Cyber Security News
Lastwatchdog
203

GUEST ESSAY: The AI illusion: Don’t be fooled, innovation without guardrails is just risk–at scale
- Artificial intelligence (AI) offers speed and precision at unprecedented scale, influencing various aspects of human life invisibly and without accountability.
- AI works based on patterns without understanding or thinking, posing risks when decisions are made without considering ethics or consequences.
- Experts like Guillaume Thierry and industry leaders such as Demis Hassabis and Geoffrey Hinton emphasize the importance of ethical frameworks for AI development.
- Nigel Toon highlights that AI performance must align with human values to prevent harm and injustice at scale.
- The potential biases and injustices embedded in AI systems, as exemplified by Amazon's recruitment tool, showcase the need for continual oversight and moral considerations.
- AI amplifies biases and injustices present in historical data, turning them into systemic issues that affect decision-making and societal structures.
- The dynamic nature of AI systems requires ongoing explainability and wisdom in their design and governance to address evolving risks and ethical concerns.
- Building AI responsibly means embedding wisdom, oversight, and accountability into the development process to ensure progress is accompanied by ethical considerations and foresight.
- The essay emphasizes the importance of leading with conscience and setting moral standards in AI advancement to prevent recklessness and promote responsible innovation.
- References to instances of biased AI tools and insights from AI experts underline the critical need for ethical governance in the AI landscape.
- The time is now to prioritize moral leadership in AI development to guide its impactful integration into society.
Read Full Article
12 Likes
Medium
358

Image Credit: Medium
Privacy in a Connected World: Navigating Smart Home Security
- Smart homes constantly collect and transmit data, posing security risks if not properly protected.
- Unsecured smart devices can be entry points for hackers, leading to unauthorized access and control of devices.
- Data collected by smart devices may be stored on external servers without explicit consent, raising privacy concerns.
- Lack of universal data privacy regulations puts the burden of protection on homeowners.
- To safeguard privacy in smart homes, it is crucial to prioritize security measures and user control.
- Okos emphasizes privacy and user control in its smart home solutions to ensure security and convenience.
- Security should be foundational in a connected world to prevent privacy infringements in smart homes.
- Smart home users are advised to stay informed, prioritize data privacy, and choose solutions that respect their privacy.
Read Full Article
21 Likes
Securityaffairs
415
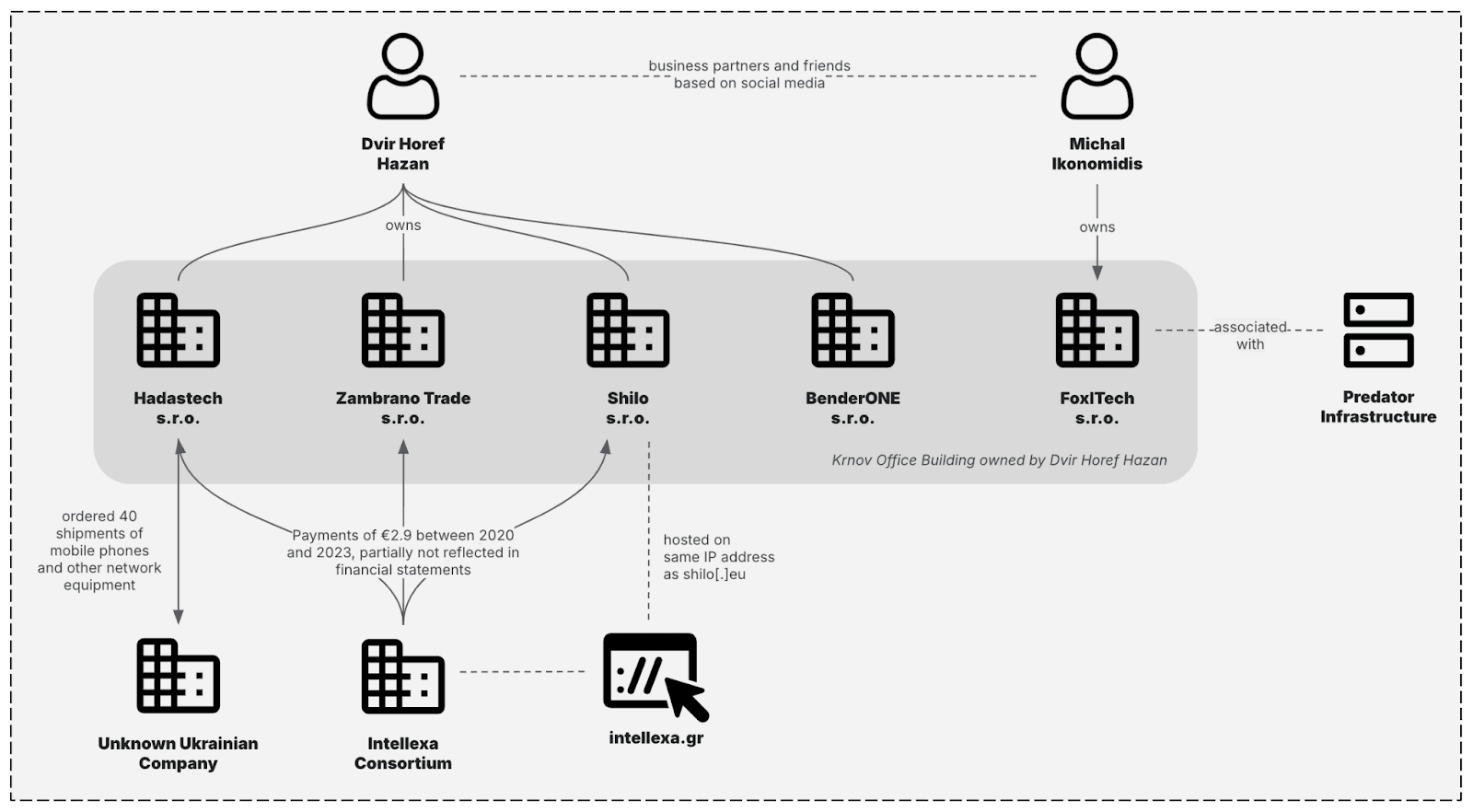
Image Credit: Securityaffairs
New Predator spyware infrastructure revealed activity in Mozambique for the first time
- Insikt Group analyzed the new Predator spyware infrastructure and found it is gaining users despite U.S. sanctions.
- Predator spyware has resurged after a decline and is being used in Mozambique.
- Over half of Predator's identified clients are in Africa, with links to the Intellexa Consortium.
- In March 2024, OFAC took actions against Intellexa Consortium members for their role in distributing Predator spyware.
- The Intellexa Consortium markets offensive cyber companies providing surveillance tools.
- Predator spyware enables compromising devices through zero-click attacks.
- Insikt Group uncovered a new Predator spyware infrastructure, including updates and high-tier components.
- The infrastructure showed renewed activity in various countries, including Mozambique.
- Predator's domains now use deceptive tactics and target specific regions.
- The spyware's infrastructure includes a five-tiered design to hide its origin and involves a Czech company.
- Operators use fake websites and other tactics to deceive targets.
- Insikt Group has monitored Predator spyware activity in over a dozen countries since March 2024.
- Some regions stopped activity due to exposure, but Mozambique emerged as a new user.
- Despite sanctions, Predator's continued use suggests the adoption of new evasion tactics.
- Public exposure and sanctions have likely impacted Intellexa's operations.
- Predator operators are using new tactics to avoid detection.
Read Full Article
24 Likes
Socprime
393

Image Credit: Socprime
What Are the Predictions of AI in Cybersecurity?
- By 2029, agentic AI is predicted to autonomously handle 80% of routine customer service inquiries, reducing costs by 30%.
- Agentic AI signifies a shift towards systems capable of independently executing tasks, impacting service interactions by automating engagement.
- AI plays a crucial role in modern cybersecurity, enabling proactive defense against advanced threats through real-time data processing and analysis.
- Growing threats from AI-driven cybercriminals highlight the importance of intelligent, adaptive, and automated security solutions to mitigate risks effectively.
- AI enhances network security by predicting, adapting, and identifying malicious behavior in real time, reducing false positives and alert fatigue.
- In data analytics, AI processes vast amounts of information to uncover hidden threats, prioritize alerts, and increase operational efficiency in cybersecurity.
- AI in cryptography offers opportunities to strengthen encryption algorithms and develop quantum-resistant techniques, presenting challenges and responsibilities for future innovation.
- Organizations are increasingly integrating AI into their cybersecurity strategies to automate tasks, improve detection engineering workflows, and enhance incident response capabilities.
- AI's future in cybersecurity includes integration with emerging technologies like blockchain and SOAR platforms, aiming for autonomous defense systems and more intelligent security ecosystems.
- The global cybersecurity industry faces a talent shortage, emphasizing the need for smarter tools and AI assistance to keep up with evolving threats and accelerate analyst development.
Read Full Article
23 Likes
Medium
415
Image Credit: Medium
How to Optimise Your GRC Fast
- GRC optimization is crucial for enhancing the efficiency and effectiveness of your GRC program.
- Transitioning to a more dynamic, outcome-driven GRC approach is essential for resilience.
- The GRC Optimization Framework facilitates continuous enhancement in performance, transparency, and business alignment.
- Identifying pain points and addressing key friction areas is the initial step in optimizing GRC.
- Connecting business priorities with risk themes can significantly enhance GRC effectiveness.
- Addressing weaknesses in the organization and aligning strategies is vital for GRC improvement.
- Implementing lean strategies and continuous evaluation are essential for optimizing GRC processes.
- Regularly monitoring metrics and progress is crucial for ongoing GRC enhancement.
- GRC Pulse dashboard can help in displaying trends, achievements, challenges, and future steps.
- Optimization is a cyclical process that requires constant refinement and evolution.
- Start small, focus on one phase at a time, and let momentum drive further enhancements in your GRC program.
Read Full Article
24 Likes
TechJuice
358

Image Credit: TechJuice
Hackers Exploit Google.com to Spread Stealthy Malware
- Cybersecurity experts have discovered hackers using Google.com, a trusted domain, to distribute hard-to-detect malware.
- Compromised e-commerce websites, especially on Magento, host a hidden script redirecting to a manipulated Google OAuth link.
- The malware hides in the callback parameter, executing obfuscated JavaScript to evade antivirus tools.
- The attackers exploit the trust in Google.com domain to avoid being flagged by security tools and browsers.
- The attack triggers only for real human behavior with keywords like 'checkout', opening a WebSocket connection to deliver harmful code.
- The attack is difficult to detect due to heavy code disguise, use of a legitimate domain, and dynamic execution.
- Users can mitigate risks by limiting third-party scripts, separating tasks on different browsers, keeping software updated, being cautious, and using behavior-based security tools.
- This campaign highlights the vulnerability of even trusted domains like Google.com to sophisticated cyberattacks, emphasizing the importance of informed security practices.
Read Full Article
21 Likes
Pymnts
375

Image Credit: Pymnts
Banks Fast-Track Merchant Acquiring to Cement Small Business Loyalty
- Banks are fast-tracking merchant acquiring strategies to strengthen small business loyalty.
- The focus is on allowing small businesses to accept card payments and diversify payment options within existing banking relationships.
- Financial institutions must plan ahead to enhance payment monetization strategies and secure regulatory approvals.
- Maverick Payments assists banks in overcoming regulatory and technical challenges when entering new business segments.
- Providing a comprehensive tech stack, Maverick supports merchants in payment processing, fraud prevention, and more.
- Improving cash flow and reducing the need for loans, payment acceptance is vital for sustaining small businesses.
- Enhanced due diligence and tailored services are crucial for different verticals to ensure safe merchant partnerships.
- Fraud prevention remains a key concern, with a focus on secure payment gateways and AI-driven risk management.
- Real-time payments adoption drives the use of AI and machine learning for enhanced risk management and compliance.
- Banks can leverage merchant acquiring strategies to generate fee income and offer seamless services through platforms like Maverick Dashboard.
Read Full Article
22 Likes
The Register
119

Image Credit: The Register
How collaborative security can build you a better business
- 95% of data breaches involve human error, highlighting the need for human-centric security.
- Organizations are urged to move beyond traditional security awareness training for better data defenses.
- Encouraging active collaboration between employees and security teams can lead to a 32% increase in profitability.
- In organizations with high security engagement, non-compliance among privileged access users decreases significantly.
- Line managers play a crucial role in shaping security culture and impacting team performance.
- Continuous, adaptive human risk management is recommended over one-time training sessions.
- Tracking behavioral changes and business impact is vital for effective security measures.
- Empowering line managers to champion security culture can significantly influence their teams.
- Creating feedback loops for employees to report security policy issues fosters collaboration and trust.
- Human-centric security not only enhances protection but also drives profitability.
- OutThink's 2025 Cybersecurity Human Risk Management Report offers valuable insights for transforming security culture.
- Building collaboration between security teams and employees is essential for a robust security framework.
- Inspiring line managers to champion security culture can yield positive outcomes for the organization.
- Genuine collaboration and open feedback mechanisms help employees feel valued and engaged in security solutions.
- The shift towards human-centric security can transform people into a strong defense and a competitive advantage for businesses.
Read Full Article
7 Likes
Dev
190

Image Credit: Dev
Data Security: Why Your Business Can't Afford to Ignore It
- Data security is crucial for businesses to protect information from unauthorized access and cyber threats.
- Failure to comply with regulations like GDPR and CCPA can lead to fines and reputational damage.
- Robust data security strategies include access controls, encryption, and threat detection measures.
- Data breaches can result in identity theft, financial loss, and reputational harm.
- Investing in data security is essential for business resilience, customer trust, and competitive advantage.
- Regular risk assessments help identify vulnerabilities and address potential risks proactively.
- Strong access controls limit unauthorized access and enhance data security and control.
- Data encryption protects sensitive information from unauthorized access.
- Employee training and awareness are crucial to prevent human errors leading to data breaches.
- Monitoring network activity and having an incident response plan are key for security incident management.
- Maintaining comprehensive data backups minimizes data loss and downtime in case of security incidents.
- Businesses should partner with experts to implement tailored data security solutions.
Read Full Article
11 Likes
Medium
269

Image Credit: Medium
The Security Risks of Using Online PDF Tools
- PDF editing can pose security risks, particularly with online tools that require document uploads to servers.
- Desktop software and mobile apps used for editing PDFs can also compromise privacy by collecting usage data and document content.
- Secure PDF editing is best done locally on your device to avoid data exposure.
- Modern browser-based tools like One23PDF allow for document processing without uploading files to servers.
- Choose tools that explicitly state 'no upload to servers' and prefer HTTPS-protected websites for security.
- Ensure tools have clear privacy statements and consider using private browsing mode for sensitive documents.
- Privacy-focused PDF editing tools are essential for specific industries like healthcare, legal, finance, and education to comply with regulations.
- Always be cautious of free services that may use your document data for purposes like advertising or AI training.
- Avoid uploading multiple sensitive documents to online services simultaneously to minimize risks.
- Clear your browser's download history after working with confidential documents and research the privacy policies of PDF editing tools.
- Implement secure alternatives like One23PDF's privacy-focused tools and educate users about the importance of secure document handling.
- It is crucial to prioritize security and privacy in PDF editing practices given the tightening regulations and evolving cyber threats.
- Secure PDF editing is not an option but a necessity to protect documents and clients' privacy.
- Begin securing your PDF workflow without delay to ensure complete privacy protection for your documents and clients.
Read Full Article
16 Likes
Tech Radar
84

Image Credit: Tech Radar
Synthetic ID document fraud is exploding worldwide thanks entirely to Generative AI: here's how to stay safe
- Synthetic identity document fraud is spreading globally due to the misuse of generative AI, with a 195% increase in fake document creation between Q1 2024 and Q1 2025.
- Europe saw a 378% surge in synthetic ID fraud, North America 311%, and MENA region 258%.
- Traditional document forgery is declining as scammers shift to AI-generated identities, which can be produced quickly.
- Most fraud, 76%, now occurs post-onboarding using methods like device spoofing and credential stuffing.
- Industries most affected include crypto, trading, transportation, fintech, and gambling, lacking strong safeguards to detect synthetic documents.
- AI-generated fake documents are becoming crucial tools for fraudsters, exposing flaws in verification systems.
- A rise in deepfake-related fraud is observed, with substantial increases in cases.
- Businesses are advised to use identity management software and multi-layered verification for enhanced protection.
- Consumers should consider reputable ID theft protection solutions and people search tools for added safety.
- North America saw a 1,100% increase in deepfake fraud cases, Europe 900%.
- Concerns are raised about the role of manipulated visuals in identity fraud, with high surges in nations like Hong Kong, Singapore, and Germany.
- Relying solely on KYC protocols may not suffice, demanding stronger security measures for individuals and organizations.
- Experts suggest the importance of safeguards in AI programs generating personal documents like passports and IDs.
- The article emphasizes using advanced security measures due to the rise in AI and deepfake-related fraud.
- Protecting against identity fraud requires a combination of tools and vigilance in verifying potentially malicious actors online.
Read Full Article
5 Likes
Tech Radar
309

Image Credit: Tech Radar
Stop using these 22 Android crypto and wallet apps ASAP, or you risk losing all your cryptocurrency
- Cyble Research and Intelligence Labs (CRIL) discovered a phishing campaign involving over 20 Android apps on the Google Play Store, designed to steal users' mnemonic phrases for cryptocurrency wallets.
- Malicious apps used the Median framework to convert websites into Android apps and displayed phishing URLs within the app code or privacy policy documents.
- These links led users to fake login pages resembling trusted services like PancakeSwap, SushiSwap, Raydium, and Hyperliquid, tricking victims into disclosing their private keys.
- The phishing infrastructure, centered around IP address 94.156.177.209, hosted over 50 other phishing domains, mirroring popular crypto platforms.
- Some malicious apps came from developer accounts previously linked to legitimate software, obscuring their true intent.
- To prevent such attacks, users are advised to download apps from verified sources, use reputable antivirus software, and avoid sharing sensitive information.
- Strong passwords, multi-factor authentication, and skepticism towards unsolicited links or requests are additional measures recommended for enhanced security.
- CRIL also highlighted that legitimate apps would never require a full mnemonic phrase during login.
- The list of 22 fraudulent apps to avoid includes fake versions of Pancake Swap, Suiet Wallet, Hyperliquid, Raydium, BullX Crypto, OpenOcean Exchange, Meteora Exchange, and others.
- The sophisticated nature of these phishing apps reinforces the importance of vigilance and caution while handling cryptocurrency transactions.
- Users must be wary of apps requesting sensitive data and should prioritize safety measures to safeguard their digital assets.
- Precautionary steps such as verifying app sources, using robust security tools, and staying informed about potential threats are crucial in mitigating risks associated with malicious apps.
- Avoiding interaction with suspicious links and maintaining a proactive approach to cybersecurity can prevent falling victim to such fraudulent schemes.
- By educating users about common tactics employed by cybercriminals, CRIL aims to reduce the success rate of phishing campaigns targeting cryptocurrency holders.
- Immediate action is necessary to avoid potential loss of funds and protect personal information from unauthorized access.
- Engaging in safe digital practices and remaining vigilant against evolving threats are paramount in safeguarding cryptocurrency investments and ensuring financial security.
- Considering the prevalent nature of cyber attacks, staying informed and employing good cybersecurity hygiene are essential for maintaining the integrity of digital assets.
- It is advisable for individuals to exercise caution and skepticism towards unexpected requests for sensitive data or login credentials to prevent falling prey to sophisticated phishing attempts.
Read Full Article
18 Likes
Medium
429

Image Credit: Medium
Day 64: Automating Cybersecurity Tasks with Cron Jobs in Bash
- Cron jobs are useful for automating cybersecurity tasks in bash.
- Each cron job is defined by five time fields followed by the command to run.
- The five stars in a cron job represent minutes, hours, days, months, and weekdays.
- Users can set these values to control when the job runs, such as every minute or on specific days or times.
- One example is backing up authentication logs daily at 1:00 AM using a cron job.
- Another example involves scheduling a weekly system scan on Mondays at 3 AM.
- Automating the saving of firewall configurations on the 1st of every month at 2 AM is also possible.
- Setting up a cron job to check for rootkits every Sunday at 4 AM helps maintain system security.
- Cron jobs ensure that tasks are completed automatically, providing a log trail for future debugging or auditing needs.
- Confirming that cron jobs trigger correctly is essential to ensure tasks are executed as expected.
- Automating tasks using cron jobs enables users to proactively address cybersecurity threats, even during inactive hours.
- The article highlights the importance of scheduling tasks to enhance cybersecurity measures.
- Users are encouraged to leverage cron jobs to improve their system's security posture.
- Learning to automate tasks through cron jobs helps users be proactive in addressing potential security vulnerabilities.
- On Day 64, readers not only learn to schedule tasks but also to enhance threat mitigation strategies while being less active.
- Automating tasks through cron jobs allows users to stay vigilant against threats even while they are not actively monitoring their systems.
Read Full Article
25 Likes
Medium
225

Image Credit: Medium
Introduction to Malware Analysis Course — From Beginner to Pro
- The Introduction to Malware Analysis Course is a hands-on, lab-driven program designed to take participants from beginner to pro in dissecting actual malware and understanding sophisticated reverse engineering tools.
- The course is practical, focusing on real-world scenarios and threats in a fully isolated environment, suitable for individuals with foundational knowledge and curiosity regardless of their current level.
- It is divided into key phases that progressively build upon each other, offering participants the opportunity to dissect complex malware, write detection rules, and use professional tools and workflows even in real-world job settings.
- Participants will learn to stay ahead of the evolving cyber threat landscape by gaining skills to analyze malware intelligently and thoroughly.
- Enrolling in the course requires readiness, and it is ideal for individuals interested in enhancing their malware analysis capabilities.
Read Full Article
13 Likes
Securityaffairs
137

Image Credit: Securityaffairs
Canada’s second-largest airline WestJet is containing a cyberattack
- Canada's second-largest airline, WestJet, has experienced a cyberattack affecting internal systems and the company's app.
- The airline is investigating the cybersecurity incident with specialized internal teams and coordinating with law enforcement and Transport Canada.
- The attack has not affected operational safety, and efforts are focused on protecting sensitive personal data.
- Guests and employees are advised to be cautious when sharing personal information.
- WestJet is working to safeguard information and ensure the safety of operations while investigating the incident.
- No technical details about the attack have been disclosed by the airline.
- The cyber threats targeting Canada's critical infrastructure are on the rise, with recent incidents involving Nova Scotia Power, Emera, Air Canada, and Suncor Energy.
Read Full Article
8 Likes
For uninterrupted reading, download the app