Cyber Security News
TechCrunch
52

Image Credit: TechCrunch
UK watchdog fines 23andMe over 2023 data breach
- The U.K. data protection watchdog fined 23andMe £2.31 million ($3.1m) for failing to protect U.K. residents’ personal and genetic data prior to its 2023 data breach.
- The Information Commissioner’s Office (ICO) fined 23andMe for not having additional verification steps for users to access and download their raw genetic data during the cyberattack.
- Hackers stole private data of over 6.9 million users during a months-long campaign by accessing thousands of accounts using stolen credentials.
- 23andMe did not require multi-factor authentication, breaking U.K. data protection law according to the ICO.
- Over 155,000 U.K. residents had their data stolen in the breach.
- 23andMe implemented mandatory multi-factor authentication for all accounts in response to the fine.
- The ICO is in contact with 23andMe’s trustee after the company filed for bankruptcy protection.
- A hearing on 23andMe’s sale is expected later on Wednesday.
Read Full Article
3 Likes
Global Fintech Series
133

Image Credit: Global Fintech Series
The AI Paradox: Artificial Intelligence Supporting Business Growth While Fueling Fraud
- AI and automation are transforming business priorities, with a BILL survey highlighting AI's role in improving cash flow and combating fraud.
- The report reveals that businesses are increasingly leveraging AI to enhance financial operations and adapt to economic uncertainties.
- AI is seen as crucial for finance leaders in decision-making, from fraud prevention to automating tasks and adapting operations.
- 92% of businesses are concerned about fraud, with AI playing a dual role as both an enhancer and a risk factor for fraud detection.
- Established businesses show more enthusiasm for AI adoption, with over 70% believing in AI's potential to strengthen financial forecasting.
- AI is perceived as a facilitator for startups, with the majority seeing it as easing the process of starting a new business and surviving the initial years.
- Businesses are focusing on smart cash flow management strategies, including diversifying suppliers, adjusting prices, and accelerating automation.
- Many businesses aim to go paperless by 2026, with improved cash flow visibility considered essential for faster response to opportunities.
- Due to an accounting talent shortage, businesses predict higher accounting service costs and are preparing for increased in-house accounting work.
Read Full Article
7 Likes
Dev
88

Image Credit: Dev
Wazuh: Your Open-Source Security Superhero
- Wazuh is an open-source security platform offering XDR and SIEM capabilities with agent-server architecture.
- Features include intrusion detection, log analysis, file integrity monitoring, vulnerability detection, and incident response.
- It simplifies security monitoring, provides proactive threat detection, and seamlessly integrates with the Elastic Stack for data visualization.
- Wazuh automates incident response to minimize damage and downtime.
- The platform is open source, free to use, and highly customizable.
Read Full Article
5 Likes
Alleywatch
246

Compyl Raises $12M to Simplify Governance and Compliance
- Compyl raised $12M in Series A funding led by Venture Guides, addressing challenges in the Governance, Risk, and Compliance (GRC) market.
- The platform turns GRC complexity into data-driven insights, unifies enterprise data in real-time, and enables risk management and compliance without heavy IT development.
- Compyl differentiates itself by offering automated security benchmark checks, real-time contextual insights, and customized GRC processes without third-party dependencies.
- The company targets mid-market and lower enterprise companies in regulated industries like software, financial services, and healthcare, aiming to streamline information security programs.
- Compyl's business model includes direct sales and channel partners, preparing for economic slowdown by prioritizing sustainable growth initiatives and customer relationships.
- Key challenges in raising capital included educating investors on the dynamic GRC space and positioning Compyl as a comprehensive GRC platform with strong differentiation.
- Investors were attracted by Compyl's experienced team, growing demand for consolidated GRC tools, strong revenue metrics, and technical depth in automating workflows for security teams.
- Future milestones include expanding go-to-market operations, accelerating AI-driven product development, and securing strategic customer wins in regulated sectors.
- Compyl advises companies to stay close to customers, build efficiently, and consider profitability or break-even operation during lean times for long-term resilience.
- The company aims to deepen its presence in core verticals, enhance product intelligence, and foster partnerships to lead the next generation of GRC innovation.
Read Full Article
14 Likes
Medium
431
Image Credit: Medium
Worst-Case Scenarios of AI Platform Account Hacks
- Accounts on AI platforms like OpenAI’s ChatGPT, Anthropic’s Claude, Google’s Bard/Gemini, X.AI’s Grok contain highly sensitive data used for work and personal tasks.
- In case of a hack or breach, attackers could access a user’s chat history, potentially revealing confidential information or private conversations.
- Worst-case scenarios of AI platform account hacks involve corporate espionage and personal trauma, supported by real incidents and expert analysis.
- AI chatbots may store data that users never share publicly, leading to unintended disclosures of proprietary data and internal documents in corporate settings.
- For instance, Samsung engineers shared semiconductor source code and meeting transcripts on ChatGPT, mistakenly seeking troubleshooting help.
- Security assessments revealed the risks associated with corporate data leakage through AI chatbots and the potential consequences.
- The accidental exposure of sensitive information due to user error when interacting with AI platforms poses significant security threats.
- Expert insights highlight that AI platform breaches can have far-reaching effects, impacting individuals, organizations, and even national security.
- Measures such as robust cybersecurity protocols, encryption of data, and user education are crucial to prevent AI platform hacks and data breaches.
- The continuous evolution of AI technologies necessitates vigilance in safeguarding personal and sensitive data stored on these platforms.
- Addressing the risks of AI platform hacks requires a collaborative effort between users, developers, and security professionals to enhance data protection measures.
- Protecting AI platform accounts from unauthorized access is essential to mitigate the potential harm caused by data breaches and security incidents.
- The growing reliance on AI assistants underscores the importance of ensuring the security and integrity of data shared and stored on these platforms.
- Heightened awareness of cybersecurity threats associated with AI platform vulnerabilities is essential for users and organizations to enhance their defenses.
- Web story eligibility for the article on worst-case scenarios of AI platform account hacks can facilitate widespread awareness and promote cybersecurity best practices.
- Considering the relevance and potential impact of the topic, the article is eligible for web story generation.
Read Full Article
25 Likes
Tech Radar
94

Image Credit: Tech Radar
Major hack against car-sharing firm Zoomcar sees 8.4 million users at risk
- Car-sharing marketplace Zoomcar disclosed a cyberattack in a recent 8-K form filed with the SEC.
- About 8.4 million users had their personal information compromised, including names, phone numbers, and addresses.
- Sensitive information such as financial details and passwords was not believed to be affected.
- Zoomcar detected the attack on June 9, 2025, and took immediate measures to contain it.
- Hackers informed the company about the breach themselves, hinting at potential data exfiltration.
- It is assumed that the threat actors may have demanded payment for deleting the stolen data.
- Zoomcar indicated in the filing that no ransom was paid, and they enhanced security measures post-incident.
- The company enlisted a cybersecurity expert, informed regulators and authorities, but reported no significant disruptions to its operations.
- Zoomcar is assessing the full ramifications of the cyber incident, including legal and financial implications.
- No material operational disruptions have been experienced yet, but the company is still evaluating the potential impacts.
- The breach did not result in any material operational disruptions.
- The company is still evaluating all ramifications, including legal, financial, and reputational aspects.
- They have not experienced any significant operational impacts as a result of the breach.
- The incident was disclosed in a recent 8-K form filed with the SEC, revealing the compromise of personal information of millions of users.
- Zoomcar responded by implementing additional security measures and involving external experts.
- While the company continues to investigate the breach, no major operational issues have been reported thus far.
Read Full Article
5 Likes
Securityaffairs
405

Image Credit: Securityaffairs
U.S. CISA adds Apple products, and TP-Link routers flaws to its Known Exploited Vulnerabilities catalog
- U.S. Cybersecurity and Infrastructure Security Agency (CISA) added Apple products and TP-Link routers flaws to its Known Exploited Vulnerabilities catalog.
- A recently patched vulnerability in Apple's Messages app, actively exploited in the wild, targeted journalists with Paragon's Graphite spyware.
- Apple addressed the flaw in its products with various software updates.
- Citizen Lab confirmed the use of Paragon's Graphite spyware to hack fully updated iPhones, targeting journalists in Europe.
- Apple alerted select iOS users of spyware targeting and patched the zero-click exploit used in the attack.
- Paragon accused the Italian government of refusing its offer to help investigate spyware use against a journalist.
- CISA added a command injection vulnerability in TP-Link routers to its catalog.
- Federal agencies are required to address the vulnerabilities identified in the catalog by July 7, 2025.
Read Full Article
24 Likes
Siliconangle
193

Image Credit: Siliconangle
Apiiro report reveals industry differences are shaping generative AI risk profiles
- A new report from Apiiro Ltd. shows differences in how industries adopt and secure generative AI in software development.
- Retail organizations are quickly integrating generative AI into customer-facing systems compared to financial institutions.
- Financial institutions are moving more cautiously with older codebases, leading to greater risk exposure.
- Apiiro's analysis found a seven-fold increase in secrets exposure in generative AI repositories in finance.
- Retail codebases are 1.8 times more likely to contain sensitive data compared to finance.
- Retail developers mainly use OpenAI's Python software development kits, while financial teams experiment with various tools.
- Generative AI in retail is customer-facing and wired into sensitive data, while in finance, it's older and layered onto legacy systems.
Read Full Article
11 Likes
Siliconangle
171
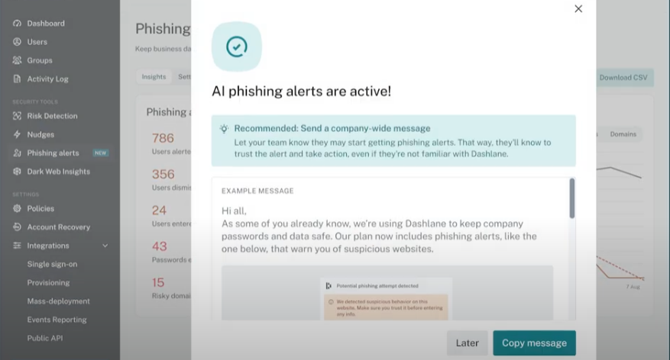
Image Credit: Siliconangle
Dashlane adds AI phishing alerts to Omnix platform to bolster credential protection
- Dashlane introduced AI phishing alerts to its Omnix platform to enhance credential security.
- The AI feature detects and alerts users to phishing risks as they visit spoofed websites.
- Admins gain insights to secure employees against suspicious domains.
- AI helps threat actors evolve tactics to evade phishing detection tools.
- Phishing alerts prompt users to verify website legitimacy in real-time.
- The AI model analyzes 79 phishing indicators to determine potentially malicious domains.
- Analysis is done directly on the user's device for privacy protection.
- Phishing alerts accelerate Dashlane Omnix's ability to uncover and combat human risk.
- AI phishing alerts address shadow IT gaps and resolve at-risk credentials for employees.
- Security teams can use tools like AI phishing alerts to combat AI-enabled phishing attacks.
- Having the right tooling in place helps protect users from falling prey to attacks.
- Dashlane's AI phishing alerts contribute to phishing resistance for enterprises.
- The offering ensures ongoing, secure management of credentials.
- AI phishing alerts complement traditional phishing protection and training methods.
- Dashlane's AI model catches threats, known and unknown, aiding enterprises in building phishing resistance.
Read Full Article
10 Likes
Siliconangle
304

Image Credit: Siliconangle
New Commvault and Kyndryl partnership focuses on hybrid cloud recovery and regulatory compliance
- Commvault Systems Inc. and Kyndryl Holdings Inc. have announced a partnership to enhance recovery, cyber resilience, and regulatory compliance for customers.
- This collaboration will include services like Incident Recovery Services, Managed Backup Services, and Hybrid Platform Recovery.
- Commvault and Kyndryl will work with Pure Storage Inc. to help organizations comply with regulations like the Digital Operational Resilience Act and others.
- The partnership will offer a four-layer architecture for compliance and fast recovery in hybrid cloud environments.
- They introduce the Cyber Resilient Vault and Clean Recovery Zone to protect backup data and enable secure forensic analysis and staged recovery.
- Production Rapid Restore allows fast restoration using Pure Storage FlashBlade, with Immutable Snapshot Recovery for application-consistent snapshots.
- The collaboration aims to meet higher standards for operational resilience set by regulatory frameworks like DORA.
- Automated testing for cyber recovery and support for public cloud and on-premises isolated recovery environments are included in the offerings.
Read Full Article
18 Likes
Managedmethods
312

Image Credit: Managedmethods
What Is Social Engineering? A Guide for K–12 School Leaders
- Social engineering is a technique used by cybercriminals to trick people into divulging sensitive information or granting access.
- In schools, social engineering can take the form of fake emails, phone calls, or messages that exploit trust, urgency, or fear.
- These attacks are dangerous as they can result in ransomware, data breaches, financial loss, and instructional disruption.
- Attackers use AI to customize emails that appear legitimate and exploit school-specific information.
- Traditional email filters may not catch sophisticated social engineering tactics, making schools vulnerable.
- Preventing social engineering requires training staff, enforcing verification protocols, and using AI-powered phishing detection tools.
- School districts can combat social engineering through awareness, internal protocols, and AI-powered phishing detection.
- Advanced Phishing Detection tools analyze context, sender history, and behavior to detect phishing attempts.
- Google Workspace and Microsoft 365 filters may not be sufficient to stop social engineering attacks.
- Combining staff training, verification procedures, and advanced email protection tools is crucial to defend against social engineering.
Read Full Article
18 Likes
Siliconangle
374

Image Credit: Siliconangle
Kusari debuts AI-powered pull request security tool for software supply chain protection
- Kusari Inc. has launched Kusari Inspector, an AI-powered pull request security tool for software supply chain protection.
- Kusari Inspector integrates industry standards, AI, and dependency graph analysis to detect supply chain risks early in the pull request process.
- The tool provides security risk analysis, real-time pull request inspection, and guidance on safe code merging.
- It flags security weaknesses, misconfigurations, risky licenses, and typo-squatted dependencies for developers.
- Kusari Inspector prioritizes risks by ranking vulnerable dependencies against trusted sources to focus on critical threats.
- The AI model continuously learns from codebases to enhance recommendations and provide precise coding fixes.
- The tool also generates Software Bill of Materials data to help maintain compliance and resilience in software supply chains.
- Kusari, a venture capital-funded startup, has raised $8.08 million and received investments from various companies.
- Michael Lieberman, the CTO of Kusari, highlights that Kusari Inspector enables developers to address security concerns early, reducing delays.
Read Full Article
22 Likes
Siliconangle
229

Image Credit: Siliconangle
Coralogix gets $115M in funding to pioneer agentic AI-powered observability
- Coralogix closes a $115 million late-stage funding round and launches an AI agent named 'olly' to democratize observability beyond technical users.
- The Series E funding was led by NewView Capital with participation from Canada Pension Plan Investment Board and NextEquity.
- Existing investors like Advent International, Brighton Park Capital, and others also joined the funding, valuing Coralogix at over $1 billion.
- Coralogix's observability platform aims to detect issues in IT infrastructure by analyzing telemetry data to prevent application failures.
- The launch of 'olly' intends to involve non-technical users like business leaders and product managers in the observability process.
- 'olly' offers a conversational interface to guide users, provide insights, and suggest actions to enhance decision-making and resolve issues.
- Users can ask 'olly' specific questions about problems and receive explanations and solutions in simple language, without technical expertise.
- The AI assistant helps technical users understand system failures by consolidating and interpreting system logs, metrics, and traces.
- Coralogix CEO Ariel Assaraf views 'olly' as an intelligent assistant that empowers employees to access data and make informed decisions.
- 'olly' marks the latest in Coralogix's updates following the acquisition of Aporia Inc., introducing new AI-powered observability capabilities.
- Coralogix previously introduced the AI Center and Continuous Profiling feature to enhance observability and improve application performance.
- The company's investors believe in its potential to drive innovation in observability using AI, distinguishing it from other vendors in the market.
Read Full Article
13 Likes
Tech Radar
185

Image Credit: Tech Radar
Major police operation takes down notorious dark web marketplace Archetyp Market
- A major international police operation led by Europol has successfully taken down the dark web marketplace Archetyp Market after more than five years of operation.
- One person was arrested in Barcelona, Spain, and 'measures' were taken against others, including a moderator and six high-profile vendors.
- Europol seized assets totaling $9 million associated with Archetyp Market.
- Archetyp Market had over 600,000 users, conducted transactions worth more than $280 million, and had over 17,000 listings at the time of its dismantlement.
- The marketplace facilitated the sale of dangerous drugs, including fentanyl.
- The infrastructure of Archetyp Market was located in the Netherlands and was targeted and taken down.
- The operation took place in five European countries - Germany, the Netherlands, Romania, Spain, and Sweden - between June 11 and 13.
- Law enforcement agencies involved in the operation included Europol, national police forces, Eurojust, US Homeland Security Investigations, IRS-Criminal Investigation, and the Department of Justice.
- The takedown of Archetyp Market signifies a significant blow to the dark web and illicit drug trade.
Read Full Article
11 Likes
Socprime
189

Image Credit: Socprime
GrayAlpha Operation Detection: The Fin7-Affiliated Group Spreads PowerNet Loader, NetSupport RAT, and MaskBat Loader
- A sophisticated campaign by GrayAlpha threat actors, linked to FIN7, uses various infection vectors to spread malicious strains like PowerNet and NetSupport RAT.
- GrayAlpha, associated with financially motivated attacks, shows an evolution in cybercrime despite claims of FIN7's dissolution.
- SOC Prime Platform offers Sigma rules for detecting GrayAlpha activity, enriching detection algorithms for FIN7-linked cyber-attacks.
- An analysis reveals GrayAlpha's deployment of PowerNet and MaskBat loaders, utilizing deceptive methods and a traffic distribution system.
- Infection methods include fake browser updates, fake 7-Zip sites, and the TAG-124 TDS, leading to NetSupport RAT infections.
- Mitigation steps involve monitoring the threat landscape, enforcing access controls, and maintaining data protection measures.
- GrayAlpha mirrors the persistence of nation-backed APT campaigns, highlighting the need for robust cybersecurity strategies.
- The campaign leveraged fake browser sites, fake 7-Zip downloads, and the TAG-124 TDS, ultimately delivering NetSupport RAT.
- Defenses recommend proactive monitoring, access restrictions, and data security to combat GrayAlpha's sophisticated attacks.
- GrayAlpha demonstrates the adaptability and persistence similar to nation-backed APT groups, emphasizing the need for comprehensive cybersecurity measures.
Read Full Article
11 Likes
For uninterrupted reading, download the app