Cyber Security News
Securityaffairs
13

Image Credit: Securityaffairs
McLaren Health Care data breach impacted over 743,000 people
- McLaren Health Care experienced a ransomware attack in 2024, exposing personal data of 743,000 individuals.
- The nonprofit health care organization operates in Michigan and discovered the breach on August 5, 2024.
- Names, Social Security numbers, driver's license numbers, health insurance details, and medical information were compromised.
- McLaren is providing affected individuals with 12 months of free credit monitoring services.
- In a previous incident in November 2023, McLaren disclosed a breach affecting 2,192,515 individuals.
- The attackers in the latest breach remain unidentified, and the company did not disclose technical details.
Read Full Article
Like
Global Fintech Series
103

Image Credit: Global Fintech Series
Ushur Launches Ushur Intelligence: Agentic AI Purpose-built for Highly Regulated Enterprises
- Ushur launched Ushur Intelligence, AI Agent solutions for highly regulated industries like healthcare, insurance, and financial services.
- Ushur Intelligence enables automation of complex workflows with enterprise-grade security and compliance.
- Enterprises face pressure to achieve more with fewer resources, driving the need for intelligent automation.
- Agentic AI by Ushur enables autonomous reasoning, decision-making, and adaptive actions in real-time.
- Ushur Intelligence deploys domain-specific AI Agents while ensuring transparency, trust, and control.
- Key capabilities include domain-specific AI Agents, multi-agent orchestration, seamless integration, compliance frameworks, real-time reasoning, and more.
- Ushur's AI solutions are designed to address urgent challenges in regulated industries with prebuilt, customizable options.
- Ushur's AI Agent solutions improve customer service and employee productivity in regulated industries.
Read Full Article
6 Likes
Tech Radar
291

Image Credit: Tech Radar
Russian hackers target Gmail passwords to crack down on international critics
- Phishing emails targeting international critics of Russia and academics have been reported.
- Russian state-sponsored group UNC6293 using social engineering tactics to target victims.
- Victims receive phishing emails with '@state.gov' addresses to build rapport.
- Attackers aim to gain victims' trust before exploiting them.
- Prominent figures like Keir Giles have been targeted in the phishing campaign.
- Victims are led to share Google app-specific passwords (ASPs) with attackers.
- ASP passcodes allow access to a user's Google Account.
- Google advises against the unnecessary use of ASPs and recommends caution.
- Social engineering and phishing tactics are highlighted as effective yet detectable.
- Users are urged to avoid clicking on unfamiliar email attachments and sharing account credentials.
- Phishing scams continue to pose cybersecurity risks.
Read Full Article
17 Likes
Siliconangle
4

Image Credit: Siliconangle
Okta debuts Cross App Access to secure AI agent interactions
- Identity access management company Okta Inc. has introduced Cross App Access, a new protocol to secure AI agents for visibility, control, and governance in interactions.
- Cross App Access aims to help software vendors provide secure integrations in the AI-powered environment by eliminating repetitive user consents and enhancing access control through the identity provider.
- The protocol addresses the complexity and risk posed by autonomous AI agents that interact with enterprise apps using the Model Context Protocol autonomously.
- It centralizes policy-based governance for AI-driven integrations, offering real-time visibility into agent access while reducing token sprawl and improving compliance.
- By enabling smoother user experiences, Cross App Access streamlines authorization processes, manages agent access securely, and enhances compliance.
- Okta's example showcases how AI tools can seamlessly access internal apps through Okta's evaluation of requests, leading to improved security and efficiency.
- This new offering positions Okta as a key player in shaping identity and access management in automated and interconnected environments amid growing enterprise adoption of AI tools.
Read Full Article
Like
Mcafee
34

Image Credit: Mcafee
16 Billion Stolen Logins for Apple, Google, Facebook and More: How to Stay Safe
- A massive compilation of 16 billion stolen login credentials, including data from major platforms, has been exposed in one of the largest data breaches in history.
- The leak involves credentials acquired from malware-infected devices and past data breaches, emphasizing the critical need for robust online security measures.
- Potential consequences of stolen credentials include social media hijacking, identity theft, phishing attacks, and financial loss.
- Steps to enhance security include checking for malware infections, updating critical passwords, enabling two-factor authentication, and utilizing scam detection technology.
- The ongoing threat of infostealer infections on unprotected devices underscores the importance of proactive cybersecurity measures.
- McAfee recommends continuously monitoring for personal data breaches, enabling two-factor authentication, and employing professional-grade identity protection services.
- The article highlights the need for a proactive security approach to safeguard against the increasing trend of large-scale credential dumps and infostealer attacks.
- Long-term protection strategies include assuming data compromise, using unique passwords, enabling 2FA, monitoring automatically, and responding swiftly to potential breaches.
- Building defense in depth involves securing devices, network, enabling identity monitoring, credit monitoring, and taking immediate action to improve cybersecurity posture.
- McAfee Identity Monitoring offers dark web alerts and comprehensive protection services to mitigate risks associated with data breaches and identity theft.
- The article from McAfee stresses the urgency of updating passwords, enhancing cybersecurity practices, and staying vigilant against the evolving threats in the digital landscape.
Read Full Article
2 Likes
Medium
47
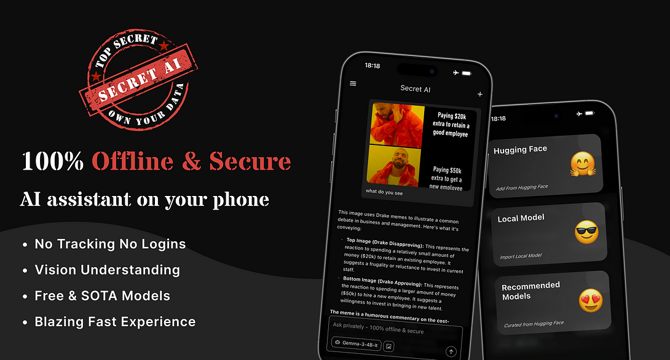
Image Credit: Medium
Introducing Secret AI: 100% Private & Local AI on Phone
- Introducing Secret AI, a private AI assistant that operates entirely offline on mobile devices without data collection for complete privacy.
- Secret AI offers impressive performance with support for CPU and GPU acceleration using popular model formats like GGUF and MNN.
- It provides access to cutting-edge open-source models from Hugging Face without any intermediary or markups.
- Users can upload photos for AI analysis with on-device computer vision capabilities, ensuring secure visual understanding.
- It features a custom API engine for connecting to self-hosted LLM API services through the internal network for enhanced capabilities while maintaining privacy.
- Secret AI promotes digital freedom by allowing discussions on sensitive topics, brainstorming business ideas, engaging in creative projects, learning, and researching without privacy concerns.
- The AI assistant is now available on the iOS App Store and Google Play Store, offering basic features for free and premium capabilities through one-time purchases or subscriptions.
- Users can experience the shift of AI power from cloud-based services to local devices, ensuring offline, private, and personal assistance.
- Secret AI emphasizes the importance of privacy, local processing, and challenges the notion that sacrificing digital privacy is necessary for AI assistance.
- It aims to keep users' secrets secure while providing AI-powered assistance for various needs without compromising privacy.
- Secret AI empowers users to explore, create, and interact with AI technology without concerns about data collection or privacy breaches.
Read Full Article
2 Likes
IEEE Spectrum
113

Image Credit: IEEE Spectrum
Transforming Physical Substation Security
- Digital transformation is reshaping the power delivery sector as utilities leverage digital tools for operational optimization and enhanced resilience.
- Despite the potential benefits, the industry faces challenges with legacy security protocols and slow technology adoption.
- Meerkat offers a solution for substation security, combining high-fidelity data and 3D modeling to identify vulnerabilities.
- Physical attacks on substations are on the rise, necessitating comprehensive threat assessments and adaptability to new threats.
- Conventional site analysis methods are often inefficient and subjective, leading to incomplete assessments.
- Meerkat by POWER Engineers enhances threat assessment accuracy, reduces assessment times, and improves protection at substations.
- The VISA method and lack of analysis present limitations in current security assessment approaches.
- Emerging technologies like real-time data analytics enhance security assessments and enable proactive measures.
- Meerkat revolutionizes physical substation security with advanced modeling, remote sensing capabilities, and stakeholder collaboration.
- By improving efficiency, accuracy, and decision-making processes, Meerkat facilitates proactive risk management and tailored security measures.
Read Full Article
6 Likes
Medium
105

Image Credit: Medium
Securing Our Energy Infrastructure: Cyber in the Era of Green Molecules®
- Cybersecurity is foundational for the clean energy system, protecting digital systems of low-carbon fuels.
- OT merging with IT increases sector efficiency but also risks of cyber threats.
- The energy sector faces rising ransomware attacks and breaches impacting reliability and decarbonization.
- Operational technology convergence with information technology expands vulnerabilities.
- Quantum computing poses challenges to energy infrastructure security.
- NIST releases post-quantum cryptography standards and investments in cyber defense.
- Resilient infrastructure design is crucial for future digital and quantum threats.
- Innovations like Bohr Quantum embed physics-based protections into grid networks.
- Cybersecurity shift towards modular deployments for clean energy systems.
- Regulatory standards promote cyber readiness and unlock capital for secure systems.
Read Full Article
6 Likes
Securityaffairs
287

Image Credit: Securityaffairs
American steel giant Nucor confirms data breach in May attack
- American steel giant Nucor confirms data breach in May cyberattack.
- Nucor, North America's largest steel maker, disclosed unauthorized access to certain IT systems.
- The company activated its incident response plan and involved law enforcement and cybersecurity experts.
- Limited data was stolen from Nucor's systems during the cyberattack.
- Operations and IT systems have been restored, and the threat actor no longer has access.
- Nucor confirmed no material business or financial impact from the incident.
- The nature of the attack was not specified in the notifications.
- Experts suggest Nucor may have been a victim of a ransomware attack.
- No group has claimed responsibility for the cyberattack on Nucor.
- The incident is being monitored for any further developments.
- Nucor is reviewing and evaluating the impacted data for potential notifications.
- The company is committed to complying with regulatory requirements following the cyber incident.
- Nucor believes it has addressed the cybersecurity incident and restored normal operations.
- The cybersecurity incident did not have a significant impact on Nucor's business or finances.
- Nucor continues to assess its cybersecurity measures to prevent future incidents.
Read Full Article
17 Likes
Tech Radar
143

Image Credit: Tech Radar
This mega DDoS attack broke all records - huge 37.4TB bombardment in 45 seconds against a single victim is the largest ever recorded
- A massive DDoS attack targeted a hosting provider and attempted to dump almost 38TB of data in 45 seconds, making it the largest attack in history.
- Cloudflare successfully blocked the attack, which generated 7.3 terabits per second (Tbps) of traffic targeting 21,925 destination ports on an IP address.
- The attack used UDP packets as the main vector and also incorporated reflection, amplification, and flood attacks to overwhelm the network.
- The DDoS attack originated from 161 countries, with a significant portion of the traffic coming from IP addresses in Brazil, Vietnam, Taiwan, China, Indonesia, Ukraine, Ecuador, Thailand, the United States, and Saudi Arabia.
- Cloudflare managed to counter the attack by leveraging the distributed nature of the DDoS attack and spreading the traffic load across data centers near the traffic's origin.
- The attack involved compromised internet-connected devices infected with malware, highlighting the prevalence of botnets in orchestrating such attacks.
- Cloudflare's DDoS detection and mitigation systems were effective in identifying and mitigating suspicious packets without disrupting legitimate traffic.
- The attack saw a peak of 45,097 unique source IP addresses per second and an average of 26,855 throughout the attack duration.
Read Full Article
8 Likes
TechJuice
82

Image Credit: TechJuice
Govt Issues Advisory on Cisco ISE Cloud Vulnerability
- The government issues an advisory on a Cisco ISE cloud vulnerability allowing full admin control.
- The flaw affects Cisco ISE instances on platforms like AWS, Azure, and Oracle Cloud.
- The vulnerability, CVE-2025-20286, has a critical CVSS score impacting versions 3.1 to 3.4.
- Credential reuse and session validation issues lead to unauthorized access risks.
- Only Cisco's official marketplace cloud deployments are affected; on-premise setups are safe.
- A public PoC exploit heightens the threat with remote access to admin functions.
- Possible consequences include policy disruption and unauthorized data access.
- Updated secure ISE cloud images are released, urging organizations to redeploy.
- Immediate mitigation steps entail blocking public access, using VPNs, and MFA.
- Further measures include isolating affected resources and rotating credentials.
- System logs review, SIEM integration, and forensic assessments are recommended.
- Swift action is crucial to secure cloud environments and avoid exploitation.
- The advisory prioritizes deploying the new builds to address the vulnerability.
- Precautionary steps involve enhancing access controls and monitoring for unusual activities.
- Administrators are advised to act promptly to prevent system compromise and data breaches.
Read Full Article
4 Likes
Medium
60
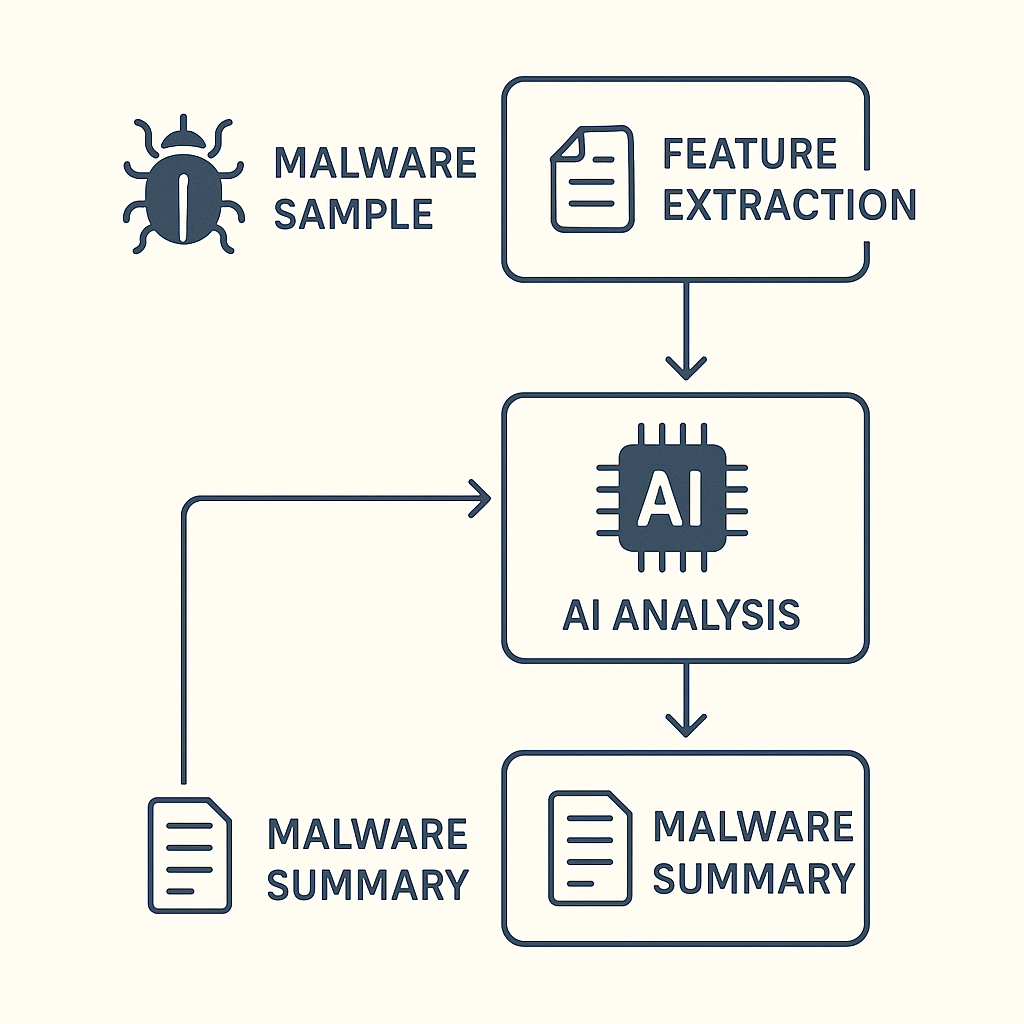
Image Credit: Medium
When AI Joins the SOC: My First Experiment in Malware Analysis !
- The author conducted an experiment using AI for malware analysis.
- The experiment aimed to make malware analysis faster and smarter.
- Traditional malware analysis is time-consuming and challenging for analysts.
- The author questioned whether AI could assist in reducing time without compromising quality in malware triage.
- The experiment focused on identifying malicious behavior based on static analysis data with the help of AI.
- The malware sample analyzed was a Remote Access Trojan.
- The AI's summary aligned well with the author's findings, emphasizing AI's potential in supporting malware analysis.
- AI is viewed as a tool to help professionals perform better, not replace their roles.
- The author encourages sharing experiences and tools for combining cybersecurity and AI.
- AI proved efficient in providing quick and consistent analysis results.
- AI is likened to a junior analyst, proficient in recognizing known patterns but still requiring guidance from experienced professionals.
- The experiment demonstrated the value of AI as a reliable assistant in malware analysis.
- AI is seen as a complement to human expertise in the field of cybersecurity.
- The author invites others to share their experiences of using AI in cybersecurity.
- AI enhances the analysis process by providing prompt insights and augmenting human capabilities.
Read Full Article
3 Likes
Tech Radar
182

Image Credit: Tech Radar
"No evidence" - here's why the massive 16 billion record data breach may not be as bad as first thought
- A recent 16 billion record data breach may not be as catastrophic as initially believed.
- Research indicates that the datasets likely consist of previously leaked information rather than new breaches.
- Although the affected individuals could still face risks, vigilance is advised.
- Initial datasets discovered contained vast amounts of personal data amounting to 16 billion records.
- It appears these datasets were likely compilations of breached credentials rather than a fresh breach.
- The information within the datasets has probably been circulating for some time and was collected through infostealers.
- Infostealers are malware types that steal credentials and upload them, often for sale on the dark web.
- Given that these breaches can contain billions of records, the current breach could be a compilation of stolen data samples.
- Individuals impacted by leaked credentials should consider using identity theft protection software and monitoring their information.
- Enabling multi-factor authentication and conducting thorough staff training on security awareness is crucial for businesses.
- Utilizing password managers and security tools like Google's Password Checkup can help safeguard user credentials.
- Experts suggest that addressing security systematically is essential to combat potential breaches effectively.
Read Full Article
10 Likes
Securityaffairs
2.4k
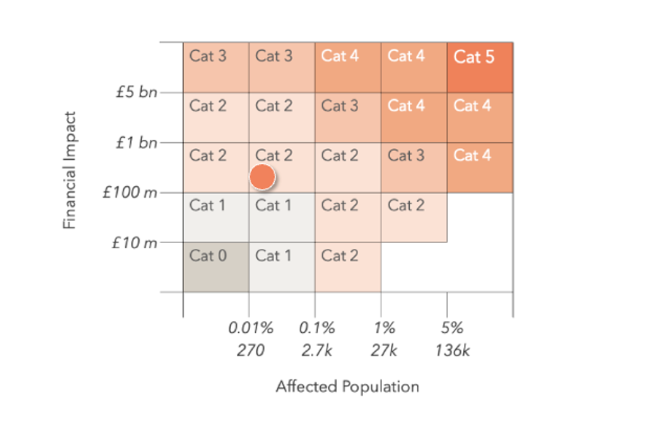
Image Credit: Securityaffairs
The financial impact of Marks & Spencer and Co-op cyberattacks could reach £440M
- The Cyber Monitoring Centre (CMC) has categorized cyberattacks on Marks & Spencer and Co-op as a Category 2 event, with estimated financial losses between £270M and £440M.
- Hackers named DragonForce claimed responsibility for the Co-op attack, accessing data of current and past members.
- Co-op initially denied customer data compromise but later confirmed data breach.
- DragonForce also targeted M&S and confessed to trying to hack Harrods, accessing staff and customer data.
- The attack exposed personal details of Co-op members but did not include sensitive information like passwords or financial data.
- DragonForce is known for ransomware attacks, data theft, and running a cybercrime affiliate service.
- The CMC linked M&S and Co-op attacks due to shared timing and threat actor, estimating total financial impact at £270M–£440M.
- The attacks caused major business disruption and financial consequences for M&S and Co-op.
- Estimated costs include legal fees, business interruption, incident response, and IT restoration for both companies.
- M&S anticipates a £300M impact, with significant declines in online sales and consumer spending.
- The incidents emphasized the vulnerability of retail supply chains and the importance of crisis preparedness and cyber resilience.
- CMC stresses the need for stress-testing crisis plans, financial resilience, enhanced cyber hygiene, and access control improvement.
- Clear crisis communication and robust recovery capabilities are essential during cyber incidents.
- CMC aims to enhance cyber readiness through collaboration and transparency.
- The financial impact of the M&S and Co-op cyberattacks highlights the widespread repercussions of cyber incidents in the retail sector.
Read Full Article
1 Like
Wired
365

Image Credit: Wired
Taiwan Is Rushing to Make Its Own Drones Before It's Too Late
- Taiwan is rushing to build its own drones due to the fear of Chinese invasion, aiming to produce 180,000 drones annually by 2028 but struggling with challenges like high costs and limited orders.
- The country faces the urgency to innovate for defense, potentially turning the Taiwan Strait into a 'hellscape' against Chinese aggression using drones and other unmanned vehicles.
- However, Taiwan struggles with sourcing critical components like chips from China due to cost and political reasons, inhibiting its drone industry growth.
- The nation's defense ministry has ordered fewer than 4,000 drones, revealing financial and political hurdles in ramping up production.
- DSET recommends US support for Taiwan's drone industry, urging partnerships and dropping tariffs to enhance mutual defense capabilities.
- Taiwan aims to expand drone capabilities beyond surveillance drones to align with American defense needs for longer-range systems.
- The report emphasizes the importance of Taiwan's defense preparations, including anti-drone systems and underwater autonomy, to counter potential Chinese invasion threats effectively.
- The risk of unsuccessful drone industry development could leave Taiwan in a gray zone of limited interoperability while the US may struggle to compete with China's defense exports.
- Despite facing challenges, Taiwan seeks to enhance its drone manufacturing industry, motivated by the success of Ukraine in developing indigenous drone capabilities.
- Taiwan's push for self-reliance in drone production showcases its determination to prepare for potential conflicts, highlighting the evolving landscape of military technology and defense strategies.
Read Full Article
21 Likes
For uninterrupted reading, download the app