Programming News
Dev
1M
32

Image Credit: Dev
LLM Memory Injection Attacks - Primer & Playbook
- Large-language-model “memories” can enhance user experience but also increase vulnerability to memory injection attacks.
- Memory injection attacks can occur through Interaction-Only Write, Dormant Persistence, and Cross-User Contamination patterns.
- Defense playbook includes hardening inputs at the edge, compartmentalizing memory, and implementing a runtime anomaly guardrail.
- Operational checklist involves edge filtering, per-tenant memory management, guardrail implementation, audit jobs, and red-team rotations.
Read Full Article
1 Like
Medium
1M
0
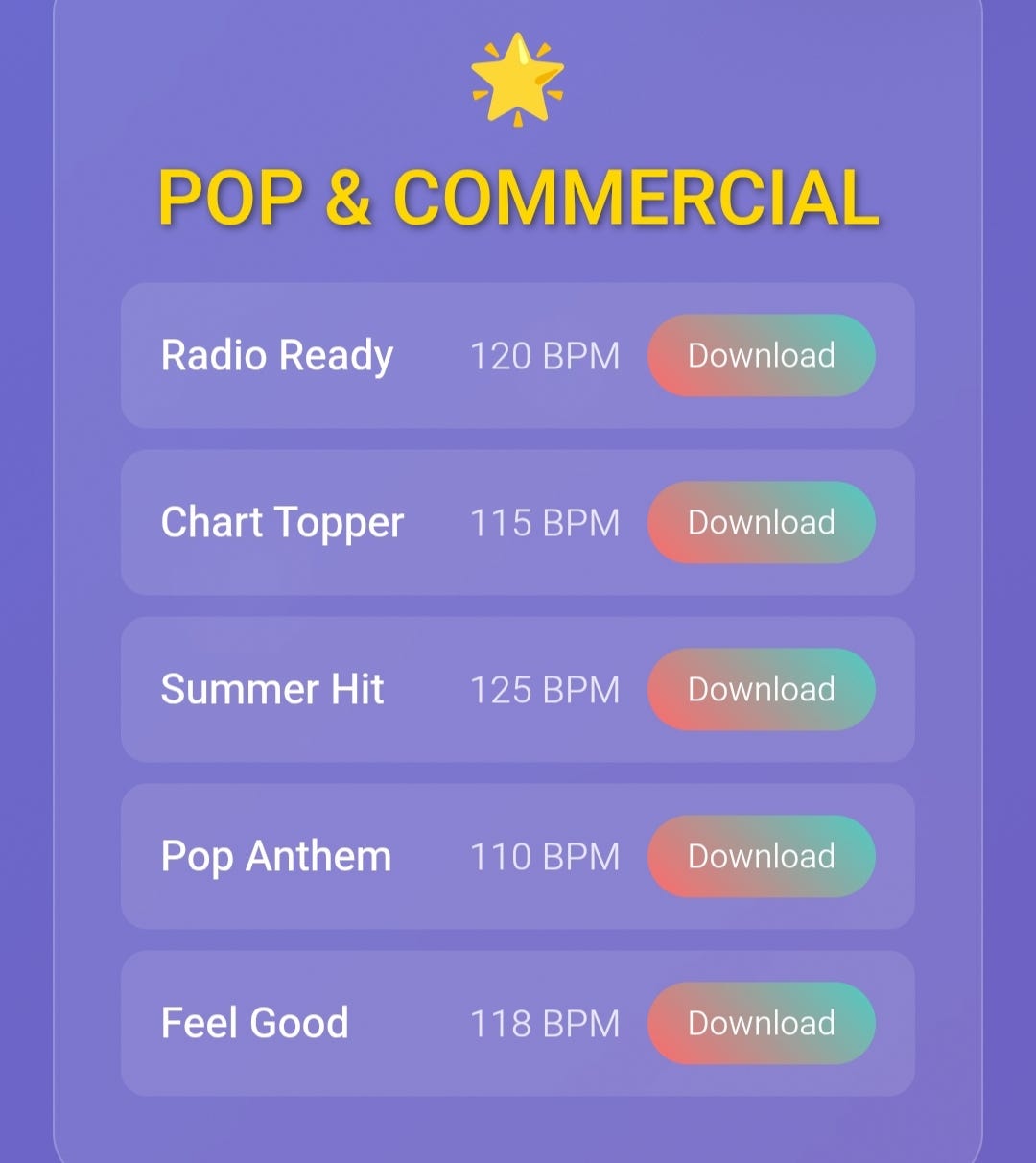
Image Credit: Medium
tvccoin Music Pack
- HTML page designed to showcase music collections with modern, responsive, and aesthetic features.
- Features smooth animations, working search bar, and cards organized by 10 music genres and 50 named tracks.
- Simulated download buttons, hover effects, and search functionality by genre or track name included.
- Genres range from Trap & Hip-Hop, Reggaeton, Electronic & EDM, R&B & Soul, Pop & Commercial, Rock & Alternative, Ambient & Chill, Latin Fusion, Drill & Street, to Afrobeat & World.
Read Full Article
Like
Dev
1M
9

Image Credit: Dev
Why Type Is the Better Choice in React + TypeScript
- React combined with TypeScript offers a powerful and safe development environment for modern web development.
- Choosing between type and interface in React projects depends on specific use cases and coding styles.
- For modern React, type is generally more suitable due to its flexibility in handling unions, intersections, and primitive types, making the code cleaner and easier to read.
- Interface may be preferred for extensible data types or working with classes, but consistency within the team or project is crucial for maintainable code.
Read Full Article
Like
Medium
1M
391

Kenniesha Burrell: protect our women and children from abuse.
- 619 women were murdered in Jamaica between 2019 and 2023, with an average of 124 women per year.
- 1,027 children were reported missing in 2023 in Jamaica, with 151 still missing, including 133 girls and 18 boys.
- Organizations like Hear the Children’s Cry are working towards raising awareness about the issue of missing children.
- Various organizations in Jamaica, such as Woman Inc. and Jamaicans for Justice, provide support and resources for those facing abuse.
Read Full Article
23 Likes
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Medium
1M
45

Image Credit: Medium
The Implementor Protocol: How Narrative Trauma Changed My AI’s Decision-Making
- Discrepancy between how people use AI publicly versus privately highlighted in the article.
- Author experimented by sharing context and stories with AI assistant instead of just writing detailed prompts.
- Results showed AI started explaining trade-offs and questioning assumptions, indicating a deeper level of reasoning.
- Observation made on the importance of cultural memory in interactions with AI and the impact on knowledge transfer.
Read Full Article
2 Likes
Dev
1M
341

Image Credit: Dev
CH-05: The Lost Code — Jai & Veeru vs. The Ghost in the Repository
- Jai and Veeru encountered a strange issue where user data was disappearing from their app logs, suspecting a ghost in the repository.
- The problem was identified as lost data in multi-threaded requests due to issues with ThreadLocal in virtual threads.
- The solution presented was to use Java 21's Scoped Values as a modern replacement for ThreadLocal, ensuring data consistency and concurrency safety.
- As Jai and Veeru celebrated fixing the data loss, they discovered a mysterious unauthorized commit in the repository, raising concerns about a potential supply chain attack and the need for security checks on dependencies.
Read Full Article
20 Likes
Dev
1M
86

Image Credit: Dev
Rank It Your Way with Tierlyst! 🎯✨
- Tierlyst is a sleek and responsive tier list editor perfect for ranking various items such as games, characters, anime, and more.
- Key Features of Tierlyst include Drag & Drop functionality for desktop and Touch Controls for mobile, Custom Image Upload, Full Customization options, Exporting as PNG or Save as JSON, No Signups required, and Multi-Language support.
- Tech Stack used in Tierlyst includes React / Next.js, Tailwind, Framer Motion, html-to-image, and next-intl.
- Explore Tierlyst at https://tierlyst.vercel.app/ for an intuitive ranking experience.
Read Full Article
5 Likes
Dev
1M
387

Image Credit: Dev
Why Functional Decomposition Leads to Bad System Design
- System decomposition should clearly show how components interact to prevent future difficulties in maintenance and extension.
- Avoid functional decomposition as it creates complex dependencies, inhibits component reuse, and leads to tight coupling within systems.
- Functional decomposition categorizes services based on tasks performed, resulting in rigid service sequences and limited reusability.
- Relying on functional decomposition makes services tightly coupled, bloated, and difficult to maintain or extend over time.
- Having the client handle service calls increases its complexity and ties it closely to system logic, leading to challenges in adapting to changes.
- Multiple entry points for clients increase redundancy, effort, and costs, while a unified entry point simplifies architecture and management.
- Beware of bad system design caused by functional decomposition, as it introduces unnecessary complexity and tight coupling.
- Anti-design patterns and strategies to avoid functional decomposition will be explored in upcoming articles by the author.
- Continuous learning and practice of effective system design principles are crucial in ensuring robust and scalable software solutions.
- Check the previous article linked in the conclusion for further insights on system decomposition and design principles.
Read Full Article
23 Likes
Dev
1M
341

Image Credit: Dev
Retrieving System MAC Address Across OS Platforms
- A PHP function is presented for retrieving the MAC address of a server, catering to Windows and Linux/Unix/Mac environments.
- Operating system detection is done using strtoupper(substr(PHP_OS, 0, 3)) to differentiate between Windows and non-Windows systems.
- For Windows, the function captures the output of 'getmac' command to extract and return the MAC address using a regular expression.
- In Linux/Unix/Mac environments, the function uses 'ifconfig' or 'ip link' along with 'grep' to extract and return the MAC address.
- Error handling is implemented to manage exceptions that may occur during the command execution in the PHP script.
- Important considerations include permissions for executing system commands, handling multiple network interfaces, security risks, and environment differences.
- Overall, the PHP snippet offers a practical method to obtain the system's MAC address across various OS platforms, emphasizing caution and awareness.
- Considerations about virtualization and containers are also highlighted in terms of MAC address retrieval.
- The script's functionality, including regex matching for MAC address extraction, provides versatility for different system setups.
- I hope this summary helps you understand the PHP function for retrieving system MAC addresses comprehensively.
- Happy coding and stay mindful of security implications and environmental variations in MAC address retrieval processes!
Read Full Article
20 Likes
Dev
1M
405

Image Credit: Dev
T vs any in TypeScript
- Both 'any' and generic 'T' in TypeScript mean 'could be any kind of type', but there is a significant difference.
- 'any' is never constrained, while generic 'T' is always under constraint somewhere.
- Example with generic 'T': 'T' is under constraint, specifying that 'stuff' can only be of 'T' type, and the return type can only be an array of 'T'.
- Example with 'any': 'any' is not constrained by anything, allowing code to be valid even if it doesn't achieve the initial goal.
Read Full Article
24 Likes
Dev
1M
4

Image Credit: Dev
AltSchool Of Engineering Tinyuka’24 Month 3 Week 5
- CSS Grid Layout simplifies complex and responsive web designs by arranging elements into rows and columns with minimal code.
- Grid Container is created by setting display property to grid or inline-grid; define rows and columns using grid-template-rows and grid-template-columns.
- Control item placement with grid-column and grid-row properties; create spacing with grid-gap, row-gap, and column-gap.
- Name grid areas with grid-template-areas and position items within those areas using grid-area.
- Responsive design is facilitated using functions like repeat() and minmax() to adjust the grid based on available space.
- Positioned layout allows precise control over element placement, offering relative, absolute, fixed, and sticky positioning options.
- Anchor positioning enables elements to be positioned relative to another element's location on the page, simplifying layout designs.
- Understanding z-index, stacking contexts, and the natural stacking order in CSS is essential for controlling visual layering of elements.
- Overflow property controls content display when it exceeds its container's boundaries, with values like auto, hidden, scroll, visible, and clip.
- Creating scroll containers using the overflow property allows content to remain within specified boundaries while enabling scrolling to access overflowed content.
Read Full Article
Like
Dev
1M
255

Image Credit: Dev
PlankDB – A Quantum-Powered Key-Value Store with Grover Search and Spring Boot
- PlankDB is an experimental key-value store that integrates quantum computing for probabilistic search using Grover's algorithm.
- It is built using Java 17 and Spring Boot, following Clean Architecture principles, and offers integration with IBM Qiskit for local or remote quantum execution.
- With PlankDB, users can create collections, insert key-value entries, and perform classical or quantum-powered search queries without needing to understand the complex math behind Grover's algorithm.
- The project is open-source on GitHub (https://github.com/swampus/plank-db) and welcomes feedback, contributions, and engagement from the community to explore real-world applications of quantum technology.
Read Full Article
15 Likes
Medium
1M
145

Image Credit: Medium
Starting My Machine Learning Journey: Why I’m Learning in Public
- The author is starting their machine learning journey and is excited about building something cool using ML, like an app that predicts memes or tunes music to your mood.
- They believe that understanding ML requires math and code, so they are focusing on object-oriented programming and plan to dive into Stanford's courses on AI concepts and reinforcement learning.
- They plan to create beginner-friendly content to give back to the community and find learning in public more enjoyable than learning alone.
- The blog will contain messy, honest, and helpful posts about tools, resources, mindsets, and the journey of learning ML, inviting others to join them on this learning path.
Read Full Article
8 Likes
Dev
1M
113

Image Credit: Dev
Getting Started with Amazon Q Developer CLI by Building a Game
- Amazon introduced Amazon Q Developer CLI, a generative AI coding assistant for developers.
- Amazon Q Developer CLI allows code generation, debugging, template creation, and application management within the terminal.
- Setting up Amazon Q Developer CLI involves specific steps for different operating systems like Windows, Linux, or macOS.
- A guide for Windows users using Windows Subsystem for Linux (WSL) to install Amazon Q CLI is provided.
- After installation, users can log in, run q doctor command, and start interacting with q chat directly from the terminal.
- Users can quickly build a game using Python and Pygame through Amazon Q Developer CLI by providing prompts.
- Amazon Q effectively scaffolds the project for a 2D Platformer Game with various features like player character, platforms, collectibles, enemies, game states, and UI elements.
- The game includes mechanics like gravity, jumping, collision detection, score, lives, and smooth gameplay loop.
- Users can further enhance the game by adding levels, power-ups, or improving visuals using sprites.
- Amazon Q Developer CLI simplifies game development even for beginners, allowing for continuous improvement and feature additions.
Read Full Article
6 Likes
Dev
1M
136

Image Credit: Dev
SAST, DAST, & SCA: The Cybersecurity Avengers Your Code Needs 🛡️💻
- SAST, DAST, and SCA are crucial for protecting code against cybersecurity threats and vulnerabilities.
- SAST (Static Application Security Testing) detects flaws in source code pre-runtime like SQL injection risks and hardcoded passwords.
- DAST (Dynamic Application Security Testing) simulates real attacks on running apps to find vulnerabilities like broken authentication and XSS.
- SCA (Software Composition Analysis) scans dependencies for risks in third-party code like outdated libraries and known vulnerabilities.
Read Full Article
8 Likes
For uninterrupted reading, download the app