Cyber Security News
Arstechnica
91

Image Credit: Arstechnica
Record DDoS pummels site with once-unimaginable 7.3Tbps of junk traffic
- Cloudflare reported a massive DDoS attack hitting 7.3 terabits per second, the largest ever.
- The attack sent 37.4 terabytes of data within 45 seconds, equivalent to over 9,300 HD movies.
- Attackers targeted a Cloudflare customer by 'carpet bombing' 22,000 destination ports on a single IP.
- UDP flood attacks overwhelmed the target's resources with high packet volumes.
- Reflection attacks accounted for a small portion of the DDoS, redirecting traffic through third-party intermediaries.
- Reflection attacks make it harder to defend against DDoS attacks and increase attack firepower.
- The DDoS used various reflection or amplification vectors like the Network Time Protocol and Quote of the Day Protocol.
- The attack was facilitated by one or more Mirai-based botnets, compromising home IoT devices.
- DDoS attack sizes have been steadily increasing, with recent attacks peaking at 6.5Tbps and 6.3Tbps.
- Large-scale attacks aim to overwhelm Internet services by sending excessive traffic, causing denial of service.
Read Full Article
5 Likes
Dataprivacyandsecurityinsider
354

CISO’s: Take a Look at CSC’s CISO Outlook 2025 Report
- Cybersecurity firm CSC releases CISO Outlook 2025 Report on upcoming challenges for CISOs.
- Report based on survey of 300 CISOs globally; predicts intensifying cybersecurity challenges.
- Key findings: 70% CISOs foresee increased security threats in the next year.
- 98% believe risks will rise over next three years; 66% expect cyber risks to be 'significant.'
- 76% somewhat confident in mitigating domain attacks; regulatory compliance remains a challenge.
- AI-powered attacks escalating threat levels; top cited risks include cybersquatting and DDoS attacks.
- Anticipated risks in next three years: cybersquatting, domain/DNS hijacking, ransomware/malware.
- CISOs acknowledge evolving and complex cyber threats, making defense harder.
- Proposed steps: Establish AI Governance Program, focus on Shadow AI, prepare for security audits, consider outsourcing.
- Protecting organizations in 2025 will remain intricate amid evolving threats and risks.
Read Full Article
21 Likes
Tech Radar
17

Image Credit: Tech Radar
FBI issues urgent warning about new SMS toll scam – here's how to spot it and what to do
- The FBI has issued a warning about a new SMS toll scam targeting drivers in the US, pretending to be from the Department of Motor Vehicles (DMV).
- The scam urges recipients to click on malicious links to steal credit card information.
- The FBI advises users to delete such messages immediately.
- The scam is a copycat of previous toll scams, tricking victims into giving away personal information.
- These scams are easy to distribute and can gather sensitive information easily.
- Common signs of fake texts include generic greetings, urgent language, unusual links, mistakes, and unknown senders.
- Most toll scam texts claim outstanding toll charges and direct recipients to fake payment sites.
- These fake sites appear official with similar fonts, colors, and logos.
- Scammers create a sense of urgency to trigger an emotional response and prompt recipients to act quickly.
- Be cautious of inconsistencies in the messages, such as fake sender details and errors.
- If uncertain, avoid clicking on links and contact the relevant agency directly for verification.
- Delete suspicious messages and report them to the FTC and FBI.
- Stay vigilant to avoid falling victim to SMS toll scams.
Read Full Article
1 Like
Tech Radar
358

Image Credit: Tech Radar
Forget Chrome and Edge - this challenger browser now offers greater protection from online scams
- DuckDuckGo introduces a new Scam Blocker tool in its browser to protect users from online scams.
- The tool aims to guard users against phishing websites, malware, fake crypto-currency exchanges, fraudulent shopping sites, and scareware.
- Online scams are on the rise, with cybercriminals using AI for more frequent and sophisticated scams, causing financial losses.
- The Scam Blocker does not send tracking information to third parties, ensuring user privacy.
- It is available for free on DuckDuckGo for mobile and desktop users.
- Privacy Pro users can enjoy full-device coverage even when using other browsers if logged into the DuckDuckGo VPN.
- The tool prevents scammy pages from loading, offers warning messages, and blocks tracker-powered ads to protect users from malvertising.
- Scam Blocker is designed to keep browsing data private and secure, storing a 'dangerous site list' locally on the device.
- DuckDuckGo's Scam Blocker is based on data from independent cybersecurity company Netcraft and does not require an account.
- The tool's scam protections are developed without sharing browsing data with third parties.
Read Full Article
21 Likes
TechCrunch
8

Image Credit: TechCrunch
Iran’s government says it shut down internet to protect against cyberattacks
- Iran recently experienced a national internet blackout.
- The government has confirmed that it shut down the internet to protect against Israeli cyberattacks.
- The shutdown limits Iranians' access to information about the ongoing war with Israel and communication with others.
- Iran's government spokesperson mentioned concerns over cyberattacks on critical infrastructure.
- Hacks on Bank Sepah and Iranian cryptocurrency exchange led to restrictions.
- Predatory Sparrow, a group claiming to be pro-Israel, has disrupted key services in Iran.
- Everyday Iranians are suffering from the internet shutdown amid Israeli bombardments.
- Families have been impacted by the lack of communication due to the shutdown.
- Some individuals manage to access the internet using virtual private servers or ADSL connections.
- Accessing the internet remains a challenge due to the complete shutdown in the country.
Read Full Article
Like
Tech Radar
4

Image Credit: Tech Radar
Tech support scammers are forcing their fake phone numbers into real webpages
- Scammers are injecting fake tech support phone numbers into legitimate websites like Apple, PayPal, and Netflix.
- The scam bypasses typical security checks and relies on injecting malicious phone numbers onto official sites.
- Attackers are using online advertising spaces and Google Ads to pose as major brands.
- Scammers manipulate legitimate URLs with malicious phone numbers to deceive users.
- The attack is described as a search parameter injection or reflected input vulnerability.
- When users call these fake numbers, scammers impersonate the brand to extract personal data or financial information.
- Other targeted companies include HP, Microsoft, Facebook, and Bank of America.
- Malwarebytes warns users to be cautious of tech support hotlines embedded in URLs and containing high-pressure terms like 'Call Now'.
- Users should check for unusual characters in URLs and navigate to official websites for support rather than trusting ads.
- Over 16 billion records were leaked in a recent major data breach.
- It is important to use antivirus and endpoint protection software to protect against such threats.
- Consider using VPNs to safeguard your digital footprint and enhance online security.
Read Full Article
Like
Pcgamer
91
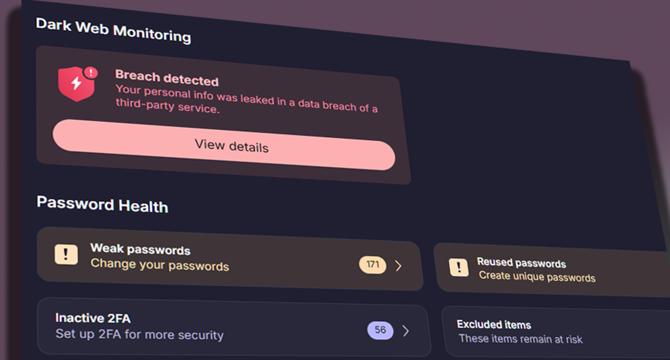
Image Credit: Pcgamer
No, 16 billion passwords didn't just get exposed in a mega-hack, but you should get with the program and stop reusing passwords anyways
- Recent claims of 16 billion passwords being exposed in a mega-hack are actually a collection of previous breaches, not a singular massive breach.
- The report originates from Cybernews, known for inflating previous breach numbers, causing skepticism in the cybersecurity community.
- The 16 billion figure is a compilation of data from multiple sources over the years, put together by a researcher, Bob Diachenko.
- Major tech companies allegedly included in this 'breach' have not confirmed or addressed the issue publicly, raising doubts about its validity.
- Cybersecurity experts point out that the collection may contain recycled or fabricated data, diminishing its credibility.
- Websites like haveibeenpwned.com monitor breaches, with the largest noted breach being Collection #1 from early 2019, demonstrating the common occurrence of such collections.
- While this 'breach' may not pose an immediate threat, it underscores the importance of using strong, unique passwords and enabling two-factor authentication.
- Advice includes using password managers like Bitwarden or Proton Pass and avoiding common passwords like '123456' or 'password'.
- Reusing passwords across multiple accounts increases the risk of theft and fraud, emphasizing the need for better cybersecurity practices.
Read Full Article
5 Likes
Siliconangle
10.3k

Image Credit: Siliconangle
Andy Jassy says AI will reduce Amazon’s workforce but at least he’s honest about it
- Amazon CEO Andy Jassy acknowledges that AI will reduce the company's workforce, emphasizing the shift to higher-value tasks.
- Microsoft reportedly plans layoffs, indicating a broader trend in the industry.
- Mark Zuckerberg aims to elevate Meta's AI capabilities through strategic acquisitions.
- Google introduces Gemini 2.5 Flash-Lite, expanding its AI model lineup.
- OpenAI secures a significant defense contract, demonstrating the interest in AI technology within government sectors.
- Companies like Broadcom and Pure Storage pivot towards AI and data-focused solutions in response to evolving cloud services.
- AWS unveils new cybersecurity features at the re:Inforce conference, prioritizing simplicity and efficiency.
- Texas Instruments plans a $60 billion investment in U.S. fabs to boost domestic chip manufacturing.
- Intel undergoes organizational changes, including both new executive appointments and layoffs.
- Various AI startups secure substantial funding for innovative projects, ranging from healthcare to enterprise solutions.
Read Full Article
32 Likes
Pymnts
402

Image Credit: Pymnts
Data Breach Exposes 16 Billion Login Records for Online Services
- Thirty databases containing 16 billion login records for various online services were briefly exposed.
- The data is recent and may include overlapping information, with only one dataset previously reported.
- Login records for social media, corporate platforms, VPNs, developer portals, and more were included with URLs, login details, and passwords.
- The data breach was most likely caused by infostealers, a type of malware that steals sensitive information.
- The Cybernews researchers warned that this data breach provides cybercriminals with credentials for account takeover and identity theft.
- Protective measures suggested include using password generators, updating passwords frequently, enabling two-factor authentication, and monitoring accounts.
- Old and recent infostealer logs included in the data make it dangerous for organizations lacking multi-factor authentication practices.
- In today's digital ecosystem, businesses need a holistic approach to cybersecurity due to increasing data breaches through various entry points.
- Protecting data now necessitates a collective effort among businesses, service providers, and vendors.
- Reported cyber and scam-related losses reached $16.6 billion in 2024, a 33% increase from the previous year, according to the FBI's IC3.
- The news was reported by Cybernews and highlighted by PYMNTS.
Read Full Article
24 Likes
Medium
201
Image Credit: Medium
Is Your Smart Home Spying on You? How to Keep Hackers Out
- Smart home gadgets offer convenience but pose hidden risks in terms of cybersecurity.
- Constant internet connection in smart devices makes them vulnerable to cybercriminals.
- Out-of-date smart gadgets without software updates become easy targets for hackers.
- Manufacturers often neglect releasing patches, leaving devices permanently vulnerable.
- Using a single Wi-Fi network for all devices can create a security risk.
- If a hacker gains access to a less secure device like a smart toaster, they can potentially access the entire network.
- This breach could compromise the security of devices ranging from baby monitors to work computers.
Read Full Article
12 Likes
Tech Radar
378

Image Credit: Tech Radar
Whole big mess - Krispy Kreme data breach sees data on over 160,000 people exposed
- Over 160,000 people, mostly Krispy Kreme employees and their family members, had their data leaked in a recent breach.
- The breach exposed a wide range of sensitive information such as names, Social Security numbers, financial details, and more.
- The stolen data was allegedly compiled into a single database, making it easier for attackers to access a large amount of information.
- The victims have been offered 12 months of credit monitoring and identity theft protection.
- Krispy Kreme has confirmed the breach and stated that they are taking steps to investigate and address the incident.
- There is no evidence of misuse of the leaked information or reports of identity theft or fraud so far.
- The Play ransomware group has claimed responsibility for the breach, although no concrete proof has been provided.
- The breach highlights the importance of safeguarding sensitive data, especially financial and personal information.
- Krispy Kreme is working with cybersecurity experts to handle the situation.
- The breach saw a significant amount of information compromised, including usernames, passwords, biometric data, and more.
- The company disclosed the breach to the Maine Attorney General's Office.
- The breach underscores the ongoing threat of cyberattacks and the potential risks to individuals' privacy.
- The Play ransomware gang claimed to have stolen various confidential data, but did not offer evidence.
- The affected individuals are at risk of credit fraud, identity theft, and other financial crimes.
- Krispy Kreme is providing support to the victims through credit monitoring and identity theft protection.
Read Full Article
22 Likes
The Verge
267

Image Credit: The Verge
Microsoft is blocking Google Chrome through its family safety feature
- Microsoft's Family Safety feature has been reported to block Google Chrome on Windows, preventing it from opening since early June.
- The issue seems to be a bug within Family Safety that targets Chrome, but other browsers like Firefox and Opera are unaffected.
- Users have found a workaround by renaming Chrome.exe to Chrome1.exe or by disabling the 'filter inappropriate websites' setting in Family Safety.
- Microsoft has not provided a timeline for fixing this problem, which has been ongoing for over two weeks.
- Microsoft has not responded to inquiries about this issue as of the time of publication.
Read Full Article
16 Likes
Global Fintech Series
100

Image Credit: Global Fintech Series
Enkrypt integrates SPACE ID’s Payment ID for seamless CEX transfers
- Enkrypt integrates SPACE ID’s Payment ID solution for easy crypto transfers to centralized exchanges (CEX) across different chains.
- Payment ID simplifies transfers by using human-readable names instead of long deposit addresses, reducing errors.
- Enkrypt users can send crypto to any CEX on any chain with just one simple name.
- Integration includes SPACE ID’s SDK for utilizing domain names for seamless crypto transfers between web3 wallets.
- Enkrypt aims to improve the user experience by making crypto transfers more secure and seamless.
- PAYMENT ID system by SPACE ID launched in April and is integrated with MetaMask and Binance.
- Enkrypt becomes one of the first wallets to natively support Payment ID and SPACE ID's identity infrastructure.
- The collaboration aims to simplify crypto transfers, removing the need for bridging and long deposit addresses.
- Harrison Seletsky from SPACE ID expresses excitement about working with Enkrypt and Unstoppable Domains for a more unified crypto payments ecosystem.
- Kosala Hemachandra of MyEtherWallet & Enkrypt highlights the focus on making crypto and web3 more user-friendly.
- Enkrypt's integration with SPACE ID and Payment ID streamlines the crypto transfer process for users.
- The partnership represents a step towards uniting the web3 space and enhancing interoperability.
- Enkrypt's goal is to simplify crypto and web3 usage for all users.
- The collaboration between Enkrypt, SPACE ID, and Unstoppable Domains aims to simplify crypto transfers and enhance security.
- This partnership showcases efforts to align the web3 user experience with web2 standards.
- The integration offers native support for Payment ID and identity infrastructure, making crypto transfers more user-friendly.
Read Full Article
6 Likes
Dev
153

Image Credit: Dev
Flutter Security: Top Best Practices
- This article emphasizes the importance of security in Flutter app development, offering essential best practices to ensure data integrity and user privacy.
- Key practices include secure data storage, utilizing flutter_secure_storage and encrypted databases for sensitive information.
- Network security measures like enforcing HTTPS, and certificate pinning for sensitive applications, are recommended to protect data in transit.
- Input validation, authentication flows, and role-based access control are essential for preventing malicious inputs and ensuring secure user identity verification.
- Code obfuscation, tamper detection, and securing dependencies are highlighted as ways to protect intellectual property and deter unauthorized access.
- Addressing error handling, logging sensitive information, and continuously updating security measures are crucial for maintaining app security.
Read Full Article
9 Likes
Medium
0

Image Credit: Medium
Meta Data Breach 2025: What Was Stolen and Why It Matters
- A massive data breach in early 2025 involving Meta and other major platforms exposed over 16 billion login credentials from more than 30 breached databases.
- Stolen data includes accounts from platforms like Facebook, Instagram, Gmail, Snapchat, Roblox, government portals, and banking services, with a majority of the data being recent, intensifying the seriousness of the situation.
- Cybercriminals obtained usernames, email addresses, plaintext passwords, session cookies, authentication tokens, metadata like IP addresses, device identifiers, browser fingerprints, and timestamps.
- Experts recommend changing passwords on important accounts, avoid password reuse, enable two-factor authentication using apps or passkeys, monitor accounts for suspicious activity, and consider using a password manager.
- This breach represents a significant cybersecurity threat with billions of up-to-date login records stolen, potentially impacting users of Facebook, Instagram, Gmail, and similar platforms.
- Users are urged to take immediate action by changing passwords, implementing stronger authentication measures, and staying vigilant to reduce their exposure to the breach.
Read Full Article
Like
For uninterrupted reading, download the app