Cyber Security News
Medium
2.4k

Image Credit: Medium
The Double-Edged Sword: How AI Empowers Both Cyber Attackers and Defenders
- Artificial Intelligence has revolutionized cybersecurity, benefiting both attackers and defenders.
- AI has enabled sophisticated defensive capabilities but also provided attackers with advanced tools.
- 87% of global organizations experienced AI-driven cyberattacks in 2024, showcasing the widespread impact.
- AI has transformed cybercrime by enhancing attack methods and making them more economically feasible.
Read Full Article
22 Likes
Dev
263

Image Credit: Dev
Setting Up Endpoint Protection
- Endpoint protection is a high-tech security system that includes antivirus, firewall, behavioral monitoring, and device control.
- When choosing an endpoint protection platform, consider features like centralized management, threat intelligence, real-time threat detection, and scalability.
- To deploy like a pro, start with a test group, use remote deployment tools, and set policies like blocking USB storage by default and restricting admin privileges.
- Endpoint protection is crucial for all devices connecting to a network, and it's important to customize settings, disable external USB ports, and train employees on cybersecurity best practices.
Read Full Article
15 Likes
Dev
8

Image Credit: Dev
Securing Remote Work Environments with VPNs
- VPN creates a secure, encrypted tunnel for internet traffic to protect data from cybercriminals.
- Remote workers are vulnerable to cyber threats due to using home Wi-Fi and accessing sensitive tools from random locations.
- Factors to consider in a VPN include strong encryption, no-logs policy, multi-device support, good speed, and a kill switch.
- Using a reputable VPN is crucial for remote work to ensure data security and privacy while working online.
Read Full Article
Like
Securityaffairs
106
Image Credit: Securityaffairs
Mirai botnets exploit Wazuh RCE, Akamai warned
- Akamai researchers warned that multiple Mirai botnets are exploiting the critical remote code execution vulnerability CVE-2025-24016 in Wazuh servers.
- The vulnerability allows for remote code execution on Wazuh servers, and active exploitation of the flaw has been observed via DAPI request abuse.
- Two Mirai botnet variants named 'Resbot' have been exploiting this bug since March 2025, utilizing Italian domain names and targeting IoT devices.
- Indicators of compromise and details on the exploitation of the Wazuh servers by Mirai botnets have been shared by Akamai researchers.
Read Full Article
5 Likes
TechJuice
370

Image Credit: TechJuice
Google Patches Critical Flaw That Exposed Private Phone Numbers
- Google has fixed a critical bug in its account recovery system that exposed users' private phone numbers, allowing attackers to brute-force recovery phone numbers tied to Google accounts without alerting owners.
- Security researcher discovered the flaw in Google's legacy non-JavaScript recovery form, enabling attackers to guess full phone numbers linked to Google accounts in a short time frame.
- The vulnerability raised concerns about privacy and potential SIM swapping attacks, as exposing private phone numbers can lead to account hijacking through intercepting SMS-based authentication.
- Google responded promptly by deprecating the flawed recovery pathway, issuing a bug bounty payout, and advising users to review and update their recovery phone numbers with stronger authentication methods.
Read Full Article
22 Likes
Tech Radar
196

Image Credit: Tech Radar
M&S online orders are back following cyberattack - here's what you need to know
- Marks and Spencer (M&S) has resumed some online orders, including standard home delivery for most of its clothing range in England, Scotland, and Wales, 46 days after a major cyberattack.
- Click and collect orders are still suspended but expected to resume within the coming weeks.
- The cyberattack occurred on April 22, with attackers compromising M&S systems through workers at Tata Consultancy Services, resulting in a forecasted cost of around 300 million in lost operating profit for M&S.
- Hackers demanded payment for the attack from M&S CEO Stuart Machin and some customer data, including home addresses, phone numbers, and dates of birth, was stolen; however, no passwords or payment details were compromised.
Read Full Article
11 Likes
Medium
303

Image Credit: Medium
Build a GRC Program That Works
- Launching a GRC program can be overwhelming, but having a clear roadmap is essential for success.
- GRC (Governance, Risk, and Compliance) is crucial for making smart decisions, managing uncertainty, and staying compliant with regulations.
- Key steps in building an effective GRC program include choosing a formal framework, gaining executive support, fostering cross-functional collaboration, and staying agile in response to regulatory changes.
- Continuous improvement, clear policies, proper tool integration, and active monitoring are essential for the success of a GRC program.
Read Full Article
18 Likes
TechBullion
17

Image Credit: TechBullion
Using Threat Intelligence Reduces Vulnerabilities and Improves Incident Response
- Threat intelligence is crucial for modern organizations to reduce vulnerabilities and enhance incident response speed and accuracy.
- It provides valuable insights into emerging threats, attacker techniques, and malicious indicators, enabling proactive defense strategies.
- Solutions like VMRay offer in-depth analysis, automation, and real-time visibility to empower organizations in threat intelligence.
- VMRay's dynamic analysis capabilities help uncover zero-day malware and polymorphic threats, enhancing vulnerability reduction and incident response.
- By prioritizing vulnerabilities actively exploited in the wild, threat intelligence guides organizations in efficient remediation efforts.
- VMRay's detailed malware reports aid incident responders in understanding attack tactics and making informed decisions swiftly.
- Automation of response tasks through VMRay's threat intelligence integration improves containment speed and minimizes human errors.
- VMRay's threat intelligence caters to diverse sectors, such as financial services, healthcare, and industrial environments, addressing unique cybersecurity challenges.
- Challenges like data overload, integration issues, and skill shortages are overcome by VMRay's actionable reports, API compatibility, and automation.
- Alignment of intelligence efforts with business risks and continuous improvement cycles are key to leveraging VMRay and threat intelligence effectively.
Read Full Article
1 Like
Silicon
196

Image Credit: Silicon
Sam Altman’s World Network Brings Iris-Scanning ‘Orb’ To UK
- Tools for Humanity, co-founded by OpenAI’s Sam Altman, is introducing its ID services to the UK through its World Network project, deploying iris-scanning 'Orb' devices for creating unique digital IDs to differentiate humans from AI and prevent fraud.
- The spherical Orb devices will be placed at various World premises in cities like London and later in other cities such as Manchester, Birmingham, Cardiff, Belfast, and Glasgow, with plans to increase production and enable self-serve usage similar to ATMs.
- The World ID created through the iris scans can currently be used to access applications like Minecraft, Reddit, and Discord, with millions of IDs already generated in several countries globally and expansion plans announced for six US cities.
- Tools for Humanity, facing privacy concerns, ensures that personal data remains on the user's smartphone, not on external servers, and intends to distribute over 12,000 Orb devices in the next year to scale up ID verifications drastically, supported by substantial venture capital funding.
Read Full Article
11 Likes
Pymnts
109
Image Credit: Pymnts
Bank of America Taps Merchant Data to Boost Payment Approval Rates
- Bank of America is leveraging merchant data to enhance payment approval rates.
- Data sharing between issuers and merchants is crucial to improve authorization decision-making, especially in the rise of card-not-present transactions.
- Technology solutions like Trusted merchant IDs and APIs are being utilized for better authentication decisions and claims investigations.
- Efforts are being made to optimize the payment experience by securely storing card information for future use and enhancing security measures like 3DS 2.0 and 3DS Data Only.
Read Full Article
6 Likes
VoIP
334

Image Credit: VoIP
Sparkle Launches Quantum-Safe VPN on AWS Marketplace
- Sparkle has introduced its Quantum Safe over Internet (QSI) solution to the Amazon Web Services (AWS) Marketplace to enhance data security against quantum computing threats.
- QSI provides secure VPN connectivity between customer sites and cloud providers, safeguarding data with advanced encryption technologies while maintaining compatibility with existing infrastructure.
- The service's cloud-native, Network as a Service (NaaS) foundation allows flexible management through a dedicated portal or API, emphasizing simplicity and efficiency in operations.
- A successful Proof-of-Concept demonstrated secure VPN tunnels between AWS regions, showcasing Sparkle's commitment to delivering future-proof cybersecurity solutions.
Read Full Article
20 Likes
Securityaffairs
14
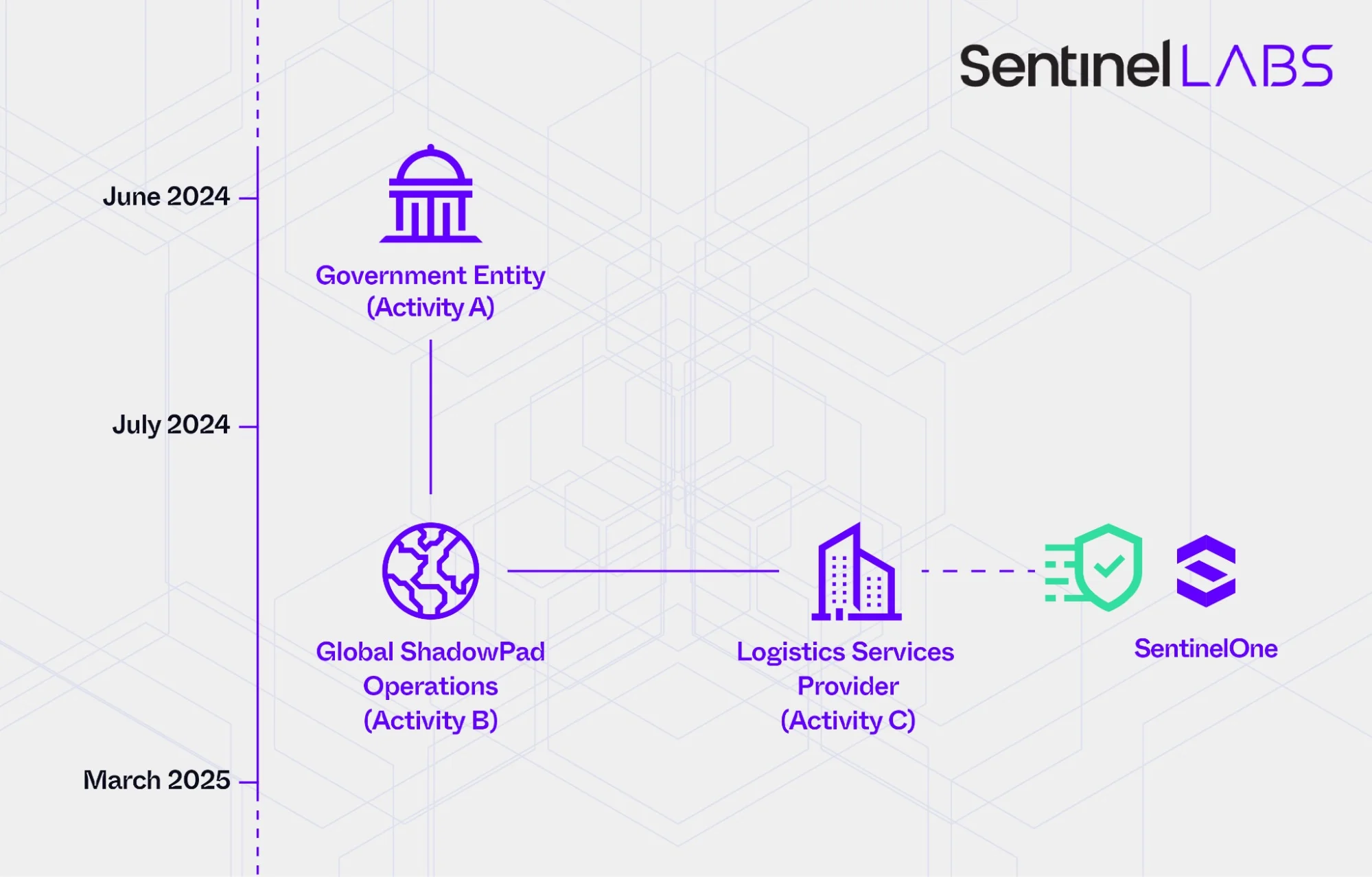
Image Credit: Securityaffairs
China-linked threat actor targeted +70 orgs worldwide, SentinelOne warns
- China-linked threat actor, PurpleHaze, targeted over 70 global organizations, including governments and media, in cyber-espionage attacks between July 2024 and March 2025.
- SentinelOne warns of targeted reconnaissance efforts by PurpleHaze to gather information for potential future attacks, with tactics and tools linked to APT15.
- The attacks used an Operational Relay Box network and a Windows backdoor called GoReShell, aligning with broader Chinese APT patterns.
- Focus on cybersecurity firms highlights the need for constant vigilance, monitoring, and rapid response capabilities to counter evolving threats.
Read Full Article
Like
The Register
407

Image Credit: The Register
Apple tries to contain itself with lightweight Linux VMs for macOS
- Apple introduced an open source containerization framework for creating and running Linux container images on Mac.
- The framework allows developers to run Linux containers on Mac, enabling them to access the environment they code for while using a Mac.
- Apple's containerization framework creates lightweight virtual machines for each container, enhancing security by reducing the attack surface and maintaining speed.
- The framework is optimized for Apple Silicon chips but has some limitations under current macOS versions, with full capabilities expected in future releases.
Read Full Article
14 Likes
Medium
49
Image Credit: Medium
How To Convert an Old PC/Laptop Into Home Lab.
- Transforming an old computer into a home lab can provide hands-on experience with ethical hacking, crucial for those pursuing a career in Offensive Security.
- Download VirtualBox from the official website, select the appropriate operating system, and install the latest version.
- After installation, set up VirtualBox by launching the program, keeping default settings, selecting location, and finishing the setup.
- Allocate around 10 GB of storage for the VirtualBox setup, and follow the steps to successfully set up Metasploitable2 with credentials: Username - msfadmin, Password - msfadmin.
Read Full Article
2 Likes
Dev
415

Image Credit: Dev
Timing Attacks: Why Your Code Might Be Leaking Secrets
- Side-channel attacks analyze unintended information leakage from the physical implementation of a system during normal operation.
- Timing attacks are a common side-channel attack that targets how code runs to extract sensitive data by measuring response times.
- Researchers demonstrated extracting RSA private keys over a network through timing analysis in 2003, highlighting the real danger of timing attacks for systems.
- Authentication systems with timing leaks can reveal sensitive information through response time differences for valid and invalid inputs.
- Rate limiting systems can become timing attack vectors, allowing attackers to detect rate limits and adjust attack patterns.
- Defending against timing attacks requires constant-time programming, architectural defenses, and monitoring systems to ensure execution time independence from secret data.
- Constant-time comparison functions and architectural defenses like decoupling requests/responses are essential in timing attack defense.
- Monitoring systems help detect timing attack attempts through analysis of request patterns and response times.
- Protecting code against timing attacks involves switching to timing-safe functions, implementing dummy processing for authentication failures, and using libraries with built-in protection.
- Combining defensive layers like constant-time implementations, architectural protections, and monitoring is crucial to resist timing attacks across various applications.
Read Full Article
24 Likes
For uninterrupted reading, download the app