Programming News
Medium
193

How We Automated Static Go Builds with Docker — No More Escaping Hell
- The article discusses the development of the 'go-builder' tool to automate static Go builds using Docker.
- The tool helps in maintaining predictable, portable, and declarative builds without relying on complex Makefiles.
- Key features of 'go-builder' include using CGO_ENABLED=1, musl-gcc instead of the default linker, embedding version info, and cross-compiling for multiple architectures.
- The tool simplifies the build process and ensures that binaries remain static, providing a consistent and controlled approach to building Go applications.
Read Full Article
11 Likes
Medium
92

What Is JA3? The Silent Fingerprint Behind Every HTTPS Connection
- JA3 is a method to create a unique fingerprint of how a client behaves at the TLS level by encoding raw data and hashing it using MD5.
- It is useful for bot and malware detection, application fingerprinting, and fraud analytics by distinguishing TLS handshakes and behaviors.
- JA3 serializes fields into a comma-separated string and produces a unique hash representing the client's TLS negotiation process.
- Cloudflare WAF uses JA3 to protect sensitive API endpoints with multiple filters.
Read Full Article
5 Likes
Medium
138
Image Credit: Medium
WebSockets Explained: How Real-Time Chat Apps Work Behind the Scenes
- Real-time chat apps like WhatsApp or multiplayer games like BGMI work smoothly using WebSockets, which enable constant two-way communication between clients and servers.
- Traditional applications communicate over standard HTTP connections, where a request is sent, a temporary connection is formed, data is received, and the connection is closed, unlike the persistent connection of WebSockets.
- WebSockets start as an HTTP request and, if accepted by the server, upgrade to a persistent connection that allows both client and server to send and receive messages freely without waiting, unlike the polling method used in HTTP for real-time experiences.
- Major companies like Slack, Trello, and Google Docs leverage WebSockets to enable real-time collaboration and instant updates, showcasing the efficiency and effectiveness of using WebSockets for real-time applications.
Read Full Article
8 Likes
Medium
162
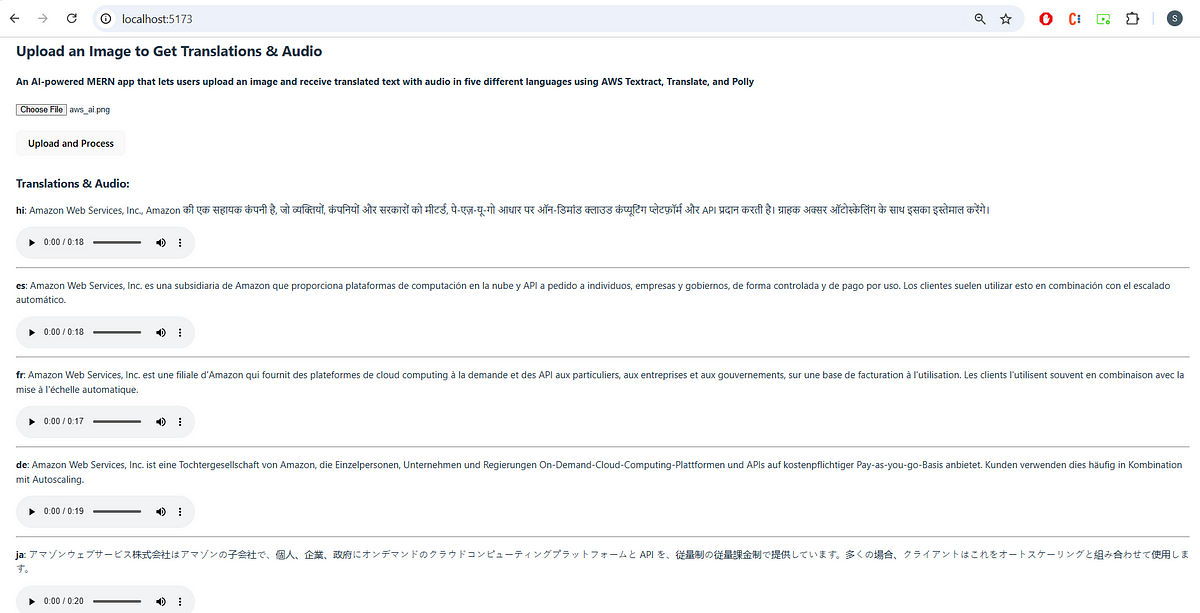
Image Credit: Medium
AI-Powered Image Translator using React JS, AWS Textract, Translate, and Polly
- AWS operations in the AI-Powered Image Translator are securely performed on the backend, ensuring no direct interaction with AWS SDKs or credentials from the frontend.
- It is recommended to use the AWS CLI to configure credentials globally for the machine, rather than hardcoding them in the code.
- Steps involve installing AWS CLI, creating an IAM user with programmatic access, and storing the credentials securely in ~/.aws/credentials and ~/.aws/config.
- The article also highlights the application's components, such as the uploaded image, user interface, and the translation with audio output, providing a comprehensive overview of the process.
Read Full Article
9 Likes
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Dev
189

Image Credit: Dev
Secrets of Coroutine Scheduler Core Implementation Principles of High Performance Async Framework(1751181427802100)
- A junior computer science student shares their transformation in understanding performance development through exploring Rust-based web frameworks.
- The combination of memory safety and performance optimization in Rust-based frameworks like Hyperlane offers an ideal environment for building high-performance applications.
- Extensive testing and optimization efforts led to remarkable performance improvements in the asynchronous architecture of the framework, maintaining code clarity.
- The student concludes that the framework's type safety, performance, and developer experience make it a great choice for scalable application development.
Read Full Article
11 Likes
Dev
122

Image Credit: Dev
Cascading context cancellation in Go: from source code to production patterns
- Exploring context cancellation in Go, from source code to production patterns.
- Learn about propagating cancellation, creating contexts with reasons, handling goroutines, and timers.
- Understand accessing from multiple goroutines, using AfterFunc, canceling contexts, and withoutCancel method.
- Discover cancelCtx patterns, considerations for timers, and the utility of closed channels for optimization.
- Context cancellation in Go simplifies lifetime management and ensures consistency in operations.
Read Full Article
7 Likes
Dev
257

Image Credit: Dev
Memory Safety Ultimate Performance Balance(1751176681301600)
- Achieving ultimate performance while ensuring memory safety is crucial for system programming learners.
- Rust language strikes a perfect balance between performance and memory safety with zero-cost abstractions.
- The language's borrow checker ensures compile-time memory error detection, enabling safe and efficient code writing.
- Rust's features like zero-cost abstractions and compile-time state checking optimize memory safety and performance.
- Mastering these technologies will be advantageous in the evolving landscape of safety and performance demands.
Read Full Article
15 Likes
Medium
201

Image Credit: Medium
Build a Private dApp on Oasis Sapphire
- Sapphire is a confidential EVM runtime built on the Oasis Network, allowing Solidity developers to build private dApps without learning a new stack.
- Sapphire introduces confidentiality to smart contract execution by encrypting input, output, and internal state inside a Trusted Execution Environment like Intel SGX.
- Developers can deploy existing contracts to Sapphire with no changes, and adding privacy logic can unlock entirely new capabilities.
- Sapphire enables the development of dApps with enhanced privacy features, such as a 'dead man’s switch' smart contract example, while keeping the experience similar to Ethereum development.
Read Full Article
12 Likes
Dev
205

Image Credit: Dev
Asynchronous Programming Art From Zero Foundation to High Concurrency Processing Transformation Journey(1751175402518700)
- A junior computer science student shared their transformation journey in understanding performance development in modern web framework design and implementation.
- They explored the power of Rust-based web frameworks known for memory safety and performance optimization, ideal for high-performance applications.
- By leveraging asynchronous architecture and zero-cost abstractions, the student achieved remarkable performance improvements through extensive testing and optimization.
- The experience deepened their understanding of web development principles and highlighted the framework's strengths in type safety, performance, and developer experience.
Read Full Article
12 Likes
Dev
237

Image Credit: Dev
Advanced Path of Network Programming Deep Exploration from TCP to Application Layer Protocols(1751175401040400)
- Exploration of network programming from TCP to application layer protocols is essential for developers.
- Understanding TCP/IP stack, protocol design considerations, and optimization techniques for performance.
- Challenges in protocol design, serialization formats, security considerations, and network application testing.
- Evolution of protocols, best practices, testing methodologies, and modern trends in network programming.
- Role of modern frameworks in simplifying network programming and conclusion on the future of network technologies.
Read Full Article
14 Likes
Medium
328

Image Credit: Medium
When Your AI App Feels Like It’s Running on Dial-Up (And How to Fix It Without Breaking)
- Building AI features often neglects the importance of production latency, resulting in frustrating user experiences.
- Key issues include model loading time, network bottlenecks, and sequential processing causing delays in responses.
Read Full Article
19 Likes
Dev
213

Image Credit: Dev
Ecosystem Integration Patterns Third Party Design(1751174799164600)
- Choosing a framework involves selecting an ecosystem, not just APIs for integration ease.
- Impressed by Rust framework seamless integration with Rust ecosystem, simplifying functionality extension.
- Perfect logging and monitoring integration, supporting structured logging and various output formats.
- Seamless configuration management integration enhances efficiency, code quality, and performance optimization.
- Deep ecosystem integration results in reduced integration time, improved code reuse, and performance.
Read Full Article
12 Likes
Javarevisited
273

Image Credit: Javarevisited
How to implement Bucket Sort in Java? [Solved] - Example Tutorial
- Some programming job interviews ask about constant time sorting algorithms like O(n) sorting algorithm.
- Research reveals constant time sorting algorithms like bucket sort, counting sort, and radix sort exist.
- These algorithms can sort an array in O(n) time but work with specific input sets.
- Article covers the implementation of Bucket Sort in Java.
Read Full Article
16 Likes
Dev
13

Image Credit: Dev
Beyond the Hype Cycle: A Deep Dive into Generative AI and its Architectural Shifts
- Generative AI is experiencing explosive growth and refinement, with a focus on multimodal models that can understand and generate content across different modalities simultaneously.
- Efficiency and scalability improvements in generative AI involve techniques like quantization, pruning, and knowledge distillation to make models smaller and faster, enabling deployment on devices with limited resources.
- Ethical concerns surrounding generative AI, such as bias mitigation and misuse prevention, are being addressed through data curation, explainable AI, and safety measures.
- Architectural innovations in generative AI, including multimodal integration, efficiency enhancements, and ethical considerations, are driving the field forward with the promise of more exciting advancements in the future.
Read Full Article
Like
Dev
190

Image Credit: Dev
Debugging Techniques and Problem Location Strategies Methodology for Rapid Problem Location in Complex Systems(1751170582875600)
- As a junior computer science student, the individual has gained insights into developer experience development, particularly web framework design and implementation.
- The exploration highlighted the benefits of Rust-based web frameworks, emphasizing memory safety and performance optimization for building high-performance applications.
- Extensive testing and optimization led to significant performance improvements, attributed to the asynchronous architecture and zero-cost abstractions of the framework.
- The experience reinforced the importance of type safety, performance, and developer experience in modern web development, recommending the framework for scalable applications.
Read Full Article
11 Likes
For uninterrupted reading, download the app