Cyber Crime News
TechCrunch
65

Image Credit: TechCrunch
US, French authorities confirm arrest of BreachForums hackers
- U.S. and French authorities have confirmed the arrests of five hackers accused of major hacks and involvement in a cybercrime forum.
- British national Kai West, known as IntelBroker, is indicted for leading a hacking group and causing over $25 million in damages targeting various victims.
- The hackers were involved in sensitive data sales and were part of a cybercrime forum named BreachForums, previously shut down by law enforcement agencies.
- West, along with four other individuals, faces extradition and charges related to computer intrusions, wire fraud, and more.
Read Full Article
3 Likes
Analyticsindiamag
261

Image Credit: Analyticsindiamag
India Lost ₹22,812 Crore to Cyber Fraud in 2024: Report
- India ranked second globally in 2024 for crypto attacks, recording 95 major attacks.
- Cybercrime complaints in India surged from 15.56 lakh in 2023 to 19.18 lakh in 2024, with citizens losing ₹22,812 crore in 2024.
- 82.6% of phishing campaigns in 2024 used AI-generated content, with a rise in QR code phishing attacks in India.
- Rural India is experiencing a rapid increase in cybercrime cases, highlighting the need for cybersecurity awareness and digital safety measures.
Read Full Article
15 Likes
TechJuice
99

Image Credit: TechJuice
What Are Some of the Common Scams Right Now? (And How To Avoid Them!)
- Common scams on the internet are evolving fast with the aid of AI tools and deepfake technology.
- AI is making scams more convincing, leading to a surge in sophisticated phishing campaigns and fraud schemes.
- AI-powered common scams include phishing, romance scams, job offer scams, sextortion, toll violation scams, and charity fraud.
- The surge in common scams is fueled by a recent mega data breach and the availability of open-source AI tools.
Read Full Article
6 Likes
VoIP
402

Image Credit: VoIP
AT&T Settles $177M for Massive Data Breach Scandals
- AT&T is set to pay $177 million in a settlement to customers affected by two major data breaches in 2019 and 2024.
- The breaches exposed sensitive personal information of millions of users, triggering class-action lawsuits.
- AT&T denies responsibility for the breaches but agreed to the settlement to avoid prolonged litigation.
- Eligible customers could receive up to $5,000 for the 2019 breach and up to $2,500 for the 2024 incident, with final approval expected soon.
Read Full Article
22 Likes
Medium
199

Image Credit: Medium
How to Protect Kids and Family from Cyber Crime?
- Cyber crime can occur through various means like hacking and scams, especially targeting children who may not comprehend the risks.
- Parents should communicate early with their children about internet risks, using simple language and encouraging questions.
- It's important to set limits on device usage to prevent potential issues and ensure both safety and health.
- Utilizing parental controls on devices can help block harmful websites and applications, adding an extra layer of security for children.
Read Full Article
12 Likes
Silicon
91

Image Credit: Silicon
Russia Frees REvil Hackers, Despite Guilty Pleas
- Russia has released four members of the REvil hacking gang, despite sentencing them to 5 years in prison.
- The hackers, who had pled guilty to fraud and malware distribution charges, were freed after spending time in detention.
- The gang was known for cyberattacks on high-profile targets like Colonial Pipeline and JBS Foods.
- US warnings led to Russian arrests, but the court ruled the hackers had served enough detention time.
Read Full Article
5 Likes
Securityaffairs
356

Image Credit: Securityaffairs
Hackers deploy fake SonicWall VPN App to steal corporate credentials
- Hackers have deployed a fake version of the SonicWall NetExtender SSL VPN app to steal user credentials for corporate networks.
- The trojanized app, known as SilentRoute, tricks users into exposing their data, allowing attackers to gain unauthorized access and steal sensitive information.
- The malicious version of NetExtender bypasses digital certificate checks and sends stolen VPN credentials to a remote server.
- SonicWall and Microsoft have taken down the fake sites hosting the trojanized app and users are advised to download software only from official sources.
Read Full Article
21 Likes
Securityaffairs
291

Image Credit: Securityaffairs
Mainline Health Systems data breach impacted over 100,000 individuals
- Mainline Health Systems, a nonprofit health center in Arkansas, disclosed a data breach affecting over 100,000 individuals.
- The breach occurred on or about April 10, 2024, impacting the company's network.
- The organization promptly investigated the incident, engaged cybersecurity experts, and notified law enforcement.
- The breach notification letter to the Maine Attorney General's Office confirmed unauthorized access to protected personal information.
- The INC RANSOM group claimed responsibility for the attack and included the organization on its Tor leak site.
- INC RANSOM, active since 2023, has targeted several organizations, including the NHS of Scotland and Xerox Corp.
Read Full Article
17 Likes
Securelist
83

Image Credit: Securelist
AI and collaboration tools: how cyberattackers are targeting SMBs in 2025
- Cyberattackers target SMBs due to assumed weaker security measures compared to larger enterprises, with AI-driven attacks increasing in prevalence.
- AI tools like ChatGPT and DeepSeek are increasingly used to disguise malware, with threats imitating popular tools such as Zoom and Microsoft Office applications.
- Top threats in 2025 for SMBs include downloaders, Trojans, and adware, with attackers leveraging collaboration platform brands to deceive users.
- Phishing campaigns often target SMBs by impersonating trusted brands, such as Google and banks, to steal login credentials and money.
- Spam emails, Nigerian scams, and dubious deals are common tactics used against SMBs, with AI now infiltrating spam offers.
- Security tips for SMBs include investing in cybersecurity solutions, employee awareness training, and enforcing strict verification procedures.
- Actions like defining access rules, backing up data, establishing clear guidelines, and implementing specialized cybersecurity solutions are recommended for SMB cyber resilience.
Read Full Article
4 Likes
Securityaffairs
200

Image Credit: Securityaffairs
Disrupting the operations of cryptocurrency mining botnets
- Cybersecurity researchers devised two attack techniques to disrupt the operations of cryptocurrency mining botnets.
- Akamai Researchers uncovered two novel techniques to disrupt cryptocurrency mining botnets by exploiting flaws in common mining topologies.
- Current methods to stop cryptocurrency mining botnets are pool bans or infrastructure takedowns, however, both are slow and complex.
- Researchers developed two techniques exploiting vulnerabilities in the stratum protocol to disrupt operations by targeting proxies or wallets, potentially forcing attackers to abandon campaigns.
- XMRogue tool was developed to disrupt cryptomining botnets using mining proxies by submitting consecutive bad shares and potentially banning the mining proxy from the pool.
- Crafted invalid shares through Stratum to malicious proxies trigger pool-level bans, halting the attacker’s operation.
- In tests conducted by Akamai, one campaign's annual revenue was reduced from $50K to $12K, a 76% drop, by banning proxies.
- Akamai's second method targets miners connected directly to public pools without proxies by flooding the pool with over 1,000 login attempts using the attacker's wallet.
- The disruption can significantly hinder the attack, as the wallet gets temporarily banned for an hour.
- Researchers demonstrated the technique targeting Monero miners, which can be adapted to other cryptocurrencies.
- Defenders can disrupt malicious cryptominer campaigns by exploiting mining pool policies without affecting legitimate miners.
- Attacks targeting wallet addresses added an additional layer of disruption for cryptominers, making it challenging for attackers to monetize effectively.
- Implementing these attack techniques with XMRogue tool helps in disrupting attacker's operations effectively.
- The report concludes that the threat of cryptominers will continue to grow, but defenders now have tools to fight back and make it challenging for attackers to monetize effectively.
Read Full Article
12 Likes
VoIP
78

Image Credit: VoIP
Many UK SMEs Lack Cyber Training Despite Rising Threats
- A study by BT and Be the Business reveals that 39% of UK SMEs have not provided cybersecurity training to their employees, despite heightened cyber attack risks.
- 42% of small businesses and 67% of medium-sized companies have experienced cyber attacks in the last year.
- On average, micro and small businesses spend around £7,960 to recover from disruptive breaches.
- Phishing affects 85% of UK businesses, while ransomware incidents have doubled in the past year, impacting 1 in 100 businesses.
- Businesses with proactive cybersecurity strategies exhibit a 20% higher growth rate.
- BT launched a security training program for SMEs to combat cyber threats like those from AI and quantum computing, as well as account takeovers and QR code scams.
- Tris Morgan, MD for Security at BT, stresses the importance of cybersecurity for SMEs, stating it is crucial for business survival.
- Effective cybersecurity is achievable for SMEs with proper training, even without extensive resources.
- 18% of UK SMEs are concerned about AI-related threats, with 69% considering AI tools to mitigate cyber risks.
- Nearly half of business leaders seek cybersecurity advice from industry experts.
- The article discusses the lack of cyber training among UK SMEs despite the increasing cyber threats and the benefits of proactive cybersecurity measures.
- BT's security training initiative aims to equip SMEs with the knowledge to protect against evolving cyber threats.
- Phishing and ransomware are highlighted as prevalent threats impacting a significant number of businesses.
- Benefits of investing in cybersecurity include reduced risk exposure and potential for higher business growth.
- SMEs are encouraged to recognize cybersecurity as essential for long-term business success.
- Many UK SMEs are looking to AI tools and external expertise to enhance their cybersecurity measures.
Read Full Article
4 Likes
Securityaffairs
87
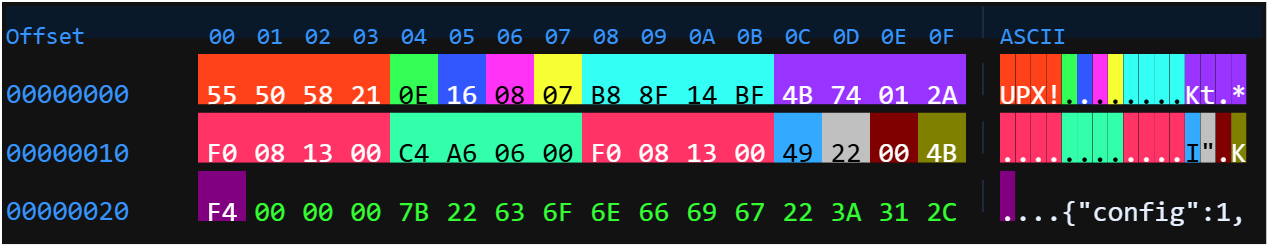
Image Credit: Securityaffairs
Prometei botnet activity has surged since March 2025
- Prometei botnet activity has surged since March 2025, with a new malware variant rapidly spreading, according to Palo Alto Networks.
- The botnet targets Linux systems for Monero mining and credential theft, using modular architecture and evasion tactics to avoid detection.
- Prometei allows attackers to control compromised systems for cryptocurrency mining and credential theft, with a focus on the Linux variant.
- First discovered in 2020, Prometei exploits vulnerabilities like EternalBlue and spreads through brute-force attacks.
- The malware primarily focuses on Monero mining and credential theft, displaying financial motivations without state ties.
- The latest Prometei variant is distributed via an HTTP GET request, utilizing UPX-packed Linux ELF files disguised as .php scripts.
- Prometei malware uses Ultimate Packer for eXecutables (UPX) for obfuscation, requiring analysts to strip a JSON config trailer for static analysis.
- Analyzing the configuration JSON reveals system information collected by the malware, including processor, motherboard, OS, uptime, and kernel details.
- Detection of the evolving Prometei botnet can be done with YARA rules targeting UPX and its configuration JSON trailer, but defenders must remain alert.
- The report provides Indicators of Compromise (IoCs) related to the Prometei botnet activity.
Read Full Article
5 Likes
Medium
413
Image Credit: Medium
What is the Dark Web and How to Keep Your Data Safe?
- The Dark Web serves various purposes, including privacy protection, avoiding tracking, and engaging in illegal activities.
- Accessing the Dark Web is not as simple as using regular search engines like Google or Bing; specialized tools like Tor are necessary, as it operates on unique network paths.
- Anonymity is crucial on the Dark Web, with most users avoiding real names or emails, making user tracing challenging due to hidden IP addresses.
- Illegal activities, such as the buying and selling of stolen data, hacking tools, and fake IDs, are common on the Dark Web, leading to various criminal acts being linked to its use.
- Hackers frequently steal login credentials from websites and then sell them on Dark Web platforms, including sensitive information like credit card details, passwords, and email accounts.
Read Full Article
24 Likes
TechCrunch
113

Image Credit: TechCrunch
Canada says telcos were breached in China-linked espionage hacks
- The Canadian government and the FBI report that telcos in Canada were targeted in cyber espionage attacks attributed to the China-backed hacking group Salt Typhoon.
- An unnamed Canadian telecom company was breached in mid-February this year, with hackers manipulating three Cisco routers for stealthy traffic collection.
- The hacking group Salt Typhoon's activities extend beyond telecommunications, having targeted U.S. phone and internet providers, and datacenter hosts previously.
- Salt Typhoon, active since late 2024, is engaged in a broad espionage campaign to gather intelligence on senior U.S. government officials.
- It is suspected that several China-linked hacking groups, including Salt Typhoon, are preparing for a potential Chinese invasion of Taiwan by 2027.
- A joint advisory by Canada and the FBI warns that the hackers are likely to continue targeting Canadian organizations for at least the next two years.
Read Full Article
6 Likes
Pymnts
53

Image Credit: Pymnts
AT&T’s Proposed Settlement of Data Breach Lawsuit Receives Preliminary Approval
- AT&T's proposed settlement of a class action lawsuit over data breaches received preliminary approval from a judge on Friday.
- The $177 million settlement was deemed fair and reasonable by the judge.
- The lawsuit stemmed from data breaches announced by AT&T in May 2024 and July, affecting tens of millions of customers.
- Under the settlement, affected customers may receive up to $2,500 or $5,000, with remaining funds distributed to others whose information was accessed.
- AT&T denied responsibility for the breaches but agreed to settle to avoid lengthy litigation.
- In a cybersecurity incident, records of calls and texts of almost all wireless customers were stolen, but no content or personal data was taken.
- The stolen data could potentially be used to associate telephone numbers with names through public tools.
- The breach was linked to an earlier incident involving cloud vendor Snowflake.
- In a separate settlement with the FCC, AT&T agreed to pay $13 million and enhance data governance following a 2023 hack.
- The settlement shows AT&T's efforts to address data breach issues and compensate affected customers.
Read Full Article
2 Likes
For uninterrupted reading, download the app