Programming News
Medium
370

Image Credit: Medium
Securing Satellite Networks and Space Infrastructure: The Next Frontier in Cybersecurity
- Space infrastructure is becoming a critical component of global digital infrastructure, leading to an increase in cybersecurity risks that are often underestimated.
- Satellite networks, especially low-Earth orbit (LEO) systems, are vulnerable to various cyber threats due to their integration into essential national infrastructure.
- Key cybersecurity risks in space systems include ground control facilities hacking, spoofing attacks, GPS signal disruption, and vulnerabilities in inter-satellite communication links.
- The article emphasizes the need for robust cybersecurity measures in space systems to prevent potential disruptions and highlights instances where space infrastructure has been targeted by cyberattacks.
Read Full Article
22 Likes
Medium
361
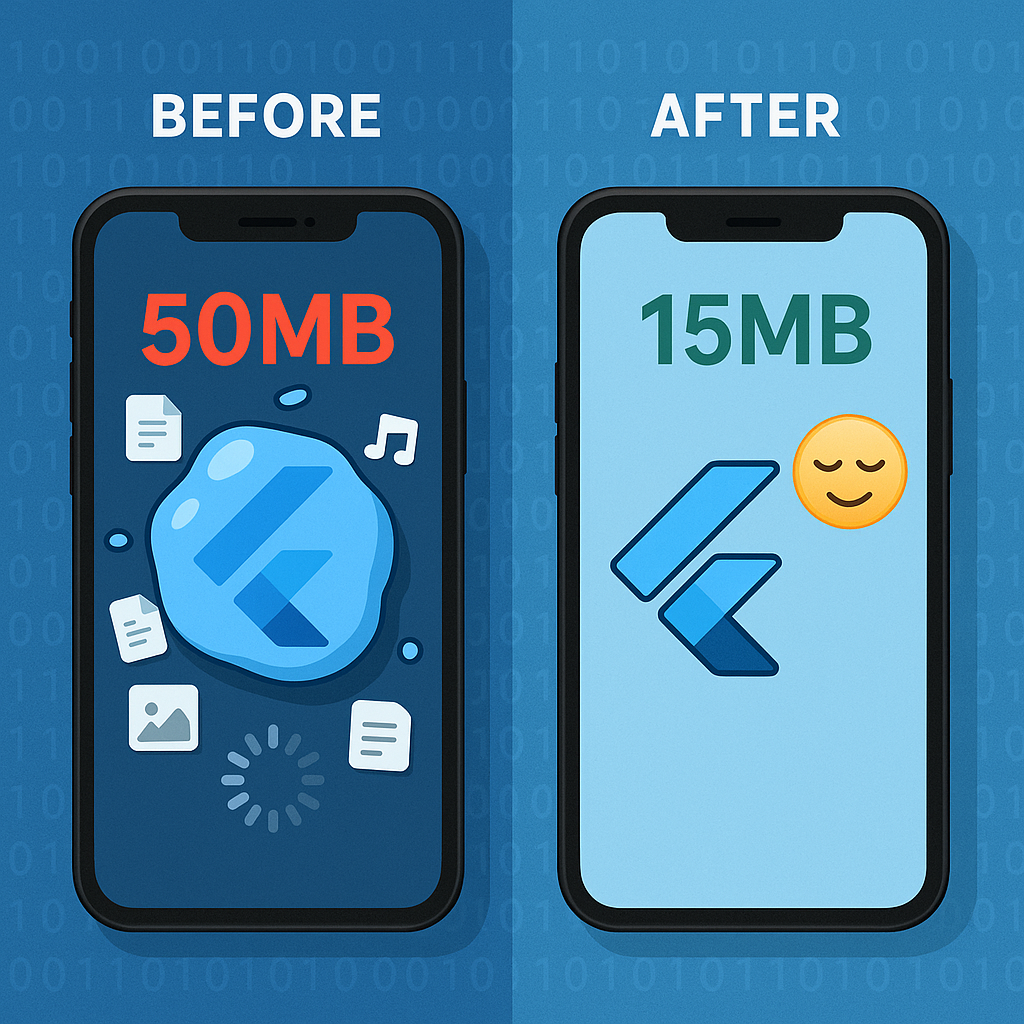
Image Credit: Medium
Flutter App Size Optimization: How I Shrunk My 50MB Monster Down to 15MB (And You Can Too!)
- Flutter app developers often face the challenge of large APK sizes, which can deter users and harm app store visibility.
- Reducing the size of Flutter apps is crucial for user engagement and retention, as larger sizes can lead to decreased install conversion rates.
- One developer managed to shrink a 50MB Flutter app down to 15MB, achieving a remarkable 70% reduction without compromising any features.
- Optimizing app size not only improves user experience but also enhances app performance and visibility on app stores.
Read Full Article
21 Likes
Medium
53

Image Credit: Medium
Barbara Liskov: The Woman Who Taught Programming to Behave
- Barbara Liskov, a pioneer in computer science, made foundational contributions by reshaping how software correctness, modularity, and trust are perceived.
- She emphasized the importance of building software like engineers build bridges, focusing on constraints, interfaces, and guarantees to combat chaos in programming.
- Liskov is known for the Liskov Substitution Principle (LSP) and her work on abstraction barriers and strong specifications, which revolutionized software design and influenced languages like Ada, Python, Java, and Go.
- Her legacy includes mentoring generations of computer scientists, shaping curricula, and paving the way for a world of software modules built on modular design and contractual promises.
Read Full Article
3 Likes
Dev
147

Image Credit: Dev
Convert a List to a Pandas DataFrames: A Complete Guide for Data Manipulation
- Converting a list to a pandas DataFrame allows for powerful data analysis and manipulation in data science workflows.
- Pandas DataFrame is a two-dimensional labeled data structure that provides analytical capabilities, unlike simple Python lists.
- The process of converting lists to DataFrames is vital for handling real-world data scenarios efficiently.
- Methods for converting simple lists include using pd.DataFrame() constructor, allowing for single or multiple lists to be transformed.
- Handling list of lists involves ensuring each inner list has the same length to maintain DataFrame structure integrity.
- Lists containing dictionaries offer flexibility for DataFrame creation, automatically extracting keys as column names.
- Managing nested lists with multiple levels requires special handling to flatten the structure or preserve hierarchical relationships.
- Custom index values can be set during conversion to provide meaningful row identifiers beyond default numerical indices.
- Data type specification during DataFrame creation ensures optimal memory usage and prevents type inference errors.
- Performance optimization becomes crucial when working with large datasets, and chunked processing is useful for handling data beyond memory capacity.
Read Full Article
8 Likes
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Javacodegeeks
383

Image Credit: Javacodegeeks
What Is an API in Java?
- APIs in Java are crucial for building scalable, modular, and maintainable applications across various domains like web development and mobile apps.
- In Java, APIs encompass built-in libraries and custom REST APIs developed using tools such as Spring Boot or Jakarta REST.
- APIs, or Application Programming Interfaces, serve as contracts facilitating communication between software applications and promoting abstraction and modularity.
- They can be Library APIs (e.g., Java's Collections API), Web APIs (e.g., RESTful services), or Hardware APIs (enabling software-device interactions).
- Java APIs include the Standard Library (JDK-provided packages like java.util) and third-party libraries (e.g., Apache Commons, Google Guava).
- In Java, APIs enable encapsulation, abstraction, code reusability, interoperability, scalability, and maintainability, enhancing developer productivity.
- Creating a RESTful Web API in Java involves frameworks like Spring Boot, where controllers define endpoints for handling HTTP requests and responses.
- Endpoints like POST /api/books (add a book), GET /api/books/{id} (retrieve by ID), and DELETE /api/books/{id} (delete) are set up in a sample BookController.
- Developers can use tools like Postman or curl to test the API endpoints after setting up a Spring Boot project with necessary dependencies like Spring Web.
- Understanding Java APIs is critical for building powerful applications efficiently, whether utilizing standard libraries, third-party APIs, or creating custom RESTful APIs.
Read Full Article
23 Likes
Dev
31

Image Credit: Dev
I tried 100+ MCP Servers and Here's my Top 10
- MCP servers like Apidog, Browserbase, and Magic enhance developer efficiency by integrating various tools seamlessly into Cursor.
- Apidog specifically aids API developers by connecting AI assistants directly to API documentation, streamlining development tasks.
- Browserbase facilitates interactions with web pages in a cloud browser environment, offering features like screenshots and JavaScript execution.
- Magic integrates generative AI capabilities into workflows, enabling tasks like image generation, text transformation, and code summarization.
- Opik connects AI assistants to real-time web search, providing up-to-date insights and references for research-intensive tasks.
- Figma Context bridges design and code by feeding Figma data to coding assistants, improving design consistency and development efficiency.
- Pandoc facilitates document conversion between various formats, making it valuable for developers dealing with diverse documentation needs.
- Excel MCP Server enables AI assistants to read, write, and process Excel files, automating reporting tasks and data manipulation.
- Mindmap MCP Server offers structured thinking maps for brainstorming and planning, aiding in organizing ideas and outlining concepts effectively.
- Markdownify converts content formats to markdown, streamlining content preparation for platforms like GitHub or technical blogs.
- Tavily provides curated knowledge for AI assistants, enhancing research, code references, and technical writing tasks with relevant information.
Read Full Article
1 Like
Medium
214

Exploring Generative AI with the Gemini API in Vertex AI
- The blog reflects the writer's experience in a course focusing on Google's generative AI models using the Vertex AI SDK.
- The course aimed to teach the participants how to utilize Google's generative AI models for text and image tasks.
- Participants were able to build small AI apps, work with models like Gemini for language tasks, and Imagen for image generation.
- The course provided hands-on experience in building AI applications, understanding the platform's capabilities, and highlighted the accessibility of generative AI tools for beginners.
Read Full Article
12 Likes
Dev
200

Image Credit: Dev
Life Path Number using Python
- Numerology is an ancient metaphysical science that explores the mystical relationship between numbers and events, often associated with spiritual significance.
- Numerology is used to discover personality traits, life paths, and more based on names and birth dates.
- This blog post explores bringing numerology into the modern era using Python to calculate Life Path Number and Name Number.
- Python script calculates Life Path Number from birth date and Name Number from full name following Pythagorean system of letter to number mapping.
Read Full Article
12 Likes
Nycdatascience
281

Image Credit: Nycdatascience
2024/2025 NBA Season Team & Player Analysis (Python Project)
- The 2024-2025 NBA season analysis focuses on team and player statistics to determine key factors contributing to game outcomes and team success.
- Key questions addressed include the impact of overall team performance versus star player performance and the statistics most correlated with team success.
- Data analysis is based on partial season data, focusing on averages due to varying game counts per team, with a breakdown of player and team statistics for each game.
- Top teams such as the Cleveland Cavaliers, Boston Celtics, and Oklahoma City Thunder are analyzed based on points scored, points allowed, turnovers, and points differential per game.
- League-wide trends reveal that teams scoring 120+ points or allowing 105 points or fewer have higher winning percentages, emphasizing the importance of points and turnovers.
- Individual player impact analysis shows that team success is not solely reliant on star players but on a balanced team chemistry and performance.
- Analysis also compares top players across offensive and defensive categories, highlighting the importance of team dynamics over individual player performance.
- The key takeaway is that basketball is a team sport, emphasizing the significance of team-specific goals and balanced team play for greater success.
- Future work involves deeper analysis on specific teams, opponents' influence on player statistics, and comparing regular season trends with playoff performances.
- The analysis provides valuable insights into team and player dynamics in the 2024-2025 NBA season, highlighting the importance of team cohesion and balanced performance in achieving success.
Read Full Article
16 Likes
Medium
334

Image Credit: Medium
Learn about python basics
- Python was created by Guido van Rossum in 1991 and further developed by the Python Software Foundation.
- Indentation in Python is used to define blocks of code, indicating that a group of statements belongs to a specific block.
- Understanding input and output operations is fundamental in Python programming, with functions like print() for output and input() for user input.
- Python's print() function allows text, variables, and expressions to be displayed on the console easily.
- Variables are essential in Python to store and manipulate data, acting as placeholders that can be referenced and reused.
- Operators in Python are symbols used for logical and arithmetic operations, including Arithmetic and Comparison Operators.
- Python keywords are reserved words with special meanings, serving specific purposes in the language syntax.
- Python offers a variety of data types that categorize data items, allowing specific operations on different data.
- Conditional statements and loops in Python are used to control the flow of a program, executing blocks of code based on conditions or for repetitive tasks.
- Python uses indentation for code structuring, with blocks of code being defined by the number of indented character spaces.
Read Full Article
20 Likes
Medium
245
Image Credit: Medium
8 ChatGPT Tips for Beginner Coders
- ChatGPT can be a useful tool for beginner coders to get help with basic coding tasks such as checking code, fixing errors, and understanding programming concepts.
- Here are 8 tips for beginners on using ChatGPT effectively: 1. Provide clear and specific questions with details like programming language and desired output. 2. Avoid vague questions and instead be precise in your queries.
- 3. When seeking help, only include the relevant code snippet where the issue occurs and mention the expected outcome or the error faced. 4. Break down complex problems into smaller parts and ask questions step-by-step for better results.
Read Full Article
14 Likes
Dev
209

Image Credit: Dev
Unlocking Business Growth: Choosing the Right CRM Software Development Company
- CRM software development is crucial for businesses to effectively manage customer relationships and drive results.
- Custom CRM development offers tailored features, seamless integration, better user adoption, scalability, and enhanced data security.
- CRM software development companies provide services like custom CRM development, migration, integration, consulting, and support & maintenance.
- Key features of a successful CRM system include contact & lead management, sales pipeline tracking, email & marketing automation, reporting, analytics, and more.
- Various industries benefit from CRM software, such as healthcare, retail, real estate, and financial services.
- Choosing the right CRM software development company involves considering experience, technical expertise, transparency, post-launch support, and customization.
- Custom CRM solutions offer businesses control over customization, cost-efficiency, and improved workflows compared to pre-packaged tools.
- CRM software enhances customer experience by centralizing data, predicting needs, and enabling personalized interactions.
- The cost of CRM software development depends on features, team size, integration complexity, design, and ongoing maintenance, ranging from $10,000 to $50,000 for SMEs.
- Future trends in CRM development include AI, machine learning, voice & chatbot integration, IoT integration, and enhanced mobility for teams on the go.
Read Full Article
12 Likes
Dev
214

Image Credit: Dev
SikkerBox-Cyber Swiss Army Knife on your cell phone
- SikkerBox is a security and network utility app combining 2FA management and network diagnostic tools for convenient use.
- Key features include highly secure 2FA with QR code scanning and manual entry support, time-based OTP generation, and offline access.
- Network utilities in SikkerBox encompass port checking, IP location lookup, WiFi scanning, ping diagnostics, WHOIS lookup, and DNS reverse lookup.
- The app offers multi-language support, modern Material Design, responsive layout, clipboard integration, and dark mode for user satisfaction.
- It supports Android, iOS, Windows, macOS, Linux, and Web platforms, ensuring secure storage and low resource consumption.
- Privacy-focused, SikkerBox does not require an account, avoids data collection, and uses open network APIs for diagnostics.
- Use cases range from security professionals to privacy-conscious users, offering solutions for network diagnostics, security validation, and more.
- The app can be installed via provided APK links and is developed with acknowledgment to the Flutter team and package maintainers.
- For enabling or replacing 2FA on Github, SikkerBox guides users through installation, scanning QR codes, and entering one-time passwords for verification.
- In case of account deletion, Github recovery codes can be used, and contributors are invited to help improve the app.
Read Full Article
12 Likes
Dev
75

Image Credit: Dev
Try UkrGuru.Sql with New Optimized `Results.Parse`
- The latest release of UkrGuru.Sql introduces an optimized Results.Parse method to streamline how developers handle SQL query results in .NET applications.
- The new method improves performance and usability by offering faster parsing of SQL result sets, reduced memory footprint, improved error handling, and simplified syntax.
- Benchmark results demonstrate significant performance gains in both serialization and deserialization with the new implementation.
- The optimized Results.Parse method helps minimize boilerplate code, improve application responsiveness, and allows developers to focus more on business logic than data plumbing.
Read Full Article
4 Likes
Insider
267
Image Credit: Insider
A Salesforce exec tells BI there's an even more important skill for employees than coding
- Salesforce's chief futures officer, Peter Schwartz, mentions that in the AI era, empathy is a more important skill than coding.
- Schwartz emphasizes the significance of empathy for employees, highlighting the need to work collaboratively and creatively with others.
- AI's impact on coding for Salesforce has been significant, leading to increased productivity among coders.
- Tech leaders have varying opinions, with some advocating for soft skills like empathy over technical coding abilities.
Read Full Article
16 Likes
For uninterrupted reading, download the app