Cyber Security News
Digit
113

Image Credit: Digit
How to find out if your passwords were compromised in the global data breach
- Researchers have confirmed a massive data breach with up to 16 billion login credentials compromised, potentially by malware.
- The leaked credentials cover various online services like social media, VPN services, and government portals.
- Tech giants like Google, Microsoft, and Meta are pushing users to switch to passkeys due to the breach.
- 16 billion leaked credentials increase the risks of identity theft, account hacking, and financial fraud.
- Users can check if their data was leaked using tools like Have I Been Pwned, Google Password Checkup, F-Secure Identity Theft Checker, Mozilla Monitor, and Microsoft Edge Password Monitor.
- If an account is affected, users should change passwords immediately, log out of all devices, use unique strong passwords, and enable two-factor authentication.
- Saving login credentials in a password manager can help manage multiple passwords securely.
- Checking for compromised passwords and monitoring potential breaches are essential to protect online accounts.
Read Full Article
6 Likes
Hackernoon
267
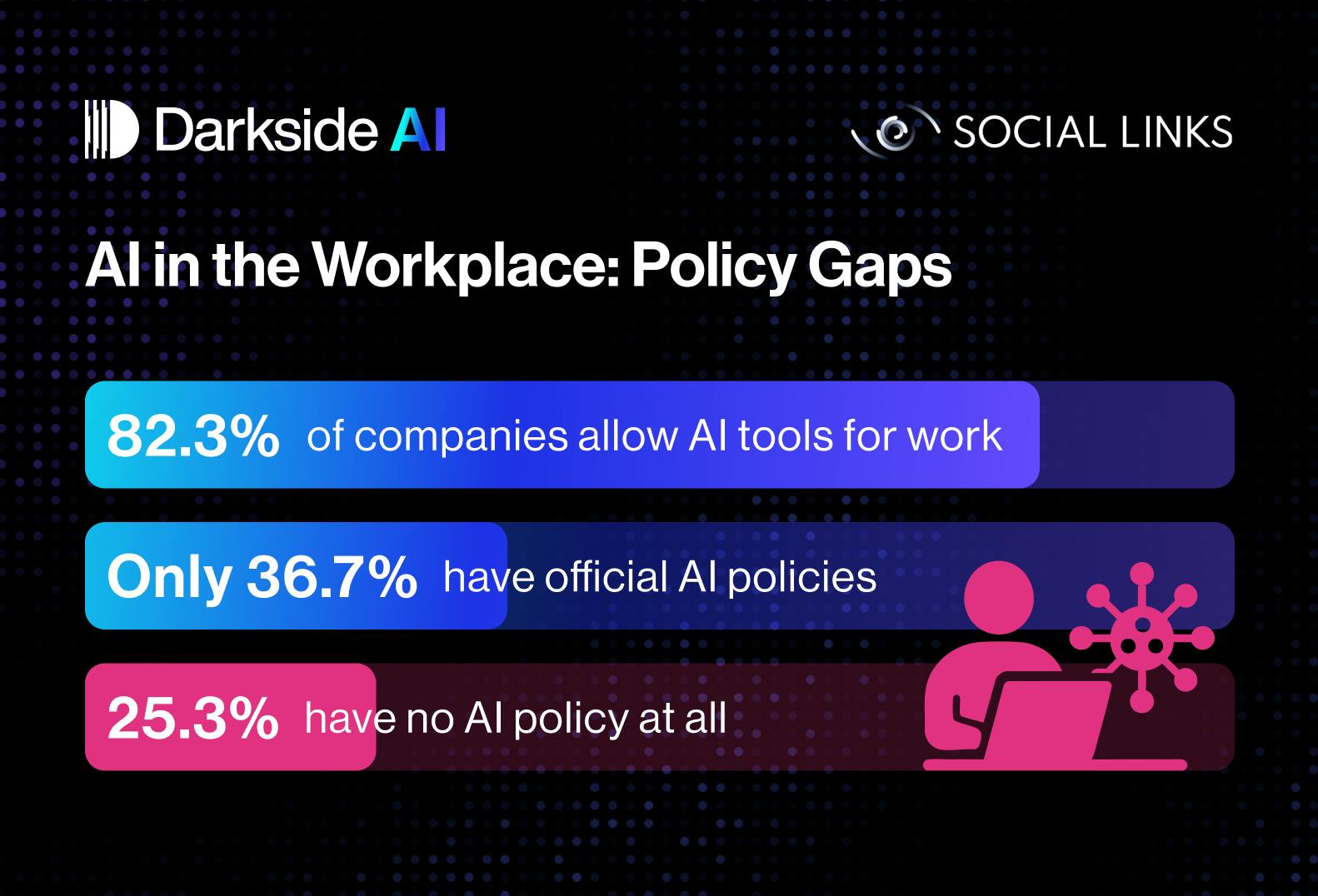
Image Credit: Hackernoon
Business Pros Underestimate AI Risks Compared to Tech Teams, Social Links Study Shows
- A study by Social Links shows a discrepancy between business and technical professionals in recognizing AI risks in cyberattacks.
- Only 27.8% of business professionals see AI-generated fake messages as a top cyber threat, compared to 53.3% of technical experts.
- This gap exposes a vulnerability as business roles are prime targets for AI-driven social engineering and deepfake schemes.
- Finance, IT, HR, and Sales departments are identified as the most vulnerable to cyber threats.
- AI-driven threats such as fake messages and deepfakes are gaining traction alongside traditional risks like phishing and malware.
- Over 60% of employees use corporate accounts for personal purposes, posing a risk for cyber incidents.
- While over 82% of companies allow employees to use AI tools, only 36.7% have a formal policy regulating their use.
- Social Links emphasizes the need for a holistic approach to cybersecurity in the AI era, including human-centric security programs.
- Effective mitigation measures include employee training on safe AI use and the development of internal policies.
- Social Links recently launched the Darkside AI initiative to address risks posed by advanced AI-driven threats.
- Social Links is a global provider of open-source intelligence solutions, supporting various sectors across 80+ countries.
Read Full Article
16 Likes
Securitysales
0

Image Credit: Securitysales
Civitas Group Brings iOT365 Cybersecurity to Eastern Europe
- iOT365 and Civitas Group have partnered to introduce the iOT365 cybersecurity platform into Romania and other Eastern European and Balkan markets.
- The collaboration allows Civitas to offer advanced cybersecurity protection for physical security systems and a full suite of OT and IoT cybersecurity services.
- iOT365's CEO, Alex Tartakovsky, expressed excitement about expanding into these markets through the partnership with Civitas.
- The partnership will provide iOT365's cybersecurity platform to Civitas for installation, management, and monitoring services.
- Civitas' clients will benefit from enhanced cybersecurity protection for physical security infrastructure like cameras and access control devices.
- The partnership with iOT365 enables Civitas to offer comprehensive OT and IoT cybersecurity solutions to existing and new clients.
- Civitas aims to address the convergence of physical and digital security by leveraging iOT365's cybersecurity platform.
- Rene Pasculescu, CEO of Civitas, highlights the significance of the partnership in providing holistic security solutions.
- The collaboration is expected to bring unparalleled protection for clients' security systems and connected devices in the region.
- The announcement was made on Security Sales & Integration and involves John Nemerofsky from Sage Integration sharing best advice.
Read Full Article
Like
BGR
253

Image Credit: BGR
16 billion logins exposed in mysterious, gigantic data breach
- Researchers have uncovered a massive data breach with over 16 billion username and password combinations.
- This breach is the second largest in history, trailing only a 2024 breach that had 26 billion logins.
- The data in the breach is still relevant to attackers and contains additional elements like cookies that could grant access to accounts.
- Hackers often use stolen credentials to conduct malware campaigns, steal personal information, and exploit financial gains.
- Some users reuse the same login details across multiple websites, increasing their vulnerability to attacks.
Read Full Article
15 Likes
Medium
122

Image Credit: Medium
The Daily Tech Digest: 20 June 2025
- The field of Artificial Intelligence and Machine Learning is experiencing dynamic expansion with advancements in model evaluation and application across diverse sectors.
- Nvidia plays a strategic role in shaping the AI ecosystem through startup investments beyond hardware.
- AI residencies are changing the conversation around artificial art, legitimizing AI-generated art in the artistic community.
- Specialized AI tools are assisting overworked college counselors in personalized educational guidance for students in the US.
- AWS showcases its role in industry transformation through AI innovations used by global leaders like BMW and Epic Games.
- Microsoft Azure AI is practically applied in the retail sector, helping customers with everyday decisions like meal planning.
- Cybersecurity challenges persist with a record DDoS attack, new Linux root exploits, and North Korean hackers using deepfakes in Zoom scams.
- Ransomware incidents like Krispy Kreme's data breach highlight the critical need for robust cybersecurity defenses across sectors.
- Cisco and Atlassian patch high-severity vulnerabilities, emphasizing the importance of prompt security updates for system protection.
- The intersection of technology and cyber threats raises questions about effective measures for online harassment and data protection.
Read Full Article
7 Likes
Tech Radar
83

Image Credit: Tech Radar
World's largest AI chip maker hit by crypto scam - Cerebras says token isn't real, so don't fall for it
- The AI chip maker Cerebras had its official X account hacked to promote a fake cryptocurrency scam involving a coin named $CEREBRAS.
- Despite suspicions from industry experts and the public, Cerebras confirmed the scam and clarified that it did not launch any token.
- Cerebras regained control over its X account and warned people to be cautious of cryptocurrency scams.
- Cerebras recently achieved record-breaking LLM inference speeds with the Llama 4 Maverick 400B model, outperforming Nvidia.
- CEO Andrew Feldman denied involvement in the scam and reiterated that Cerebras does not endorse any cryptocurrency or token.
- Director James Wang also confirmed that Cerebras is not launching a token and urged people not to click on any suspicious links.
- The company's objective is to reclaim control of the account and prevent further fraudulent activities.
- Cerebras secured a $45 million US government contract with Ranovus to enhance inter-chip connections.
Read Full Article
5 Likes
TechBullion
135

Image Credit: TechBullion
Beyond Firewalls: Why the Human Layer Is the Weakest Link in Cyber Defense
- 95% of cybersecurity breaches are caused by human error, showcasing the vulnerability within the human layer of cyber defense.
- Traditional cybersecurity methods focusing on technology overlook the fact that most attacks target people, not machines.
- Human-centered cybersecurity emphasizes education, behavior change, and awareness to strengthen defenses against attacks.
- Human error, driven by emotions like fear and urgency, often leads to successful cyberattacks through social engineering.
- Phishing simulations, like those offered by ClearPhish, are essential to prepare employees to identify and resist emotional manipulation in attacks.
- ClearPhish introduces Emotional Vulnerability Index Scoring to measure susceptibility to phishing attacks based on emotional behavior patterns.
- Utilizing story-based micro modules, ClearPhish creates engaging and realistic scenarios for cybersecurity training that resonate with employees.
- By integrating cybersecurity training into organizational culture and focusing on human vulnerability, ClearPhish helps organizations strengthen their defense against cyber threats.
- ClearPhish differentiates itself by combining behavioral psychology, realism, and continuous training to address the human element of cybersecurity risks.
- A human-first approach to cybersecurity, emphasizing emotional intelligence and ongoing training, can empower employees to be a strong defense against evolving cyber threats.
Read Full Article
8 Likes
Medium
35

Secure Storage in iOS with Swift: A Practical Guide
- Mobile devices contain sensitive data, highlighting the importance of secure storage in iOS apps.
- Apple offers the Keychain for securely storing sensitive information like passwords and tokens.
- The Keychain is encrypted and designed to safeguard secrets even if the device is compromised.
- Examples demonstrate how to save passwords and manipulate Keychain items for retrieval, update, or deletion.
- Pro Tip: Consider using wrappers like KeychainAccess for a more user-friendly API.
- For storing large files like PDFs or images, utilize the file system with secure practices.
- iOS offers file encryption options to secure files, allowing access only when the device is unlocked.
- For more advanced control, such as encrypting files before storage, employ encryption libraries like RNCryptor.
- Avoid hardcoding encryption keys in apps; store them securely, preferably in the Keychain.
- Different storage methods (Keychain, File Protection, Manual Encryption) cater to various data types with varying security levels.
- Implementing secure storage practices in Swift apps safeguards users, app reputation, and provides peace of mind.
- No excuses for insecure storage with straightforward tools provided by Apple for iOS app developers.
- Readers are encouraged to ask questions or share tips in the comments.
Read Full Article
2 Likes
Medium
337

Image Credit: Medium
AI in Cybersecurity: The War on Two Fronts
- AI models in cybersecurity can detect zero-day attacks, lateral movement, and insider threats.
- Automated SOAR platforms enhance incident response by accelerating triage and containment.
- AI assists in threat intelligence by summarizing incidents and digesting open-source intel.
- Predictive analytics are used for proactive threat hunting to identify early-stage indicators of compromise.
- Companies like Google Chronicle, Microsoft Sentinel, and Darktrace leverage AI in cybersecurity.
- Deepfakes and AI-powered techniques are used in hyper-targeted phishing campaigns.
- AI helps threat actors model user behavior to evade detection and launch targeted attacks.
- Recalibrating employee awareness training is recommended to include AI-related modules.
- AI-driven upgrades in software and hardware help in AI-aware cybersecurity measures.
- Continuous red teaming with AI involves simulating adversarial AI scenarios to stress test cybersecurity.
- Challenges include cross-border AI model usage, deepfake mitigation, and ensuring AI decisions are audited.
- Solutions involve deploying AI endpoint agents and ML-based deception technology.
- AI-vs-AI simulations are used to test infrastructure against evolving threats.
- Emphasis on employee training and AI-aware upgrades in cybersecurity are crucial for cyber resilience.
- Threat actors are utilizing AI to not only hack systems but also manipulate human behavior at scale.
- AI explainability clauses and understanding AI decisions are key considerations in cybersecurity measures.
Read Full Article
20 Likes
Tech Radar
113

Image Credit: Tech Radar
Is crime turning digital? Almost all Brits believe cybercrime is more of a risk - here's how to stay safe
- A survey by Avast and Neighbourhood Watch reveals that 92% of Brits see cybercrime as a significant threat.
- Approximately 1 in 3 respondents admit to falling victim to online scams, resulting in many experiencing financial loss.
- Phishing scams have surged by 466% quarter-on-quarter, attributed to criminals using AI to conduct more frequent and sophisticated social engineering attacks.
- Fraudsters can now create campaigns quickly using AI tools, which previously required days of work.
- Brits are losing more money to cybercrime, with 59% of victims losing up to £500.
- Women tend to lose under £500, while men are more likely to suffer higher losses ranging from £501 to £2000 and beyond.
- Being vigilant online is crucial as cybercriminals utilize advanced tactics and create convincing scams.
- Staying cautious with unexpected communications, especially those prompting immediate action, is key in avoiding engineering attacks.
- Individuals are advised to be cautious with requests from supposed family or friends due to deep-fake technologies that can clone voices and images.
- Avoid clicking on links or attachments from untrusted sources and follow guidelines for creating secure passwords.
- Recommendations for malware removal software, AI tools, and combating identity fraud attacks using AI are also provided.
Read Full Article
6 Likes
TronWeekly
341

Image Credit: TronWeekly
Crypto Users at Risk: 16 Billion Leaked Credentials Raise Major Concerns
- Over 16 billion credentials have been leaked, exposing crypto owners to cyberattacks.
- Data from Apple, Google, and Facebook was compromised, risking digital asset theft.
- Users are advised to update passwords, enable two-factor authentication, and secure recovery phrases.
- A report by Cybernews revealed 30 datasets from major online services had been leaked, exposing users to security threats.
- The breach included records from tens of millions to over 3.5 billion per data set, totaling 16 billion revealed credentials.
- Most data was exposed by unsecured instances and poses a risk of exploitation by cybercriminals.
- The leaked information includes records from Apple, Facebook, Google, GitHub, and Telegram, raising concern in the crypto community.
- Hacked credentials could lead to targeted account access, potentially granting cybercriminals access to private keys and digital assets.
- Vulnerabilities highlighted by the breach include password reuse and weak authentication methods, exposing wallets to risk.
- Potential cyberattacks against crypto platforms may increase due to the leak, prompting exchanges to enhance security measures.
- Crypto users are urged to update passwords, utilize two-factor authentication, and safeguard recovery phrases.
- The breach underscores the need for improved security in the cryptocurrency sector, with analysts advising caution and prompt action from owners.
- The leak may result in heightened cyberattack activity against crypto platforms, emphasizing the importance of securing assets.
- Users should remain vigilant and take necessary steps to protect their wallets and assets in response to the security threat.
- ASIC has banned a financial adviser over a $14.8 million crypto scam fraud, highlighting security concerns in the industry.
Read Full Article
20 Likes
Securityaffairs
96

Image Credit: Securityaffairs
Linux flaws chain allows Root access across major distributions
- Researchers discovered two local privilege escalation flaws that could let attackers gain root access on systems running major Linux distributions.
- Qualys researchers found two vulnerabilities that can be exploited to escalate privileges to gain root access on Linux systems.
- The vulnerabilities identified are CVE-2025-6018 affecting *SUSE 15's PAM and CVE-2025-6019 affecting libblockdev via udisks.
- CVE-2025-6018 enables unprivileged local user impersonation to access machine actions usually reserved for physical users.
- CVE-2025-6019 in libblockdev through udisks allows users to escalate their access to root privileges.
- When combined, these vulnerabilities allow unprivileged attackers full control over a system.
- The link between the flaws enables an unprivileged attacker to achieve full root access easily.
- Recent exploits, like those using the 'allow_active' user loophole, highlight the severity of related vulnerabilities.
- The vulnerabilities impact systems such as Ubuntu, Debian, and FQualys.
- Qualys created proof-of-concept exploits to demonstrate the vulnerabilities on affected operating systems.
- Users are advised to apply security patches or adjust Polkit rules for temporary mitigation.
- The flaws represent a significant risk due to the potential for unprivileged attackers to gain root access.
- The combination of vulnerabilities poses a serious threat to Linux systems and requires immediate attention from users and administrators.
- Addressing the vulnerabilities promptly is crucial to prevent unauthorized access to sensitive systems.
- Overall, the flaws highlight the importance of maintaining up-to-date security measures to protect against potential exploits.
- Follow security updates on Twitter: @securityaffairs, Facebook, and Mastodon for the latest information.
- Author: Pierluigi Paganini (SecurityAffairs - hacking, Linux)
Read Full Article
5 Likes
Tech Radar
657

Image Credit: Tech Radar
Mystery of M&S hack deepens as TCS claims none of its systems were compromised
- Tata Consultancy Services (TCS) claims none of its systems or users were compromised in the cyberattack on Marks and Spencer (M&S).
- M&S suffered a major cyberattack in 2025, allegedly linked to compromised workers at TCS.
- TCS, a third-party supplier for M&S for over a decade, secured a $1 billion contract in 2023 to modernize M&S' legacy technology.
- TCS is conducting a full investigation into its potential role in the cyberattack.
- M&S estimates the attack could cost around 300 million in lost operating profit.
- Hackers from the DragonForce collective demanded payment in a mocking email to M&S CEO Stuart Machin.
- M&S has not confirmed paying a ransom but admitted some customer data, excluding sensitive payment details, was stolen.
- TCS has not responded to inquiries for comment on the matter.
Read Full Article
5 Likes
Pymnts
91

Image Credit: Pymnts
Payment Glitches Stall Brazil’s Mobile Shopping Surge
- Brazilian consumers are highly engaged in digital shopping, with a majority using smartphones for retail purchases.
- 61% of consumers in Brazil made their latest retail purchase using a phone, indicating a 10% increase since 2022.
- Consumers in Brazil lead in using phones for in-store shopping, surpassing traditional economies like the US and UK in the shift from computers to phones for digital shopping.
- Despite high digital engagement, 99% of Brazilian consumers faced payment-related issues during their latest retail purchase.
- Payment processing errors and friction, with declined payments being common, were reported by 67% of Brazilian shoppers.
- Brazilian shoppers were 1.5 times more likely than the global average to manually enter payment information for online purchases, adding to friction.
- The use of stored credentials for online purchases was lower in Brazil compared to the global average, with concerns about data security and trust in merchants.
- With a gap in cross-channel shopping capabilities, 33% of Brazilian shoppers wanted to use such features but found them unavailable.
- Merchants in Brazil are not fully meeting consumer demand for cross-channel shopping capabilities, with only 45% offering such features.
- Pervasive payment friction in Brazil presents an opportunity for financial services and payments professionals to invest in technologies for seamless payment processing.
Read Full Article
5 Likes
TechJuice
302

Image Credit: TechJuice
Hacked by Ads? WordPress Sites Spreading Malware to Millions!
- WordPress malware is becoming a significant threat as hackers use legitimate ad networks to distribute malicious payloads.
- Research uncovered coordination between hacked WordPress sites and ad networks like Los Pollos and RichAds.
- The malware delivery mechanism impacts regular browsing experiences.
- Infoblox identified the VexTrio traffic distribution system used to redirect visitors to malware download pages.
- Infected WordPress sites display fake captchas that lead to push notification subscriptions.
- Users are exposed to scam links and drive-by downloads through push notifications.
- Ad networks such as Partners House and BroPush are central to VexTrio's operations.
- These networks profit by promoting gift card scams, phishing sites, and malware installers.
- Over 40 percent of hacked WordPress sites redirect users to malicious destinations through these networks.
- Adtech companies' vetting processes may expose hackers to detection by authorities.
- Site owners are advised to check for suspicious plugins, DNS entries, and JavaScript.
- Visitors should avoid interacting with suspicious pop-ups and captcha prompts requesting notification access.
- Strengthened endpoint security and partnership between adtech firms and cybersecurity experts are recommended to combat WordPress malware.
- The post was published on TechJuice.
- The news article qualifies for web story generation due to its relevance and potential for user engagement.
Read Full Article
18 Likes
For uninterrupted reading, download the app