Cyber Security News
Medium
431

Image Credit: Medium
Unlocking Trust and Behavior: A Closer Look into Password Manager Adoption Among Indonesian Digital…
- Password security remains crucial in today's digital landscape despite user habits of reusing passwords.
- A study titled 'An Analysis of Password Manager Adoption and Trust Among Indonesian Digital Users' delved into trust, behavior, and habit in digital security.
- Most Indonesian digital users still opt to create their own passwords rather than accept system-generated ones, revealing issues of trust and habit.
- 73% of users preferred creating their own passwords despite being prompted to use randomly generated ones.
- The study highlights the human factors of habit and lack of trust influencing password management choices, aligning with established psychology literature on digital behavior.
- Developers and security practitioners should focus on improving user trust and addressing habitual behavior to enhance password security adoption.
- The study emphasizes the need for a secure system that users have faith in, beyond just technical security measures.
- It suggests that simple prompts for stronger passwords are insufficient; a holistic approach involving human-centered design, transparency, and education is essential.
- The study, conducted by Telkom University, aims to contribute to applied cybersecurity research with an Indonesian perspective.
- Despite a modest sample size, the study offers profound insights that call for further dialogue and action in addressing digital security challenges.
Read Full Article
25 Likes
Medium
117

A Step-by-Step HIPAA Compliance Roadmap: Essential Guide for Healthcare Organizations
- HIPAA compliance is crucial for healthcare organizations to protect patient trust and avoid financial penalties.
- Implementing HIPAA standards is essential due to the increasing cyber threats in the healthcare industry.
- Start by understanding the core HIPAA rules and conducting regular risk assessments to proactively address vulnerabilities.
- Develop a robust security framework that includes encryption, access controls, and incident response plans.
- Employee training is vital to prevent data breaches caused by human error.
- Document all policies, risk assessments, training sessions, and security measures to maintain compliance.
- Continuous monitoring and annual reviews are necessary to ensure ongoing compliance.
- For a detailed HIPAA compliance roadmap, a comprehensive guide is available on Dev.to.
- Expert assistance for HIPAA compliance is offered by Defense Rabbit to help organizations safeguard their data.
Read Full Article
7 Likes
Medium
74

Image Credit: Medium
A Simple Guide to Privacy Online
- The article provides a simple guide to improving online privacy from around 1% to 60%, focusing on practical steps rather than aiming for perfect privacy.
- Key points include using Brave browser to block trackers, Mozilla VPN to hide internet activity, Signal for secure messaging, and OsmAnd for location privacy.
- Tips include avoiding sharing photos with location data, questioning privacy in different contexts, and not trusting platforms like Google or Facebook for privacy.
- Recommendations also cover search engines like DuckDuckGo, the importance of ad-blocking, and caution against using Tor without deep understanding.
- The article emphasizes that privacy is a right and suggests that being private online is about common sense, not having anything to hide.
Read Full Article
4 Likes
Dev
1.3k

Image Credit: Dev
Revolutionizing DevSecOps: How AI is Reshaping Software Security
- The article discusses how AI is transforming DevSecOps to enhance software security throughout the SDLC.
- AI aids in threat intelligence by detecting anomalies in real-time, enabling predictive threat detection and response.
- It improves vulnerability detection tools by reducing false positives and prioritizing critical flaws efficiently.
- AI enhances security testing through intelligent fuzzing, generating diverse test cases to uncover complex vulnerabilities.
- It automates security policy enforcement, suggesting remediation steps, and orchestrating incident response for efficient DevSecOps workflows.
- AI assistants help in secure code generation and review by identifying potential security issues during coding and code reviews.
- Benefits include increased speed, improved accuracy, reduced manual effort, proactive security, and optimized resource allocation.
- Challenges include data privacy concerns, algorithmic bias, the need for human oversight, management of false positives/negatives, and integration complexity.
- Future outlook predicts more advanced AI models for complex code understanding, zero-day vulnerability prediction, and autonomous patching.
- The integration of AI into DevSecOps offers both benefits and challenges, shaping the future of software security.
Read Full Article
24 Likes
Dev
11

Image Credit: Dev
AI in DevSecOps: Actionable Strategies for Next-Gen Software Security
- The integration of security in DevSecOps is crucial in the evolving software landscape to combat cyber threats proactively using AI.
- AI aids in threat modeling by predicting attack vectors and prioritizing risks through data-driven analyses.
- For static and dynamic application security testing, AI reduces false positives, enhancing the accuracy and effectiveness of vulnerability identification.
- AI assists in automated vulnerability remediation by suggesting or generating code fixes, expediting the resolution process.
- In production environments, AI enables anomaly detection by monitoring unusual patterns for rapid response and containment of security breaches.
- Challenges in AI integration include data quality, model bias, explainability, and pipeline complexity, addressed by best practices like starting small, ensuring high-quality data, maintaining human oversight, focusing on explainability, and continuous learning.
- Successful AI adoption in DevSecOps requires embracing practical strategies to leverage AI effectively for resilient and efficient pipelines.
Read Full Article
Like
Medium
161

Image Credit: Medium
Reimagining Risk Assessment with AI: From Static Checklists to Dynamic Intelligence
- Many companies still use outdated checklists for cybersecurity risk assessments, which are insufficient for today's rapidly changing cyber threats.
- Traditional risk assessments are manual, slow, and limited to past information, while AI provides real-time insights and predictive analysis.
- AI helps in continuous monitoring to detect anomalies, predict potential threats, and adapt to the evolving environment.
- Biased models and lack of transparency in AI decision-making pose challenges, requiring attention to compliance and human oversight.
- AI enhances risk management by offering early warnings, automating responses, and improving decision-making.
- The future of risk assessment lies in proactive AI-driven approaches that keep pace with dynamic cyber risks.
- AI serves to complement human decision-making by providing better visibility, quicker responses, and enhanced risk awareness.
- Moving from reactive to proactive risk management enables organizations to stay ahead in cybersecurity defenses.
- Relying solely on static checklists for cyber risk assessment is insufficient in today's fast-paced digital landscape.
- AI's capabilities in real-time monitoring, pattern recognition, and adaptability revolutionize cybersecurity risk management.
Read Full Article
9 Likes
Medium
148

Image Credit: Medium
Proof-of-Favo: A Hybrid Consensus Architecture for the Mobile Web3 Era
- Proof-of-Favo (PoFavo) is a hybrid consensus model introduced by FavoChain for global network creation.
- FavoChain combines a core of professional validators (FavoSeal) with a swarm of millions of mobile devices (FavoSwarm) in its architecture.
- FavoSeal provides speed and security comparable to top DPoS systems, aiming to address centralization issues.
- FavoSwarm consists of mobile devices verifying transaction signatures, contributing to decentralization.
- The system faces significant engineering challenges that require the expertise of top engineers to solve.
- Key challenges include security guarantees, scalability, and economic incentives for participants.
- FavoChain is seeking co-founders and contributors to collaboratively address these complex problems.
- The project is in the architectural manifesto stage, emphasizing the importance of finding innovative solutions.
Read Full Article
8 Likes
Medium
357

Image Credit: Medium
The gentle way out.
- The author reflects on their journey of finding moderation as a way out of addiction and escape.
- They describe how addiction promised relief but always came with shame, leading to a cycle of seeking comfort that turned into a cage.
- The author used to swing between extremes of indulgence and deprivation, always followed by guilt and shame.
- Learning to pause, breathe, and assess their true needs helped the author start responding instead of reacting to cravings.
- Moderation, for the author, meant saying 'not now' instead of 'never again,' allowing rest without guilt, and setting boundaries that respected their body and soul.
- Through moderation, the author regained a sense of power and trust in themselves, realizing they could sit with desires without losing control.
- The journey towards moderation was not about perfection but progress anchored in peace and the acceptance of humanity.
- It was a process of surrendering to grace and coming home to oneself instead of fighting internal battles.
- The author encourages others to embrace a slower, quieter path that listens to the body, respects boundaries, and allows the soul to breathe.
- A message of hope is shared for those still struggling, emphasizing that finding balance and healing is a journey that doesn't require running away anymore.
Read Full Article
21 Likes
Tech Radar
205

Image Credit: Tech Radar
The TSA has issued an urgent warning about criminals using fake USB charging ports, free Wi-Fi honeypots to steal your identity ahead of summer holidays
- The TSA has issued a warning about criminals using fake USB charging stations and free Wi-Fi networks to steal personal information from travelers.
- Criminals are using 'juice jacking' attacks to install malware on public USB charging stations, capturing text messages, contact lists, and keystrokes from connected devices.
- Free public Wi-Fi networks, also known as 'honeypots,' controlled by criminals, can intercept data transmitted by travelers and lead to identity theft.
- Travelers are advised to use their own wall adapters or power banks and avoid direct USB connections from untrusted sources to mitigate risks.
- To protect against Wi-Fi risks, users are encouraged to use virtual private networks (VPNs) and ensure their devices are safeguarded with identity theft protection software.
- It is recommended to refrain from entering sensitive information while using unsecured public Wi-Fi networks to prevent identity theft.
Read Full Article
12 Likes
VentureBeat
414

Image Credit: VentureBeat
Cloud quantum computing: A trillion-dollar opportunity with dangerous hidden risks
- Quantum computing (QC) poses both groundbreaking possibilities and significant risks as major tech players offer commercial QC cloud services and specialized firms gain unicorn status.
- The global QC market could potentially boost the economy by more than $1 trillion between 2025 and 2035, yet concerns arise about the balance between benefits and risks.
- QC systems hold promise in revolutionizing areas like drug discovery, climate modeling, AI, and potentially artificial general intelligence, while also introducing cybersecurity challenges.
- The main cybersecurity fear linked to QC is its potential to break current encryption algorithms, presenting a serious risk to data privacy and security.
- Concerns revolve around the ability of quantum computers to decipher encryption methods that are currently deemed unbreakable by classical computers.
- Grover's algorithm and Shor's algorithm are noted for their impact on encryption methods, necessitating a shift towards more robust encryption standards like AES-256.
- Organizations need to adopt 'crypto agility' to swiftly replace cryptographic algorithms and implementations as new vulnerabilities arise due to quantum threats.
- AI and quantum computing integration raise concerns due to the complexity and opacity of quantum processes, potentially leading to unpredictable AI decisions in vital sectors like healthcare and finance.
- NIST's Post-Quantum Cryptography Standardization project and subsequent rollout of post-quantum cryptographic standards aim to mitigate quantum threats, with tech giants like Apple, Google, and Microsoft implementing early protections.
- While the timeline for quantum threats varies, preparations against quantum security threats are vital for organizations, urging the adoption of post-quantum cryptography and proactive measures.
- In the quantum era, technology readiness and human error remain critical aspects, emphasizing the need for a strategic approach to quantum security challenges.
Read Full Article
24 Likes
Tech Radar
296
Image Credit: Tech Radar
Cybercriminals are targeting gamers with expired Discord invite links which redirect to malware servers - here's how to stay safe
- Cybercriminals are repurposing expired Discord invite links to launch multi-stage malware attacks on users, particularly gamers.
- Attackers are registering once valid invite links with custom vanity URLs, redirecting users to malicious servers hosting malware campaigns.
- Users are lured to fake Discord servers and tricked into running PowerShell commands disguised as CAPTCHA fixes.
- Malware installations are stealthily initiated through a series of cloud services like Pastebin and GitHub, evading detection mechanisms.
- A tool known as AsyncRAT grants attackers remote control over infected systems, while Skuld Stealer is utilized to extract credentials and crypto wallet data.
- Gamers are a primary target, with malware disguised as popular tools like The Sims 4 DLC unlockers to deceive users.
- The Skuld Stealer poses a significant risk by enabling extraction of crypto wallet data and passwords, giving attackers control over victims' digital assets.
- End users are advised to enhance their security measures with identity theft protection services to detect unauthorized use of personal information and assist in recovering compromised identities.
- Despite popular belief, traditional endpoint protection tools may not adequately defend against these sophisticated attacks due to their multi-layered structure.
- To mitigate risks, users should exercise caution with Discord invite links, avoid executing suspicious scripts, and refrain from following unverified verification steps.
Read Full Article
17 Likes
Medium
257

Image Credit: Medium
# The Code and the Blade: Why Omega Browser Isn’t Just Another Privacy-Focused Browser
- The Omega Browser is a new privacy-focused browser that aims to give users total control over their digital footprint.
- The browser has been developed by studying the architecture of other browsers that promise user protection while still collecting data in the background.
- The creator of Omega Browser reverse-engineered network traffic flows, dissected data collection systems, and analyzed fingerprinting techniques to ensure privacy.
- Every time a page is loaded in the Omega Browser, behavioral data is collected, user profiles are updated, and fingerprinting algorithms track various user actions.
- The browser focuses on 'User Experience Optimization,' which the creator criticizes as 'Surveillance Disguised as Usability.'
- Features in the browser are vetted to ensure they protect user privacy, while anything that compromises privacy is removed.
- The Omega Browser emphasizes total user control over data and behavior metrics, promising not to track or manipulate user information.
- The browser is still in active development and is not without imperfections, but it aims to cater to users who are concerned about their online privacy and data security.
- It is positioned as a tool for users who want to avoid being treated as 'inventory data' and believe that their online actions belong only to them.
- The Omega Browser is described as not just software but a 'blade' that will cut through the noise surrounding online privacy and data collection.
Read Full Article
15 Likes
Medium
366

The Prime Collapse: Cybersecurity’s Tipping Point
- Researchers have made a mathematical breakthrough to detect prime numbers without divisibility checks.
- The breakthrough is based on integer partition theory and was published in the Proceedings of the National Academy of Sciences.
- Prime numbers are crucial for encryption schemes like RSA, ECC, and blockchain wallet generation.
- Predicting primes poses a significant risk to digital security and encryption methods.
- There is a current emphasis on Rapid AI/Cryptographic Evolution to address prime prediction risks.
- TAC Consulting provides solutions like Prime Anomaly Detection and PQC Migration Engine to secure against prime prediction threats.
- Zero-Trust Crypto Enclaves and AI-Aided Red Team Simulations are also utilized to mitigate risks.
- Individuals are advised to take proactive security measures in light of this mathematical inflection point.
Read Full Article
22 Likes
Medium
165
Image Credit: Medium
Chasing Ghosts: My Journey to Building a Truly Anonymous Messaging System in 2025
- The article discusses the increasing concerns about digital privacy due to heightened surveillance by governments and corporations.
- The author embarked on a mission to create a fully anonymous and untraceable messaging system in 2025.
- The post details the author's research, experiments, and a Proof of Concept (PoC) system for anonymous messaging.
- The DOT Framework, a three-pronged approach, was used to achieve anonymity in digital communications.
- Briar emerged as the most anonymous system but has scalability and speed limitations, requiring both parties to be online simultaneously.
- Nation-states and adversaries exploit metadata and traffic patterns to de-anonymize users, showcasing encryption's inadequacy.
- A visual guide illustrates the communication flow, including peer discovery, secure session establishment, and data exchange.
- The article emphasizes the importance of addressing high-risk attack vectors through a Risk Matrix and mitigation strategies.
- The author encourages community involvement, offering the project as open source under the MIT License on GitHub.
Read Full Article
9 Likes
Securityaffairs
310
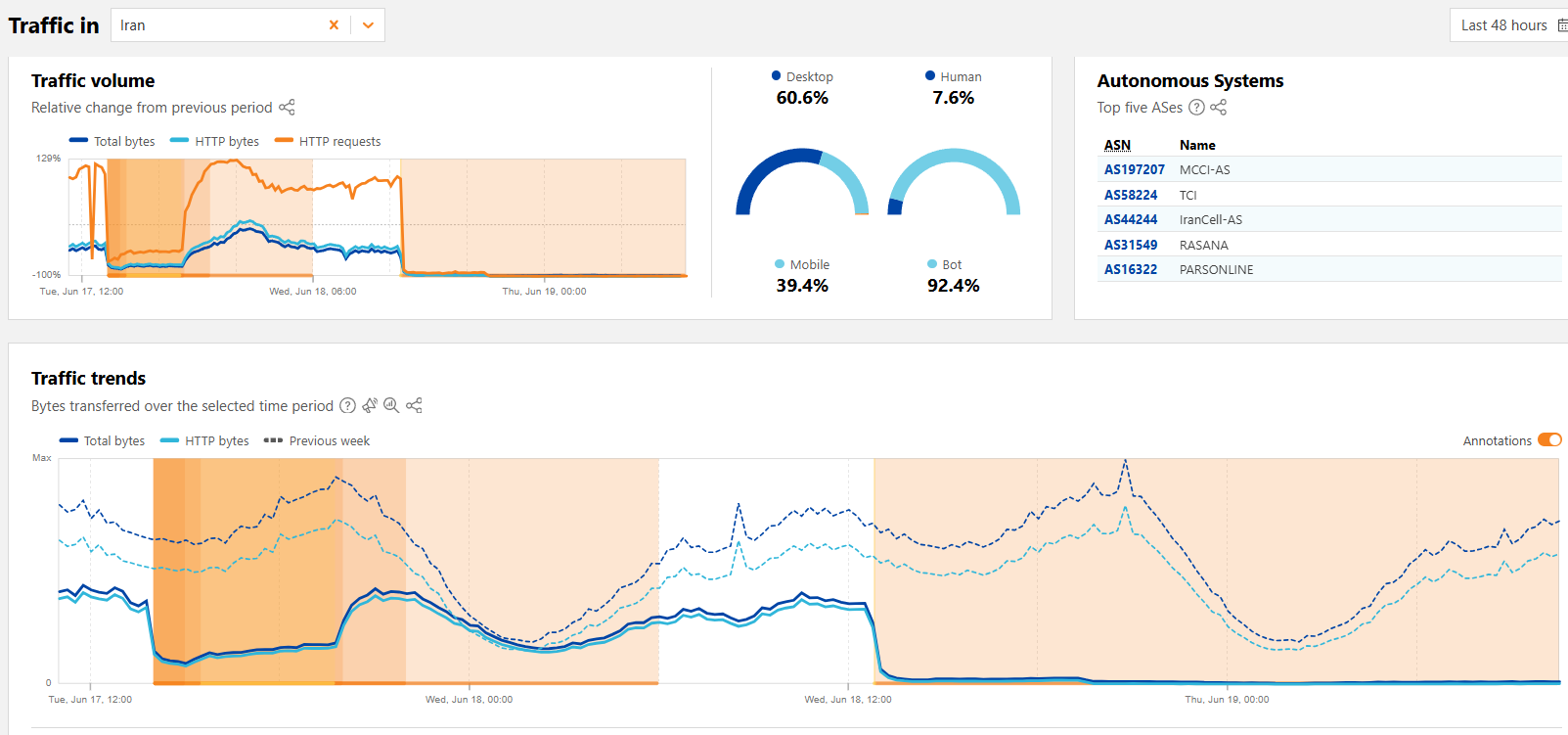
Image Credit: Securityaffairs
Iran confirmed it shut down internet to protect the country against cyberattacks
- Iran confirmed an internet shutdown to counter Israeli cyberattacks aimed at protecting critical infrastructure and preventing drone interference.
- The internet blackout in Iran occurred amid escalating military tensions with Israel, impacting the country's communication and information access.
- The exact cause of the internet shutdown remains uncertain, with no definitive evidence linking it to a technical failure, deliberate government action, or external cyber operation.
- The Iranian government has acknowledged ordering the shutdown to safeguard against cyberattacks, citing threats to infrastructure and drone control.
- Reports indicate that enemy drones were controlled through the internet, prompting the restriction to ensure national security and prevent further disruptions.
- The internet blackout followed cyberattacks on Iranian institutions, including the hacking of Iran's largest crypto exchange and disruptions in banking services.
- A pro-Israel hacking group, 'Predatory Sparrow,' claimed responsibility for the cyberattacks on Iran, targeting financial institutions and crypto exchanges.
- The group accused Iran of using crypto exchanges to evade sanctions and claimed to have destroyed data at Iran's state-owned Bank Sepah, leading to potential banking disruptions.
- Cybersecurity firms confirmed the theft of crypto assets and their transfer to accounts referencing Iran's Revolutionary Guard Corps, highlighting the ongoing cyber warfare.
Read Full Article
18 Likes
For uninterrupted reading, download the app