Cyber Security News
TechJuice
290

Image Credit: TechJuice
Hackers and Gamers Fall Victim to Backdoored GitHub Repositories
- A hacker inserted backdoors into over 130 GitHub repositories, targeting gamers and aspiring hackers with cheat tools and exploit kits.
- Security researchers found malicious code disguised as safe and frequently updated repositories, with nearly 60,000 fake commits to appear credible.
- The backdoors used PreBuildEvent scripts that downloaded malware upon code compilation, including trojans, RATs, and password stealers.
- Experts warn users to verify open-source code, avoid running unfamiliar scripts on primary machines, and use sandboxed environments when testing suspicious tools to combat the growing threats in the open-source ecosystem.
Read Full Article
17 Likes
Dev
4

Image Credit: Dev
Vite File Read Vulnerability Exposed (CVE-2025-30208)
- A critical Vite file read vulnerability (CVE-2025-30208) was disclosed in March 2025, allowing attackers to read sensitive files from the host server.
- The vulnerability stems from how Vite handles certain query parameters, enabling attackers to access files outside the allowed directory scope.
- The impact includes arbitrary file read on the host machine, potential credential leakage, and a severity level classified as high.
- To address the vulnerability, users are recommended to upgrade to patched versions immediately or follow temporary mitigations if unable to upgrade yet.
Read Full Article
Like
Dev
187

Image Credit: Dev
Bridging Physical and Digital Risk: Applying Marine Safety Lessons to Tech-Driven Projects
- The modern project manager faces a challenge as technology advances quickly while risks in critical infrastructure and safety-sensitive environments remain complex.
- Lessons from maritime engineering like Failure Mode and Effects Analysis (FMEA), compliance culture, redundancy for resilience, incident drills, and stakeholder visibility can benefit tech-driven projects.
- Applying principles from marine safety can help tech projects in embedding structured risk analysis, compliance requirements, redundancy planning, incident response drills, and clear stakeholder alignment.
- By combining insights from marine safety practices with tech initiatives, a balance between innovation and accountability can be achieved, leading to the development of more trustworthy and resilient digital systems.
Read Full Article
11 Likes
Dev
35

Image Credit: Dev
Lockin Company and AFI Sign MOU for Cooperation in the Game Industry
- Mobile app security global service company Lockin Company and AFI signed an MOU for cooperation in the game industry.
- Lockin Company offers mobile app security technologies through LIAPP, while AFI provides game server solutions through BACKND.
- The agreement aims to promote joint growth in the game industry by leveraging the strengths of LIAPP and BACKND.
- The cooperation includes supporting game developers in security and server services, expanding the developer network, and improving game industry data analysis and security services.
Read Full Article
2 Likes
Medium
125

Image Credit: Medium
Cyber Threat Analyzer Using LLMs and Cloud
- The project is a web app where users can upload .txt, .log, or .pdf files for cyber threat analysis using LLMs and cloud technology.
- It utilizes AI, specifically LLMs like BART, to understand and analyze unstructured log text to extract valuable insights.
- Each IP address from the logs is evaluated to determine an abuse score ranging from 0 to 100, with scores above 50 indicating potential threats.
- The tool boasts user-friendly features such as easy upload functionality, AI-driven analysis, a beginner-friendly interface, and the integration of LLMs and threat intelligence.
Read Full Article
7 Likes
Dev
295

Image Credit: Dev
HellRush: Building a Python-Based DDoS Simulation Toolkit for Security Education
- HellRush is an open-source educational toolkit written in Python that simulates DDoS attack vectors and includes network reconnaissance tools for security professionals and students.
- The toolkit addresses the gap between theoretical knowledge and practical application in cybersecurity education without ethical and legal challenges by offering a controlled environment for learning.
- HellRush includes a Network Reconnaissance component for domain to IP resolution and port scanning, as well as a DDoS Simulation Engine with six attack vectors like UDP Flood, SYN Flood, ICMP Flood, HTTP Flood, DNS Amplification, and Slowloris.
- The toolkit is implemented in pure Python without external dependencies, uses multithreading for realistic simulations, features real-time animation for attack progress, and emphasizes ethical usage with clear documentation and warnings.
Read Full Article
17 Likes
Securityaffairs
232

Image Credit: Securityaffairs
Over 950K weekly downloads at risk in ongoing supply chain attack on Gluestack packages
- A supply chain attack targeted NPM, compromising 16 popular Gluestack 'react-native-aria' packages with over 950K weekly downloads.
- The attack involved injecting malicious code with Remote Access Trojan (RAT) capabilities into packages' files, affecting 16 out of 20 packages.
- Approximately 960,000 weekly downloads were affected by the compromised packages, and researchers believe the same threat actors were behind a previous attack on the 'rand-user-agent' package.
- Aikido Security attempted to notify Gluestack about the ongoing supply chain attack but has not received a response yet, urging users to stay updated on the situation.
Read Full Article
14 Likes
Dev
268

Image Credit: Dev
🔐 June: Password Management Month – Strengthen Your Digital Locks
- June is Password Management Month, emphasizing the importance of strong digital locks.
- Passwords remain crucial for accessing systems and apps, making password security essential.
- Best practices include using passphrases, avoiding password reuse, enabling MFA, and securely storing passwords.
- Tools like Bitwarden, HaveIBeenPwned, and built-in options like Google Password Manager help improve password security.
Read Full Article
16 Likes
Securityaffairs
201

Image Credit: Securityaffairs
Security Affairs newsletter Round 527 by Pierluigi Paganini – INTERNATIONAL EDITION
- Security Affairs newsletter Round 527 by Pierluigi Paganini – INTERNATIONAL EDITION
- 4 billion Chinese user records leaked in the largest known data breach. Fortinet flaws exploited to deploy Qilin ransomware. Russia-linked threat actors target Ukraine with PathWiper wiper. U.S. offers $10M bounty for RedLine malware info.
- Multiple cyber attacks reported worldwide. U.S. seizes criminal marketplace domains. Ransomware gang claims responsibility for Kettering Health hack. Cyber criminals defraud Hedera Hashgraph network users. Malware exploits and vulnerabilities identified.
- Intelligence and Information Warfare updates include Ukraine hacking Tupolev and DOJ accusations against Chinese researchers. Cybersecurity incidents such as Victoria's Secret security breach and largest data leak of 4 billion user records.
- AI and cybersecurity advancements highlighted in EU initiative and increase in cyber attacks with AI involvement. Ongoing developments in digital certificate security and threat actor collaboration.
Read Full Article
12 Likes
Arstechnica
147

Image Credit: Arstechnica
Cybercriminals turn to “residential proxy” services to hide malicious traffic
- Gray market services like bulletproof hosts have been popular among cybercriminals for maintaining web infrastructure anonymously.
- Law enforcement crackdowns on bulletproof hosts have pushed cybercriminals towards using residential proxy services to hide malicious traffic.
- Some service providers are now offering purpose-built VPNs and proxies to rotate and mask customer IP addresses, making it difficult to distinguish between legitimate and malicious traffic.
- While the technology of using proxies is not new, the shift towards using them by cybercriminals has been significant in the last couple of years.
Read Full Article
8 Likes
Medium
35

Open-source AI models are revolutionising cybersecurity, powering everything from scam/fraud…
- Nation-states and sophisticated threat actors can compromise cybersecurity by poisoning widely used open-source AI models, creating blind spots in critical infrastructure and government agencies.
- Two categories of attacks on AI models are pre-training attacks involving embedding malicious data during training and post-training attacks executed after the model is deployed.
- Examples of pre-training attacks include Model Poisoning, where tainted data trains the AI to ignore certain attack signatures, and Adversarial Evasion, where crafted inputs exploit model vulnerabilities.
- Post-training attacks involve reverse-engineering detection capabilities and exploiting predictable blind spots in the model, highlighting the importance of rigorous adversarial testing before integrating open-source AI into security solutions.
Read Full Article
2 Likes
Medium
0

Fully Homomorphic Encryption (FHE) & AI & EU Privacy Regulations: Limitations and Opportunities in…
- Fully Homomorphic Encryption (FHE) is seen as a promising solution for balancing data privacy and threat intelligence sharing.
- Challenges faced in implementing FHE for real-time scam prevention include AI compatibility limitations and performance bottlenecks.
- AI Compatibility Limitations: FHE struggles with nonlinear operations and scalability of encrypted search, adding computational overhead.
- Performance Bottlenecks: FHE operations are significantly slower than plaintext equivalents and impractical for large models, hindering real-time use cases.
Read Full Article
Like
Medium
380

Image Credit: Medium
IPv4 Address Classes Explained: A Comprehensive Guide to Class A, B, C, D, and E
- IPv4 addresses are classified into five classes - A, B, C, D, and E, based on their first few bits.
- Class A addresses are designed for large networks with thousands or millions of devices.
- Class B addresses are suitable for medium to large-sized organizations like universities or mid-size businesses.
- Class C addresses are built for small networks such as home users, small offices, or local businesses.
Read Full Article
22 Likes
Medium
53
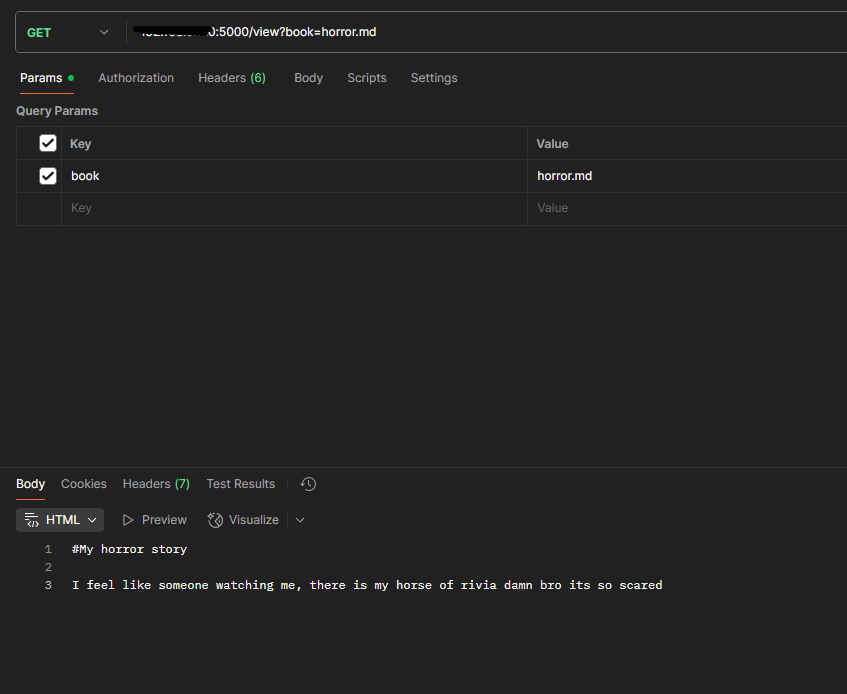
Image Credit: Medium
Building a CTF Lab with LFI bug vulnerability using ExpressJS
- Building a Capture The Flag (CTF) Lab with Local File Inclusion (LFI) bug vulnerability using ExpressJS.
- Testing LFI bug vulnerability with requests like /view?q=../../../../../etc/passwd.
- Combining the LFI bug with the interface, creating a simple page listing different books.
- Successfully resolving issues with rendering packages, fixing errors, and demonstrating the working LFI bug.
Read Full Article
3 Likes
Dev
104

Image Credit: Dev
Safe Data Practices for AI Training & Inference | AI Security series
- AI Security series is focusing on safe data practices for AI training and inference, emphasizing the importance of data security in building trustworthy AI systems.
- Data plays a crucial role in AI, where threats like training data leaks, data poisoning, inference-time attacks, and logging leaks can compromise the system's integrity.
- Best practices include anonymizing user data, validating and sanitizing inputs, limiting memorization, versioning and auditing datasets for training, and implementing input filtering, token limits, response monitoring, and data logging precautions for inference.
- Tools like Presidio, Cleanlab, TextAttack, Datasette, along with suggestions for fine-tuning with user support tickets and custom data guards for pipelines, can enhance data security practices in AI applications.
Read Full Article
6 Likes
For uninterrupted reading, download the app