Cyber Security News
Siliconangle
338

Image Credit: Siliconangle
Aim Security details first known AI zero-click exploit targeting Microsoft 365 Copilot
- Aim Security Ltd. has uncovered the first known zero-click AI vulnerability, dubbed EchoLeak, targeting Microsoft 365 Copilot, allowing attackers to exfiltrate data without user interaction.
- EchoLeak exploited an 'LLM Scope Violation' in Copilot's generative AI tool, using crafted markdown syntax to bypass security defenses and retrieve sensitive data.
- The exploit leveraged Microsoft's trusted domains to embed malicious content in emails processed by Copilot, posing a significant threat to internal data security.
- The attack required no user interaction, operating behind the scenes with Copilot's automation triggering the entire data exfiltration process.
- Aim demonstrated a proof-of-concept showing how internal documents could be leaked undetected, prompting Microsoft to acknowledge the issue.
- There is no evidence of the vulnerability being exploited in the wild, but cybersecurity experts warn of future risks as AI services are susceptible to similar attacks.
- Responding to the disclosure, Microsoft addressed the vulnerability responsibly, highlighting the need for enhanced security measures in AI systems.
- Security experts emphasize the broader implications of such vulnerabilities for sectors like government, defense, and healthcare, where AI assistants can be manipulated by attackers.
- AI assistants processing untrusted inputs alongside internal data are vulnerable to scope violations, indicating a systemic flaw that requires stricter measures for content separation.
Read Full Article
20 Likes
Medium
80

Image Credit: Medium
Let’s Talk About Girl Gamers!
- Girls gaming habits help increase their social connections compared to boys who tend to have online friends rather than IRL friends.
- Negative stereotypes about girl gamers have little impact on their performance or attitudes, aiding in building resilience against gender-related stereotypes.
- Gaming contributes positively to female brain development, enhancing visual attentional resources and closing the gender gap in spatial attention and mental rotation skills.
- Girls gaming from an early age manage visual attention better, eliminating performance gaps with boys due to gaming.
- Boys have a tendency to get 'addicted' to gaming more than girls, as per research findings.
- Encouraging girls to game can lead to lasting neurological impacts and empowerment in the gaming industry.
- Savvy Cyber Kids recommends not discouraging girls from gaming and suggests using negative online interactions as learning opportunities to navigate real-world challenges.
Read Full Article
4 Likes
Medium
262

Image Credit: Medium
Netflix Docuseries “Web of Lies: A Murder in D.C.” Discussion Questions
- The second episode of Netflix’s docuseries “Web of Make Believe: Death, Lies, and the Internet” delves into conspiracy theories surrounding the death of Seth Rich, a DNC worker.
- Initially thought to be a botched robbery, internet speculation grew, suggesting he was murdered for political reasons.
- Misinformation spread, including claims from Russian intelligence and implications from the founder of Wikileaks.
- The episode portrays the chaos caused by out-of-control information and the role of conspiracy theories during traumatic events.
- Reporter Kelly Weill highlights that conspiracy theories often arise in challenging moments when explanations are elusive.
- These theories are seen as humans' way of seeking patterns in the world, but they can also generate undue panic.
- Individuals may exploit theories for personal gain, leveraging them for public attention.
- The Seth Rich case underscores the importance of researching and drawing conclusions based on facts, rather than falling for misleading narratives.
Read Full Article
15 Likes
Medium
298

Image Credit: Medium
What is Social Media Usage Doing to Our Children and Teens?
- Children and teens are growing up in a unique social media-driven world where they face pressures and risks like cyberbullying.
- Social media is integral to how they express themselves and interact globally, but it comes with downsides.
- Teens' profiles are crucial to their self-image, leading to judgments on appearance, friends, and interactions.
- Research highlights negative impacts of social media on mental health, such as depression and anxiety disorders.
- Passive users monitoring others' posts are linked to lower self-esteem, while active users show less depression.
- Girls may be more affected by social media standards of beauty than boys, impacting them positively or negatively.
- Children spend 5–8 hours daily on social media, replacing physical activities and face-to-face interactions.
- Parents now have the task of guiding their children on online privacy and time management, using tools like Bark for monitoring.
- Encouraging breaks from social media, creating non-digital activities, and promoting outdoor time are suggested for parents.
- Addressing the impact of social media on children's well-being is crucial in the digital age.
Read Full Article
17 Likes
TechJuice
325

Image Credit: TechJuice
Scammers Using AI To Steal Loans And Fake Classes
- Scammers are using AI to exploit student loan fraud and enroll people in fake classes.
- AI-powered bots mimic real applicants, automate processes from applications to coursework.
- These sophisticated bots can participate in classes, attend lectures, submit assignments without human intervention.
- The primary goal is to divert financial aid - loans, grants - to scammer accounts.
- Individuals face identity theft and fraudulent debt under their names due to these scams.
- Online education normalization and AI tools contribute to the rapid growth of this issue.
- California community colleges reported 1.2 million suspicious applications leading to significant financial loss.
- Scammers use AI to automate complex identity theft and fraud, posing a serious threat to online education.
Read Full Article
19 Likes
Medium
374

Image Credit: Medium
“HACKERONE” I Didn’t Break It — I Just Showed It Was Already Fragile
- The author found a vulnerability using an invisible Unicode character in JSON payloads sent to Hostinger's configuration API.
- The phantom key bypassed validation and reached the backend, allowing injection of unauthorized parameters.
- The system accepted the payload with the Unicode character, demonstrating the flaw in the system's validation logic.
- Despite providing a detailed report, code, video proof, and evidence of impact, the author was repeatedly dismissed by Hostinger.
- The vulnerability allowed for unauthorized changes in account tiers without valid authorization.
- The author exposed a logic-level vulnerability that posed a real business risk, but Hostinger downplayed its significance.
- The author's meticulous work was dismissed by Hostinger, highlighting how vulnerabilities can be overlooked if they are not straightforward or cause immediate disruption.
- Hostinger asked the author to close the report to avoid damaging their reputation, showing a reluctance to acknowledge the severity of the vulnerability.
- Despite following best practices in reporting the vulnerability, the author's findings were ignored, emphasizing the challenges faced by researchers in getting their concerns addressed.
- This experience serves as a reminder that even legitimate and well-documented vulnerabilities can be disregarded if they are not convenient for the affected system.
Read Full Article
22 Likes
Siliconangle
432
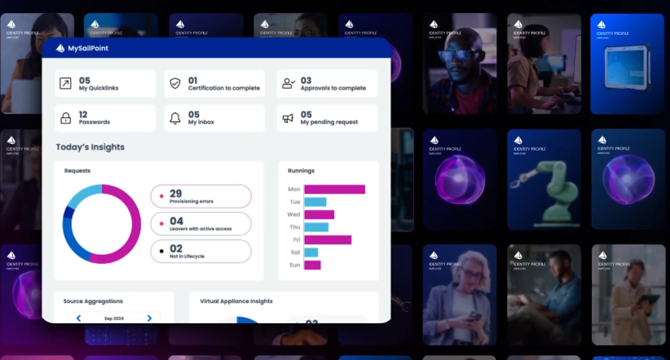
Image Credit: Siliconangle
SailPoint shares jump 14%+ on strong first-quarter earnings
- Shares of cybersecurity provider SailPoint Technologies Inc. surged over 14% after exceeding expectations with its first-quarter earnings and raising full-year guidance.
- SailPoint's revenue rose by 23% in the fiscal first quarter to $230 million, driven by a 27% year-over-year growth in the subscription business to $215 million.
- The company's annualized SaaS revenue grew by 39% year-over-year, surpassing $500 million in annual sales and outpacing other segments.
- SailPoint reported an adjusted profit of a penny per share, contrary to analysts' expectations of a penny per share loss.
- The company's dollar-based net retention rate was at 115%, and it experienced increased demand from large enterprises, with the number of customers spending over $1 million annually rising by 62%.
- CEO Mark McClain attributed the strong quarter to customer base expansion and adoption among Fortune 500 and Forbes Global 2000 companies.
- SailPoint upgraded its adjusted profit outlook to 16-20 cents per share and raised its revenue projection to $1.034-$1.044 billion for the fiscal year.
Read Full Article
25 Likes
Securityaffairs
271

Image Credit: Securityaffairs
Operation Secure: INTERPOL dismantles 20,000+ malicious IPs in major cybercrime crackdown
- INTERPOL conducted Operation Secure, targeting malicious IPs tied to info-stealing malware.
- The operation, held from January to April 2025, involved 26 countries and partners like Group-IB, Kaspersky, and Trend Micro.
- 20,000+ malicious IPs/domains were dismantled, with 41 servers seized and 32 arrests made.
- Authorities alerted over 216,000 victims for securing accounts after the operation.
- Vietnam, Sri Lanka, Nauru, and Hong Kong were among the countries where arrests and seizures took place.
- Vietnam arrested 18 suspects, Sri Lanka and Nauru made 14 arrests, and Hong Kong Police exposed phishing servers.
- INTERPOL emphasized the importance of collaborative action against cyber threats during Operation Secure.
Read Full Article
16 Likes
Medium
227

Image Credit: Medium
How to Fortify Cloudflare Against Brute-Force and Credential Stuffing Attacks
- Cloudflare's Under Attack Mode is a blunt-force approach that can frustrate real users and slow down legitimate traffic.
- Default Cloudflare protections may not be sufficient to stop credential stuffing attacks.
- Attackers can mimic normal user behavior to evade automated defenses.
- Proactive defenses against brute-force and credential stuffing attacks include setting up specific rules and WAF expressions.
- It's important not to set thresholds too low to avoid blocking legitimate login attempts.
- Automating early-warning systems can help react to threats before users are impacted.
- Under Attack Mode should be a last resort, with rate limiting, bot management, and WAF rules being more proactive defenses.
- Tuning Cloudflare setup is crucial as attackers do not wait for manual reactions.
Read Full Article
13 Likes
Siliconangle
66

Image Credit: Siliconangle
The cybersecurity workforce is shifting — AI agents are leading the charge
- Amazon is redefining security by integrating AI, physical safety, and public-private collaboration to combat digital threats.
- Steve Schmidt, Amazon's Chief Security Officer, emphasizes the importance of considering physical security in addition to digital security.
- Amazon's security posture is described as proactive, AI-driven, and deeply integrated across physical and digital realms.
- AI agents are used by Amazon for proactive threat detection, simulate attackers and defenders, and respond swiftly to attacks.
- Defensive agents in Amazon generate digital signatures quickly to prevent future attacks, transforming the defense of systems.
- Although AI enhances accuracy and speed, human oversight is crucial for validating actions before deployment according to Schmidt.
- Some AI agents could become fully autonomous in low-risk environments, but high-stakes systems will still require human supervision.
- As a paid media partner for the AWS Summit Washington, DC event, TheCUBE conducted an exclusive interview with Steve Schmidt discussing AI agents for cybersecurity at Amazon.
Read Full Article
4 Likes
Tech Radar
271

Image Credit: Tech Radar
Millions of patients possibly at risk due to poor passwords at healthcare orgs - here's how to stay safe
- A report by NordPass and NordStellar reveals poor password practices in the healthcare industry, leading to immense risks for patient data.
- Analysis of 2.5TB of data from various sources found healthcare organizations relying on predictable or weak passwords.
- Commonly used weak passwords in healthcare include '123456', 'P@ssw0rd', 'password', and more, making systems vulnerable to cyberattacks.
- Weak passwords like personal names or simple number patterns are targets for brute-force attacks, allowing cybercriminals to compromise networks.
- One successful breach can lead to extensive damage, such as data exposure, malware infections, and ransomware threats.
- Healthcare institutions are advised to implement strong password policies, avoid default passwords, use password managers, provide staff training, and enable 2FA.
Read Full Article
16 Likes
Wired
316

Image Credit: Wired
How Waymo Handles Footage From Events Like the LA Immigration Protests
- During the LA immigration protests, Waymo robotaxis were vandalized and set on fire, prompting the company to temporarily shut off service in certain areas.
- Waymo's advanced driverless cars have 29 external cameras and unspecified internal cameras, raising concerns about potential surveillance on protestors.
- The company has shared video footage with police in response to legal requests, but details on compliance are undisclosed.
- Waymo's policy is to challenge overly broad or questionable data requests, emphasizing data sharing for legal compliance and safety.
- It is uncertain if any footage from the vandalized Waymo cars in LA was destroyed, and the storage location of collected data remains unspecified.
- Waymo does not specify the retention period for camera footage nor disclose details on data storage practices.
- The company declined to provide information on internal cameras, footage retention duration, or past sharing of footage with law enforcement.
- Waymo's robotaxi service operates in select U.S. cities and has complied with law enforcement requests for footage in criminal investigations.
- Instances of Waymo providing footage to police for cases like road rage incidents and murders have been reported in Arizona and San Francisco.
- Waymo's video recording practices are not unique, as self-driving vehicles utilize various data sources, with other companies like Cruise also sharing footage with law enforcement.
Read Full Article
19 Likes
TechCrunch
316

Image Credit: TechCrunch
US government’s vaccine website defaced with AI-generated content
- The U.S. Department of Health and Human Services (HHS) vaccine information website has been defaced with AI-generated spam, mostly related to gay-themed and LGBTQ+ posts.
- The website has been hosting this content since at least May 12, according to an archived version.
- It's unclear who is responsible for the defacement or the purpose behind it other than pushing spam.
- Official U.S. government domains have been previously hijacked for hosting scam ads and hacking services.
- The HHS website is part of a broader spam operation, involving websites of NPR, Nvidia, and Stanford University, all leading to a nonsense SEO spam page hosted on wowlazy.com.
- 404 Media journalist Sam Cole reported on this spam operation.
- HHS did not reply to inquiries from TechCrunch about the incident.
Read Full Article
19 Likes
TechCrunch
374

Image Credit: TechCrunch
Whole Foods warns of shortages after cyberattack at its primary distributor UNFI
- Whole Foods is facing shortages due to a cyberattack at its primary distributor, United Natural Foods (UNFI), which is experiencing a nationwide technology system outage.
- The cyberattack is affecting UNFI's ability to select and ship products, impacting delivery schedules and product availability.
- Whole Foods instructed staff to limit communication with customers and cite 'temporary supply challenges' as the only approved response.
- UNFI is gradually restoring its systems and aims to increase capacity over the coming days.
- The company disclosed the cyberattack to federal regulators and took its network offline after detecting the intrusion.
- TechCrunch observed empty shelves at some Whole Foods and other grocery stores reliant on UNFI.
- The full impact of the cyberattack on stores and customers may not be evident until later this week.
- Whole Foods spokeswoman mentioned they are working on restocking shelves quickly and apologized for any inconvenience caused.
- UNFI's net sales for the quarter ended May 3, 2025, were reported at $8.1 billion.
- Readers with information regarding the cyberattack or impacted corporate customers can contact the reporter via encrypted message.
- The story was first published on June 10 and updated with information on UNFI's recovery.
- Whole Foods did not specify how quickly the situation may be resolved as UNFI works to bring back ordering and receiving capabilities.
- The cyberattack has led to disruptions in grocery supply chains, potentially affecting stores across the U.S. and Canada.
- Reports of empty shelves have emerged, signifying ongoing challenges faced by retailers reliant on UNFI.
- UNFI CEO disclosed taking the entire network offline following the intrusion, aiming to restore services and meet customer expectations.
- The impacts of the cyberattack may escalate through the week as UNFI continues its recovery efforts.
Read Full Article
22 Likes
Pymnts
357

Image Credit: Pymnts
WhatsApp Submits Evidence Supporting Apple in UK Encryption Case
- WhatsApp has joined a legal challenge against the U.K. government's demand for access to encrypted customer data owned by Apple.
- The order was issued under the U.K.'s Investigatory Powers Act by the U.K. Home Office in January.
- Apple responded by withdrawing iCloud Advanced Data Protection from the U.K. and launched a legal challenge.
- Two human rights campaign groups, Privacy International and Liberty, also filed a legal action against the demand.
- WhatsApp stated that it would challenge any attempt to weaken encryption and support people's right to private online conversations.
- The U.K. Home Office has not specifically targeted WhatsApp with a similar order like the one given to Apple.
- A London court hearing related to Apple's appeal was held in secret, with media barred from attending.
- Security Minister Dan Jarvis has not confirmed the order's existence but mentioned the importance of balancing privacy and security.
- Authorities argue that strong encryption can hinder investigations into serious crimes such as terrorism and child exploitation.
- In April, the Investigatory Powers Tribunal revealed that Apple is contesting the order and denied a request to keep case details confidential.
Read Full Article
21 Likes
For uninterrupted reading, download the app