Cloud News
Tech Radar
321

Image Credit: Tech Radar
NYT Strands today — hints, answers and spangram for Monday, September 16 (game #197)
- NYT Strands is the NYT's latest word game, following Wordle and Connections.
- Today's theme for NYT Strands is 'What a stud!'
- The clue words for NYT Strands today are LONE, BORN, SCAR, SCAN, PING, and MEET.
- The spangram hint for today's NYT Strands is 'Skin adornments', and it touches the left side of the 4th row and the right side of the 5th row.
Read Full Article
19 Likes
Tech Radar
50

Image Credit: Tech Radar
Quordle today – hints and answers for Monday, September 16 (game #966)
- Quordle has nearly completed 1000 games and still continues to offer challenges to players
- The number of vowels in Quordle for game #966 is 4, excluding 'Y'
- Two Quordle answers contain a repeated letter for game #966.
- The letters 'J', 'Q', 'X' and 'Z' are not present in Quordle for game #966.
- None of the Quordle answers for game #966 start with the same letter.
- The starting letters of the Quordle answers for game #966 are - 'R', 'S', 'F' and 'U'.
- The answers to Quordle for game #966 are - 'ROUGE', 'SWAMP', 'FUGUE' and 'UNDUE'.
- There are five 'U's in game #966, including two in 'FUGUE' and 'UNDUE'.
- The game for day #966 is quite vowel-heavy, with 10 of the 20 letters being A, E, O, or U.
- The game has mixed difficulty levels with repeated letters and uncommon words.
Read Full Article
3 Likes
Dev
280

Image Credit: Dev
Unveiling Azure: The Future of Cloud for .NET Developers
- Azure is Microsoft’s cloud computing platform, offering a wide range of services to help businesses and developers build, test, deploy, and manage applications.
- For .NET developers, Azure offers a series of benefits that make cloud development simpler and more integrated.
- Key Azure services for .NET developers include Azure App Service, Azure Functions, Azure SQL Database, Azure Blob Storage, and Azure Service Bus.
- Azure provides a complete ecosystem for developing, managing, and monitoring .NET applications efficiently and securely.
Read Full Article
16 Likes
Dev
372
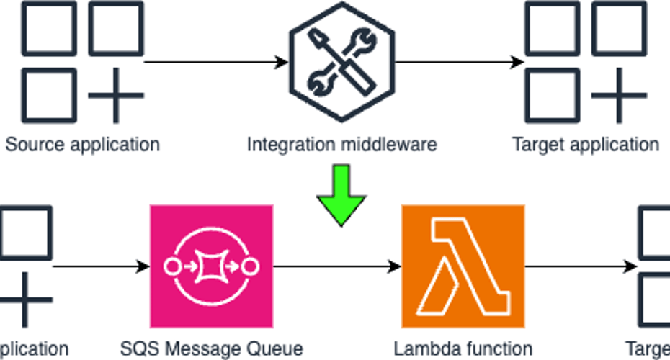
Image Credit: Dev
AWS SQS as an alternative to traditional application integration middleware
- Traditional application integration middleware has limitations when it comes to handling large amounts of data or high traffic.
- AWS SQS, a managed message queue service, offers strong scalability capabilities and can be a good alternative.
- An example project using AWS SQS and Lambda function showed high performance and resilience.
- SQS supports features like processing messages in order and limiting the number of messages sent in parallel.
Read Full Article
22 Likes
Discover more
- Programming News
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Digitaltrends
170
Image Credit: Digitaltrends
NordPass vs. Proton Pass: best free and low-cost password manager
- NordPass and Proton Pass are two of the best password managers and both have surprisingly affordable plans, as well as good free versions.
- NordPass has a good free version that lets you store an unlimited number of passwords to sync and autofill logins across devices.
- Proton Free is a cybersecurity bundle that includes Proton Pass at no charge. It’s more complete than NordPass Free, since secure sharing is supported for two vaults.
- With both services, you get more when you subscribe, and the prices are inexpensive. Unless your budget is very tight, a subscription is usually worthwhile.
- Both have modern designs, and I had no trouble finding my way around. NordPass and Proton Pass also have web versions.
- Autofill and cross-platform syncing are the most critical components of a password manager. NordPass handles this effortlessly, and so does Proton Pass.
- Secure login sharing is another essential feature of the best password managers. NordPass and Proton Pass offer good sharing features, with options to limit whether the recipient can autofill the login, share it with others, or edit it.
- NordPass and Proton commit to protecting your privacy. Both get regular independent security audits to verify their servers can’t be breached and the encryption technology is working correctly with no vulnerabilities that hackers can take advantage of.
- Overall, I prefer Proton Pass, which has full-featured free and paid versions of its password manager. However, for families of four to six, the NordPass Family plan offers better value.
- Bitwarden offers a lower-cost family plan with support for six premium accounts.
Read Full Article
10 Likes
Tech Radar
165

Image Credit: Tech Radar
Meta Connect 2024: 5 things I want to see at the rumored Meta Quest 3S launch event
- Meta Connect 2024 is an annual Meta event that reveals new hardware coming soon and future hardware and software.
- Five announcements are expected at the event, with the Meta Quest 3S likely to be the biggest reveal.
- The Quest 3S will boast the Snapdragon XR2 Gen 2 chipset, but a bulkier body and lower-spec displays to target a lower price tag.
- Non-Meta VR headsets from Asus, Lenovo and Xbox may finally be showcased utilizing Meta's Horizon OS.
- Meta may tease a prototype AR glasses model despite launch seeming unlikely anytime soon.
- Meta AI is likely to have plenty of time devoted to it, with a wider rollout and better parity with AI rivals being expected.
- A mini Quest Gaming Showcase featuring new and exciting VR titles seems unlikely at the event despite the potential revival of GTA: San Andreas VR.
Read Full Article
9 Likes
Unite
261

Image Credit: Unite
Scientists Engineer Molecule-Scale Memory States, Surpassing Traditional Computing Limits
- A group of researchers at the University of Limerick have developed a method for designing molecules that can outperform traditional computing.
- The approach, inspired by the human brain's functioning, aims to enhance the speed and energy efficiency of artificial intelligence systems.
- Using the natural movements of atoms within molecules, the researchers achieved multiple memory states within a single molecular structure.
- This breakthrough in molecular-scale manipulation has the potential to revolutionize various industries and lead to more efficient and powerful computing systems.
Read Full Article
15 Likes
Dev
137

Image Credit: Dev
Security Posture for Production Grade K8 Cluster
- Securing a production Kubernetes cluster requires a multi-layered approach, addressing network security, access control, cluster hardening, pod-level security, and continuous monitoring.
- Use Network Policies: Kubernetes allows you to define network policies to control the communication between pods.
- Enable TLS/SSL to encrypt traffic between different Kubernetes components, such as communication between the API server and etcd.
- Implement RBAC to restrict what users and service accounts can do in the cluster.
- Integrate Kubernetes with identity providers such as AWS IAM, Azure AD, or Google Cloud IAM to leverage existing identity management solutions for authenticating users.
- Use cloud provider-specific security groups to control access to the nodes. Only expose necessary ports and limit access to trusted IPs.
- Ensure pods are not running as root by specifying runAsNonRoot in the security context of the pod specification.
- Use trusted and verified container images from secure registries, and avoid using images with known vulnerabilities.
- Use Kubernetes Secrets to store sensitive data such as API keys and passwords. Ensure secrets are encrypted at rest.
- Enable Kubernetes audit logs to track all events in the cluster. Monitor the performance of the cluster and set up alerts for unusual activities.
Read Full Article
8 Likes
Dev
174

Image Credit: Dev
Set version numbers in Bicep templates
- Bicep templates and package.json files are being updated with new version numbers.
- Bicep templates now use the versions set by rush in the Azure bicep templates.
- Provisioned resources will be appropriately tagged with the new version numbers.
- A new Template Spec version will be calculated based on the version changes of the Bicep templates.
Read Full Article
10 Likes
Dev
317

Image Credit: Dev
Rush configuration
- This post outlines the configuration needed to implement rush orchestration for various purposes in an IaC project.
- The configuration includes steps to install rush, generate rush configuration files, and add package.json files for each folder containing Bicep templates.
- The rush.json file is updated to configure the repository URL, email validation, project references, and version policies.
- Release managers can use rush version to increase package versions and generate/update changelog files.
Read Full Article
19 Likes
Digitaltrends
257

Image Credit: Digitaltrends
Apple just proved it learned from the Touch Bar’s failure
- Apple has revealed a new touch-sensitive Camera Control in its latest iPhone range coupled with the ability to take photos, change the camera’s focus and control depth of field; its compactness makes it practical. The Camera Control has striking similarities to Apple’s touch-sensitive strip, the Touch Bar, which was a failure because it didn’t get enough support from third-party apps and required users to move their hands away from the keyboard and trackpad. Apple appears to have learnt from the Touch Bar’s failure and made the Camera Control highly specific to camera use, small and compact, out of the way when you don’t need it, but ready and waiting when you do.
- It is believed that Apple has reworked a previously questionable idea into something that could actually have wider applications than just taking pictures on your iPhone. Apple's ability to learn from previous mistakes and pull something better out of its proverbial hat has given rise to the possibility of adapting the Camera Control on Mac devices, with potential to be used to enable quick actions and gestures in macOS.
- While this is still in the realm of speculation, the Camera Control has shown that Apple is capable of innovating concepts from the past into something better, as it has done in the case of the Mac Pro’s “cheese grater” design, and doing more with it. Apple fans wait with bated breath to see what amazing development lies ahead.
Read Full Article
15 Likes
Tech Radar
78

Image Credit: Tech Radar
Flappy Bird reboot will never match the awfulness of the original and that's a problem
- Flappy Bird, the popular mobile game known for its simplicity and high level of difficulty, set a new standard in mobile gaming upon its release in 2014.
- Despite its frustrating gameplay, Flappy Bird garnered a large following and became a phenomenon, leading to the developer, Dong Nguyen, removing the game from the app store.
- Since then, various attempts have been made to recreate the success of Flappy Bird, but none have matched the original's appeal.
- A new Flappy Bird created by fans aims to incorporate traditional mobile gaming elements like levels, skins, and multiplayer features, but it may lose the challenging and addictive nature of the original.
Read Full Article
4 Likes
Tech Republic
307

Cloud Access Security Broker Policy
- The Cloud Access Security Broker Policy aims to establish guidelines and procedures for secure and efficient use of cloud-based services.
- It mitigates risks associated with cloud adoption, protects sensitive data, ensures compliance, and promotes best practices for CASB deployment and usage.
- The policy includes implementing a CASB solution for continuous monitoring, management, and security of cloud service usage.
- The CASB solution enforces security policies, detects policy violations, and regularly updates to address emerging threats.
Read Full Article
18 Likes
Dev
101

Image Credit: Dev
Transforming Java 8 Code to Java 17 Using Amazon Q Transformation
- Upgrading from Java 8 to Java 17 offers substantial benefits such as performance improvements and enhanced security.
- Amazon Q's transformation capabilities automate the process of upgrading Java 8 code to Java 17.
- Java 17 introduces features like sealed classes, pattern matching, and text blocks.
- After transformation, it is essential to test the code, make manual refinements if necessary, and deploy the upgraded application.
Read Full Article
6 Likes
Digitaltrends
0

Image Credit: Digitaltrends
Nvidia’s most underrated DLSS feature deserves far more attention
- Nvidia's Ray Reconstruction is an AI-powered denoiser that improves graphics quality in games with heavy path tracing or ray tracing implementations.
- Although Ray Reconstruction has been available for over a year, only five games currently support it.
- The lack of Ray Reconstruction became obvious while playing Black Myth: Wukong.
- In games using path tracing or ray tracing, images can appear noisy due to a sampling of rays for each pixel.
- Ray Reconstruction is a denoiser-powered AI that smoothens over rough edges and delivers better results in terms of reflections, shadows, and highlights.
- The feature reproduces the transparency of shallow water, which is lost in its absence.
- Compared to DLSS Frame Generation, Ray Reconstruction has no restrictions on older RTX graphics cards.
- Nvidia suggests that Ray Reconstruction works best with heavy ray tracing games, and it unlocks the gaming features visually.
- In the future, as more games push for heavy ray tracing implementations, Ray Reconstruction is expected to keep pace.
- Nvidia's Ray Reconstruction is a key feature that deserves more attention and support from game developers.
Read Full Article
Like
For uninterrupted reading, download the app