Cyber Security News
Socprime
189

Image Credit: Socprime
GrayAlpha Operation Detection: The Fin7-Affiliated Group Spreads PowerNet Loader, NetSupport RAT, and MaskBat Loader
- A sophisticated campaign by GrayAlpha threat actors, linked to FIN7, uses various infection vectors to spread malicious strains like PowerNet and NetSupport RAT.
- GrayAlpha, associated with financially motivated attacks, shows an evolution in cybercrime despite claims of FIN7's dissolution.
- SOC Prime Platform offers Sigma rules for detecting GrayAlpha activity, enriching detection algorithms for FIN7-linked cyber-attacks.
- An analysis reveals GrayAlpha's deployment of PowerNet and MaskBat loaders, utilizing deceptive methods and a traffic distribution system.
- Infection methods include fake browser updates, fake 7-Zip sites, and the TAG-124 TDS, leading to NetSupport RAT infections.
- Mitigation steps involve monitoring the threat landscape, enforcing access controls, and maintaining data protection measures.
- GrayAlpha mirrors the persistence of nation-backed APT campaigns, highlighting the need for robust cybersecurity strategies.
- The campaign leveraged fake browser sites, fake 7-Zip downloads, and the TAG-124 TDS, ultimately delivering NetSupport RAT.
- Defenses recommend proactive monitoring, access restrictions, and data security to combat GrayAlpha's sophisticated attacks.
- GrayAlpha demonstrates the adaptability and persistence similar to nation-backed APT groups, emphasizing the need for comprehensive cybersecurity measures.
Read Full Article
11 Likes
Securityaffairs
105
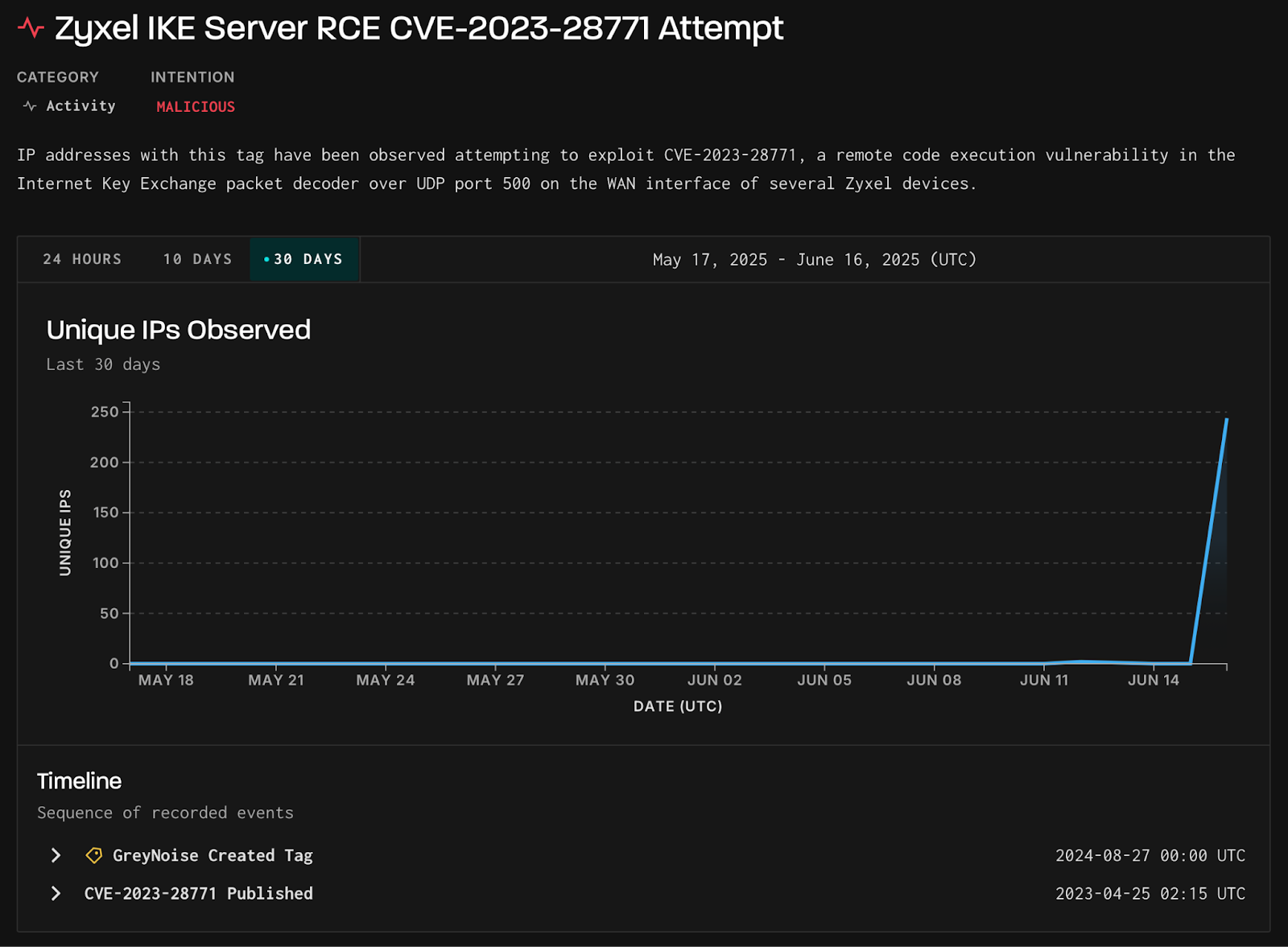
Image Credit: Securityaffairs
Attackers target Zyxel RCE vulnerability CVE-2023-28771
- Attackers are actively targeting the Zyxel RCE vulnerability CVE-2023-28771, according to GreyNoise researchers.
- On June 16, a surge in exploit attempts against the Zyxel IKE decoders vulnerability was observed, with 244 unique IPs involved.
- The main targets of the attack were the U.S., U.K., Spain, Germany, and India.
- All 244 IP addresses related to the exploitation attempts were traced back to Verizon Business in the U.S., but the use of UDP means the IPs could be spoofed.
- The exploit attempts were linked to Mirai botnet variants, as confirmed by VirusTotal.
- GreyNoise recommends blocking the identified malicious IPs, verifying device patches, monitoring for post-exploitation activities, and limiting exposure on IKE/UDP port 500.
- In April 2023, Zyxel addressed the CVE-2023-28771 vulnerability in its firewall devices and urged customers to install patches to mitigate the risk.
- The U.S. CISA added the vulnerability to its Known Exploited Vulnerability to Catalog after observing active exploitation.
Read Full Article
6 Likes
Dev
317

Image Credit: Dev
Fortifying Your Aptos Assets: A Practical Guide to Key Account Rotation
- Key rotation is a crucial security practice for blockchain accounts, allowing the periodic replacement of cryptographic keys to mitigate compromised keys and prevent long-term exposure.
- Aptos offers a unique advantage by enabling key rotation without changing the account address, enhancing security for users.
- The process involves generating new private keys, setting up local networks, initializing profiles, and rotating authentication keys.
- Preparation steps include documenting key usages, backing up keys, ensuring sufficient APT tokens for gas fees, and choosing a new key management strategy.
- The guide provides detailed CLI commands and security considerations for a successful key rotation on Aptos.
- It includes commands for setting up a local network, generating private keys, initializing profiles, and rotating authentication keys with native support.
- The process involves verifying changes, comparing profiles, cleaning up test profiles, and ensuring the security of private and public key files.
- This comprehensive guide ensures a seamless and secure key rotation process for Aptos users while emphasizing the importance of ongoing security practices.
Read Full Article
19 Likes
Medium
339
Image Credit: Medium
How to Measure GRC Success Right
- Measuring GRC success requires focusing on specific, impactful metrics, such as tracking documented risks, new risks added, and risk severity distribution.
- Efficiently treating high-risk issues, evaluating mitigation costs, and assessing remaining risk post-mitigation are crucial for effective GRC management.
- Monitoring compliance gaps, audit trends, and completion of mandatory training by employees helps in reducing regulatory risks and enhancing organizational culture.
- Tracking vendor compliance, timeliness of report filing, and proactive vs. reactive compliance measures are essential for risk management.
- Escalating top risks to leadership, evaluating control effectiveness, and timely incident response contribute to operational maturity and risk foresight.
- Establishing baseline values, setting SMART goals, and embedding metrics into routine practices are key steps in improving GRC performance.
Read Full Article
20 Likes
Silicon
145

Image Credit: Silicon
Huawei, ByteDance ‘Plan’ Major Brazil Cloud Deals
- Huawei and ByteDance are planning major investments in Brazil's cloud sector amid US concerns of growing Chinese influence in Latin America.
- Huawei is set to announce a deal using data centers operated by Dataprev, Brazil's state-run social data systems manager.
- They are also discussing partnerships with Edge UOL, a cloud services division of Grupo UOL PagSeguro.
- The potential data center deal was discussed after a meeting in Dongguan, China, attended by key executives.
- Huawei Cloud aims to be a link between China and Latin America, focusing on infrastructure, cybersecurity, and AI with Edge UOL.
- ByteDance is exploring data center projects in Brazil, including a large data center in Ceara region in partnership with Casa dos Ventos.
- In the past year, Brazil and China signed a cooperation agreement on AI, emphasizing joint work on platforms and AI training.
- Brazil aims to integrate Chinese AI technology into factories for enhanced productivity, amid efforts to work closely with China on technology collaborations.
- Brazil has traditionally pursued a non-alignment strategy, seeking partnerships with both the US and China.
- US officials have expressed concerns over Chinese companies' influence in Latin America, citing national security risks like data theft and surveillance.
- Huawei and ByteDance have faced US scrutiny over national security risks, with Huawei under sanctions since 2019 and TikTok facing potential bans.
- In a separate incident, Brazilian authorities suspended a Chinese electric vehicle plant's construction due to reported labor violations.
Read Full Article
8 Likes
Kaspersky
207

Image Credit: Kaspersky
How to buy and connect a travel eSIM with Kaspersky eSIM Store | Kaspersky official blog
- In today’s world, staying connected is a necessity, facilitated by eSIMs for global travel SIM card needs.
- The Kaspersky eSIM Store simplifies finding, buying, and activating mobile-data plans globally.
- eSIMs store GSM keys, contacts, and multiple carrier profiles without physical swapping of SIM cards.
- Kaspersky eSIMs offer data plans for various regions with non-expiring options and easy activation.
- The eSIMs do not support voice calls but enable data usage while your primary SIM remains active.
- Privacy and convenience are enhanced with eSIM activation not requiring ID verification and supporting smart top-up.
- Value is emphasized with a wide range of plans, including local, regional, and global options.
- Flexibility in purchasing and activating eSIMs is provided, allowing for rollover and multi-region use.
- Security measures are elevated with Kaspersky eSIMs, offering secure connections and protection against online threats.
- Additional security features like securing online payments and VPN services provide added protection for travelers.
Read Full Article
12 Likes
Securityaffairs
432

Image Credit: Securityaffairs
India-based car-sharing company Zoomcar suffered a data breach impacting 8.4M users
- India-based car-sharing company Zoomcar has disclosed a data breach affecting 8.4M users after attackers compromised its systems and contacted the company staff.
- The breach involved unauthorized access to Zoomcar's information systems, leading to exposure of names, contacts, and addresses of users.
- No financial data or passwords were compromised in the breach.
- Zoomcar is investigating the security incident and has taken measures to enhance cloud and network security with the help of cybersecurity experts.
- The company notified authorities about the breach, and its operations have not been significantly impacted so far.
- Legal, financial, and reputational impacts of the breach are being assessed by Zoomcar.
- The company has not provided specific details about the cyber attack, and no ransomware group has taken responsibility for the incident.
- Zoomcar had previously experienced a data breach in July 2018 that affected over 3.5 million users.
Read Full Article
26 Likes
Securityaffairs
396

Image Credit: Securityaffairs
State-sponsored hackers compromised the email accounts of several Washington Post journalists
- State-sponsored hackers compromised the email accounts of several journalists at the Washington Post.
- The cyberattack, believed to be carried out by state-sponsored hackers, targeted Microsoft email accounts of Washington Post journalists covering China and national security.
- The attack was discovered on June 13, with the intrusion potentially granting access to work emails of affected journalists.
- The Washington Post notified its employees about the incident on June 15 and reset all employee passwords as a precaution.
- News Corp, the owner of the Washington Post, revealed in February 2022 that it fell victim to a cyber attack by an advanced persistent threat actor.
- The attack on News Corp was believed to be conducted by a nation-state actor, with suspicions pointing towards a China-linked APT group.
- Mandiant, a cybersecurity firm, has been enlisted to assist in the investigation into the News Corp breach.
- The compromised systems at News Corp gave attackers access to employee emails and documents.
- The attack on News Corp also affected other media outlets under the conglomerate, such as The Wall Street Journal and New York Post.
- The Washington Post is one of the most influential newspapers in the U.S., known for its investigative journalism and political coverage.
- Jeff Bezos acquired the Washington Post in 2013.
- The intrusion at the Washington Post did not impact other systems or customers of the newspaper.
- Cybersecurity incidents like these highlight the ongoing threats faced by media organizations and the need for robust security measures.
- The attack on the Washington Post underscores the importance of cybersecurity vigilance, especially for journalists covering sensitive topics.
- The motive behind the cyber attacks appears to be espionage, targeting sensitive information to benefit the interests of the sponsoring nation.
- The cyber threats faced by media organizations emphasize the critical role of cybersecurity in safeguarding journalistic integrity and protecting sensitive data.
Read Full Article
23 Likes
Fintechnews
282
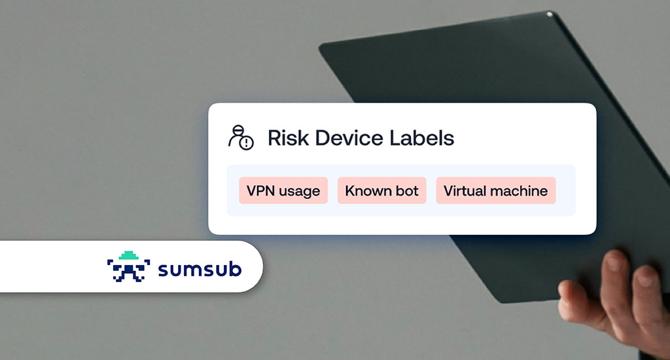
Image Credit: Fintechnews
Sumsub Leverages Device Intelligence to Monitor Fraud Activity in Real Time
- Sumsub has integrated advanced device intelligence from Fingerprint to enhance fraud prevention capabilities.
- The update helps businesses detect suspicious behavior early in the customer journey, especially post-onboarding, a common target for fraud.
- Technical parameters like browser type, operating system, VPN usage are analyzed to identify threats such as bot activity and account takeovers.
- The solution by Fingerprint also spots incognito mode and developer tool usage as potential red flags.
- Sumsub's integration aims to cut unnecessary KYC costs and improve fraud detection without user disruption.
- The tool is beneficial for high-risk industries like crypto, fintech, and e-commerce, aiding in early threat detection.
- Sumsub emphasizes the solution's role in reducing false positives and enhancing fraud detection through various user interactions.
- Sumsub's CPO, Andrew Novoselsky, highlights the collaboration for a comprehensive fraud prevention system.
- This integration enables real-time fraud prevention to mitigate financial losses and operational disruptions.
- Sumsub's platform, combining device intelligence with identity verification solutions, aims to enhance user insights and streamline onboarding experiences.
- Shaun Per from Fingerprint emphasizes the joint effort to reduce fraud and offer smooth onboarding experiences through real-time signals.
- The collaboration benefits businesses by improving fraud prevention accuracy and operational efficiency.
- Overall, the integration of device intelligence enhances Sumsub's fraud monitoring capabilities.
- The expansion aims to provide a more robust fraud prevention system without requiring coding on the clients' end.
- Sumsub and Fingerprint together aim to deliver more effective fraud prevention measures.
- The article was originally published on Fintech Singapore.
- The companies believe the collaboration will help businesses combat fraud effectively.
Read Full Article
16 Likes
TechCrunch
105

Image Credit: TechCrunch
Google to scale up AI-powered fraud detection and security operations in India
- Google introduces Safety Charter in India to enhance AI-powered fraud detection and security operations, focusing on combating digital fraud and scams across the country.
- India witnessed a significant increase in digital fraud cases, with instances related to UPI fraud and arrest scams perpetrated through video calls and predatory loan apps.
- The launch of Google's security engineering center (GSec) in India aims to collaborate with local entities to develop solutions for cybersecurity, privacy, safety, and AI problems.
- Google partners with the Indian Cyber Crime Coordination Centre and the Ministry of Home Affairs to raise cybercrime awareness and implement fraud identification programs like DigiKavach.
- Google will focus on combating online scams, enhancing enterprise cybersecurity, and promoting responsible AI in India through its GSec initiative.
- Google utilizes AI globally to tackle online scams, with initiatives like Scam Detection in Google Messages and Play Protect, which have safeguarded users from suspicious messages and high-risk app installations.
- Google VP Heather Adkins discusses the misuse of AI tools, Google's testing of AI models to prevent harmful content, and the development of frameworks like the Secure AI Framework to curb AI misuse.
- Adkins emphasizes the threats posed by commercial surveillance vendors like NSO Group and other enterprises selling surveillance tools, highlighting the need for industry collaboration to address these challenges.
- Google stresses the importance of multi-factor authentication (MFA) to enhance online security, despite challenges in persuading users to move beyond traditional password-based authentication methods, especially in diverse markets like India.
Read Full Article
6 Likes
Nordicapis
13

APIs and Identity in the Age of the Sovereign Cloud
- Peter Steiner’s 1993 cartoon in The New Yorker humorously depicted online anonymity with the famous phrase 'On the Internet, nobody knows you're a dog.' The rise of the sovereign cloud movement, emphasizing control and compliance, is impacting identity management in the digital space.
- The sovereign cloud movement, gaining traction in the EU, focuses on ensuring proper authorization amid new legislation and federated login systems, sparking significant changes in authentication standards and API access with regional restrictions.
- European lawmakers aim to reduce reliance on foreign-owned digital services, favoring 'sovereign digital infrastructure' to enhance economic independence and security, reflecting global concerns around data jurisdiction and control.
- Sovereign clouds, tailored for specific regulatory environments like the EU's GDPR, require compliance with data processing laws of their respective regions, leading major providers like Amazon and Google to engage in such initiatives.
- In the context of digital sovereignty, ensuring cross-border compliance for API data transfers between jurisdictions becomes crucial, with GDPR-inspired practices such as access controls and encryption playing a key role in meeting regulatory standards.
- The emergence of regional identity providers like itsme and SwissID challenges existing authentication protocols, potentially necessitating a shift towards decentralized identity standards to address interoperability and compliance hurdles.
- The shift towards enhanced identity verification, potentially via self-sovereign identity and verifiable credentials, may lead to greater data security but also raise concerns about privacy and anonymity, as seen in recent legal and ethical debates.
- While sovereign cloud initiatives aim to improve security and control over data access, the trade-off with online anonymity is evident, prompting discussions on how to balance identity verification without compromising individual privacy.
- The move towards stricter data controls and regional identity verification may offer opportunities to innovate in secure authentication methods, leveraging technology like zero trust architecture and decentralized identifiers via APIs.
- In this evolving landscape of digital sovereignty and identity management, APIs could serve as a vital tool in maintaining online security and privacy while adapting to changing regulatory landscapes and technological advancements.
- The article delves into the implications of the sovereign cloud movement on digital identity, highlighting the tension between enforcing compliance and protecting user privacy in an increasingly regulated and interconnected online environment.
Read Full Article
Like
TechJuice
247

Image Credit: TechJuice
Anubis Ransomware Now Wipes Data After Encryption, Experts Warn
- The Anubis ransomware has evolved to not only encrypt data but also destroy it, making recovery impossible, as per recent research by Cisco Talos.
- Unlike typical ransomware, Anubis overwrites files if encryption fails, giving victims the grim choice of paying the ransom or losing their data permanently.
- This advanced version of Anubis has been observed targeting various sectors like education, manufacturing, and technology, with the potential for further aggressive updates.
- The ransomware spreads through phishing emails, malicious attachments, and exploited remote services, moving laterally within networks and deleting files if there's any resistance.
- Experts suggest attackers may now be more interested in collecting ransom, making Anubis a significant threat to enterprises concerned with uptime and data integrity.
- Ransomware attacks are evolving to be more ruthless, with a shift towards including file destruction in their strategies, making traditional recovery methods insufficient.
- Cybersecurity experts recommend improving email filtering and regularly updating security measures as precautionary measures against threats like Anubis.
- Anubis ransomware signifies a larger trend of increasing ruthlessness among ransomware actors, emphasizing the need for proactive defense strategies.
- The post concluded that staying vigilant and taking preventive measures remain the primary defenses against Anubis ransomware.
- The research highlights the shift from mere data encryption to data destruction by Anubis ransomware, posing a significant challenge for victims trying to recover their files.
- Victims of Anubis ransomware are faced with a tough decision: pay the ransom or lose data permanently, as the malware wipes files if it fails to encrypt them.
- Anubis ransomware has been detected targeting multiple sectors through common entry points like phishing emails and compromised services, showcasing its widespread impact.
- The evolving nature of Anubis ransomware serves as a warning sign of the escalating tactics employed by ransomware operators to maximize extortion and data sabotage.
- With the threat landscape evolving towards destructive ransomware like Anubis, organizations are advised to bolster their cybersecurity defenses beyond traditional backup strategies.
- Anubis ransomware's destructive capabilities underscore the urgent need for organizations to prioritize cybersecurity measures to mitigate the risk of data loss and extortion.
- Experts emphasize the importance of proactive security measures and continuous vigilance in the face of evolving ransomware threats like Anubis.
- Given the evolving nature of ransomware threats such as Anubis, cybersecurity professionals stress the need for robust security practices to safeguard against data breaches and financial losses.
Read Full Article
14 Likes
Fintechnews
433

Image Credit: Fintechnews
Experian and GBG Join Forces to Tackle Identity Fraud in Australia and NZ
- Experian and GBG have expanded their partnership to enhance fraud prevention and identity verification services in Australia and New Zealand.
- The collaboration combines Experian’s data capabilities with GBG’s greenID platform for real-time identity verification across various sectors.
- The solution enables fast and secure identity checks using name, address, and date of birth matching without paperwork or in-person visits.
- Growing concerns around identity-related fraud prompt the move.
- Experian's report highlights that 71% of businesses in EMEA and APAC struggle to keep up with evolving fraud threats.
- 68% of businesses in Australia and New Zealand saw a rise in fraud last year, with identity verification as a top challenge.
- The partnership leverages GBG's past work with illion and is one of the first customer-facing outcomes of the integration.
- Mathew Demetriou, of Experian, highlights the focus on enhancing customer experience through technology.
- Carol Chris from GBG emphasizes the need for powerful tools to manage fraud risk and customer experience.
- The partnership aims to deliver innovative, robust, and user-friendly solutions to the market.
- The collaboration signifies the commitment to combat identity fraud and protect consumers and businesses.
- The partnership aims to assist clients in onboarding faster and staying ahead of fraud.
- Experian plans to make high-performing technology more accessible to clients through this partnership with GBG.
- Fraud risk management and customer protection are crucial in the rapidly evolving fraud landscape.
- The combined efforts reflect trust and alignment between GBG and Experian in delivering compliant solutions.
- The collaboration aligns with the shared goal of delivering robust and innovative solutions to combat fraud.
Read Full Article
26 Likes
Medium
48

Image Credit: Medium
Privacy Issues in Cybersecurity: How Residential Proxies Can Solve Them
- Privacy issues in cybersecurity include data breaches, tracking of online activities, and vulnerability on public Wi-Fi networks.
- Residential proxies offer solutions by masking real IP addresses, enhancing security, and enabling access to geo-blocked content.
- They help avoid surveillance, protect sensitive data, and bypass anti-scraping technologies effectively.
- Thordata's residential proxies provide global coverage, high anonymity levels, and automated IP rotation for enhanced security.
- Encrypted connections and data protection are prioritized by Thordata to ensure user security.
- Residential proxies are crucial for maintaining online anonymity, protecting data, and navigating geo-restrictions.
- Thordata offers reliable, secure, and efficient residential proxy services for individual users and businesses.
- Using Thordata's proxies can enhance online privacy, data security, and browsing experiences.
- Consider utilizing Thordata's residential proxies to safeguard your online activities effectively.
- Engage with the community to discuss experiences with residential proxies and enhance online privacy together.
Read Full Article
2 Likes
Bworldonline
79

Image Credit: Bworldonline
Need for cybersecurity experts grows as PH goes more digital, says DICT
- The Department of Information and Communications Technology (DICT) highlights the growing need for cybersecurity professionals as major infrastructure projects connect the Philippines digitally.
- DICT Secretary emphasized the importance of cybersecurity experts in defending against external threats faced by the country.
- About 60% of DICT's focus has been on cybersecurity following the May midterm elections.
- Cyberwarfare is emphasized as a critical concern affecting critical systems in the country.
- The National Intelligence Coordinating Agency (NICA) revealed 234 data breaches in high-level government agencies in 2025.
- Cyber-related crimes tripled in 2024, with reported complaints reaching 10,004 and financial losses totaling P198 million.
- The Cybersecurity Council of the Philippines (CSCP) was formalized to enhance digital resilience in collaboration with industry leaders and government offices.
- CSCP aims to promote cybersecurity awareness and facilitate public-private partnerships for enhanced digital security.
- DICT plans to triple national cell sites from 30,000 in partnership with telecom companies while prioritizing cybersecurity measures to fortify digital defenses.
- Efforts are ongoing to improve the accessibility and affordability of Starlink satellite internet in the Philippines, potentially positioning it as the second-largest market for the provider.
Read Full Article
4 Likes
For uninterrupted reading, download the app