Programming News
Self-Learning-Java
414

Creating a Dataset in BigQuery Using the bq Command-Line Tool
- The bq command-line tool in Google BigQuery allows users to create datasets directly from the terminal.
- Different ways to create a dataset using bq mk are explained, including setting metadata like default table expiration, partition expiration, and descriptions.
- Additional properties like default table expiration, default partition expiration, and description can be defined while creating the dataset using bq mk.
- The guide provides examples of creating datasets with additional metadata, such as setting default table and partition expiration times and adding descriptions to the dataset.
Read Full Article
24 Likes
PlanetPython
30

Image Credit: PlanetPython
Mike Driscoll: An Intro to ty ��� The Extremely Fast Python type checker
- Ty is a new Python type checker written in Rust by Astral, makers of Ruff.
- It is currently in preview and not recommended for production use but can be tested alongside Mypy.
- Installation of ty can be done via pip or other methods provided by Astral.
- A VS Code extension is available for ty, and the tool aims to offer fast and useful features like Ruff.
Read Full Article
1 Like
Logrocket
419

Image Credit: Logrocket
How to future-proof your PM career with emotional intelligence
- AI-driven tools are reshaping careers, requiring a blend of emotional intelligence and technical skills.
- Key skills include emotional intelligence, love for learning, and practicing balance in work.
- Successful professionals must combine art and science, empathy, and creativity in decision-making.
- Emotional intelligence, continuous learning, and balance are crucial for future career success.
- Find harmony between creativity and structure to excel in an evolving technological landscape.
Read Full Article
25 Likes
Medium
364

Image Credit: Medium
The Ultimate 2025 Developer’s Guide to Productivity and AI Assisted Coding
- AI is transforming software development with AI-powered coding assistants.
- The guide covers the importance and trends in AI-assisted coding for 2025 developers.
- Key interaction modes include Agent, Edit, and Chat Mode for different coding workflows.
- Popular tools for Agent Mode: Trae, Windsurf, and Cursor enhance collaboration.
- Leading assistants like GitHub Copilot excel in autocomplete experiences in Edit Mode.
- Chat Mode enables pair programming simulations with Cursor and Continue as top implementations.
- The quality of AI assistants relies on underlying language models with free and professional options available.
- Model Context Protocols (MCPs) and tools enhance AI reach and capabilities in IDEs.
- MCPs revolutionize AI coding assistants by enabling secure, third-party interactions within IDEs.
- Built-in tools within AI-native IDEs and MCPs offer additional functionalities for AI assistants.
- Effective context management, essential development rules, and security best practices are vital for implementing AI assistants.
- Collaborating with AI tools will be key for developers to build better software efficiently.
Read Full Article
21 Likes
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Medium
190

Image Credit: Medium
Why I Love Programming: My Journey in the World of Code
- Programming is not just about writing code, but about creating a new world.
- The feeling of building and controlling something in the world of programming is exciting.
- Starting with languages like Python and HTML, the journey had its challenges.
- Making mistakes is considered a part of the learning process.
- Programming is likened to a good friend that continuously teaches something new.
- The writer emphasizes the belief that through practice and passion, becoming a great programmer is achievable.
- Encouragement is given to those interested in programming to take the first step.
Read Full Article
11 Likes
Medium
349

Image Credit: Medium
My First “Hello World..!”
- Writing the first 'Hello World..!' program marked a significant shift for the author from physical engineering to software development.
- The basic program printed on a screen made the author realize the potential of communicating with a machine through code.
- This initial encounter with programming sparked curiosity and led to further exploration of languages like C, Python, and databases.
- The transition from electrical engineering to software development revealed the transferability of skills like logic, precision, and problem-solving.
- The author now works in the IT industry using engineering principles to create software systems for various operations.
- The foundational discipline of an engineer, including structured thinking and attention to detail, seamlessly translated into coding and problem-solving in the digital realm.
- The 'Hello World..!' program symbolized a gateway that shifted the author's focus from physical electronics to virtual software development.
- Running the first program occasionally serves as a nostalgic reminder of the author's progress in the software industry.
Read Full Article
21 Likes
Dev
418

Image Credit: Dev
How AI is Revolutionizing Live TV, Video on Demand, and IPTV
- AI is revolutionizing industries like live television, video on demand (VOD), and IPTV by processing data, personalizing experiences, and automating workflows.
- Content personalization is key with platforms using AI to offer tailored content catalogs and dynamic interfaces based on user preferences and interactions.
- AI optimizes live streaming by adjusting resolution in real time, providing subtitles, translations, and dubbing, and enhancing global accessibility.
- AI tools help in content creation by generating scripts, voiceovers, summaries, and virtual presenters, reducing production costs, and fostering innovative formats.
- Targeted advertising is made possible by AI, displaying personalized ads to increase engagement and revenue for platforms.
- Automation in media production shifts the job market towards digital skills like data analysis and cybersecurity, creating new roles while phasing out traditional technical positions.
- Ethical concerns arise with mass data collection and automated content, emphasizing the need for regulations to safeguard user privacy and combat misinformation.
- AI revolutionizes the IPTV industry by enhancing service quality, providing smart content recommendations, auto-generating content highlights, and offering powerful tools for resellers.
- The transformation by AI in producing, distributing, and consuming audiovisual content brings greater personalization, speed, and automation, but requires a strong ethical framework to ensure responsible use.
Read Full Article
25 Likes
Dev
410

Image Credit: Dev
Oreo's Top K Treats (Bucket Sort)
- Oreo, a data-driven Persian cat with a treat addiction, sets out to determine the top treats in its daily feast using bucket sort.
- Oreo encounters the 'Top K Frequent Elements' problem and uses bucket sort for a quick solution.
- By analyzing recent treat data provided by its human, Oreo identifies shrimp and cookies as the top treats.
- Oreo first counts treat frequencies using a Map and then organizes treats into frequency-based buckets.
- The bucket sort approach allows Oreo to efficiently find its top K treats while avoiding traditional sorting complexities.
- The time complexity of the approach is O(n), making it a linear time solution well-suited for this specific problem.
- The space complexity is also O(n) due to the use of a map for storing treat counts and buckets for frequency organization.
- Oreo's top 2 treats, shrimp and cookies, are confirmed to appear 3 times each based on the bucket sort results.
Read Full Article
24 Likes
Dev
73

Image Credit: Dev
Building OTT Apps for Education and E-Learning
- The education sector is embracing digital changes with the application of OTT technology.
- OTT platforms offer scalability, flexibility, and interactivity in delivering educational content to users.
- Key features include video library, live streaming, interactive tools, progression tracking, and secure hosting.
Read Full Article
4 Likes
Medium
342
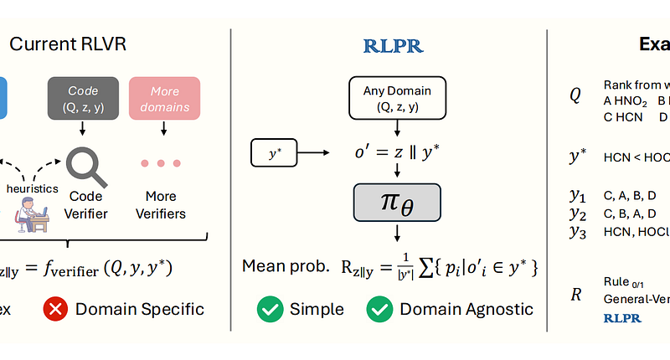
Image Credit: Medium
No Verifier? No Problem: Reinforcement Learning with Reference Probabilities
- RLPR (Reinforcement Learning with Reference Probability Reward) is proposed to address the limitation of RLVR in general domains without verifiers.
- RLVR is often restricted to math and code tasks due to the reliance on domain-specific verifiers for rewards.
- RLPR uses the model's own probability of generating a reference answer as a reward signal, eliminating the need for external verifiers.
- This self-rewarding setup alleviates manual reward engineering and enhances scalability across different domains.
- The authors present two main technical contributions in the RLPR framework.
- Experiments conducted on 7 benchmarks and 3 model families (Qwen, Llama, Gemma) demonstrate that RLPR improves general reasoning and outperforms verifier-free baselines and even specialized verifier methods like LLMs.
- The code for RLPR has been made publicly available.
Read Full Article
20 Likes
Alvinashcraft
371

Dew Drop – June 25, 2025 (#4446)
- Celebrating innovation, scale, and real-world impact with Serverless Compute on Azure.
- Stay secure with Windows 11, Copilot+ PCs and Windows 365 before Windows 10 support ends.
- TechBash Early Bird Discounts End Monday, June 30th at 11:59pm EDT.
Read Full Article
22 Likes
Self-Learning-Java
410

How to Execute a Query Using bq query Command in BigQuery?
- Executing queries in Google BigQuery using the bq query command is a common task from the command line.
- To execute a SQL query with the bq CLI tool, it is advisable to use standard SQL for its enhanced capabilities and clarity.
- In the bq query command, specifying --use_legacy_sql=false ensures the use of standard SQL over legacy SQL.
- The basic syntax for running a standard SQL query is: bq query --use_legacy_sql=false "SELECT * FROM my_project.my_dataset.my_table"
- For queries in the default project, the project ID can be omitted from the command.
- An example query to retrieve all records from the employees table in test_dataset is demonstrated.
- Executing the query correctly formats and displays the fetched data in a tabular structure.
- Using --use_legacy_sql=false in bq query promotes standard SQL usage for improved query writing.
- Adopting standard SQL is highly recommended for a better query experience in BigQuery.
- Mastering the bq query command with standard SQL can simplify data exploration and analytics tasks.
- Utilizing standard SQL enhances query readability and performance in BigQuery.
- For most BigQuery users, transitioning to standard SQL is the more preferred and powerful approach.
- Using bq query with --use_legacy_sql=false streamlines the query writing process for various data analysis tasks.
- The --use_legacy_sql=false flag allows users to leverage the full potential of standard SQL functions.
- Executing queries in standard SQL with bq query facilitates building complex analytics pipelines efficiently.
- Practicing and understanding the bq query command with standard SQL can significantly benefit users in their data handling endeavors.
Read Full Article
24 Likes
Javacodegeeks
82

Image Credit: Javacodegeeks
[FREE EBOOKS] The Chief AI Officer’s Handbook, Natural Language Processing with Python & Four More Best Selling Titles
- The Chief AI Officer’s Handbook provides strategies for AI leadership, innovation, and business growth, offering insights for CAIO roles and transforming organizations with AI.
- Natural Language Processing with Python is a comprehensive guide to mastering NLP with Python, covering foundational concepts, advanced techniques, and real-world applications.
- Essential explores distributed teams, generative AI, and human-powered leadership, highlighting the need for transformative management practices in a changing business landscape.
- AI for Social Good focuses on the potential of AI to impact society positively, offering insights on AI tools, challenges, and ethical considerations for creating impactful solutions.
- Microsoft 365 Copilot At Work delves into leveraging AI tool Copilot for enhanced productivity within Microsoft applications, providing strategies for integration and implementation.
- Excel Quick and Easy offers a convenient reference for Excel users at any skill level, covering essential tasks, functions, and data manipulation techniques for improved proficiency.
Read Full Article
4 Likes
Dev
228

Image Credit: Dev
Useful Array Methods Every Beginner Must Master
- Arrays in JavaScript are very popular, and efficient manipulation is possible using array methods.
- push() adds an item to the end of an array.
- pop() removes the last item from the array.
- shift() removes the first item, unshift() adds to the beginning of an array.
- map() creates a new array by applying a function to each item.
- filter() returns only the items that match a condition.
- find() returns the first item that matches a condition.
- includes() checks if a value exists in the array.
- join() turns the array into a string.
- Array Methods Playground on CodePen for interactive testing.
- Beginners are encouraged to practice these array methods.
- Array manipulations using methods like map, filter, and find can simplify coding.
- Continuous practice helps in mastering array methods efficiently.
- Community engagement is encouraged for sharing insights and learning from each other.
- Readers are invited to provide feedback for improvement or suggest ideas for future tutorials.
- Follow for more concise and practical tutorials on JavaScript.
- Sharing knowledge and learning together is the key focus.
Read Full Article
13 Likes
Dev
64

Image Credit: Dev
The Second Raku Core Summit
- The Second Raku Core Summit was organized in June 2025 after a successful first edition in 2023, bringing Raku enthusiasts together for discussions and hacking sessions.
- Although the original plan was for 9 attendees, only 6 could make it, leading to more intimate discussions and challenges due to colder and wetter weather.
- Attendees faced travel disruptions, including a country-wide strike affecting public transport, necessitating alternative arrangements such as driving to pick up participants.
- Discussion topics at the summit included Raku language updates, grammars, debugger, documentation, adoption strategies, backends, and improving websites.
- The event featured days of discussions, hacking, and social gatherings, with attendees appreciating the camaraderie and Wendy's excellent catering.
- Despite logistical challenges and weather issues, the summit provided a productive environment for advancing Raku programming language development and collaboration.
- The summit concluded with attendees departing, some facing travel disruptions due to the continuation of railway strikes, with alternative transport arrangements made.
- Reflecting on the packed week, organizers highlighted the positive experiences and progress made in Raku development during the event.
Read Full Article
3 Likes
For uninterrupted reading, download the app