Programming News
Medium
426

Image Credit: Medium
Massive Steam hack leaks 89M users are you one of them?
- Reports indicate that 89 million Steam accounts may have been leaked, exposing emails, purchase history, and IP addresses through a third-party service provider used by Valve.
- While no passwords or payment information have been confirmed to be leaked, the user metadata being out there could lead to increased phishing scams and targeted attacks.
- The leaked data, deemed 'highly credible,' includes emails, purchase histories, and more, highlighting the vulnerability when data is shared with partners who lack proper security measures.
- Valve has not officially acknowledged the breach, leading to concerns within the gaming community about the lack of communication and transparency regarding the incident.
- Even though sensitive data like passwords and payment card numbers are believed to be safe, the leaked information can still be used for phishing attempts and account takeovers, especially if users reuse login credentials across multiple platforms.
- The leaked data is already being traded on hacker forums, emphasizing the importance of enhancing security measures and being cautious of potential scams.
- To protect themselves, users are advised to change their passwords, activate Steam Guard Mobile Authenticator, review active sessions, and monitor authorized services linked to their accounts.
- The incident underscores the broader issue of data security vulnerabilities in modern platforms, often stemming from weaknesses in third-party services that handle backend operations.
- Users are urged to stay vigilant against scams, update their security measures, and advocate for enhanced data protection practices to prevent future breaches and maintain trust in online platforms.
- While the breach may not have compromised sensitive payment information, the exposure of user data serves as a stark reminder of the importance of proactive security measures and transparent communication in the digital age.
- Let this serve as a wake-up call for everyone to prioritize data security, push for improved infrastructure, and demand accountability from companies to safeguard user information effectively.
Read Full Article
25 Likes
Medium
81

Image Credit: Medium
Using Vision-Language Models
- Vision-language models (VLMs) are designed to handle tasks involving visual and textual data such as describing images and generating text based on images.
- Most VLMs use transformer-based architectures adapted to process both pixel data and token-based text.
- Dual-encoder models in VLMs use separate neural networks for processing images and text to align embeddings in a shared latent space.
- One popular dual-encoder model, OpenAI’s CLIP, uses transformer-based text encoder and a vision encoder like ResNet or ViT for image processing.
Read Full Article
4 Likes
Dev
145

Image Credit: Dev
Understanding the "Object Literal May Only Specify Known Properties" Error in React + TypeScript
- The error 'Object Literal May Only Specify Known Properties' in React + TypeScript occurs when useState is not properly typed for a state with objects.
- To resolve this error, define a type or interface for the state object to provide type safety and enable autocomplete functionality.
- By defining a type or interface, such as User with uid and name fields, you ensure better type safety, autocompletion, and improved debugging in React components.
- Best practices for using useState with objects include always typing your state, using 'null' for optional states, preferring interfaces for clarity, and validating before rendering for cleaner and more robust components.
Read Full Article
8 Likes
Dev
49

Image Credit: Dev
Daily JavaScript Challenge #JS-179: Sum of Squares of Odd Numbers
- Daily JavaScript Challenge #JS-179: Sum of Squares of Odd Numbers
- The challenge involves calculating the sum of squares of all odd numbers in an array, ignoring even numbers. If the array is empty or has no odd numbers, the function should return 0.
- Developers are encouraged to participate by forking the challenge, writing a solution, testing it, and sharing their approach.
- For more information and to join the discussion, visit the provided links for documentation and interaction with the community.
Read Full Article
3 Likes
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Dev
213

Image Credit: Dev
The Caffeine Chronicles: What Happens When a Developer is Always High on Coffee
- Software developers often rely on caffeine to stay sharp and alert during long coding sessions, but constant consumption can lead to diminishing returns.
- Excessive caffeine intake can disrupt sleep patterns, resulting in shallow and unsatisfying rest, leading to decreased cognitive function and productivity.
- Caffeine-induced anxiety and decision fatigue can negatively impact a developer's mental well-being and ability to focus on important tasks.
- Long-term reliance on caffeine can take a physical toll on the body, leading to jitters, heartburn, dehydration, and eventual burnout.
Read Full Article
12 Likes
Dev
231

Image Credit: Dev
How to Fix Android Studio Plugin Issues After Updates?
- Many developers face plugin issues after updating Android Studio, with plugins breaking or becoming invisible.
- The problem stems from compatibility issues due to changes in Android Studio's API, dependency management, or IDE architecture.
- To fix plugin problems like Android Drawable Importer not showing up, developers can update dependencies, verify plugin configuration, clean and rebuild the project, check logs, and seek help from online resources.
- Enabling debug logging, reviewing community repositories like MPArnold's and Skeaner’s, and staying updated on plugin configurations can help resolve post-update plugin issues in Android Studio.
Read Full Article
13 Likes
Medium
395
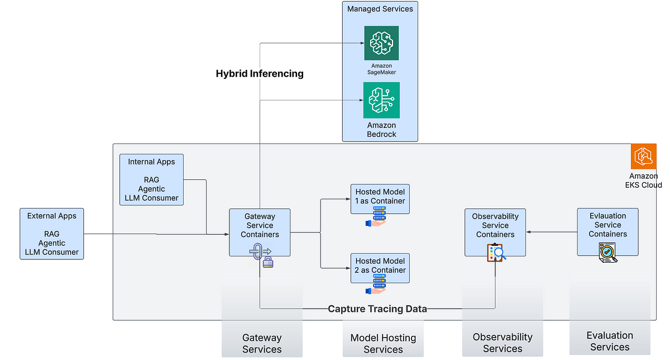
Image Credit: Medium
Building GenAI solutions on Amazon EKS
- Self-hosting AI solutions on Amazon EKS provides more control over sensitive data and hybrid deployment, enhancing quality and productivity for teams through integration of existing data sources.
- Customizing models through self-hosting allows tuning to specific needs, resulting in competitive performance with cost efficiency.
- Hosting models on the same platform as applications reduces latency, ensuring better user experience, particularly for applications with strict latency requirements.
- Deploying generative AI applications in production requires complementary components like prompt caching, guardrails for safe usage, observability tools, and model evaluation capabilities.
- A self-hosting stack requires multiple components, leveraging open-source software to self-host models in a cost-efficient manner with Amazon EKS.
- Key components include Model Gateway Service, Model Hosting Services, Model Evaluation Services, and Model Observability Services, all running as containers using Amazon EKS.
- Model Gateway enables centralized access to models, hybrid inferencing, and secure model access, while Model Hosting Services expose model weights as APIs with efficient inferencing capabilities.
- Model Evaluation Services assist in choosing the right model through rigorous testing, real-time evaluation, and continuous optimization of models and prompts.
- Model Observability Services capture essential metrics like latency and payload data, enabling better model assessment and optimization for changing business needs.
- Open-source frameworks such as LiteLLM, vLLM, LangFuse, and others fulfill the roles of key components for self-hosting AI solutions on Amazon EKS.
- LangFuse offers observability by tracking various data points, while also assisting in model evaluation through benchmarking and automated evaluation methods.
Read Full Article
23 Likes
Python Blogs
231

Image Credit: Python Blogs
What is the purpose of VPN in AWS?
- VPN in AWS is crucial for establishing secure connections between on-premises environments and cloud resources.
- It encrypts data transmission, ensuring privacy and protection of sensitive information.
- Key purposes include secure communication, hybrid cloud architecture, remote access, and reducing public exposure.
- AWS offers types of VPNs like Site-to-Site VPN, Client VPN, and third-party solutions, providing benefits of security, cost-effectiveness, scalability, and redundancy.
Read Full Article
13 Likes
Dev
63

Image Credit: Dev
What Are Today’s Top Movie Plots? I Wrote a Python Scraper to Find Out
- A Python scraper was built to analyze the plots of today's top movies by pulling data from IMDb.
- The script gathers plot summaries of the top 25 movies, creates word clouds to visualize common themes, and offers insights into popular genres.
- Skills acquired include data cleaning with NLTK, web scraping using requests and BeautifulSoup, and data visualization with WordCloud and matplotlib.
- The project also focused on handling website quirks, avoiding anti-bot measures, and being considerate by using time.sleep() to avoid overloading IMDb's servers.
Read Full Article
3 Likes
Medium
177
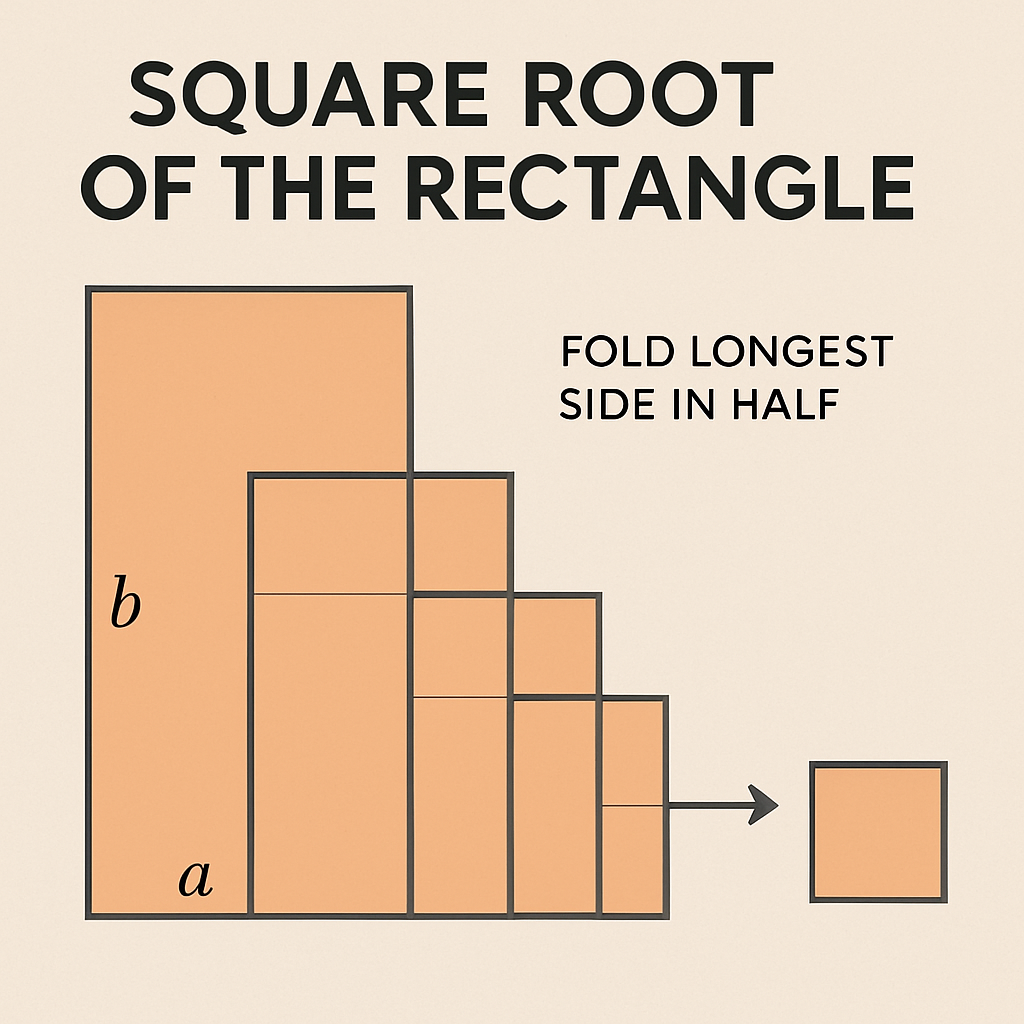
Image Credit: Medium
Square Root Of The Rectangle!
- The article explores the concept of folding a rectangle into a square and determining the number of folds based on the rectangle's dimensions.
- Initially perceived as a silly thought, the idea persisted in the author's mind, leading to a deeper investigation.
- After struggling manually, the author turned to a Python code, which surprisingly simplified the calculations in about ten lines of code.
- The process involves dividing one side of the rectangle in half until it matches the length of the other side.
- The article discusses patterns where one side must be a power of two and the other side a multiple of the first.
- Following a general formula, the author tested various numbers and successfully reached a square after 2148 folds.
- However, the limitation of floating-point numbers in computers caused discrepancies in the results as the numbers approached equality.
- The author's friend explained that due to machine precision, the code might return seemingly accurate results that are actually too close to differentiate.
- This limitation led to the realization that only a specific equation (*) could solve the concept, with other numbers infinitely approaching 0 but never reaching a 0x0 square.
- The article concludes by highlighting the application of mathematical concepts in everyday life and the importance of curiosity and learning in exploring complex problems.
Read Full Article
10 Likes
Medium
249

Growing Laravel in Uganda: A Community on the Rise
- A small but passionate Laravel community is emerging in Uganda and seeking support to grow and flourish.
- Laravel is a popular PHP framework globally, known for its clean syntax, built-in tools, and emphasis on developer happiness.
- Uganda's rising tech talent is aligning with Laravel due to its approachable syntax, detailed documentation, and large support base.
- Challenges faced by the Laravel community in Uganda include limited resources, lack of visibility, and the need for more structured support and events.
Read Full Article
15 Likes
Medium
435
Image Credit: Medium
5 (More) Bash Snippets That Saved My Dev Life
- Developed a helper script to manage zombie or orphaned processes in AI inference applications.
- Created a tracker to log config.json changes in AI model behavior experiments.
- Implemented a script to prevent ffmpeg from filling up disk space while recording video feeds on edge devices.
- Utilized a watchdog script to ensure post-deployment configs and binaries integrity.
Read Full Article
26 Likes
Dev
22

Image Credit: Dev
DocTextExtractor: A Flutter Package to Extract Text from Word, PDF, Google Docs, and Markdown
- DocTextExtractor is a Dart package created to extract text from various formats like .doc, .docx, .pdf, Google Docs URLs, and .md files.
- The tool was developed to support NotteChat, an app facilitating conversational interaction with documents using AI.
- Challenges in supporting multiple document formats led to the creation of DocTextExtractor for seamless text extraction.
- Key features include unified API, clean filename extraction, minimal dependencies, and cross-platform support.
- Various technologies like http, syncfusion_flutter_pdf, archive + xml, and markdown were used to build DocTextExtractor.
- The Dart package offers a TextExtractor class with features like unified return types, smart format detection, and offline support.
- Format-specific logic was applied for .doc, .docx, .md, PDF, and Google Docs for efficient text extraction.
- DocTextExtractor is crucial for NotteChat's AI-powered document chat, enabling AI chat, offline use, smart UX, and versatile support.
- Steps to integrate DocTextExtractor into Flutter apps involve adding dependencies, importing, initializing, and extracting text from URLs or local files.
- Integration with AI APIs like OpenAI, Gemini, or Sonar can enhance app functionality using extracted text.
Read Full Article
1 Like
Dev
299

Image Credit: Dev
Deploying Storage Solution for Testing and Training.
- A technical specification for a storage infrastructure has been outlined for the IT department's testing and training environments with a focus on scalability, high availability, and performance.
- To set up the project resources, a resource group needs to be created in the Azure portal with a specified name and region for consistent use.
- For facilitating testing and training, a storage account must be set up in the Azure portal with basic settings like Locally-redundant storage (LRS) and Secure transfer enabled.
- To ensure security and efficiency, configurations like Minimum TLS version 1.2, Disable storage account key access, and enabling public network access from all networks need to be implemented.
Read Full Article
18 Likes
Johndcook
376

Multiplying by quaternions on the left and right
- The map that takes a quaternion x to the quaternion qx is linear, represented as multiplication by a matrix.
- The matrix representation for multiplying on the left by q is different from the matrix representation for multiplying on the right by q.
- One can prove both matrix representations are correct by demonstrating their accuracy when q = 1, i, j, and k.
- The post discusses how to represent rotations with quaternions and provides an equation for the equivalent rotation matrix for a rotation described by a quaternion.
Read Full Article
22 Likes
For uninterrupted reading, download the app