Programming News
Medium
8

Image Credit: Medium
Runnit.Fun: The Fastest Growing On-Chain Gambling Game on Solana With $400,000 Paid in 32 Hours
- Runnit.Fun is a new on-chain gambling game on Solana offering five mini-games for players to bet real SOL against algorithmic odds.
- Within just 32 hours of launch, Runnit.Fun attracted 800+ active users and paid out over $400,000 in SOL.
- Runnit.Fun offers games like Crash, where players cash out before it crashes, Jackpot for pooling wagers, Mines to find gems and avoid bombs, and Plinko for a chance-based win.
- Players can win big by pulling out at the right moment in Crash, joining a live pool in Jackpot, collecting gems in Mines, or landing on prize slots in Plinko.
- The game is designed for degen gamblers and Solana enthusiasts, providing a fast-paced and rewarding gambling experience.
- Runnit.Fun has rapidly paid out substantial amounts in SOL, proving its popularity and potential for users to earn rewards quickly.
Read Full Article
Like
Dev
244

Image Credit: Dev
How to Structure a React Project in 2025: Clean, Scalable, and Practical
- Organizing a React project involves thinking about the app's size and complexity; suggested structure includes folders for assets, components, pages, routes, hooks, services, utils, contexts, and styles.
- The 'assets' folder houses static files; 'components' contain shared UI components; 'pages' for route-level components; 'hooks' for custom hooks; 'services' for external API logic; 'utils' for utility functions; 'contexts' for React Context Providers; and 'styles' for global styling.
- Additionally, 'App.jsx' serves as the main application shell, and 'main.jsx' is the root file for rendering React to the DOM.
- As projects grow, transitioning to a feature-sliced or domain-driven structure is recommended for scalability and organization.
- Planning project structure early is crucial for maintainable code; start small, organize by features, and evolve into a modular, domain-based architecture for readability and scalability.
Read Full Article
14 Likes
Medium
271
Image Credit: Medium
Who Says Web Design Doesn’t Have a Future?
- Web design is evolving into something smarter, deeper, and more impactful.
- AI tools like Wix ADI, Framer AI, and ChatGPT can quickly create landing pages.
- AI lacks understanding of client's brand story, user emotions, and business goals.
- Designers play a crucial role in adding character and personal touch to designs.
- AI is viewed as a tool by most Redditors and not a replacement for human designers.
- Web design requires creativity and human intuition which AI may lack.
- Many agree that AI complements but doesn't replace the role of human designers.
- The role of web designers involves adding unique elements to design based on context.
- Designers are seen as chefs who know how to enhance designs with creativity.
- AI is likened to a blender that can mix ingredients, whereas designers are chefs who add unique flavors.
- AI excels at creating standard designs, but designers bring innovation and creativity.
- Importance of human designers in understanding nuances and subtleties crucial for effective web design.
- Designers have the ability to make design choices based on emotions and business objectives.
- Web design involves more than just aesthetic appeal; it includes storytelling and brand representation.
- The field of web design is thriving as it adapts to new technologies and demands.
- Web design continues to be relevant and essential in shaping digital experiences.
Read Full Article
16 Likes
Dev
66

Image Credit: Dev
What are MCP Servers? | A Detailed Guide
- The Model Context Protocol (MCP) is an open-source, vendor-agnostic standard created by Anthropic in November 2024.
- MCP serves as a universal connector between large language models (LLMs) and external data sources or tools.
- It aims to standardize how LLMs request, retrieve, and manipulate external data using a uniform protocol.
- MCP employs a client-server model with MCP Hosts, MCP Clients, and MCP Servers as its core components.
- The workflow involves the user asking AI to fetch data, the host spinning up an MCP client, and the client making a standardized JSON‑RPC call to the MCP server.
- MCP adoption is growing, with various organizations leveraging it for tool integrations and workflows.
- Use cases include IDE assistants pulling live code context from GitHub and enterprise agents querying internal databases.
- Pros of MCP include unified integrations, vendor-agnosticism, scalability, and security-by-design.
- Challenges include security vulnerabilities, governance gaps, and potential market incentives issues.
- Future outlook for MCP includes broader adoption, enhanced security layers, and advanced tooling.
- MCP aims to enable context-aware agentic AI by standardizing interactions between LLMs and external tools.
- Security, governance, and ethical design are crucial for the safe scaling of MCP in intelligent applications.
- MCP could play a key role in the future of applications bridging human intent and digital systems.
Read Full Article
4 Likes
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Dev
106

Image Credit: Dev
How to Create an Offline Version of Websites Using Kiwix and ZIM Files
- Kiwix and ZIM files allow offline access to web content, useful for trips or areas with no connectivity.
- Kiwix is free software enabling offline web content access, compatible with various platforms.
- ZIM files are compressed formats storing web content for offline usage, including images and videos.
- Getting started involves installing Kiwix, downloading ZIM files from the library, and opening them in Kiwix.
- Users can create their ZIM files using Zimit for websites not in the Kiwix library.
- Benefits include offline access to educational content, faster browsing, and preservation of resources.
- Use cases include students in low-connectivity areas, travelers needing offline materials, and researchers archiving knowledge.
- Final thoughts emphasize the utility of Kiwix and ZIM files for offline browsing and resource preservation.
- Kiwix empowers users to access the web without an internet connection by creating offline versions of websites.
- Users can share their experiences with using Kiwix and ZIM files in the comments or on social media.
- Platforms supported by Kiwix include Windows, macOS, Linux, Android, and iOS.
- ZIM files offer compressed and fast-loading offline content with the full website structure.
- Creating a ZIM file involves pasting a website's URL on Zimit, generating the file, and opening it in Kiwix.
- Note that not all websites are easily portable to ZIM format, especially those with login systems or heavy JavaScript usage.
- Downloading Kiwix enables users to build their offline knowledge base, useful for various situations, such as travel or study.
- The guide provides steps to begin using Kiwix and ZIM files for offline web content access.
Read Full Article
6 Likes
Dev
195

Image Credit: Dev
Web Performance Optimization in 2025: Build a Site Faster Than a Rocket!
- In 2025, website speed is crucial, with 53% of users leaving if a site takes over 3 seconds to load.
- Google uses Core Web Vitals like LCP, INP, and CLS to judge user experience and SEO rankings.
- Optimization techniques include image optimization using WebP or AVIF, server speed improvements, clean code practices, responsive design, AI utilization, and focusing on Core Web Vitals.
- Addressing server speed with quality hosting and CDNs like Cloudflare can significantly enhance site performance.
- Clean coding practices such as minifying, removing unused code, and loading scripts asynchronously are recommended.
- Designing responsively for mobile, optimizing fonts, and conducting cross-device testing are crucial for mobile optimization.
- AI offers tools for user behavior analysis, automated optimization, and predictive alerts for web performance enhancement.
- Improving Core Web Vitals metrics, including LCP, INP, and CLS, is fundamental for SEO success in 2025.
- Google emphasizes Core Web Vitals for SEO; strategies to enhance these metrics involve optimizing images, JavaScript, and preventing layout shifts.
- By implementing these techniques, websites can achieve faster loading speeds, better user experience, and higher search rankings.
- Overall, web performance optimization in 2025 is critical for retaining users, increasing revenue, and improving search engine rankings.
Read Full Article
11 Likes
Dev
279

Image Credit: Dev
Building Africa’s AI Future: Yamify’s Vision for Education and Infrastructure
- Africa's potential in the global AI revolution hinges on education and infrastructure according to Yamify.
- Yamify addresses the gap by offering immersive and localized AI education.
- Their approach includes AI Sandboxes, localized learning, and problem-driven curriculum.
- Infrastructure is crucial for AI development, with Africa having limited cloud capacity.
- Yamify's AI-native cloud platform provides GPU compute at local rates and data centers in Africa.
- Empowering learners and providing infrastructure leads to faster innovation in AI products.
- Yamify calls for partnerships to drive Africa's AI future through locally trained developers.
Read Full Article
16 Likes
Dev
311

Image Credit: Dev
App Intents for Apple ecosystem
- App Intents is an ecosystem in the Apple system expanding app functionality.
- Core Architecture involves Grammar System and Build-Time Processing.
- Basic Intent Structure includes title, perform() method, and supported modes.
- Parameters & App Enums allow for fluent action descriptions and input variables.
- App Entities manage dynamic data with persistent identifiers and EntityQuery.
- App Shortcuts provide automatic system exposure for app actions.
- Integration features like Transferable Protocol and Spotlight Indexing improve user experience.
- Advanced integration features enhance data sharing and spotlight integration.
- Multi-Target Architecture supports code sharing and dependency management.
- Key 2024 updates include Mac Spotlight Integration and Swift Package Support.
Read Full Article
18 Likes
Pymnts
115

Image Credit: Pymnts
Peymo Launches AI-Powered Digital Finance Platform
- Peymo, a UK-based FinTech, launched an AI-powered digital finance platform integrating fiat banking, cryptocurrency wallets, and embedded finance.
- The platform, referred to as an 'AI-powered multi-hybrid bank,' allows users to manage British pounds, euros, crypto assets, and branded debit cards.
- Enterprises can leverage APIs for full banking functions.
- Features include a voice-first interface for hands-free banking, AI agents monitoring user behavior, and AI tools for navigation.
- Peymo is expanding globally and involving partners, early adopters, and regulatory stakeholders.
- Investors are invited to join Peymo for a transformative journey in the financial landscape.
- Mobile banking apps are preferred by many customers, with millennials and Gen Z using them as primary financial tools.
- Salesforce research shows that customer demand for better service and personalized experiences drove 25% of bank switches.
- 39% of customers switched banks in pursuit of improved customer service.
- The trend towards digital-first banking does not exclude the importance of personalized experiences.
- PYMNTS offers daily newsletters on digital transformation and AI coverage.
Read Full Article
6 Likes
Dev
124

Image Credit: Dev
WWDC 2025 - Automate dev process with App Store Connect API
- Apple has expanded the App Store Connect API with new features for automation and real-time notifications to streamline app development workflows.
- Key new features include Webhooks API for push notifications, Build Upload API for automating build uploads, and Feedback API for retrieving TestFlight feedback programmatically.
- Webhooks offer notifications for build and beta state changes, TestFlight feedback, app version state changes, and Apple-Hosted Background Asset state changes.
- Webhooks can be set up through the web interface or programmatically, requiring a name, endpoint URL, and secret key for verification.
- The automation loop involves uploading builds, receiving webhook notifications, distributing to TestFlight, and getting instant feedback notifications.
- Webhook notifications include HMAC-SHA256 signatures for verification that notifications are from Apple.
- These API enhancements aim to improve automation in App Store Connect, allowing developers to focus on creating user experiences rather than deployment processes.
- Developers are recommended to implement webhook listeners, automate based on events, and explore additional automation possibilities within the App Store Connect API.
Read Full Article
7 Likes
Dev
93

Image Credit: Dev
WWDC 2025 - App Store server APIs for In-App Purchase
- Apple has introduced significant updates to the App Store server APIs for In-App Purchase to simplify and enhance app server responsibilities.
- The updates focus on managing In-App Purchases, signing requests, and participating in refund decisions, providing more flexible transaction management for developers.
- The introduction of the appTransactionId offers a consistent identifier per Apple Account across all transactions, making it easier to associate customer accounts with their activities.
- Enhancements in appAccountToken management allow setting tokens for various transactions, updating values, fixing inconsistencies, and applying them to all product types.
- The new Get App Transaction Info endpoint enables fetching app download details directly on the server, offering insights for better app performance evaluation.
- Apple has unified the signing process using a JWS format, simplifying promotional offers, enhancing control over eligibility, and standardizing signing formats across functions.
- The Send Consumption Information V2 endpoint streamlines the refund participation process, reducing required inputs, extending support to all product types, and introducing prorated refund options.
- Prorated refund support allows specifying consumption percentages, handling partial revocations based on actual usage, and providing enhanced notification data for better customer satisfaction.
- Developers are recommended to adopt the appTransactionId, migrate to V2 endpoints, utilize prorated refunds, and implement unified signing to leverage the new features effectively.
Read Full Article
5 Likes
Dev
53

Image Credit: Dev
WWDC 2025 - Meet Containerization
- Apple announces Containerization, a new open-source Swift framework for running lightweight Linux containers on macOS.
- Containerization provides each container with its own lightweight virtual machine, improving security and resource efficiency.
- The framework introduces vminitd, a Swift-built init system that handles critical tasks within each virtual machine.
- Container filesystems are exposed as EXT4-formatted block devices for optimal performance.
- Apple released a companion container command-line tool for standard container operations and quick container startup.
- Both the Containerization framework and container tool are open-source on GitHub for developers to explore and contribute.
- This innovation advances container technology on macOS, offering a more secure, performant, and efficient way to work with Linux containers.
Read Full Article
3 Likes
Amazon
75

Image Credit: Amazon
Amazon Q Developer Java Upgrades: A Deep Dive into the New Selective Transformation Feature
- Amazon Q Developer now supports customization of Java upgrades with a new selective transformation feature, offering greater control over modernization journeys.
- The selective transformation feature allows targeting specific components and libraries for transformation, avoiding risky 'big bang' upgrades and ensuring application stability.
- Development teams can opt for individual developer-driven upgrades or orchestrated transformation campaigns managed by Center of Excellence teams.
- Selective transformation facilitates tailoring transformation plans using natural language chat or input files for more precise Java upgrades.
- The feature supports selecting steps from a transformation plan, upgrading first-party and third-party dependencies, and customizing their versions during JDK upgrades.
- The transformation can be run in interactive mode for user feedback or in no-interactive mode for continuous transformation without user input.
- The selective transformation feature streamlines Java version upgrades, reduces technical debt, and modernizes applications with minimal disruption, enhancing efficiency for development teams.
- The CLI provides practical examples of upgrading dependencies interactively or non-interactively, offering detailed transformation plans and user feedback options.
- The article emphasizes the importance of maintaining security, avoiding unvetted artifacts, and validating transformed code for functionality and security post-upgrades.
- Selective transformation in Java upgrade CLI revolutionizes Java modernization by providing granular control, natural language interactions, and targeted dependency management for a manageable, incremental process.
- The feature encourages teams to identify critical components for upgrading and leverage selective transformation for a tailored upgrade strategy, ensuring efficient, risk-managed Java modernization.
Read Full Article
4 Likes
Medium
80
Image Credit: Medium
I Quit Sugar for 30 Days – Days 1 to 5: The Fog, the Crashes, and the First Spark
- A person decided to quit sugar for 30 days after realizing their addiction to it while studying neurotransmitters like dopamine in class.
- Dopamine plays a key role in motivation, focus, habits, and the brain's reward system, influencing activities that spike dopamine like junk food and social media.
- The individual set rules including no social media, refined sugar, processed foods, and aimed for a high-protein diet with daily exercise and water intake.
- Day 1 was challenging without social media, leading to feelings of emptiness that were countered by exercise and a protein-rich diet with minimal sugar.
- On Day 2, despite a dull start, focusing on study became easier without distractions after sticking to the routine.
- Day 3 brought mental lows and emotional flatness, making studying difficult, but determination to complete the 30-day challenge persisted.
- By Day 4, physical changes like reduced puffiness, a more defined jawline, and decreased waist size were noticed, boosting motivation to continue.
- Day 5 marked a shift with refreshed mornings, lifted mental fog, and increased motivation, indicating progress in the sugar-free journey.
Read Full Article
4 Likes
Medium
440
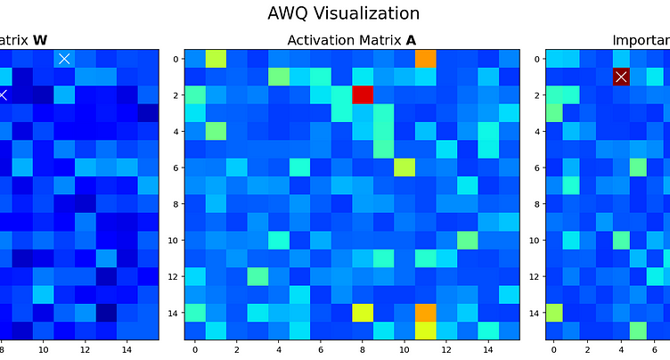
Image Credit: Medium
How to Use AWQ to Quantize LLMs
- Quantization is a method used to enable the use of large language models (LLMs) on limited hardware by reducing the number of bits per parameter.
- Most LLMs currently utilize 16-bit floating point formats, but using 4-bit quantization can lead to up to a 4x reduction in model size.
- Quantization algorithms are designed to minimize model size while maintaining performance.
- This article delves into the Activation-Aware Weight Quantization (AWQ) algorithm and its application to a small local LLM in a practical scenario.
- Quantization involves reducing the number of bits required to represent variables, resulting in smaller data storage.
- An example demonstrates the process of converting a 16-bit floating-point number to a 4-bit representation through a scaling factor.
Read Full Article
26 Likes
For uninterrupted reading, download the app