Cyber Crime News
Securityaffairs
101
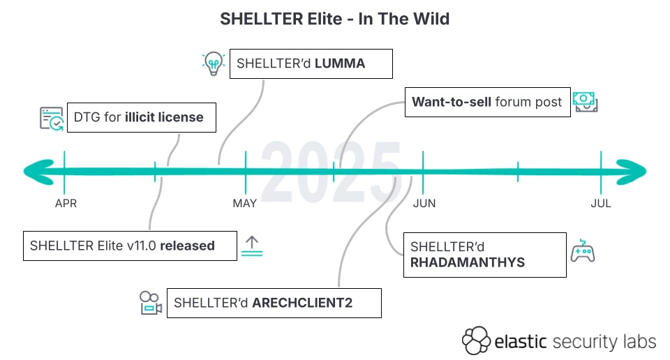
Image Credit: Securityaffairs
Hackers weaponize Shellter red teaming tool to spread infostealers
- Hackers exploit leaked Shellter Elite copy for infostealer attacks, bypassing security measures.
- Elastic Security Labs identifies malware campaigns using Shellter for evasion and malware deployment.
- Dynamic unpacker released by Elastic to detect and analyze SHELLTER-protected malware more effectively.
- Threat actors adopt Shellter for infostealer attacks, prompting efforts to counter abuse.
Read Full Article
6 Likes
Dynamicbusiness
57

Image Credit: Dynamicbusiness
What’s a cash-strapped business owner supposed to do about fraud these days?
- SMEs facing growing fraud threats struggle with limited budgets for robust security solutions.
- However, basic security practices like multi-factor authentication and staff training can offer protection.
- Managed detection and response services provide affordable security assistance without in-house teams.
- Prevention strategies include employee education, automation, and consolidating security efforts for cost-effective defense.
- Cyber fraud prevention calls for awareness, practical safeguards, and simple, smart steps to protect businesses.
Read Full Article
3 Likes
Siliconangle
60

Image Credit: Siliconangle
Report: Marco Rubio impersonator used AI to contact government officials
- A bad actor impersonated U.S. State Secretary Marco Rubio using AI to contact government officials, including a U.S. governor and foreign ministers.
- The impersonation campaign involved AI-generated voicemails and text messages to imitate Rubio, aiming to gain access to information or accounts of the officials.
- The State Department is urging diplomats to warn about impersonation attempts, while CNN reports a second impersonation campaign targeting government employees.
- Previous incidents include phishing campaigns targeting former government staffers and the hacking of a White House chief of staff's phone to impersonate officials.
Read Full Article
4 Likes
TechCrunch
427

Image Credit: TechCrunch
Marks & Spencer chair refuses to say if retailer paid hackers after ransomware attack
- Marks & Spencer chairman declined to disclose whether the company paid hackers following a ransomware attack earlier this year.
- Chairman Archie Norman mentioned that they are not discussing details of their interaction with the threat actor, citing law enforcement and public interest reasons.
- Norman stated that nobody at Marks & Spencer directly communicated with the ransomware group DragonForce, attributed to the attack.
- In May, Marks & Spencer reported a data breach with customer information stolen, leading to disrupted operations. Recovery efforts are expected to continue until October or November.
Read Full Article
24 Likes
Guardian
374
Image Credit: Guardian
M&S boss says two big UK firms hit by unreported cyber-attacks
- M&S boss suggests legally requiring UK firms to report major cyber-attacks.
- M&S suffered a cyber-attack that forced their online store to close for weeks.
- MPs were informed of unreported cyber-attacks on large British companies.
- M&S increased cybersecurity spending after facing a sophisticated hack.
Read Full Article
21 Likes
Securityaffairs
316

Image Credit: Securityaffairs
IT Worker arrested for selling access in $100M PIX cyber heist
- Brazilian police arrested IT worker João Roque for allegedly aiding a cyberattack that stole over $100 million through the PIX banking system.
- Roque is accused of selling system access and developing a tool for fund diversion, claiming he only communicated with criminals via phone and changed devices frequently to avoid detection.
- The cyberattack targeted multiple financial institutions, leading to at least six being impacted, resulting in the market being shaken.
- Authorities have frozen $270 million, suspended part of C&M's operations to prevent further attacks, and confirmed the company's systems were not the source of the breach.
Read Full Article
18 Likes
Securityaffairs
152
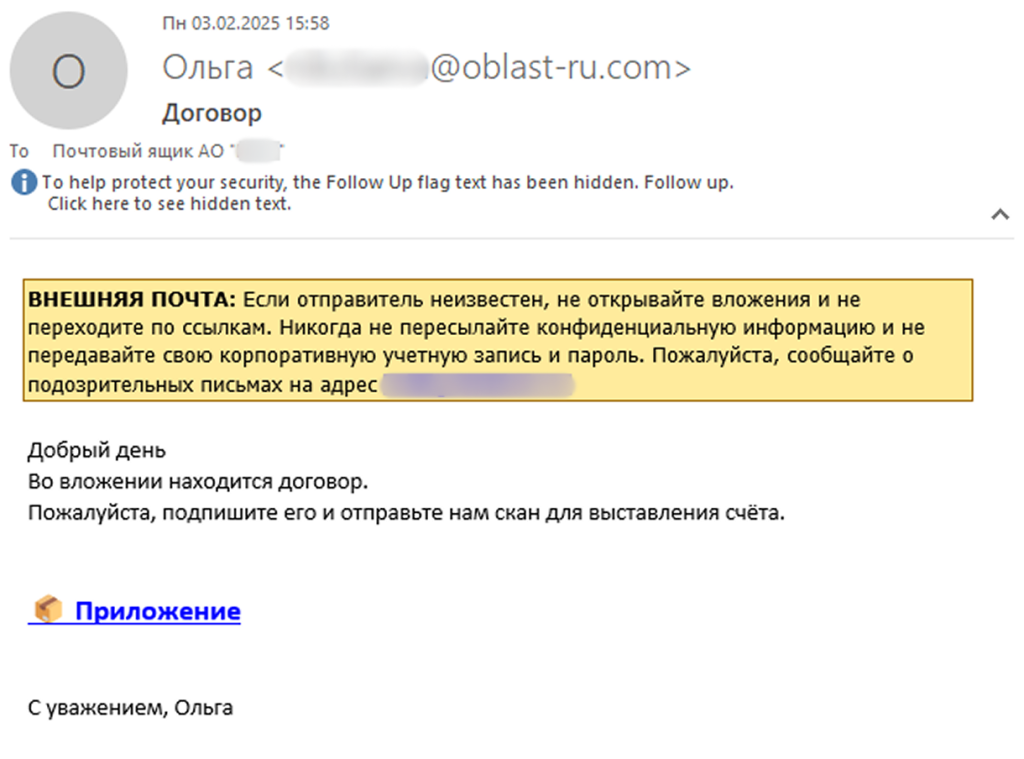
Image Credit: Securityaffairs
New Batavia spyware targets Russian industrial enterprises
- A new spyware named Batavia is being spread through fake contract-themed emails targeting Russian organizations since March 2025.
- The spyware includes a VBA script and two executables, detected by Kaspersky as Trojan.Batavia variants, designed to steal internal documents.
- The attack involves multiple stages where the malware collects system info, spies on the system by capturing screenshots and exfiltrating data to a command-and-control server.
- The victims of the Batavia spyware campaign are Russian industrial enterprises, with over 100 users across multiple organizations falling prey to the phishing messages.
Read Full Article
9 Likes
Ars Technica
256

Image Credit: Ars Technica
“No honor among thieves”: M&S hacking group starts turf war
- A ransomware group responsible for recent cyberattacks on UK retailers has entered a turf war with a competitor, leading to potential fallout for corporate victims.
- The conflict between DragonForce and RansomHub in the ransomware-as-a-service market may increase risks for companies, including the possibility of being extorted twice.
- The rivalry escalated after DragonForce rebranded itself as a 'cartel,' widening its services and attracting more affiliate partners, causing friction with RansomHub.
- Experts warn that the conflict between these hacking groups could lead to increased cyberattacks and double extortion of victims, highlighting the lawless and volatile nature of the cybercrime landscape.
Read Full Article
15 Likes
TechCrunch
447

Image Credit: TechCrunch
Ingram Micro says ongoing outage caused by ransomware attack
- Ingram Micro, a U.S. technology distributing giant and managed services provider, confirms that a ransomware attack caused an ongoing outage at the company.
- The hack started on Thursday, leading to the company's website and network going down, impacting its ability to process orders.
- The outage at Ingram Micro is affecting software licensing, hindering customers from using or provisioning certain products reliant on the company's systems.
- Although no specific ransomware group has claimed responsibility, reports suggest the SafePay ransomware gang may be behind the attack, aiming to extort victims into paying ransoms.
Read Full Article
15 Likes
Silicon
149
Image Credit: Silicon
Hackers Steal Data From Louis Vuitton Korea
- Hackers compromised Louis Vuitton Korea's IT systems in June, accessing some data, including customer information.
- No financial data such as payment card or bank account details were included in the breach, and the incident has been contained.
- Louis Vuitton Korea is investigating the attack, has notified authorities, and is enhancing system security along with working with third-party experts.
- Considering recent breaches affecting luxury brands like Louis Vuitton and airlines like Qantas, cybersecurity threats continue to evolve, with hackers targeting sensitive data for ransom purposes.
Read Full Article
8 Likes
TechBullion
111

Image Credit: TechBullion
Massive Global Crypto Fraud Network Dismantled in Spain, Over 5,000 Victims Targeted
- Spanish authorities, with international support, dismantled a global cryptocurrency fraud network in Spain, targeting over 5,000 victims through fake crypto investment deals and laundering over €460 million.
- Criminals used fake identities, shell companies, and accomplices to carry out the fraudulent activities, making it challenging for authorities to trace the funds and deceive victims into transferring money unknowingly.
- The arrests were part of a coordinated operation involving Europol, leading to the apprehension of five individuals suspected of laundering more than $540 million in June 2025.
- The rise of cryptocurrency scams poses a significant threat to investors worldwide, necessitating increased vigilance and awareness to protect against fraudulent schemes in the evolving crypto landscape.
Read Full Article
6 Likes
Medium
133

Cyber Security & Individual Privacy
- Introduction of Unified Payment Interface (UPI) has reduced the need for cash transfers in India, but cyber traps pose a significant threat.
- Senior citizens, particularly pensioners, and women are vulnerable to cybercrimes through malicious links, harassment on social media, and online dating scams.
- Hindering equitable access to online resources, like misusing Tatkal ticket booking schemes, is considered a cybercrime in India.
- Responsible usage of online platforms, awareness campaigns, prompt cyber complaint filing, and structural overhaul in cyberspace, like implementing blockchain technology, are crucial to tackling evolving cyber threats.
Read Full Article
7 Likes
Dev
41

Image Credit: Dev
The Scariest Threat in Cybersecurity? It Might Be the Person Sitting Next to You
- Insider threats, originating from within an organization, are a significant cybersecurity risk often underestimated.
- These threats come from intentional insiders seeking to harm or unintentional insiders causing vulnerabilities.
- Insider threats are dangerous as access is already granted, harder to detect, and can lead to catastrophic damage.
- Real-world examples like Edward Snowden and incidents at Tesla and Capital One highlight the severity of insider threats.
Read Full Article
2 Likes
Pymnts
407

Image Credit: Pymnts
Scammers Impersonate Trump Inaugural Committee to Steal Crypto
- Scammers posed as the presidential inaugural committee to steal over $250,000 in cryptocurrency by using phony email addresses similar to the committee's official ones.
- The scammers tricked victims into sending money by creating fake email addresses with subtle differences to deceive them into contributing to the Trump-Vance Inaugural Committee.
- Authorities aim to seize around $40,400 in cryptocurrency to deter criminal activity and compensate victims affected by the scam.
- The incident comes amidst warnings from the FATF about the potential risks associated with the growing use of stablecoins by illicit actors, highlighting the need for stricter regulations in the virtual asset space.
Read Full Article
24 Likes
Pymnts
235

Image Credit: Pymnts
Brand Impersonation Scams Surge as Hackers Prey on Public Trust
- Hackers are impersonating brands like PayPal and Apple to steal information and distribute malware, as per Cisco Talos' research.
- Phishing scams involve victims calling scammers who pretend to be representatives and aim to extract confidential details or install malware.
- A surge in brand impersonation attacks includes a tactic known as callback phishing, tricking individuals into disclosing sensitive data.
- Increased focus on secure digital identities is emphasized due to the potential risks brought on by advances in artificial intelligence, says Cerby CEO Belsasar Lepe.
Read Full Article
14 Likes
For uninterrupted reading, download the app