Cyber Security News
Socprime
405

Image Credit: Socprime
CVE-2025-33053 Exploitation: A Critical WebDAV Zero-Day RCE Vulnerability Actively Weaponized by Stealth Falcon APT Group
- A critical zero-day RCE vulnerability (CVE-2025-33053) in Microsoft Windows is actively exploited by the Stealth Falcon APT group. The flaw enables RCE through manipulation of the system's working directory and advanced anti-analysis techniques.
- Exploitation of vulnerabilities as initial attack vectors has increased by 34% in 2025, leading to more security breaches.
- Stealth Falcon's campaign targets high-profile entities in the Middle East and Africa, deploying custom implants, keyloggers, stealth backdoors, and the Horus Agent for cyber espionage.
- The attack flow involves phishing emails with malicious URL files exploiting CVE-2025-33053 to execute malware deployment from the adversary's WebDAV server.
- CISA has added CVE-2025-33053 to its KEV catalog with a patch release by Microsoft on June 10, 2025, emphasizing the importance of prompt mitigation measures.
- Recommendations include updating Windows systems, training staff against spear-phishing, monitoring WebDAV traffic, and implementing security solutions to detect unauthorized activities.
- The significance of patching and threat monitoring is emphasized due to the critical risks posed by the widespread use of WebDAV in enterprise environments.
- Stealth Falcon's exploitation highlights their advanced capabilities and strategic focus on high-value targets, necessitating proactive defense measures and continuous monitoring.
- The SOC Prime product suite offers comprehensive defense solutions backed by zero-trust principles, AI, automation, and actionable threat intelligence for global organizations.
Read Full Article
24 Likes
Socprime
173

Image Credit: Socprime
CVE-2025-33073: Windows SMB Client Zero-Day Lets Attackers Gain SYSTEM Privileges
- The number of discovered vulnerabilities is growing at an unprecedented pace, with over 21,000 new CVEs recorded by NIST this year and a projected 49,000+ by year’s end.
- Microsoft addressed a critical zero-day vulnerability (CVE-2025-33073) in its latest Patch Tuesday release, impacting the Windows SMB client.
- Vulnerability exploitation was a common initial access vector for attackers in 2024, emphasizing the need for constant monitoring and proactive defense.
- Security professionals can access threat intelligence on SOC Prime Platform to identify and respond to attacks, including those exploiting zero-day vulnerabilities.
- CVE-2025-33073 allows attackers to escalate privileges to the SYSTEM level on Windows devices through the SMB protocol's improper access controls.
- An attacker can trick a machine into authenticating to a rogue SMB server, granting them SYSTEM-level access and control over the compromised system.
- Exploiting CVE-2025-33073 enables attackers to disable security tools, access sensitive data, install malware, and move laterally within networks.
- Immediate patching or enabling server-side SMB signing through Group Policy can mitigate the risks associated with this vulnerability.
- The SOC Prime Platform offers AI-powered technologies to help organizations detect and prevent attacks like zero-day exploitations proactively.
Read Full Article
10 Likes
Securityaffairs
436

Image Credit: Securityaffairs
Over 80,000 servers hit as Roundcube RCE bug gets rapidly exploited
- A critical remote code execution (RCE) vulnerability in Roundcube, tracked as CVE-2025-49113, was exploited by threat actors just days after the patch release, affecting over 80,000 servers.
- Roundcube, a popular webmail platform, has been targeted by advanced threat groups in the past, exploiting vulnerabilities for stealing login credentials and spying on communications.
- The vulnerability, with a CVSS score of 9.9, was discovered by Kirill Firsov and allows attackers to run malicious code on affected systems.
- The flaw in Roundcube Webmail before versions 1.5.10 and 1.6.x was found in the program/actions/settings/upload.php file.
- The vulnerability has been patched in versions 1.6.11 and 1.5.10 LTS.
- Approximately 53 million hosts, including systems like cPanel, Plesk, ISPConfig, and DirectAdmin, are impacted by the flaw.
- Positive Technologies researchers have confirmed the exploitability of CVE-2025-49113 in Roundcube and advise immediate updating to the latest version.
- The Shadowserver Foundation noted that around 84,000 unpatched Roundcube instances are exposed on the Internet, posing a significant risk.
- Data from Shadowserver indicates that over 84,000 Internet-facing servers are still vulnerable to the RCE flaw in Roundcube.
- The vulnerability has been a target for possible state actors in targeted attacks, emphasizing the critical need for patching.
- The situation underscores the importance of prompt software updates to mitigate cybersecurity risks and protect against potential exploitation.
- Users are urged to follow security recommendations and apply patches promptly to safeguard their systems and data.
- The security community continues to monitor the situation closely and raise awareness about the implications of unpatched vulnerabilities.
- For further updates, follow security experts on Twitter: @securityaffairs and Facebook for the latest cybersecurity news.
- Stay informed about emerging threats and best practices in cybersecurity to enhance digital defense measures.
Read Full Article
26 Likes
Siliconangle
271
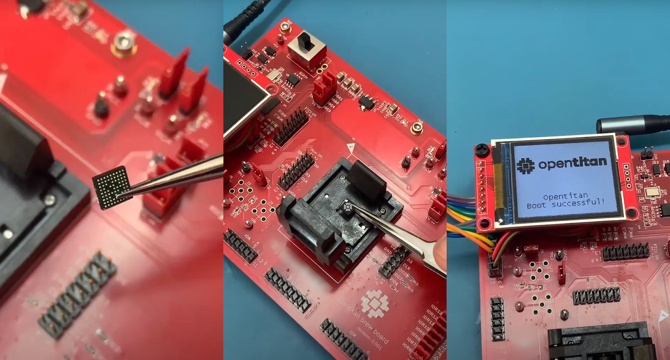
Image Credit: Siliconangle
ZeroRISC raises $10M to expand open-source silicon security platform
- ZeroRISC Inc. has secured $10 million in funding to expand its open-source silicon security solutions and Integrity Management Platform across the silicon supply chain.
- The startup, founded in 2023 by Dominic Rizzo, offers a full-stack security solution starting at the silicon level with a commercial-grade chip based on the OpenTitan root of trust.
- This chip verifies device boot integrity and prevents unauthorized code execution, providing immutable and verifiable trust, crucial for regulatory compliance and cybersecurity demands.
- ZeroRISC also provides the Integrity Management Platform, combining silicon hardware, embedded software, and cloud-based management tools for enhanced security.
- Their Rust-based embedded OS enforces strict security policies, isolation, and secure ownership transfer, giving device owners control over security rules.
- The platform tracks device integrity through the supply chain and in-field lifecycle, offering real-time attestation and policy management at scale.
- ZeroRISC has integrated post-quantum cryptography using the SPHINCS+ algorithm for firmware signing, ensuring future-proof security in a post-quantum world.
- The $10 million seed funding was led by Fontinalis Partners with participation from other investors, including industry veterans and angel investors.
- Experts commend ZeroRISC for bringing open-source technology to enterprise customers with a focus on secure by default devices.
Read Full Article
16 Likes
Medium
307

Image Credit: Medium
How to Protect Your Data Online: A Complete Guide
- Using strong and unique passwords is essential to protect your online accounts from hackers. Avoid using the same password across multiple sites.
- Enable two-factor authentication (2FA) to add an extra layer of security to your important accounts like email and banking.
- Be cautious of phishing scams, where cybercriminals attempt to trick you into divulging sensitive information. Verify sender details and avoid clicking on suspicious links.
- Regularly update your software to patch security vulnerabilities and protect your devices from exploits.
- Avoid using public Wi-Fi for sensitive transactions to prevent data interception by hackers. Consider using a Virtual Private Network (VPN) for added security.
- Limit the personal information you share online to minimize the risk of identity theft and social engineering attacks.
- Opt for encrypted messaging apps like Signal and secure browsers such as Firefox or Brave to enhance your privacy online.
- Back up your data regularly using cloud storage or external hard drives to guard against data loss due to various factors.
- By following these practices consistently, you can reduce security risks and have better control over your online data.
- For more cybersecurity tips and knowledge, check out https://blogginz.com/
Read Full Article
18 Likes
Medium
164

Image Credit: Medium
Who Owns What in Your GRC Plan?
- Building a GRC program requires clear roles and responsibilities to avoid slowdowns and missed controls.
- The article highlights the importance of defining core GRC roles, such as governance leaders, risk analysts, and control owners.
- It emphasizes the need for clarity and purpose in each role to ensure the program's effectiveness.
- The guide provides insights on how to address challenges, scale roles as organizations grow, and promote cross-functional collaboration for efficient GRC management.
Read Full Article
9 Likes
Medium
289

Image Credit: Medium
Tiny Habits
- In 2010, a coder created a small app in his dorm room, which later turned into Instagram sold for $1 billion.
- You don't need a large following, expensive equipment, or a degree to start; what you need is momentum.
- Small actions compound into habits, habits lead to mastery, and mastery opens doors for opportunities.
- Begin with imperfect starts, take small steps, and over time, you will become unstoppable. Share your 'tiny first step' story to inspire others.
Read Full Article
17 Likes
Pymnts
26

Image Credit: Pymnts
Retail Brands Risk Losing Billions When Checkout Processes Fall Short
- Retail brands are at risk of losing billions when checkout processes are not optimized, even with a focus on user experience and brand loyalty in global eCommerce.
- Recent findings show that 84% of shoppers find one-click checkout important, which can boost authorization rates by over 10% and enhance user experience.
- Cross-border commerce is growing, but 72% of merchants report higher failure rates in international payments compared to domestic ones due to outdated fraud filters and lack of localized payment options.
- Checkout optimization is crucial for revenue and long-term loyalty, and companies need to view it as a strategic lever by investing in the right payments infrastructure to improve conversions and reduce payment failures.
Read Full Article
1 Like
Pymnts
361

Image Credit: Pymnts
Visa: Issuer Customer Lifetime Value Hinges on Personalization and Real-Time Experiences
- The PYMNTS Intelligence and Visa DPS report focused on what separates the best card issuers in driving customer lifetime value.
- Personalization, real-time experiences, and improving fraud performance are key components for issuers to enhance customer relationships.
- Data and artificial intelligence play crucial roles in targeting customer interactions and boosting customer lifetime value.
- Visa's innovations, like the Flexible Credential, aim to improve customer relationships and offer seamless payment experiences.
Read Full Article
21 Likes
Hackernoon
405

Image Credit: Hackernoon
Mastering MCP Server Management with ToolHive
- ToolHive simplifies MCP server management and deployment by integrating container security and configuration automation.
- ToolHive operates as a CLI tool running on Go, ensuring simple installation and use.
- Installation of ToolHive involves building it from source, requiring dependencies like golang, git, and make.
- Configuring the initial MCP server involves enabling auto-discovery and launching tools like Fetch MCP server.
- ToolHive supports GitHub tokens with encrypted secrets, allowing secure handling of sensitive information.
- The tool includes an integrated MCP registry for easy browsing and access to available servers.
- Custom MCP servers can be configured and run using images and protocols such as uvx://, npx://, and go://.
- ToolHive offers permission customization using JSON profiles for setting specific access rights.
- A preview feature allows deployment of MCP servers in Kubernetes using an Operator.
- Manual client enrollment is possible in ToolHive for cases when auto-discovery is not operational.
- ToolHive is recommended for managing MCP servers effectively, with resources available on GitHub and documentation for guidance.
Read Full Article
24 Likes
TechBullion
160

Image Credit: TechBullion
Navigating Cybersecurity Education in Texas: Programs, Skills, Costs, and Careers
- Texas offers bachelor’s and master’s degrees in cybersecurity through online, hybrid, and campus-based formats, with accreditation from organizations such as ABET or SACSCOC ensuring academic quality and employability.
- Curricula focus on technical skills, managerial knowledge, and soft skills, and programs offer real-world case studies and teamwork to prepare graduates for cybersecurity challenges.
- Costs for cybersecurity degrees in Texas vary, with in-state tuition at public universities averaging $7,000–$12,000 per year and out-of-state students paying $20,000–$30,000, with additional fees for labs and materials.
- Hands-on training, internships, certifications, and networking opportunities help Texas cybersecurity graduates stand out in roles like security analysts, penetration testers, with a projected growth of 32% in the next five years.
Read Full Article
9 Likes
TechJuice
370

Image Credit: TechJuice
Rust‑Based Myth Stealer Malware Spreads via Fake Gaming Sites
- Myth Stealer is a Rust-based malware that steals sensitive data such as passwords and browser cookies.
- It spreads through fake gaming websites offering 'free cheats' or 'cracked games'.
- Myth Stealer is equipped with evasion features, anti-debugging tools, and frequent updates by its developers.
- It operates as Malware-as-a-Service on Telegram, targeting gamers and digital creatives through infected downloads.
Read Full Article
22 Likes
Securityaffairs
66

Image Credit: Securityaffairs
A flaw could allow recovery of the phone number associated with any Google account
- A vulnerability was discovered that could potentially allow for the recovery of the phone number associated with any Google account through a brute force attack.
- The flaw was found in a deprecated, JavaScript-disabled version of Google's username recovery page that lacked anti-abuse protections.
- By bypassing CAPTCHA rate limits and using BotGuard tokens, an attacker could rapidly test combinations of a user's phone number, revealing recovery details linked to a Google account display name.
- After reporting the issue to the vendor, a reward was given to the security researcher, and mitigations were rolled out to address the vulnerability.
Read Full Article
4 Likes
Nordicapis
436

Top 10 API Gateways in 2025
- The market for API gateways in 2025 offers a variety of options catering to different needs in terms of security, business functions, and AI integrations.
- Leading API gateways include Kong Gateway, known for its scalability, extensibility, and Kubernetes integrations, ideal for organizations requiring flexibility and high performance.
- Zuplo is a developer-friendly API gateway designed for rapid deployment, offering a code-first approach and integrated rate limiting, suitable for startups prioritizing simplicity.
- Tyk API Management Platform offers open-source flexibility with GraphQL support, attracting enterprises looking for a range of features in a single platform.
- Gravitee supports both REST and asynchronous APIs, making it ideal for companies combining REST APIs with event streaming or IoT.
- MuleSoft Anypoint API Manager provides deep integrations through Anypoint Exchange, best suited for large enterprises needing full-stack integration.
- Axway Amplify API Management offers policy-based security gateway, aiding enterprises modernizing legacy systems without complete architecture overhaul.
- Sensedia API Platform focuses on AI integration and adaptive governance, particularly beneficial for financial services and open banking implementations.
- Azure API Management by Microsoft provides tight integrations with the Azure ecosystem, offering high control and flexibility for teams utilizing Azure cloud platform.
Read Full Article
26 Likes
TechBullion
374

Image Credit: TechBullion
Agentic AI Security: Safeguarding Autonomy in the Age of Intelligent Agents
- Agentic AI has become a crucial technology in shaping enterprise infrastructure, decision-making, and innovation in the digital landscape of 2025 and beyond.
- The security challenges associated with agentic AI systems that operate autonomously are increasing, necessitating the development of strategies to safeguard their behaviors and interactions.
- Threats to agentic AI systems include prompt injection attacks, vulnerabilities in plug-ins or APIs, credentials compromise, and identity risks.
- Companies like Zenity offer platforms focused on enabling AI development with robust governance to mitigate security threats and ensure integrity in autonomous agent deployment.
Read Full Article
22 Likes
For uninterrupted reading, download the app