Operating Systems News
Cultofmac
370

Image Credit: Cultofmac
Tariff relief for iPhone and Mac won’t last long
- Late on Friday night, President Trump clarified that he did not announce a tariff exemption for iPhones and Macs, and the 20% Fentanyl tariffs will still apply to them with potentially higher tariffs coming soon.
- President Trump backtracked on the reciprocal tariffs for 90 days but China still faces a hefty 145% tariff.
- Electronics items and semiconductors imported from China will continue to face a 20% Fentanyl tariff and will be subject to a special-focus semiconductor tariff in the near future.
- For now, iPhones, Macs, and other electronic devices are safe from the 10% global tariffs in the US, but this may change in the future.
Read Full Article
22 Likes
TechViral
411

Image Credit: TechViral
How to Fix PFN List Corrupt BSOD Error on Windows 11
- BSOD errors like PFN List Corrupt are common in Windows 11, often stemming from RAM issues or corrupted system files.
- Updating Windows 11, uninstalling security programs, and updating drivers can help resolve PFN List Corrupt errors.
- Using the Windows Memory Diagnostic tool and Check Disk Utility can identify and fix memory or drive-related problems.
- Running the SFC/DISM commands and BSOD troubleshooter can address system file corruption and other issues.
- Disabling RAM overclocking and reverting hardware changes may also assist in resolving the BSOD error.
- Keeping device drivers updated and following troubleshooting steps can improve the stability of Windows 11.
- By following these steps, users can troubleshoot and potentially fix the PFN List Corrupt BSOD error on Windows 11.
- Users experiencing this issue should try these methods and seek further assistance if needed.
- Maintaining system health through regular updates and diagnostic tools is crucial for optimal performance.
- Resolving BSOD errors enhances the overall user experience and system functionality on Windows 11.
Read Full Article
24 Likes
Dev
237

Image Credit: Dev
Apple M1+ web developers are cheating. You should do that, too
- Web development in certain communities has reached a level of bloat comparable to Java, indicating a lack of learning from past mistakes.
- Developers using Apple M1/M2/M3/M4 Macs can efficiently run workloads like Next.js, VSCode, and React due to the Unified Memory Architecture.
- Apple's MacOS employs memory compression and aggressive swapping to handle memory leaks and bloated applications effectively.
- Linux users can implement memory compression using zram kernel module to mitigate memory leaks in a similar manner to MacOS.
- To implement zram on Linux, users can create a pseudo-swapfile using commands such as sudo zramctl and swapon.
- Creating a traditional swapfile on Linux involves steps like allocating a file, cleaning its contents, setting it up as a swapfile, and activating it.
- Adjusting swappiness and vfs_cache_pressure settings in Linux can help maintain a balance between RAM usage and performance.
- Despite these measures, memory leaks are inevitable and may still cause performance issues over time.
- The ethical implications of supporting a development ecosystem plagued by bloat and memory leaks are pondered, questioning the sustainability of such practices.
- Further topics include discussions on productivity tools, UI libraries, and Streams Oriented Programming.
Read Full Article
14 Likes
Dev
263
Image Credit: Dev
Automate Your EC2 Setup Using AWS CLI and User Data
- This article explains how to automate the setup of an EC2 instance using AWS CLI and User Data.
- The article provides a step-by-step guide on launching an EC2 instance that automatically installs an Apache web server, starts the Apache service, and creates a basic webpage.
- The necessary tools for the setup, such as AWS CLI and an existing AWS Key Pair, are also mentioned.
- The article emphasizes the benefits of using the User Data field to automate EC2 instance server setup and save time.
Read Full Article
10 Likes
Discover more
- Programming News
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Dev
320

Image Credit: Dev
How I Built a TUI Without Leaving the Terminal
- TUI, which stands for Terminal User Interface, allows users to interact with software features directly from the terminal using a keyboard-driven approach.
- TUI tools are fast, scriptable, lightweight, and favored by developers, sysadmins, and minimalists for their efficiency and simplicity.
- The author built a music streaming TUI named Sparklines-TUI on a custom backend built on JioSaavn, leveraging React and Ink for the interactive command-line app.
- The tech stack included NodeJS, TypeScript, Ink, mpv for music playback, and custom backend on top of JioSaavn, making it suitable for Termux (Android), though unstable.
- The UI development using React and Ink was streamlined, allowing the author to utilize previous web development knowledge with minimal learning curve.
- Challenges in the project included implementing music playback with mpv, handling logs, managing custom commands with NodeJS, and working on UI perfection and modularization.
- The TUI project features functionalities like controlling music, login/register, API key-based interaction, continuous playback, custom shortcuts, search, recommendations, and more.
- A help menu offers useful commands like navigation shortcuts, play/pause, volume control, seeking, speed adjustment, and display options within the TUI.
- The author views the project as a personal experiment to push the limits of terminal UI in JS and values the process of learning and experimentation more than external recognition.
- The TUI project showcases the potential of leveraging terminal interfaces for personalized applications, emphasizing the importance of self-motivated projects in driving innovation.
- This informative article was originally published on https://blog.samay15jan.xyz, delving into the author's journey of building a music streaming TUI within the terminal environment.
Read Full Article
19 Likes
Dev
128
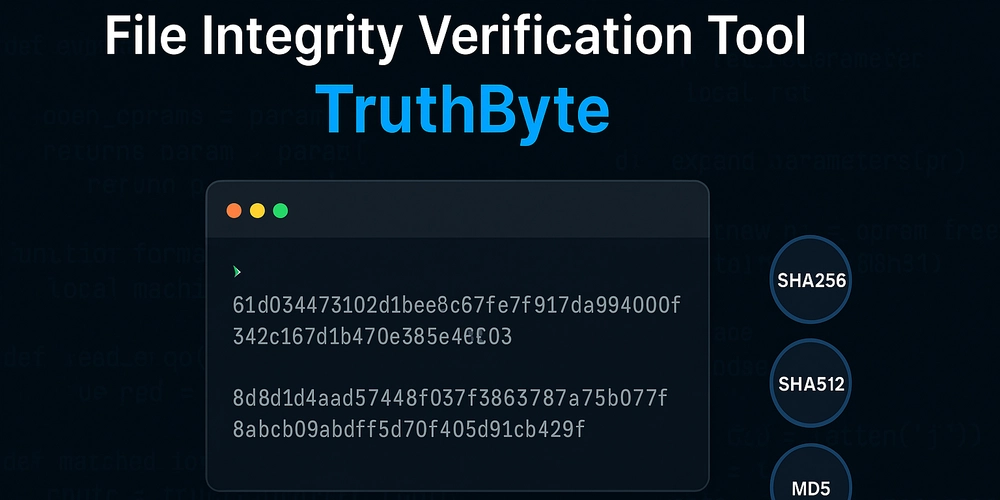
Image Credit: Dev
Introducing TruthByte: A Command-Line Tool for File Integrity Verification
- TruthByte is a command-line utility designed to verify file integrity using various hash algorithms, including SHA256, SHA512, MD5, and SHA1.
- Key features include multiple hash algorithm support, single file verification, directory verification, flexible hash file format, path flexibility, output options, user-friendly interface, and convenient access.
- TruthByte can be installed from source or using the .deb package.
- The tool is open-source and welcomes contributions on GitHub.
Read Full Article
7 Likes
Itsfoss
362

Image Credit: Itsfoss
Birth of Unix
- Unix, with its ideals, has influenced Linux and macOS, with FreeBSD being used on servers.
- Originally developed in secrecy, Unix revolutionized computing beyond punch card interfaces.
- Multics, a time-sharing computer project, influenced Unix's development by AT&T engineers.
- Unix creators, including Ken Thompson and Dennis Ritchie, started Unix after Multics project ended.
- Thompson's initial project named Unics on a PDP-7 evolved into Unix with the help of the team.
- Unix development continued on a PDP-11, leading to its first official manual in 1971 and public debut in 1973.
- AT&T released Unix's source code under license due to legal constraints, leading to the first user groups for support.
- The creation of the C programming language by Dennis Ritchie at Bell Labs further fueled Unix's development.
- Today, Unix's legacy can be seen in various programming languages, operating systems, and derivatives like Linux, BSD, and Unix-like systems.
Read Full Article
21 Likes
Ubuntu Handbook
129

Pinta 3.0 Released! How to Install it in Ubuntu 24.04 | 22.04
- Pinta 3.0, a free open-source drawing and image editing app, has been released with new features including GTK 4.0 and Libadwaita for modern UI integration with GNOME desktop environments.
- New effects in Pinta 3.0 include Dithering, Voronoi Diagram, Vignette and Dents, Feather Object, Align Object, and Outline Object.
- The release also brings back Add-ins support, an improved color picker dialog, canvas grid size customization, and more options for tile reflection effect.
- Users can install Pinta 3.0 on Ubuntu using Flatpak package, Snap package, or by compiling from source code.
- For Snap package installation, users can simply search and install Pinta from the App Center or Ubuntu Software.
- The Flatpak installation process involves installing Flatpak daemon first and then installing Pinta as a Flatpak package using specific commands.
- Compiling Pinta from source requires installing necessary dependency packages and following specific commands for configuration, building, and installation.
- Uninstallation processes are provided for Snap, Flatpak, and source code installations of Pinta 3.0.
- Users need to follow different steps for each installation method, such as using apt install, flatpak install, flatpak uninstall, or make uninstall commands.
- For compiling Pinta from source, users should heed system requirements like needing GTK 4 > 4.12 and LibAdwaita >= 1.4, which are applicable for Ubuntu 24.04 and higher versions.
Read Full Article
7 Likes
TechViral
91

Image Credit: TechViral
How to Fix ‘A Driver Can’t Load on This Device’ Error
- If you encounter the 'A Driver Can’t load on this device’ error on Windows, there are several ways to resolve it.
- Update the problematic driver manually from the Device Manager by searching automatically for drivers.
- Roll back the driver update to the previous version if the drivers are already up to date.
- Disable the Memory Integrity feature in the Windows Security app, as it can sometimes prevent drivers from loading.
Read Full Article
5 Likes
TechViral
274
Image Credit: TechViral
4 Different Ways to Clear Windows Update Cache
- Windows 11 updates can sometimes take as much as 15GB of storage space on your device.
- Clear Update Cache Manually: Stop Windows Update Service, Delete files from SoftwareDistribution folder, Start Windows Update Service.
- Clear Update Cache on Windows 11 With Disk Cleanup Tool: Use Disk Cleanup tool, select 'Windows Update Cleanup' option.
- Clear Windows Update Cache Using Command Prompt: Stop Windows Update Service using command line, Delete Windows Update Cache, Start Windows Update Service using command line.
Read Full Article
16 Likes
TechViral
96

Image Credit: TechViral
How to Use MSRT Tool on Windows to Remove Malicious Programs
- The Malicious Software Removal Tool (MSRT) is a utility provided by Microsoft to remove malicious programs from infected systems.
- MSRT is different from Windows Security as it is designed to run on already infected systems and does not provide real-time protection.
- To use MSRT on Windows, you can download the portable tool from Microsoft's webpage and run it on your system.
- The tool offers different scan options (Quick Scan, Full Scan, Customized Scan) and provides a detailed report of scan results.
Read Full Article
5 Likes
TechViral
306

Image Credit: TechViral
4 Ways to Install Missing Drivers on Windows 11
- Windows 11 updates itself automatically, but sometimes the update process gets stuck, leading to missing drivers.
- Four ways to install missing drivers on Windows 11 are: utilizing Windows Updates, using Device Manager, downloading drivers from the official website, and using third-party driver updater tools.
- To use Windows Updates, go to Windows Update tab in Settings, click on Advanced Options, and select Optional Updates to download and install missing drivers.
- To use Device Manager, open it, right-click on the device with missing driver, select Update driver, and follow the instructions to install the missing driver.
Read Full Article
18 Likes
Dev
297

Image Credit: Dev
Want to Know Where Popular Web Technologies Serve Websites on Red Hat Linux? Let’s Break It Down!
- Web technologies (e.g., Apache, Nginx, Node.js) serve websites on Red Hat Linux by handling HTTP requests.
- Popular tools such as Apache HTTP Server, Nginx, Node.js, and PHP operate on Red Hat Linux for serving websites.
- Red Hat Linux is preferred for hosting websites due to its stability, security, and dnf package manager. It also supports containerization for scalable deployments.
- For more information, refer to Red Hat Documentation or try Red Hat Enterprise Linux for experimentation.
Read Full Article
17 Likes
Dev
320
Image Credit: Dev
How to Install LAMP on Ubuntu: A Step-by-Step Guide for Beginners
- LAMP is an acronym for Linux, Apache, MySQL, and PHP, which is a popular web stack for creating and deploying dynamic web applications.
- To install LAMP on Ubuntu at Hostinger, you can use the operating system template via hPanel, which simplifies the installation process for newcomers.
- Alternatively, you can manually install each component of LAMP on Ubuntu by following a step-by-step guide.
- Ensure that all the prerequisites are met and take necessary steps to install Apache, MySQL, and PHP.
Read Full Article
19 Likes
Dev
210

Image Credit: Dev
How to Safely Kill Processes in Linux: A Comprehensive Guide
- In Linux, killing processes helps maintain system health by freeing up resources or addressing unresponsive applications.
- Prerequisites for killing processes include a Linux-based machine, terminal or SSH access, and appropriate permissions.
- Commands like ps, pidof, and pgrep help locate processes in Linux using various criteria like process ID and user name.
- The 'kill' command in Linux sends signals to processes for specific actions like termination or interruption.
- Signal options include SIGTERM for termination, SIGKILL for forced termination, and others like SIGINT and SIGHUP.
- The 'pkill' command can kill processes by name, while 'killall' targets all instances of a process by name.
- For GUI environments, the 'xkill' command allows terminating unresponsive applications with a simple click.
- The 'top' command provides real-time process monitoring and termination capabilities based on CPU and memory usage.
- Cautiously managing processes is crucial for system stability; familiarity with kill commands enhances system control.
- Different ways to kill processes include using 'kill' with PID, terminating multiple processes, and employing 'pkill', 'killall', 'xkill', or 'top' commands.
Read Full Article
12 Likes
For uninterrupted reading, download the app