Cyber Crime News
Guardian
85
Image Credit: Guardian
M&S fashion rivals ‘benefited from its pause on online orders after cyber-attack’
- Marks & Spencer (M&S) paused online orders for almost seven weeks after a cyber-attack, benefiting rivals like Zara and H&M.
- M&S experienced a 20% drop in clothing sales compared to the previous year during the downtime period.
- The halt in online orders occurred from April 25 to June 10, missing out on crucial sales during a warmer season.
- Despite the cyber-attack affecting online sales, M&S stores performed well, especially in womenswear.
- M&S maintained its position as the largest UK clothing retailer by value despite the sales decline.
- Sales growth for M&S declined to 1% in the later period from 11.5% prior to the cyber-attack.
- Rivals like Next saw an increase in sales growth, benefitting from M&S's digital disruption.
- Zara and H&M experienced significant growth in sales, aided by their online presence.
- Zara's sales growth rose to 27.8%, while H&M's sales growth increased to 18.1%.
- Primark did not benefit from M&S's online pause, with sales growth falling to +2.7%.
- The news highlights the impact of cyber-attacks on businesses and the importance of online sales channels in the retail sector.
Read Full Article
3 Likes
TechCrunch
78

Image Credit: TechCrunch
US insurance giant Aflac says customers’ personal data stolen during cyberattack
- Aflac, a major insurance company in the U.S., reported a recent cyberattack where hackers stole customers' personal data.
- The breach occurred on June 12, with the company confirming the intrusion and containing it.
- The stolen personal information includes customers' claims, Social Security numbers, and health data.
- The breach also impacted data of Aflac's beneficiaries, employees, and agents.
- Aflac stated that ransomware was not involved in the attack but attributed it to a cybercrime group targeting the insurance sector.
- The hackers used social engineering tactics to gain access to Aflac's network.
- Despite having around 50 million customers, it is unclear how many are affected by the breach.
- Aflac is not the only U.S. insurance company facing cyberattacks, with warnings of increased targeting in the industry.
- Recent disclosures indicate cyberattacks on companies like Erie Insurance and Philadelphia Insurance Companies by the same hacker group.
- The hackers linked to these attacks are known for financial motivations and have a history of intrusions in various sectors.
Read Full Article
4 Likes
Securityaffairs
13

Image Credit: Securityaffairs
McLaren Health Care data breach impacted over 743,000 people
- McLaren Health Care experienced a ransomware attack in 2024, exposing personal data of 743,000 individuals.
- The nonprofit health care organization operates in Michigan and discovered the breach on August 5, 2024.
- Names, Social Security numbers, driver's license numbers, health insurance details, and medical information were compromised.
- McLaren is providing affected individuals with 12 months of free credit monitoring services.
- In a previous incident in November 2023, McLaren disclosed a breach affecting 2,192,515 individuals.
- The attackers in the latest breach remain unidentified, and the company did not disclose technical details.
Read Full Article
Like
Securityaffairs
288

Image Credit: Securityaffairs
American steel giant Nucor confirms data breach in May attack
- American steel giant Nucor confirms data breach in May cyberattack.
- Nucor, North America's largest steel maker, disclosed unauthorized access to certain IT systems.
- The company activated its incident response plan and involved law enforcement and cybersecurity experts.
- Limited data was stolen from Nucor's systems during the cyberattack.
- Operations and IT systems have been restored, and the threat actor no longer has access.
- Nucor confirmed no material business or financial impact from the incident.
- The nature of the attack was not specified in the notifications.
- Experts suggest Nucor may have been a victim of a ransomware attack.
- No group has claimed responsibility for the cyberattack on Nucor.
- The incident is being monitored for any further developments.
- Nucor is reviewing and evaluating the impacted data for potential notifications.
- The company is committed to complying with regulatory requirements following the cyber incident.
- Nucor believes it has addressed the cybersecurity incident and restored normal operations.
- The cybersecurity incident did not have a significant impact on Nucor's business or finances.
- Nucor continues to assess its cybersecurity measures to prevent future incidents.
Read Full Article
17 Likes
Schneier
126

Largest DDoS Attack to Date
- A recent unprecedented DDoS attack reached 7.3 Tbps.
- The attack mainly utilized User Datagram Protocol packets.
- UDP is commonly used for time-sensitive communications like gaming and video playback.
- UDP speeds up communication by not requiring a formal connection setup before data transfer.
- Unlike TCP, UDP does not establish a connection through a handshake or ensure proper data reception.
- In UDP flood attacks, high volumes of packets flood random or specific ports on the target IP.
- These floods can overwhelm the target's Internet link or internal resources with excessive packets.
- Attackers can flood servers using UDP without obtaining permission, causing strain on the target system.
- UDP floods often send numerous datagrams to multiple ports on the target system.
- The targeted system must respond with an equal number of data packets, leading to strain and denial of legitimate traffic.
Read Full Article
7 Likes
Securityaffairs
2.4k
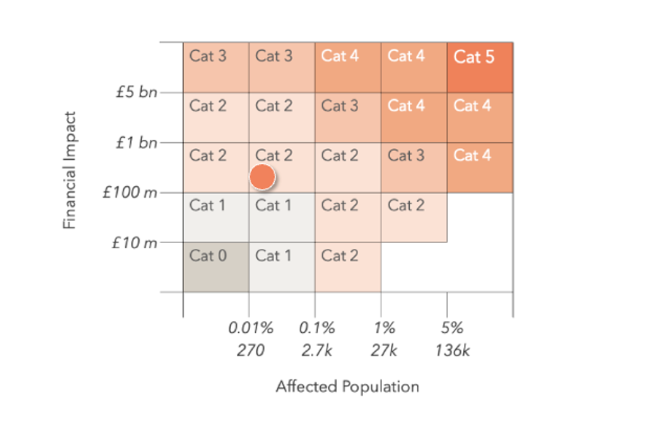
Image Credit: Securityaffairs
The financial impact of Marks & Spencer and Co-op cyberattacks could reach £440M
- The Cyber Monitoring Centre (CMC) has categorized cyberattacks on Marks & Spencer and Co-op as a Category 2 event, with estimated financial losses between £270M and £440M.
- Hackers named DragonForce claimed responsibility for the Co-op attack, accessing data of current and past members.
- Co-op initially denied customer data compromise but later confirmed data breach.
- DragonForce also targeted M&S and confessed to trying to hack Harrods, accessing staff and customer data.
- The attack exposed personal details of Co-op members but did not include sensitive information like passwords or financial data.
- DragonForce is known for ransomware attacks, data theft, and running a cybercrime affiliate service.
- The CMC linked M&S and Co-op attacks due to shared timing and threat actor, estimating total financial impact at £270M–£440M.
- The attacks caused major business disruption and financial consequences for M&S and Co-op.
- Estimated costs include legal fees, business interruption, incident response, and IT restoration for both companies.
- M&S anticipates a £300M impact, with significant declines in online sales and consumer spending.
- The incidents emphasized the vulnerability of retail supply chains and the importance of crisis preparedness and cyber resilience.
- CMC stresses the need for stress-testing crisis plans, financial resilience, enhanced cyber hygiene, and access control improvement.
- Clear crisis communication and robust recovery capabilities are essential during cyber incidents.
- CMC aims to enhance cyber readiness through collaboration and transparency.
- The financial impact of the M&S and Co-op cyberattacks highlights the widespread repercussions of cyber incidents in the retail sector.
Read Full Article
1 Like
Securityaffairs
314
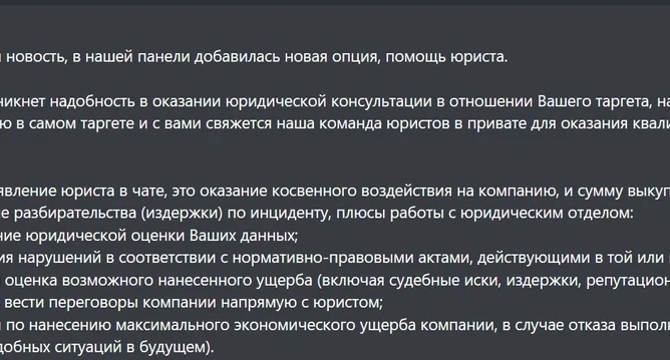
Image Credit: Securityaffairs
Qilin ransomware gang now offers a “Call Lawyer” feature to pressure victims
- The Qilin ransomware group now offers a "Call Lawyer" feature to provide legal support to affiliates and pressure victims into paying, as reported by cybersecurity firm Cybereason.
- Qilin, active since at least August 2022 and gaining attention in June 2024 for attacking a UK governmental service provider, uses double extortion tactics and takes a percentage of ransom payments.
- Affiliates are ordered not to target systems in CIS countries like other ransomware operations.
- Qilin is positioning itself as a full-service cybercrime platform, offering advanced tools, legal support, spam services, and large data storage.
- The "Call Lawyer" feature increases pressure on victims during ransom negotiations by offering legal consultations and introducing legal risks.
- By introducing network spreading and a DDoS option, Qilin demonstrates sophistication and adaptability in various cyberattack scenarios.
- A translation of the ransomware group's text explains how the "Call Lawyer" feature works to increase ransom amounts and apply legal pressure on companies.
- Qualys also highlights the strong operational model and legal support provided by Qilin to clients for successful ransomware payouts.
- The Qilin ransomware group is intensifying its activity, as shown by a heatmap reporting host compromises.
- Organizations are advised to adopt proactive measures to defend against sophisticated threats like Qilin ransomware, as per Qualys' recommendations.
- Qilin ransomware group's strategy includes legal support, incentives, and technology for successful ransom payouts.
- Cybereason's report emphasizes Qilin's emergence as a major ransomware player, offering more than just malware and aiming to lead the next wave of ransomware-as-a-service operations.
Read Full Article
18 Likes
Gizchina
21

Image Credit: Gizchina
Urgent Warning: 16 Billion Passwords Leaked: How to Stay Safe
- A significant leak of 16 billion passwords raises concerns about online security and highlights the dangers of password reuse.
- The leaked data is a compilation from various sources and poses a serious threat as cybercriminals can exploit it.
- The risk primarily stems from 'credential stuffing,' where reused passwords grant unauthorized access to multiple accounts.
- Individuals are urged to assess their exposure using tools like 'Have I Been Pwned' and adopt strong, unique, and lengthy passwords.
- Implementing a password manager is recommended to handle multiple complex passwords effectively.
- Enabling Two-Factor Authentication (2FA) provides an additional layer of security against unauthorized access.
- Future security measures like Passkeys, utilizing biometrics, are emerging as a more secure alternative to traditional passwords.
- Despite the alarming nature of password leaks, proactive steps such as these can significantly enhance digital defense.
- Read Gizchina.com for the latest technology news and updates.
- The article focuses on the impact of a massive password leak and offers practical steps to bolster online security.
Read Full Article
1 Like
Blackenterprise
210

Image Credit: Blackenterprise
Time To Change Those Passwords After Largest Data Breach In History
- Cybernews researchers discovered the largest compilation breach of leaked login data in history, with 16 billion records from 30 unsecured data sets.
- The breached data includes passwords for popular services like Google, Facebook, Apple, and more.
- The leaked data did not originate from a central breach but was compiled from various incidents by malicious software called 'infostealers'.
- The true number of affected individuals remains unclear due to potential duplicates, with the number of records exceeding the world's population.
- Experts warn that the breach provides a blueprint for mass exploitation through phishing, identity theft, and account takeovers.
- The exposure appears recent and poses a significant threat as the data was collected from recent incidents.
- Researchers secured the data after finding it briefly accessible online through unprotected cloud storage.
- Users are advised to take immediate protective measures such as changing passwords, enabling two-factor authentication, and using password managers.
- Google suggests using passkeys and non-password login methods to enhance security.
- Services like Apple, Facebook, and Google's password managers can alert users if their credentials are involved in known data breaches.
Read Full Article
12 Likes
Guardian
206
Image Credit: Guardian
Internet users advised to change passwords after 16bn logins exposed
- Internet users are advised to change passwords and enhance digital security after 16 billion login records were exposed by researchers.
- Research by Cybernews revealed 30 datasets containing credentials from 'infostealers' and leaks, potentially exposing login details for services like Facebook, Apple, and Google.
- There was no centralized data breach at the companies mentioned, with the exposed data being briefly available due to poor storage on remote servers.
- Cybersecurity specialist Bob Diachenko discovered and downloaded the files and plans to notify affected individuals and companies.
- Google stated that the reported data did not result from a Google breach, recommending people to use tools like Google’s password manager for protection.
- Internet users can check if their email was compromised using haveibeenpwned.com, with the leaked datasets following a clear structure of URL, login details, and passwords.
- The data mainly consisted of infostealers and a small portion from previous breaches like LinkedIn, emphasizing the importance of regular password updates and strong security measures.
- Experts advise implementing multifactor authentication and password managers to mitigate credential issues from data leaks.
- The exposed data highlights the vast amount accessible to cybercriminals, prompting proactive security steps for individuals and organizations.
- Infostealers are real threats that scrape information like browser cookies and metadata, but following cybersecurity best practices can help mitigate risks.
- The datasets, described as blueprints for mass exploitation, present risks like identity theft and phishing, emphasizing the need for stringent security measures.
- Experts recommend updating passwords regularly and adopting zero trust security measures to combat increasing data breaches.
Read Full Article
12 Likes
Pymnts
404

Image Credit: Pymnts
Data Breach Exposes 16 Billion Login Records for Online Services
- Thirty databases containing 16 billion login records for various online services were briefly exposed.
- The data is recent and may include overlapping information, with only one dataset previously reported.
- Login records for social media, corporate platforms, VPNs, developer portals, and more were included with URLs, login details, and passwords.
- The data breach was most likely caused by infostealers, a type of malware that steals sensitive information.
- The Cybernews researchers warned that this data breach provides cybercriminals with credentials for account takeover and identity theft.
- Protective measures suggested include using password generators, updating passwords frequently, enabling two-factor authentication, and monitoring accounts.
- Old and recent infostealer logs included in the data make it dangerous for organizations lacking multi-factor authentication practices.
- In today's digital ecosystem, businesses need a holistic approach to cybersecurity due to increasing data breaches through various entry points.
- Protecting data now necessitates a collective effort among businesses, service providers, and vendors.
- Reported cyber and scam-related losses reached $16.6 billion in 2024, a 33% increase from the previous year, according to the FBI's IC3.
- The news was reported by Cybernews and highlighted by PYMNTS.
Read Full Article
24 Likes
Alvinashcraft
175

Dew Drop – June 20, 2025 (#4444)
- 16 billion passwords exposed in record-breaking data breach, opening access to Facebook, Google, Apple, and any other service imaginable (Vilius Petkauskas & Jurgita Lapienytė)
- Announcing Warp Preview (Hong Yi Chen)
- GIF export in Snipping Tool begins rolling out to Windows Insiders (Dave Grochocki)
- Copilot Compared: Advanced AI Features in Visual Studio 2022 vs. VS Code (David Ramel)
- Fine-Tuning LLMs with C#: A Practical Guide to Customizing Models with ML.NET and Introduction to Semantic Kernel: The .NET Developer’s Guide to Building Powerful AI Agents (Sudhir Mangla)
- Best practices for administering GitHub Copilot with Luis Pujols | Beyond the Commit (GitHub Team)
- Mastering iOS Development: Your Essential Resource List (Coder)
- Strengthen mobile device security with Edge for Business, the secure enterprise browser (Patrick Brosset)
- SQL Server 2025: Secure by Default | Data Exposed (Anna Hoffman, Pratim Dasgupta & Pieter Vanhove)
- freeCodeCamp Podcast #176 – From Therapist to six figure freelance dev (Beau Carnes)
Read Full Article
10 Likes
Digit
114

Image Credit: Digit
How to find out if your passwords were compromised in the global data breach
- Researchers have confirmed a massive data breach with up to 16 billion login credentials compromised, potentially by malware.
- The leaked credentials cover various online services like social media, VPN services, and government portals.
- Tech giants like Google, Microsoft, and Meta are pushing users to switch to passkeys due to the breach.
- 16 billion leaked credentials increase the risks of identity theft, account hacking, and financial fraud.
- Users can check if their data was leaked using tools like Have I Been Pwned, Google Password Checkup, F-Secure Identity Theft Checker, Mozilla Monitor, and Microsoft Edge Password Monitor.
- If an account is affected, users should change passwords immediately, log out of all devices, use unique strong passwords, and enable two-factor authentication.
- Saving login credentials in a password manager can help manage multiple passwords securely.
- Checking for compromised passwords and monitoring potential breaches are essential to protect online accounts.
Read Full Article
6 Likes
Hackernoon
268
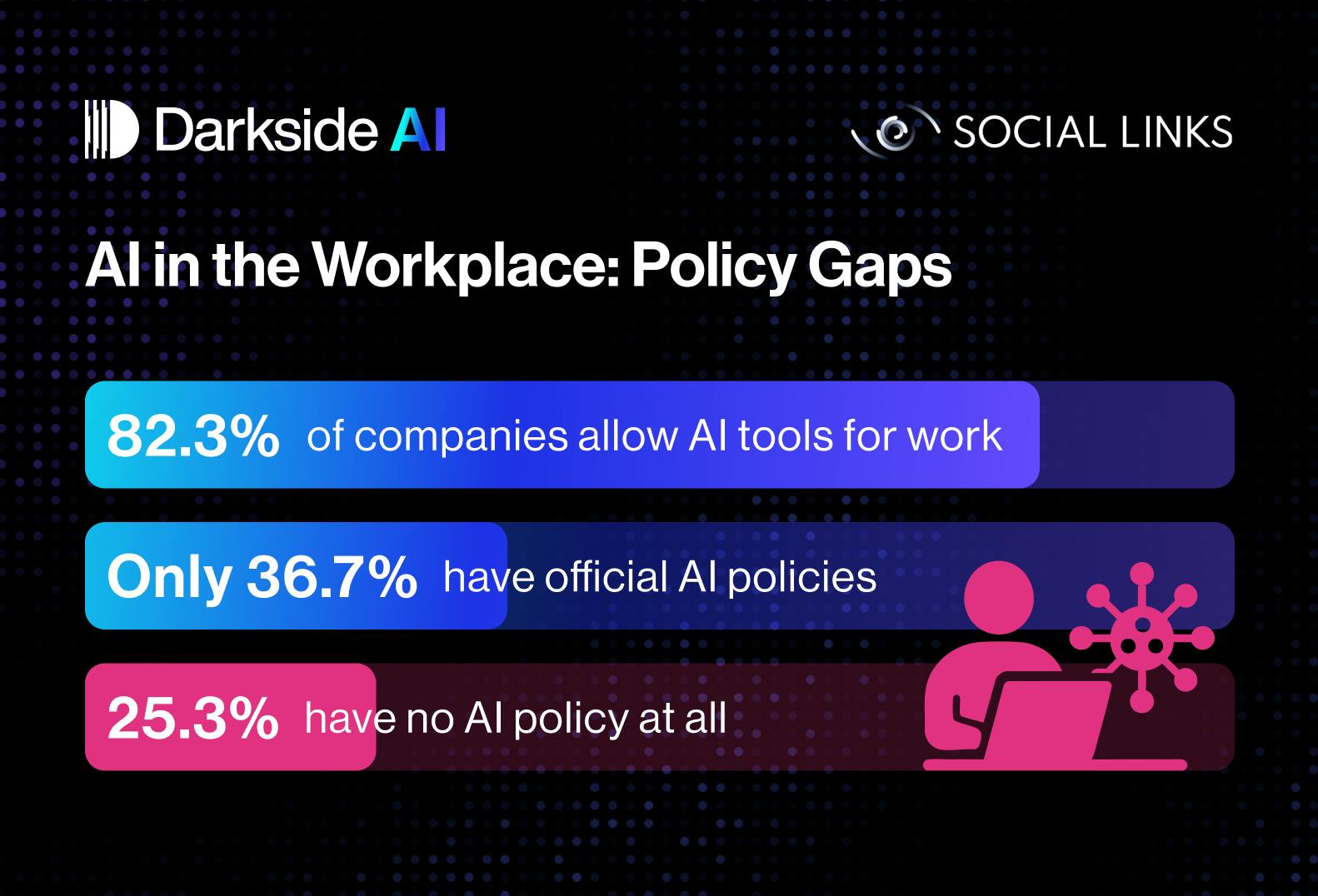
Image Credit: Hackernoon
Business Pros Underestimate AI Risks Compared to Tech Teams, Social Links Study Shows
- A study by Social Links shows a discrepancy between business and technical professionals in recognizing AI risks in cyberattacks.
- Only 27.8% of business professionals see AI-generated fake messages as a top cyber threat, compared to 53.3% of technical experts.
- This gap exposes a vulnerability as business roles are prime targets for AI-driven social engineering and deepfake schemes.
- Finance, IT, HR, and Sales departments are identified as the most vulnerable to cyber threats.
- AI-driven threats such as fake messages and deepfakes are gaining traction alongside traditional risks like phishing and malware.
- Over 60% of employees use corporate accounts for personal purposes, posing a risk for cyber incidents.
- While over 82% of companies allow employees to use AI tools, only 36.7% have a formal policy regulating their use.
- Social Links emphasizes the need for a holistic approach to cybersecurity in the AI era, including human-centric security programs.
- Effective mitigation measures include employee training on safe AI use and the development of internal policies.
- Social Links recently launched the Darkside AI initiative to address risks posed by advanced AI-driven threats.
- Social Links is a global provider of open-source intelligence solutions, supporting various sectors across 80+ countries.
Read Full Article
16 Likes
Securityaffairs
109

Image Credit: Securityaffairs
A ransomware attack pushed the German napkin firm Fasana into insolvency
- A ransomware attack has pushed the German napkin firm Fasana into insolvency, exacerbating its financial troubles.
- The cyberattack occurred on May 19, shutting down Fasana's systems and causing a halt in orders worth over €250K the next day.
- Fasana, located in Stotzheim, Germany, with 240 employees, had to cease production and postpone May salaries.
- The company estimates a €2 million loss within two weeks of the cyberattack and is now seeking a new buyer after being acquired in March.
- The attack rendered Fasana incapable of printing delivery notes, leading to a complete paralysis of business operations.
- The insolvency administrator Maike Krebber highlighted the severe consequences of the cyberattack on Fasana and its employees.
- The ransomware attack by an unidentified group encrypted files and locked Fasana's systems, but no gang has claimed responsibility.
- Although the hackers sought financial gain, the exact method of their entry remains unclear.
- Operations have resumed, and deliveries and invoicing restarted the prior week.
- Reportedly, a known police-monitored group was involved in sending ransomware to Fasana's systems.
- The malware circulated rapidly, locking data until a ransom was paid, with printers displaying extortion messages during the attack.
- No ransomware group has officially admitted to the cyberattack as of now.
- Fasana is under pressure to find a buyer within eight weeks as it looks to recover from the insolvency caused by the ransomware attack.
Read Full Article
6 Likes
For uninterrupted reading, download the app