Cyber Security News
Tech Radar
39

Image Credit: Tech Radar
M&S and Co-op hacks publicly defined as a single attack - and could cost more than £400 million
- The Cyber Monitoring Centre (CMC) considers the recent cyberattacks on M&S and Co-op as a single combined event by the attacker named Scattered Spider.
- The attacks are estimated to have a financial impact of between £270 million to £440 million on both firms.
- The disruption costs are mainly driven by business disruption, impacting not just the retailers but also their suppliers and partners.
- M&S and Co-op faced business disruption, data loss, and incurred costs for incident response and IT rebuild.
- The wider cost analysis includes the impacts on partners, suppliers, and other entities.
- The attack on Harrods, another major UK retailer, has not been included due to insufficient information about the cause and impact.
- M&S reported the attack on April 22 which may cost them around £300 million in lost operating profit.
- M&S has not confirmed paying a ransom to the hackers but admitted some customer data was stolen, excluding sensitive payment details.
- Customers concerned about data exposure are advised to check using dark web monitoring services or breach monitors like Have I Been Pwned.
- The mystery of the M&S hack has deepened, with TCS claiming none of its systems were compromised.
Read Full Article
2 Likes
Securityaffairs
47

Image Credit: Securityaffairs
Iran-Linked Threat Actors Cyber Fattah Leak Visitors and Athletes’ Data from Saudi Games
- Iran-linked threat actors known as Cyber Fattah have leaked thousands of records on athletes and visitors from past Saudi Games, as reported by U.S.-based cybersecurity firm Resecurity.
- The stolen data, leaked in the form of SQL dumps, includes personal information about visitors and athletes from the Saudi Games.
- Resecurity views this incident as part of a broader information operation conducted by Iran and its proxies to instill insecurity and disrupt peace in the region.
- Iran is increasing anti-US, anti-Israel, and anti-Saudi propaganda activities in cyberspace, targeting major sports and social events.
- The incident is significant amidst escalating tensions between Israel and Iran, with threat actors leveraging the roles of Saudi Arabia and the United States in regional relationships and security.
- Hezbollah-linked, Hamas-linked, and pro-Iranian groups in Iraq have amplified the incident through targeted propaganda activities on digital media channels.
- The data originates from a database associated with the Saudi Games 2024 official website, containing personal information such as International Bank Account Numbers (IBANs) and medical examination certificates.
- The breach poses serious implications for cybersecurity, sports integrity, and global audiences.
- No confirmed date yet for the Saudi Games 2025, with Saudi Arabia hosting various major sports events like the Islamic Solidarity Games and Esports World Cup 2025.
- Saudi Arabia aims to host the Olympics in 2036, with threat actors potentially targeting the reputation and efforts of the country through cyberattacks.
- The cyberattack on the Saudi Games is part of a broader narrative aimed at spreading insecurity and disrupting peace in the region.
- The incident underscores the vulnerability of major sports competitions to cyber threats and serves as a reminder of the importance of safeguarding sensitive data.
- For more information, follow Pierluigi Paganini on Twitter: @securityaffairs, Facebook, and Mastodon.
- Credit: SecurityAffairs - hacking, Cyber Fattah
Read Full Article
2 Likes
TechJuice
187

Image Credit: TechJuice
Critical Android Flaw Could Trick Users into Malware Downloads
- A critical Android flaw has been discovered that allows cybercriminals to insert hidden Unicode characters in app notifications.
- These invisible characters can disguise malicious links as legitimate ones, potentially leading to malware downloads without user knowledge.
- The exploit takes advantage of Android's interpretation of Unicode in notifications, creating a mismatch between visual content and system processing.
- This technique can be used in phishing campaigns, drive-by downloads, or credential theft.
- The flaw is not limited to a specific Android version, making numerous devices and apps vulnerable, especially messaging and email apps.
- The emergence of the Crocodilus banking Trojan further compounds Android's security issues, using Accessibility Services for complex attacks.
- Crocodilus overlays fake screens on banking apps, records keystrokes, steals login details, and manipulates contact lists for scam calls.
- Security experts recommend monitoring notifications, activating Google Play Protect, updating devices, limiting Accessibility Service access, and using reputable security apps.
- Users are advised to be cautious of suspicious notifications and adopt defensive measures against evolving cybersecurity threats on Android.
- Experts urge Google and developers to address the Unicode flaw promptly to enhance system transparency and secure mobile ecosystems.
Read Full Article
11 Likes
Dev
222

Image Credit: Dev
LetsDefend.io | SOC202- FakeGPT Malicious Chrome Extension
- The article discusses the investigation of a malicious Chrome extension named FakeGPT on LetsDefend.io, detailing the event's severity, date, and related information.
- The investigation covers areas such as file hash reputation check, suspicious processes analysis, network connections, browser history review, and log entries examination for possible Command and Control (C2) communication.
- The file hash was not flagged by antivirus vendors but had a negative community score, indicating potential malicious activity.
- Suspicious processes like chrome.exe and OpenWith.exe were analyzed, with details on their legitimacy and execution paths provided.
- Network actions revealed communication with several IPs, including EC2 instances in Singapore that were flagged for potential scam activities.
- Browser history showed the user downloading the extension, ignoring warnings, and accessing legitimate sites like OpenAI.
- Log investigations indicated outbound connections to potentially malicious hosts and IP addresses, with some flagged by antivirus vendors.
- Containment actions were taken swiftly upon confirming communication with a Command and Control infrastructure.
- Indicators of Compromise (IoCs) such as SHA-256 hash, malicious IPs, domains, and URLs were identified, leading to recommendations for removal, re-imaging, and security enhancements.
- The investigation showcased the detection and response process to a malicious Chrome extension event, emphasizing proactive security measures to mitigate risks.
Read Full Article
13 Likes
Wired
34

Image Credit: Wired
What Satellite Images Reveal About the US Bombing of Iran's Nuclear Sites
- The US bombing of Iran targeted nuclear facilities at Fordow, Natanz, and Isfahan, with significant impact seen at Fordow.
- Satellite images reveal six craters at Fordow, targeting ventilation shafts and support infrastructure, potentially leaving core components intact.
- US military uses massive ordnance penetrators to create shockwaves and damage underground facility without penetrating full depth.
- Bombing campaign aimed at strategic destruction rather than temporary shutdown, raising questions about long-term impact on Iran's nuclear program.
- Uncertainty remains over Fordow's damage extent, with possibilities of nuclear material movement before the attack.
- Iran's nuclear program likely damaged but not eliminated; strategic implications yet to be fully realized.
Read Full Article
2 Likes
Securityaffairs
313
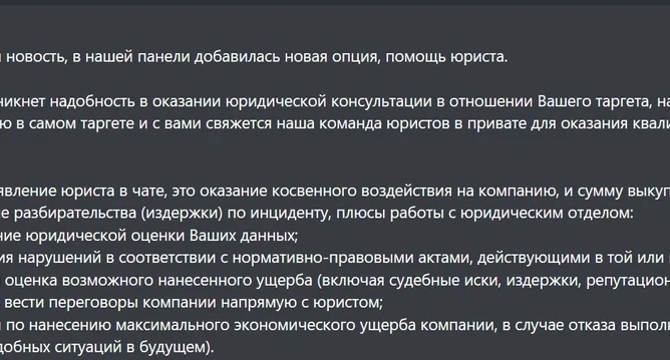
Image Credit: Securityaffairs
Qilin ransomware gang now offers a “Call Lawyer” feature to pressure victims
- The Qilin ransomware group now offers a "Call Lawyer" feature to provide legal support to affiliates and pressure victims into paying, as reported by cybersecurity firm Cybereason.
- Qilin, active since at least August 2022 and gaining attention in June 2024 for attacking a UK governmental service provider, uses double extortion tactics and takes a percentage of ransom payments.
- Affiliates are ordered not to target systems in CIS countries like other ransomware operations.
- Qilin is positioning itself as a full-service cybercrime platform, offering advanced tools, legal support, spam services, and large data storage.
- The "Call Lawyer" feature increases pressure on victims during ransom negotiations by offering legal consultations and introducing legal risks.
- By introducing network spreading and a DDoS option, Qilin demonstrates sophistication and adaptability in various cyberattack scenarios.
- A translation of the ransomware group's text explains how the "Call Lawyer" feature works to increase ransom amounts and apply legal pressure on companies.
- Qualys also highlights the strong operational model and legal support provided by Qilin to clients for successful ransomware payouts.
- The Qilin ransomware group is intensifying its activity, as shown by a heatmap reporting host compromises.
- Organizations are advised to adopt proactive measures to defend against sophisticated threats like Qilin ransomware, as per Qualys' recommendations.
- Qilin ransomware group's strategy includes legal support, incentives, and technology for successful ransom payouts.
- Cybereason's report emphasizes Qilin's emergence as a major ransomware player, offering more than just malware and aiming to lead the next wave of ransomware-as-a-service operations.
Read Full Article
18 Likes
Tech Radar
365

Image Credit: Tech Radar
Kali Linux gets a major upgrade with more than 10 new hacking tools, plus VPN IP extension, great for ethical hackers and pentest pros
- Kali Linux 2025.2 introduces over a dozen new hacking tools and enhancements to improve user experience and platform support.
- Offensive Security aligns Kali Linux with the MITRE ATT&CK framework to enhance hacking functionality.
- The update includes 13 specialized tools for offensive operations targeting complex enterprise environments.
- New tools like azurehound for Azure directory data collection and bloodhound-ce-python indicate a focus on advanced offensive capabilities.
- Additional tools like crlfuzz and donut-shellcode cater to skilled practitioners, enhancing offensive capabilities.
- Kali Linux 2025.2 also introduces prebuilt binaries for tunneling and pivoting, along with tools for enumeration and lateral movement.
- The update features integration with the GNOME VPN IP extension for easy viewing of the VPN IP address.
- Support for GNOME 48, KDE Plasma 6.3 desktop environments, Raspberry Pi OS image compatibility, and Kali NetHunter CARsenal for automotive security analysis are part of the new update.
- While Kali Linux remains a top choice for ethical hacking, users may still consider alternatives with different security focuses.
Read Full Article
22 Likes
Dev
357

Image Credit: Dev
🔒 Dymo has identified a critical vulnerability affecting the Public Prosecution Office of the Sultanate of Oman
- Dymo discovered a critical vulnerability affecting the Public Prosecution Office of the Sultanate of Oman, leading to unauthorized access to email servers used for fraudulent cryptocurrency campaigns.
- The emails appear legitimate as they are sent from genuine institutional addresses, making conventional security filters ineffective and heightening the risk to potential victims globally.
- A previous incident in Ecuador's highest police authority showed a similar vulnerability, emphasizing security weaknesses in governmental organizations across different nations.
- Dymo has reported the vulnerability to the Public Prosecution Office of the Sultanate of Oman and provided recommendations to mitigate the breach and prevent future exploitation.
- The incidents underscore the importance of enhancing protective measures in state organizations to combat escalating cyber threats.
- Keywords: Cybersecurity, Phishing, Fraud, Government, Oman, Ecuador, Dymo, Vulnerability, Responsible Disclosure, Digital Security
Read Full Article
21 Likes
Tech Radar
243

Image Credit: Tech Radar
Hackers could trick users into downloading malware and opening malicious sites using a flaw in Android - here's what you need to know
- A security flaw in Android's notification system allows hackers to deceive users into triggering hidden app actions.
- Research identifies a flaw in how Android processes certain Unicode characters within notifications, leading to misinterpretation of links.
- Invisible or special Unicode characters embedded within URLs can cause Android to interpret visible text and actionable link differently.
- This flaw enables attackers to redirect users to different sites or trigger app actions without user consent.
- Malicious actors can use URL shorteners and trusted-looking text to make attacks less detectable.
- The vulnerability affects major apps like WhatsApp, Telegram, Instagram, Discord, and Slack, as shown through various tests.
- Standard defenses like antivirus software may miss these exploits as attackers manipulate UI behavior.
- Endpoint protection tools are recommended for broader detection based on behavioral anomalies to counter such attacks.
- Users are advised to stay cautious with notifications and links, particularly from suspicious sources or URL shorteners, until a formal fix is deployed.
Read Full Article
14 Likes
Tech Radar
74

Image Credit: Tech Radar
Criminals could pick up your voice through a foot-thick concrete wall, thanks to AI and a flaw in popular laptop microphones - here's what you need to know
- AI can reconstruct speech through concrete using laptop microphones' wiring.
- Laptop mic cables act as antennas, leaking audio through radio harmonics.
- A vulnerability in MEMS microphones enables eavesdropping without compromise or malware.
- Researchers demonstrated reconstructing speech through a 25 cm concrete wall using FM receiver and ML.
- Laptops are vulnerable due to their unshielded wiring turning microphones into antennas.
- Accuracy of up to 94.2% in recognizing spoken digits was achieved.
- Several MEMS microphones from different manufacturers were examined for vulnerabilities.
- STMicroelectronics confirmed that MEMS microphones emit signals leaking data through radio harmonics.
- Experts recommend relocating microphones and shielding wires to mitigate risks.
- Users are advised to invest in antivirus solutions to protect against such privacy breaches.
Read Full Article
4 Likes
Gizchina
21

Image Credit: Gizchina
Urgent Warning: 16 Billion Passwords Leaked: How to Stay Safe
- A significant leak of 16 billion passwords raises concerns about online security and highlights the dangers of password reuse.
- The leaked data is a compilation from various sources and poses a serious threat as cybercriminals can exploit it.
- The risk primarily stems from 'credential stuffing,' where reused passwords grant unauthorized access to multiple accounts.
- Individuals are urged to assess their exposure using tools like 'Have I Been Pwned' and adopt strong, unique, and lengthy passwords.
- Implementing a password manager is recommended to handle multiple complex passwords effectively.
- Enabling Two-Factor Authentication (2FA) provides an additional layer of security against unauthorized access.
- Future security measures like Passkeys, utilizing biometrics, are emerging as a more secure alternative to traditional passwords.
- Despite the alarming nature of password leaks, proactive steps such as these can significantly enhance digital defense.
- Read Gizchina.com for the latest technology news and updates.
- The article focuses on the impact of a massive password leak and offers practical steps to bolster online security.
Read Full Article
1 Like
Dev
257

Image Credit: Dev
Secure Note Manager in React – Part 1: Cryptography with WebCrypto API
- The article discusses building a secure note manager in React that runs in the browser and encrypts data client-side.
- Tech stack includes React for UI, WebCrypto API for cryptographic operations, and IndexedDB for storage.
- The article covers setting up the project, routing with React Router, and configuring the Redux store.
- It focuses on implementing cryptography functions like key derivation with PBKDF2, encryption & decryption with AES-GCM, and SHA-512 hashing.
- Cryptography utilities for exporting keys, salt generation, and encoding data are also discussed.
- The article provides detailed code snippets and explanations for key derivation, encryption, decryption, hashing, and other cryptographic processes.
- Functions are explained step by step with details on inputs, operations, and outputs.
- The article emphasizes secure practices like using random salts, IVs, and encoding data for safe storage.
- The article concludes by highlighting the importance of the cryptographic backbone for a secure note manager.
- In-depth tutorial on building secure note manager with React and WebCrypto API while following best cryptographic practices.
- The article is informative and suitable for web story generation.
Read Full Article
15 Likes
Medium
340

Image Credit: Medium
16 Billion Passwords Leaked: What Happened and How to Protect Yourself
- The recently leaked 16 billion passwords, dubbed "RockYou2024," is a massive compilation from hundreds of data breaches over the past decade.
- This leaked dataset is organized by cybercriminals into a single searchable database, making it easier for exploitation.
- Reusing passwords puts individuals at risk, as hackers can use old leaks to access current accounts.
- Tools like Bitwarden, 1Password, or Dashlane are recommended to manage passwords securely.
- Creating strong passwords is crucial, with examples like L!9zB7#p@4RtXq suggested.
- Adding a second layer of protection with apps like Google Authenticator or Authy is advised.
- Avoid saving passwords in browsers like Chrome or Firefox and opt for password managers instead.
- Encrypted cloud storage is recommended for safely backing up password vaults.
- The leak serves as a reminder to take online security seriously and prompts individuals to audit accounts, set stronger passwords, and protect their digital identity.
- Users are encouraged to visit haveibeenpwned.com to check if their email or password was leaked and change passwords promptly if affected.
Read Full Article
20 Likes
Dev
191

Image Credit: Dev
Web Application Penetration Testing: How to Hack Like a Hacker (Before You Find You)
- Penetration testing, also known as pen testing, simulates attacks on web applications to uncover vulnerabilities before malicious hackers exploit them.
- In 2025, the complexity of the threat landscape necessitates penetration testing to identify security flaws that may not be detected by automated scans.
- Pen testing goes beyond automated vulnerability scanning to emulate real attack scenarios, discover business logic defects, session vulnerabilities, and injection issues.
- Key findings from penetration testing include logically flawed patterns, insecure authentication, poor input sanitization leading to XSS or SQLi, vulnerable dependencies, open APIs, and hidden endpoints.
- Essential techniques for web app penetration testing include reconnaissance, input validation testing for injection flaws, authentication and session testing, access control testing, and business logic testing.
- Common tools used for web app penetration testing include Burp Suite, OWASP ZAP, Nikto, Nmap, SQLmap, and Recon-ng.
- Mistakes to avoid in penetration testing include over-reliance on automated tools, overlooking session and token vulnerabilities, neglecting testing of third-party services, skipping post-exploitation analysis, and lacking test documentation and fix plans.
- The goal of pen testing is not to break an app but to enhance trust, strength, and security to prevent real-world attacks and protect the brand's reputation.
Read Full Article
11 Likes
Livebitcoinnews
292

Image Credit: Livebitcoinnews
CoinMarketCap Removes Malicious Wallet Popup After Security Breach
- CoinMarketCap swiftly removed a malicious wallet pop-up after a security breach.
- The pop-up aimed to trick users into connecting wallets, but no user funds were reported stolen.
- The breach was quickly addressed by CoinMarketCap, with new security measures implemented.
- The compromised feature was traced back to an external partner, leading to a full security check on the platform.
- CoinMarketCap urged users to be cautious and verify wallet links due to vulnerabilities in third-party integrations.
- Security procedures on the platform were enhanced, including increased monitoring and stricter examination of third-party services.
- The incident highlighted the ongoing threat of phishing attacks in the cryptocurrency market.
- Users were advised to be vigilant and verify the authenticity of wallet connection alerts.
- The reaction of CoinMarketCap to the breach was commended for transparency and accountability.
- The incident underscores the importance of strong cybersecurity measures in the digital asset ecosystem.
Read Full Article
17 Likes
For uninterrupted reading, download the app