Cyber Security News
Dev
400

Image Credit: Dev
Locking the Gate: Secure and Scalable API Authentication in Phoenix
- API authentication is a crucial component for secure and reliable communication in Phoenix framework.
- Phoenix provides flexibility to handle authentication without enforcing specific methods like cookies, JWTs, sessions, or OAuth.
- Authentication can be implemented at the router level by defining an authenticated pipeline and using custom plugs for token extraction and validation.
- Best practices include keeping controllers focused on business logic, centralizing access logic based on roles and scopes, and implementing observability features like logging and rate limiting.
Read Full Article
23 Likes
Medium
246
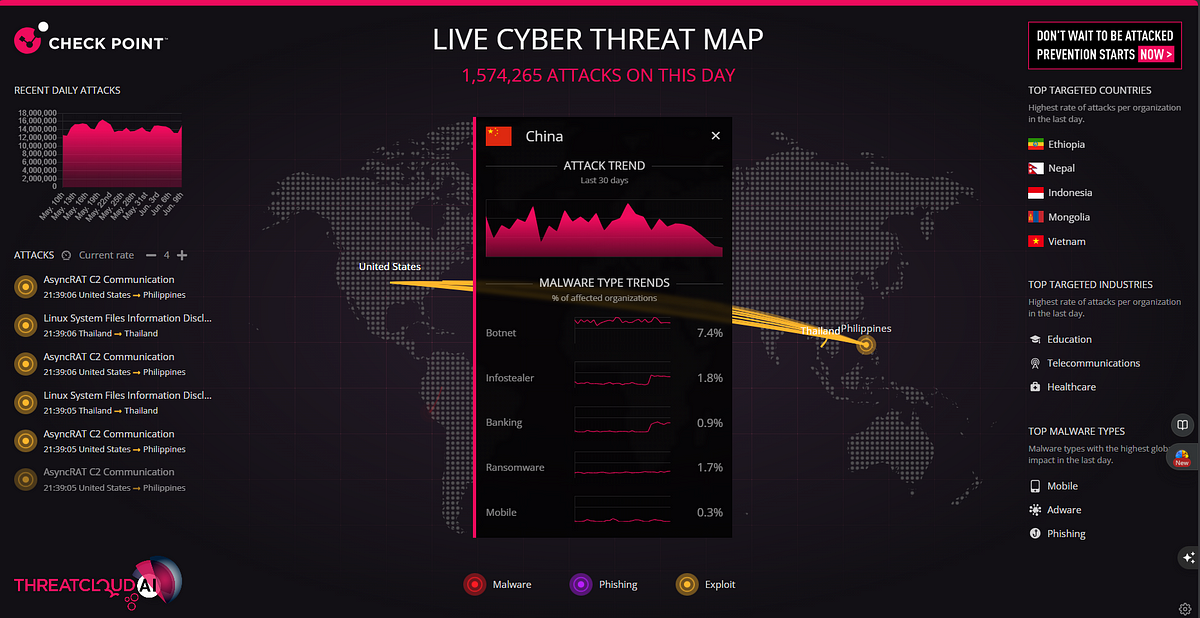
Image Credit: Medium
What if Every Call You Make Is Already Being Recorded?
- Chinese malware was found embedded in a U.S. telecom core network, undetected for seven months, raising concerns about cyber warfare.
- China's cyber warfare strategy includes infiltrating infrastructure and targeting high-profile Americans with zero-click exploits on iPhones.
- AI is being used in cyber warfare for automating phishing, vulnerability discovery, and disinformation campaigns, posing new challenges.
- APT groups like Volt Typhoon and Salt Typhoon are examples of Chinese state-sponsored cyber attacks targeting critical infrastructure and telecom networks.
Read Full Article
14 Likes
Medium
9.4k
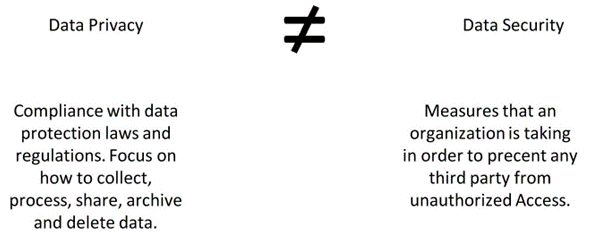
Image Credit: Medium
Data Security and Data Privacy
- Data Privacy focuses on managing contracts or policies, applying governing regulations like GDPR, and third-party management.
- Data Security ensures unauthorized access is prevented, and it prevents intentional or accidental loss, and corruption of data.
- Data Privacy safeguards personally identifiable information and manages access control to data.
- Data Security includes activity monitoring, network security, breach response, encryption, and multi-factor authentication.
Read Full Article
41 Likes
Medium
263

Image Credit: Medium
Drone Fleet Management & Geofencing via Smart Contracts
- Drones are now essential for various applications like logistics, humanitarian aid, agriculture, and surveillance.
- Managing numerous autonomous drones securely across different regions is a significant challenge, tackled by blockchain-based smart contracts.
- The concept of Autonomous Drone Fleet Management with Smart Contracts involves enforcing tasks like delivery, pick-up, and geofencing through blockchain technology.
- Ensuring secure autonomy, scalability, and neuroethical considerations are key aspects in the deployment of blockchain-based geofencing for drones.
Read Full Article
15 Likes
Wired
321

Image Credit: Wired
Apple Intelligence Is Gambling on Privacy as a Killer Feature
- Apple showcased several new features at its Worldwide Developers Conference keynote, including Messages screening, Call Screening, and Live Translation, all running locally on Apple Intelligence-enabled devices.
- Local processing for AI features ensures data remains on the device, enhancing privacy and security by eliminating the need to send data through the cloud.
- Apple's focus on privacy differentiates its AI offerings in a competitive landscape, leveraging privacy as a key selling point.
- While Apple incorporates some third-party generative AI services through opt-in integrations, its emphasis on local processing indicates a strong commitment to privacy and may be a strategic business move.
Read Full Article
19 Likes
Siliconangle
156

Image Credit: Siliconangle
Horizon3.ai secures $100M to expand partner reach and federal adoption
- Horizon3.ai raises $100 million in new funding to scale up its partner ecosystem, expand platform capabilities, and accelerate adoption in the U.S. federal market.
- The company offers an artificial intelligence-powered autonomous pentesting platform called NodeZero, which emulates real-world cyberattacks across networks and cloud environments autonomously.
- NodeZero goes beyond traditional vulnerability scanning by executing full attack chains, post-exploitation actions, and providing actionable insights for fixing vulnerabilities.
- The Series D funding round was led by New Enterprise Associates Inc., with participation from SignalFire, Craft Ventures Management, and 9Yards Capital; NEA partner Lila Tretikov will join the Horizon3.ai board.
Read Full Article
9 Likes
VentureBeat
392

Image Credit: VentureBeat
The five security principles driving open source security apps at scale
- Open-source AI is revolutionizing cybersecurity, driving innovation and results across various sectors, from startups to established companies like Cisco.
- Startups are increasingly relying on open-source AI to accelerate product development and meet enterprise needs, often outpacing traditional cybersecurity providers.
- Partnerships like Databricks' collaboration with Noma Security highlight the disruptive impact of open-source AI on legacy cybersecurity players.
- The rise of machine-scale threats emphasizes the importance of AI in cybersecurity, as noted by Cisco's President at RSAC 2025.
- Successful cybersecurity startups leverage open-source AI to not only innovate but also navigate security, compliance, and monetization challenges.
- Gartner's Hype Cycle warns of vulnerabilities within open-source codebases and the need for better security measures in AI development.
- The complexity of compliance, especially with regulations like the EU AI Act, is a growing concern for startups, driving the need for strategic governance.
- Cybersecurity founders stress the importance of contributing to open-source communities for sustainable competitive advantages and industry leadership.
- Strategic use of open-source AI can offer cybersecurity startups unparalleled growth opportunities and positioning as industry leaders in transformative security.
- VentureBeat's roundtable at Transform 2025 will delve into the strategic insights and best practices for cybersecurity startups leveraging open-source solutions.
Read Full Article
23 Likes
Securityaffairs
50

Image Credit: Securityaffairs
Texas Department of Transportation (TxDOT) data breach exposes 300,000 crash reports
- Hackers breached Texas DOT (TxDOT), stealing 300,000 crash reports with personal data from its Crash Records Information System (CRIS).
- Threat actors compromised the CRIS system, leading to unauthorized access and download of crash reports containing personal information.
- TxDOT, as a state agency managing transportation systems in Texas, oversees various functions, including traffic safety and crash data management through CRIS.
- Following the breach, TxDOT disabled the compromised account, initiated an investigation, and is enhancing security measures to prevent future incidents.
Read Full Article
2 Likes
Tech Radar
8

Image Credit: Tech Radar
Experts warn GTA and Minecraft being used to lure in cyberattack victims - here's how to stay safe
- Experts warn that popular games like GTA, Minecraft, and Call of Duty are being exploited by hackers to distribute malware among the gaming community, with millions of attempts detected.
- GTA V, Minecraft, CoD, and The Sims are among the most targeted games due to their large communities and modding capabilities.
- Hackers lure victims with promises of exclusive content, mods, and cracks, which often turn out to be malware like infostealers, backdoors, and Trojans.
- Gamers are advised to avoid downloading pirated content and to be cautious of offers like rare skins and bonuses to protect themselves from cyberattacks.
Read Full Article
Like
TechCrunch
182

Image Credit: TechCrunch
Whole Foods tells staff cyberattack at its primary distributor UNFI will affect product availability
- Whole Foods informed its employees about ongoing outages and disruptions at its primary distributor, United Natural Foods (UNFI), due to a nationwide technology system outage described as a cybersecurity incident.
- The cyberattack is affecting UNFI's ability to select and ship products, impacting normal delivery schedules and product availability for Whole Foods.
- Whole Foods instructed staff to limit communications with customers and provided a single approved customer talking point about temporary supply challenges.
- UNFI, one of the largest food distributors in North America, disclosed the cyberattack and took its entire network offline. Real-world impacts on grocery stores and customers may become more evident later this week.
Read Full Article
11 Likes
Arstechnica
165

Image Credit: Arstechnica
Found in the wild: 2 Secure Boot exploits. Microsoft is patching only 1 of them.
- Researchers have discovered two Secure Boot exploits that can bypass protections provided by the mechanism designed to load secure operating system images during the boot-up process.
- Microsoft has decided to patch only one of the exploits, specifically CVE-2025-3052, which affects over 50 device manufacturers. The vulnerability allows attackers to disable Secure Boot and install malware before the operating system loads.
- The unpatched Secure Boot bypass vulnerability poses a significant risk, especially to devices running on Linux. It can be exploited remotely to enhance the stealth and potency of attacks, particularly in scenarios where the attacker has administrative control.
- The root cause of the vulnerability lies in a critical flaw within a firmware flashing tool utilized by DT Research, a supplier of rugged mobile devices. This flaw has been present on VirusTotal since last year and was digitally signed in 2022, indicating it has been available through various channels for some time.
Read Full Article
9 Likes
Tech Radar
178

Image Credit: Tech Radar
Watch out - your DVR box could be targeted by one of the nastiest botnets around
- Kaspersky warns multiple DVR devices, such as TBK DVR-4104 and DVR-4216, are being targeted with malware that assimilates them into a botnet with DDoS and proxy capabilities.
- A year-old vulnerability (CVE-2024-3721) in these devices is being exploited to expand the Mirai botnet, allowing attackers to take full control remotely.
- The malware drops an ARM32 malware on the targeted devices, enabling DDoS attacks and proxying malicious traffic; victims are located globally, with a significant concentration in China, India, and Russia.
- Despite the discovery of the vulnerability a year ago, there is uncertainty regarding patch availability, as it is reported that manufacturers like TBK Vision might not have provided a fix, affecting various third-party brands that use these devices as a basis for their models.
Read Full Article
10 Likes
Securityaffairs
169

Image Credit: Securityaffairs
SAP June 2025 Security Patch Day fixed critical NetWeaver bug
- SAP released a security patch in June 2025 to fix a critical vulnerability in the NetWeaver framework that allowed attackers to bypass authorization checks and escalate privileges.
- The vulnerability, tracked as CVE-2025-42989 with a CVSS score of 9.6, could impact the integrity and availability of the application by letting authenticated attackers escalate privileges.
- The flaw was found in SAP's Remote Function Call (RFC) framework, enabling attackers to bypass checks and escalate privileges, posing risks to app integrity and availability.
- In addition to the critical NetWeaver bug, the June 2025 Security Patch addressed a total of five high-severity flaws and several other medium to low-severity vulnerabilities.
Read Full Article
10 Likes
Tech Radar
107

Image Credit: Tech Radar
Google has fixed an issue that could have revealed your phone number to anyone - here's what you need to know
- Google fixed a flaw that could expose the phone number associated with any Google account.
- A security researcher discovered a way to bypass Google's anti-bot mechanism, enabling automated guessing of phone numbers.
- The process of guessing phone numbers could take roughly 20 minutes depending on the number of digits.
- Google has addressed the vulnerability and expressed gratitude to the researcher for reporting the issue.
Read Full Article
6 Likes
Pymnts
40

Image Credit: Pymnts
Fed Vice Chair Bowman May Seek Regulatory Rollbacks, Benefitting Smaller Banks
- Michelle Bowman was sworn in as vice chair for supervision at the Federal Reserve on June 9.
- Bowman aims to relax regulations on smaller financial institutions to address risks in the system and allow banks to fail without destabilizing the banking system.
- She emphasizes the need to streamline de novo bank processes, re-examine regulations for community banks, combat fraud, and encourage innovation in the banking system.
- The focus is on establishing clearer standards, separating smaller banks from larger ones in terms of supervision, and addressing issues such as fraud and embracing innovation in financial services.
Read Full Article
2 Likes
For uninterrupted reading, download the app