Katz Stealer malware.
- Sigma rules targeting Katz Stealer domains are translated to XSIAM rules, improving detection capabilities.
- Uncoder AI simplifies the process by automating field translations and adding metadata inline.
- This conversion eases the complexity of writing detection logic for XSIAM and enhances detection fidelity.
- It accelerates multi-platform coverage, reduces dependency on vendor-specific knowledge, and improves DNS-based detections in Cortex XSIAM.
Read Full Article
23 Likes
Socprime
395

Image Credit: Socprime
Detect Linux Reconnaissance in Microsoft Sentinel with Sigma-to-KQL Conversion
- A new feature in Microsoft Sentinel translates a Linux-based Sigma rule targeting the sysinfo system call into KQL for better detection.
- The sysinfo system call provides attackers with system metadata crucial for reconnaissance activities.
- The feature converts the Sigma rule's Linux auditd telemetry targeting sysinfo into KQL, excluding benign admin processes like splunkd.
- It uses sophisticated logic to filter syslog messages for sysinfo events and excludes known non-malicious activities like Splunk agent usage.
- This innovation streamlines cross-platform detection, translating auditd rules to Sentinel-compatible queries automatically.
- Uncoder AI facilitates the translation process by parsing Sigma logic, mapping to syslog fields, and preserving essential filters.
- The automation reduces the time and effort required for manual translation of detection rules from Sigma to Microsoft Sentinel.
- Security teams benefit from enhanced threat coverage across hybrid cloud and Linux environments without the need for manual KQL scripting.
- The feature aids in tactical reconnaissance detection, offering cleaner signals and better detection capabilities against early-stage attacks.
- By operationalizing Linux audit rules in Microsoft Sentinel, Uncoder AI enables faster and more effective threat detection.
Read Full Article
23 Likes
Pymnts
324

Image Credit: Pymnts
Services and APIs Turning Interchange Pressure Into Merchant Growth
- Payment processing is crucial for banks and FinTechs in winning customer loyalty amidst high competition.
- North, formerly North American Bancard, has rebranded to offer specific capabilities for new and emerging markets.
- North's simplified banner represents a single technology stack catering to startups and large enterprises.
- The company bundles operational software around its gateway to protect margins amidst pricing scrutiny.
- Merchants can control their payment options with transparency in North's Payments Hub.
- Developers receive a concierge treatment with easy integration options and AI models for fraud prevention.
- North aims to provide value-added services beyond processing, competing with software-led acquirers and banks.
- The company's evolution from ISO to a platform with flexible services aims to meet the demands of specialized payment verticals.
- North's rebrand signals its intent to expand services and cater to a wider range of distribution channels.
Read Full Article
19 Likes
Pymnts
315
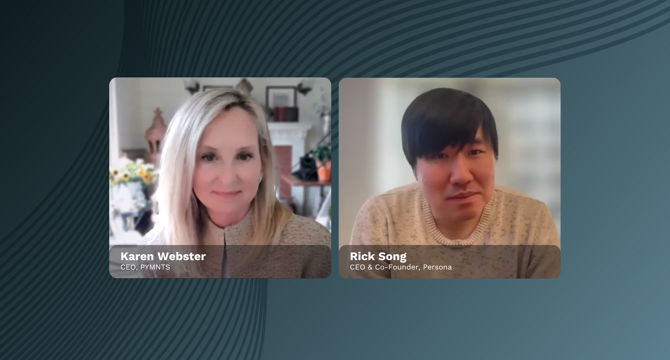
Image Credit: Pymnts
Bots Overtake Fraudsters as Digital Identity’s Main Threat, Says Persona CEO
- Digital identity's challenges in security-critical operations like commerce, banking, and payments have intensified due to the main threat shifting from human fraudsters to bots, driven by artificial intelligence.
- The future may require new identity paradigms to identify AI bots and manage AI traffic effectively, highlighting the importance of proxies and efficient identity management.
- Persona CEO emphasizes the need for seamless and frictionless identity verification processes to distinguish between bots and legitimate users.
- The goal is to enable instant and reliable identification without compromising privacy or requiring intrusive measures like biometric scans or government IDs.
- Persona aims to create a three-layer architecture for identity verification, orchestration, and data management, integrating various digital credentials to enhance security and user experience.
- The evolving landscape of digital identity faces challenges in building consumer trust and combating identity theft, prompting the exploration of proxy identities and innovative digital ID solutions.
- The future vision involves combining proxy identities with AI models to enable seamless transactions and transform commerce into goal-driven interactions.
- Anticipated societal and governmental reactions to AI advancements include data protectionism, digital ID fragmentation, and the development of localized digital identity frameworks.
Read Full Article
18 Likes
Pymnts
84
Image Credit: Pymnts
Payment Hubs Offer Banks a Path to Avert $98.5 Million in Annual Losses
- In the digitized financial landscape, traditional banks are under pressure to transform their payment infrastructures to meet customer expectations and compete with digital-first challengers.
- The PYMNTS Intelligence report, 'Payment Hubs Fuel Digital Modernization for Banks,' in collaboration with FIS, highlights that fast, secure, and frictionless payment experiences are now fundamental expectations for consumers and businesses choosing where to bank.
- Payment hubs, modern centralized systems, consolidate payment processing across various payment rails like real-time networks and wire transfers to provide a seamless payment experience.
- These payment hubs enhance customer journeys by ensuring faster transactions, instant confirmations, and transparency on timing and fees, while also unlocking operational efficiencies for banks.
- Key data points reveal that 57% of organizations experience weekly payment processing friction, and significant customer attrition risk exists as 42% of consumers consider transitioning to non-traditional financial providers.
- Businesses face annual losses estimated at $98.5 million due to disruptions and inefficiencies in money movement driven by cyber threats, fraud, and regulatory complexities.
- Payment hubs offer multi-rail optimization, intelligent payment routing, fraud detection, compliance tools, and analytics to enhance efficiency and cost savings.
- The systems automate processes, reduce errors, maintenance costs, and technical debt, allowing banks to adapt to market changes, scale payment capabilities, and introduce new services with cloud technology and open APIs.
- By breaking down traditional silos, payment hubs empower banks to focus on innovation rather than managing complex legacy systems.
- Overall, the report emphasizes the importance of payment hubs in modernizing payment infrastructures, improving customer experiences, and driving operational efficiencies for banks.
- The capabilities of payment hubs include facilitating multi-rail optimization, ensuring efficient payment routing, and offering advanced features such as fraud detection, compliance tools, and analytics.
- Payment hubs enhance operational efficiency through automation, reducing manual intervention, errors, maintenance costs, and technical debt, while allowing banks to adjust to market changes and introduce new services with cloud technology and open APIs.
- These efficiencies enable banks to innovate and focus on growth by freeing up resources previously tied to managing complex legacy systems.
- The report underscores the crucial role of payment hubs in aiding banks in meeting customer expectations, staying competitive, and avoiding significant financial losses due to inefficiencies.
- The significance of payment hubs lies in their ability to streamline payment processes, enhance customer experiences, and drive operational efficiencies that benefit both banks and customers alike.
- In conclusion, payment hubs represent a pivotal solution for traditional banks to modernize their payment infrastructure, improve operational efficiency, and stay relevant in the evolving financial landscape.
Read Full Article
5 Likes
Medium
115

Image Credit: Medium
Forma company wins the grand prize for the security messenger SECURET for the third year in a row!!!
- Forma Company won the “Service Innovation Award” for its Web3-based secure messenger SECURET for the third consecutive year.
- SECURET encrypts conversations end-to-end and doesn't store user data on servers, claiming to have an impenetrable security algorithm.
- Users can use SECURET without signing up or verifying their identity, offering anonymity and security simultaneously.
- The messenger has over 10 million global downloads, attributed to its user-friendly interface and fast response time.
- SECURET is praised for providing worry-free conversation experiences and is popular both domestically and internationally.
- The app caters to those who prioritize security for various types of sensitive information exchanges, like family discussions, business meetings, and medical consultations.
- Users are encouraged to embrace the right to speak securely by leveraging SECURET's philosophy and technology.
Read Full Article
6 Likes
Medium
404

Image Credit: Medium
Planetary Chain of Custody: Securing Martian Mining Data with Blockchain
- Humanity is moving towards interplanetary resource extraction, focusing on securing extraterrestrial data integrity and ownership.
- Off-Earth mining of resources like helium-3, Martian ice, and asteroid materials is becoming crucial.
- The vulnerability of space data, including mineral reports and resource claims, is a significant concern.
- Blockchain technology is proposed as a solution to safeguard extraterrestrial data.
- Decentralized consensus through Blockchain is essential for ensuring data trustworthiness in space.
- A Planetary Chain of Custody using Blockchain ensures the immutability and integrity of space data.
- Blockchain enables auditable processes like extracting water ice from beneath the Martian surface.
- Blockchain offers immutability, decentralization, and verifiable consensus for space data.
- The next cyber frontier involves securing data integrity in interplanetary missions.
- It is crucial to future-proof the integrity of interplanetary civilization's data.
- Efforts are focused on building truth systems for interplanetary data security.
- Collaboration opportunities are encouraged for space data infrastructure, cross-chain interoperability, and legal-tech frameworks for planetary claims.
- Ensuring that data integrity matches human vision upon returning from Mars is highlighted.
- The article emphasizes the importance of securing data integrity for future space missions.
- Blockchain technology is positioned as a key tool for ensuring trustworthiness in extraterrestrial data management.
Read Full Article
24 Likes
Medium
439

Image Credit: Medium
The $500 Facebook Bug That Taught Me the Real Meaning of Respect
- The author recounts discovering a bug on Facebook in 2019 while hunting for vulnerabilities outside work hours.
- The bug found was a privacy glitch related to Facebook pages that allowed admins to hide their business address.
- Despite not being a high-profile bug like Remote Code Execution (RCE), it was insightful for the author.
- The author shares the scenario of testing a Facebook page from an account with an 'analyst' role, which typically does not have access to the page's hidden address.
Read Full Article
26 Likes
Hackernoon
430

Image Credit: Hackernoon
What’s The Worst That Could Happen? These Security Mistakes Nearly Showed Me
- Security breaches often start with small mistakes rather than elite hackers.
- Trusting every plugin, package, or API can lead to security vulnerabilities.
- Leaving debug mode on in production can expose sensitive data like API keys.
- Not wiping old computers clean before disposal can result in data theft.
- Sharing API keys in public repositories can lead to unauthorized access.
- Exposing admin panels can make your system vulnerable to attacks.
- Hardcoding secrets into the codebase can expose critical systems.
- Sharing one login across the team can lead to accountability issues and unauthorized access.
- Using random USB drives can introduce malware to your system.
- Practicing caution and implementing security measures early can prevent chaos later on.
Read Full Article
25 Likes
Securityaffairs
31

Image Credit: Securityaffairs
Trend Micro fixes critical bugs in Apex Central and TMEE PolicyServer
- Trend Micro addressed critical vulnerabilities in its Apex Central and Endpoint Encryption PolicyServer products.
- The vulnerabilities impact products such as Trend Micro Endpoint Encryption (TMEE) PolicyServer and Apex Central.
- Apex Central is a centralized management server used in Trend Micro’s Endpoint Encryption solution.
- A patch has been released to resolve several vulnerabilities in Trend Micro Endpoint Encryption PolicyServer.
- The vulnerabilities include SQL injection privilege escalation, deserialization RCE, and authentication bypass issues.
- Trend Micro highlighted the need for immediate application of security updates to mitigate risks.
- No evidence of active exploitation has been reported for these vulnerabilities.
- The company fixed flaws in Apex Central related to deserialization RCE vulnerabilities.
- The vulnerabilities in Apex Central have not been actively exploited in the wild.
- Administrators use Apex Central for centralized management of Trend Micro products and services.
- Apex Central provides a single monitoring point for network-wide antivirus and content security products.
- Follow @securityaffairs, @Facebook, @Mastodon for more cybersecurity news.
- Author: Pierluigi Paganini (SecurityAffairs - hacking, Apex Central)
Read Full Article
1 Like
Global Fintech Series
115

Image Credit: Global Fintech Series
Mobile First, Security Always: Millennials Reshape Payment Landscape, PXP Survey Reveals
- Millennials are embracing digital wallets, especially those with multi-currency features for international use, while prioritizing security above all else, according to a new study by PXP.
- The study shows that 64% of millennials value digital wallets, especially for international travel, with 40% considering security their top priority when selecting payment methods.
- Mobile wallets like Apple Pay are gaining popularity among younger millennials, with 20% using them daily, while traditional payment methods still remain popular for everyday spending.
- Debit cards are preferred for everyday shopping, with 40% of millennials using them primarily in grocery stores, while credit cards are favored for high-ticket online purchases.
- Cash is still used for certain transactions, with 20% of millennials opting for it when dining out, primarily for splitting bills in group settings.
- Online shopping dominates, with 80% of millennials doing most of their shopping online.
- For travel and accommodation, 38% of millennials use debit cards for hotel bookings, while 26% prefer credit cards for rewards, insurance, or cashback benefits.
- Millennials seek payment options that align with their mobile-first lifestyles without compromising security, expecting both innovation and trust in payment systems.
- Insights from the study indicate that millennials are attracted to retailers offering exclusive discounts for specific payment methods, prefer brands with personalized shopping experiences, and are drawn to payment methods that offer rewards or cashback.
- Hidden fees are the biggest frustration for 36% of millennials when making payments.
- PXP's introduction of PXP Unity aims to support businesses in meeting changing consumer demands by providing security, flexibility, and a seamless payment experience across channels.
- Businesses can implement strategies like mobile wallet incentives, bill-splitting features, loyalty-integrated payment systems, and BNPL options to cater to millennial preferences and enhance the payment journey.
- Meeting millennial payment expectations is crucial for business growth, and PXP Unity helps merchants deliver secure and flexible payment options.
- By tailoring approaches to attract millennial customers, businesses across different industries can expect higher engagement, increased loyalty, and improved conversion rates from this digitally-savvy generation.
Read Full Article
6 Likes
Pv-Magazine
315

Cybersecurity for resilient energy storage projects
- Compliance with cybersecurity regulations is challenging for many in the energy storage industry but presents opportunities for risk mitigation.
- Robust cybersecurity safeguards are essential for the resilience of grid infrastructure as the energy storage sector evolves.
- The digitalization of grid operations has increased the cyber attack surface, necessitating the implementation of cybersecurity measures.
- North American Electric Reliability Corporation highlighted the rise in vulnerable points in US power grids, emphasizing the need for cybersecurity.
- Energy storage investors are advised to address evolving cybersecurity risks and regulations to prevent revenue losses and project disruptions.
- Fluence views cybersecurity as a way to enhance customer value by reducing project risk associated with cyber non-compliance and incidents.
- Cybersecurity is crucial in mitigating revenue loss and ensuring project availability amidst changing regulatory requirements and cyber threats.
- Fluence experts Katherine Hutton and Lars Stephan emphasize the importance of cybersecurity measures in energy storage projects.
- Investing in robust cybersecurity strategies can help safeguard energy storage projects against cyber-related disruptions and potential revenue impacts.
- For more information, readers are encouraged to visit the ESS News website for further insights on cybersecurity in energy storage projects.
Read Full Article
18 Likes
Dev
302

Image Credit: Dev
GeoServer Hit by Critical SSRF and XXE Vulnerabilities — Patch Now!
- GeoServer, widely used for geospatial data, is affected by critical SSRF and XXE vulnerabilities (CVE-2024-29198, CVE-2025-30220) allowing unauthenticated access to sensitive files.
- The SSRF vulnerability arises from misconfigured PROXY_BASE_URL allowing attackers to exploit the TestWfsPost endpoint.
- The XXE flaw in GeoTools library can lead to arbitrary file read or network access due to improper EntityResolver configuration.
- Both vulnerabilities pose a high-risk, remote network exploitation threat with no need for authentication.
- GeoServer versions prior to 2.24.4, 2.25.2, 2.27.1, 2.26.3, 2.25.7 are affected along with corresponding GeoTools and GeoNetwork versions.
- Temporary mitigation for SSRF involves blocking TestWfsPost access, while permanent fix requires updating to specified patched versions.
- For XXE, providing a secure EntityResolver is a temporary workaround with an upgrade to patched versions advised for permanent solution.
- Several security platforms like Yuntu, Dongjian, SafeLine, and Quanxi are responding to these vulnerabilities with detection and support services.
- The advisory for these vulnerabilities was released on June 12, 2025, urging immediate patching due to the severity of these issues.
- Action is highly recommended for GeoServer users to prevent potential full system compromise and unauthorized file access.
- Community support is available for SafeLine users through updates and resources shared in the SafeLine community.
- Patching these critical vulnerabilities is crucial for system security and prevention of unauthorized data access.
- GeoServer users are advised to follow the provided mitigation steps and promptly update to the patched versions to secure their systems.
- Immediate action is necessary for GeoServer users to safeguard against the exploitation of these high-risk vulnerabilities.
- Stay informed and updated within the SafeLine community to address security concerns and implement necessary measures.
- If you run GeoServer, patch immediately to avoid potential system compromise as these vulnerabilities pose a serious threat to server security.
Read Full Article
18 Likes
For uninterrupted reading, download the app