Cyber Security News
Silicon
44
Image Credit: Silicon
The Common Challenges of API Development and How to Overcome Them
- APIs serve as the backbone of modern software development, enabling applications to interact and share data efficiently.
- Challenges in API development include legacy system integration, security vulnerabilities, and complex data manipulation.
- Key challenges include meeting user needs, ensuring security, optimizing performance, handling error responses, and ensuring cross-system compatibility.
- Developing intuitive and functional APIs with clear documentation and regular testing is crucial to meeting user requirements.
- Security measures such as OAuth2 authentication, encryption, and regular auditing are essential to protect APIs from security threats.
- Optimizing API performance involves caching data, efficient database queries, pagination, and scalable infrastructure.
- Effective error handling with standardized status codes and descriptive error messages is vital for user experience.
- API design should focus on flexibility and compatibility with different systems, utilizing widely accepted standards like JSON or XML.
- As technology advances, APIs will continue to play a critical role in driving innovation, improving efficiency, and enabling personalized user experiences.
- Developers need to embrace best practices, address common challenges, and stay updated on evolving regulations to harness the full potential of APIs.
- The future of APIs holds endless opportunities for enabling real-time data-driven applications and facilitating seamless interactions across various platforms.
Read Full Article
2 Likes
Global Fintech Series
255
Image Credit: Global Fintech Series
Why Distributed Ledger Technology Is More Than Just a Buzzword
- The surge of Bitcoin in 2017 brought distributed ledger technology (DLT) into mainstream consciousness, showcasing its transformative potential.
- DLT is not merely about volatile crypto markets but an architectural innovation for data structuring and sharing across decentralized networks.
- It consists of pillars like data entry structure, inter-node communication rules, and consensus mechanisms ensuring data integrity.
- In fintech, DLT eliminates intermediaries by distributing ledgers across a network, enhancing transparency, reducing friction, and boosting security.
- DLT enables decentralized consensus, whether through permissioned systems for enterprises or permissionless systems like Bitcoin.
- Key traits of DLT include distributed architecture, peer-to-peer communication, tamper resistance, consensus mechanisms, and cryptographic security.
- DLT is crucial for financial inclusion, as evidenced by initiatives like the Better Than Cash Alliance focusing on DLT-based payment projects.
- DLT is being used in real-world applications to help underserved populations access financial services, underscoring its potential for large-scale impact.
- Transparency in DLT is a deliberate design choice, not automatic, and efficiency and security of DLT systems depend on contextual factors.
- While DLT offers benefits like tamper resistance, challenges like energy costs in certain models and vulnerabilities in connected systems must be considered.
Read Full Article
15 Likes
Medium
273

Building a proactive incident response plan with AI tools
- AI tools for incident response can detect anomalies before they escalate into major issues, such as spotting insider data misuse based on unusual user behavior.
- These AI systems adapt and can trigger actions based on various unusual events like spikes in traffic or unrecognized logins, enhancing cybersecurity measures.
- To maximize the effectiveness of AI, it should be integrated into a comprehensive incident response plan with automation, playbooks, and clear communication protocols for faster and more confident responses.
- The goal of a proactive incident response plan with AI is to reduce reaction time and enhance clarity in anticipating threats, emphasizing the importance of incorporating AI into response workflows for automated containment and faster forensics.
Read Full Article
16 Likes
Medium
323

Image Credit: Medium
The GRC Career Path
- The GRC career path involves different stages from entry-level positions to executive roles, focusing on risk management, regulatory compliance, and corporate governance.
- The typical stages in the GRC career path include gathering data and learning, leading projects and teams, managing priorities and turning goals into actions, influencing strategy and decision-making, and balancing risk and innovation at the executive level.
- Key factors for success in the GRC field include continuous learning, building trust and reputation within the industry, communicating risks effectively, and focusing on skill development and alignment with personal values.
- To advance in the GRC career, individuals are advised to map their current stage, focus on skill development, seek guidance from mentors, and continue learning to stay updated on regulations and industry trends.
Read Full Article
19 Likes
Hackernoon
40

Image Credit: Hackernoon
Get Real-Time Server Security Alerts in Microsoft Teams with This Fail2Ban Integration
- A recent solution has been developed to bridge Fail2Ban security monitoring with Microsoft Teams notifications, providing real-time alerts with detailed information about potential attackers.
- The integration offers features like real-time notifications sent directly to Teams channels, geographical information about blocked IP addresses, easy configuration, customizable alerts for different services, and detailed threat analysis with IP geolocation data.
- It consists of two main components: teams-geo.conf (Fail2Ban action configuration file) and teams-notify.sh (notification script that formats and sends alerts to Teams).
- Users can set up this integration by following the provided installation steps, which include prerequisites, installation components, configuring Teams webhook, adding to jail configurations, and testing it out to monitor server security events effectively.
Read Full Article
2 Likes
Dev
336

Image Credit: Dev
Critical RCE Vulnerabilities Found in DataEase (CVE-2025-49001/49002)
- Critical Remote Code Execution (RCE) vulnerabilities (CVE-2025-49001/49002) have been discovered in DataEase, an open-source data visualization platform.
- The vulnerabilities allow unauthenticated RCE and authentication bypass, posing a significant risk to internet-facing deployments.
- CVE-2025-48999 enables attackers to inject malicious JDBC parameters, CVE-2025-49002 allows code execution through JDBC parameters, and CVE-2025-49001 permits unauthorized access via JWT tokens.
- Recommended mitigations include using WAF/Firewall, restricting outbound access, and upgrading to DataEase v2.10.10 to fix the vulnerabilities.
Read Full Article
20 Likes
Siliconangle
381

Image Credit: Siliconangle
Rubrik delivers strong results on surging cloud and subscription revenue
- Rubrik Inc. exceeded expectations for its fiscal 2026 first quarter with an adjusted earnings per share loss of 15 cents and revenue of $278.5 million.
- The strong revenue growth was driven by subscription revenue, which increased by 54% year-over-year to $266.8 million.
- Rubrik's annual recurring revenue reached $1.181 billion, up 38%, and cloud ARR rose by 60% to $972 million.
- The company announced various business highlights, including the expansion of cyber resilience capabilities, support for Oracle Cloud Infrastructure, and a strategic collaboration with Rackspace Technology Inc. for the Rackspace Cyber Recovery Cloud.
Read Full Article
22 Likes
Securityaffairs
332

Image Credit: Securityaffairs
U.S. CISA adds Google Chromium V8 flaw to its Known Exploited Vulnerabilities catalog
- The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added Google Chromium V8 Out-of-Bounds Read and Write Vulnerability, CVE-2025-5419, to its Known Exploited Vulnerabilities catalog.
- Google released out-of-band updates to address three vulnerabilities in its Chrome browser, including CVE-2025-5419 that is actively exploited.
- The vulnerability in V8 JavaScript engine in Google Chrome can trigger a heap corruption via a crafted HTML page.
- CISA orders federal agencies to fix the vulnerabilities by June 26, 2025, and private organizations are advised to address vulnerabilities in their infrastructure.
Read Full Article
20 Likes
Amazon
49

Image Credit: Amazon
Many voices, one community: Three themes from RSA Conference 2025
- RSA Conference 2025 featured 730 speakers, 650 exhibitors, and 44,000 attendees discussing topics like agentic AI, cryptography, and public-private collaboration.
- The conference highlighted the potential of agentic AI in augmenting decision-making and the need to balance its risks and opportunities.
- AI agents, utilizing large language models, are predicted to see significant enterprise adoption by 2028, presenting both opportunities and security challenges.
- Speakers addressed AI risks, emphasizing the importance of security posture assessment and diverse protection layers.
- Encryption discussions focused on passwordless technology and post-quantum encryption, urging organizations to be proactive in adopting secure practices.
- Collaboration between public and private sectors was emphasized for enhancing security, with a call for continued partnership to combat cyber threats collectively.
- Talks at the conference detailed examples of industry cooperation in identifying and disrupting cybercriminal activities, showcasing the value of shared intelligence and resources.
- The importance of working together to improve cybersecurity resilience was highlighted, reiterating that security is a collective effort.
- The event reinforced the idea that addressing evolving challenges and building resilience requires collaborative efforts and a shared perspective across the industry.
- Sessions also delved into topics like the changing role of the CISO, women in cybersecurity, and cloud security, showcasing the diverse discussions at the conference.
- The collective learning and engagement at RSA Conference 2025 underscored the criticality of unity in combating cyber threats and fostering a secure digital environment.
Read Full Article
2 Likes
Unite
431

Image Credit: Unite
Security Teams Are Fixing the Wrong Threats. Here’s How to Course-Correct in the Age of AI Attacks
- Cyberattacks now involve AI, leading to faster attacks like polymorphic malware and automated reconnaissance that security teams struggle to combat effectively.
- Security defenses often rely on reactive measures, such as known indicators of compromise and historical attack patterns, creating opportunities for attackers to succeed.
- Security teams are fixing the wrong issues due to the industry's reliance on compliance checklists and fragmented security tools.
- The use of risk scores like CVSS to prioritize vulnerabilities often results in patching non-exploitable issues, giving attackers room to exploit overlooked weaknesses.
- Traditional signature-based detection methods are becoming less effective against AI-generated attacks like polymorphic malware and AI-generated phishing emails.
- Regulatory pressures, such as the SEC's cybersecurity disclosure rules and the EU's DORA regulations, demand a shift towards continuous cyber risk management that most organizations are unprepared for.
- Most organizations struggle with threat prioritization, relying on static risk scoring systems that do not consider vulnerability context, leading to inefficiencies in managing cyber risk.
- A proactive approach focusing on continuous attack simulation and exploitability-driven defense is recommended to combat AI-generated attacks effectively.
- Security teams should prioritize continuous attack simulations, exploitability over severity, unified security telemetry, automated defense validation, and modern cyber risk reporting for improved security operations.
- By shifting to continuous validation and exploitability-based prioritization, organizations can enhance security operations, improve incident response, and align with regulatory demands.
Read Full Article
25 Likes
Wired
238

Image Credit: Wired
Ross Ulbricht Got a $31 Million Donation From a Dark Web Dealer, Crypto Tracers Suspect
- Ross Ulbricht received a $31 million bitcoin donation suspected to originate from a long-defunct dark web market, AlphaBay, by cryptocurrency tracing firm Chainalysis.
- The funds tied to Ulbricht were believed to have emerged from AlphaBay around 2016-2017, possibly coming from a large-scale seller on the market.
- Independent crypto investigator ZachXBT found that the donation did not come from the Silk Road and traced it to an address linked to illicit activity.
- The donor used Bitcoin 'mixers' and deposited cryptocurrency in small amounts, indicating potential criminal origins of the funds.
- Chainalysis, known for identifying illegal digital markets, played a role in dismantling AlphaBay in an investigation called Operation Bayonet.
- AlphaBay, a major black market, facilitated millions in daily sales before being shut down in 2017, creating crypto moguls with significant wealth.
- Speculation surrounds why an AlphaBay figure would donate $31 million to Ulbricht, with possibilities ranging from repayment to admiration for Ulbricht's pioneering role in anonymous transactions.
- Taylor Monahan, a security researcher at MetaMask, suggests the donation could stem from gratitude inspired by Ulbricht's journey and survivor's guilt.
- The mystery behind the substantial donation further raises questions about the interconnected world of dark web markets, cryptocurrency, and criminal activity.
- The complex nature of tracing crypto transactions underscores the ongoing challenges in identifying and combatting illicit financial activities in the digital realm.
Read Full Article
14 Likes
Medium
256
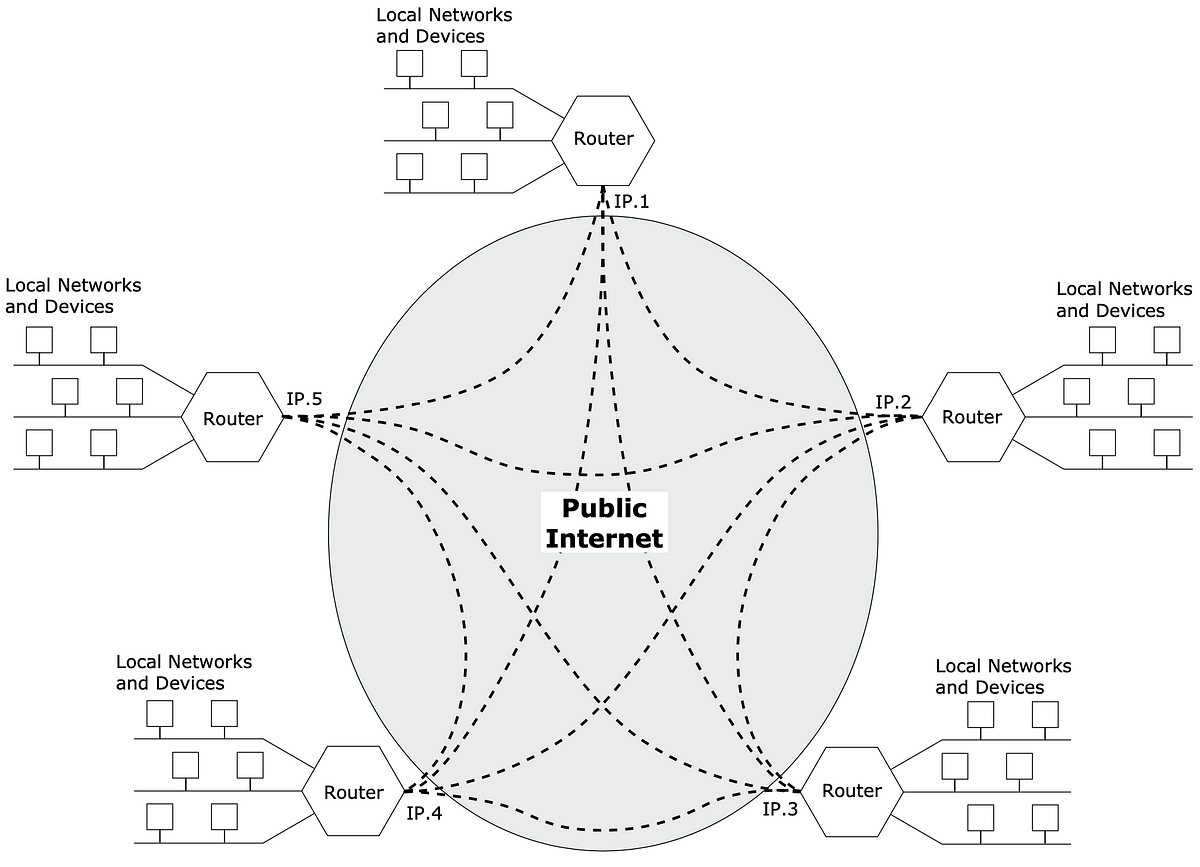
Image Credit: Medium
What is a VP²N, and What makes it a better VPN?
- VP²N, a dual-purpose approach to building networks, aims to offer both exclusivity and confidentiality for greater security.
- VPNs first emerged in the 1980s as telco-provided point-to-point circuits without encryption.
- The shift towards private networks via leased telco circuits resulted in cost savings and improved communications for enterprises.
- VPN networks should prioritize elements like authentication, perfect forward secrecy, recovery planning, firewall rules, and audit controls.
- Layered encryption, traffic hiding, Internet access strategy, and network management are crucial for VPN security.
- To enhance security, VP²N eliminates default routes in routers, adding robust exclusivity and a multi-factor authentication approach.
- Full-mesh VP²Ns offer consistency in inter-site communications, making management and maintenance easier while supporting dual-stack configurations.
- Resilience in VP²Ns can be enhanced by utilizing redundant routers, parallel inter-site connections, and alternative pathways like wireless or satellite networks.
- VP²N is beneficial for various sectors like public safety, industrial control, financial networks, and scalable from small to large networks with many devices.
- Implementing confidentiality and exclusivity in a coordinated manner is essential for successful VP²N deployment.
Read Full Article
15 Likes
TechBullion
283

Image Credit: TechBullion
Critical Air-Traffic Control Infrastructure at Risk: The Urgent Challenge of America’s Vulnerable Transportation Networks
- Recent communication failures at Newark Liberty International Airport exposed critical vulnerabilities in America's aviation infrastructure, highlighting systemic weaknesses in communication network design and maintenance.
- A 90-second blackout at the airport revealed a dangerous convergence of aging infrastructure and cybersecurity vulnerabilities, emphasizing the need for modernization in critical sectors like transportation and air traffic control.
- Actelis Networks, based in California, offers innovative solutions to upgrade networking capabilities practically overnight, addressing cybersecurity threats while integrating existing infrastructure types to enhance reliability and security.
- With Actelis' hybrid-fiber networking technology, transportation authorities can achieve high-speed, secure connectivity across legacy copper, coax, and fiber networks without extensive downtime or massive overhauls, providing a future-proof solution for evolving technological and security landscapes.
Read Full Article
17 Likes
Siliconangle
8

Image Credit: Siliconangle
Surfing the AI wave with zero trust everywhere: Five takeaways from CEO Jay Chaudhry’s keynote at Zscaler’s Zenith Live
- Zscaler CEO Jay Chaudhry emphasized the importance of zero trust security and its role in enabling artificial intelligence at Zenith Live event.
- Zero trust everywhere approach limits device communication to prevent broad data breaches if a trusted endpoint is compromised.
- Zscaler has expanded zero trust to cover workloads, IoT devices, and AI agents, working with companies like Microsoft to secure AI entities.
- AI-driven security operations and exposure management help streamline risk mitigation, reducing detection and investigation times significantly.
- Chaudhry highlighted the need for organizations to embrace AI, as threat actors are using AI and the only way to combat AI-driven threats is with AI.
- The shift to a café-like connectivity model with zero trust services can provide secure remote access for users working from anywhere.
- Comprehensive data protection and LLM proxies play a key role in ensuring AI security, by preventing risks from public-facing AI applications.
- Network engineers are urged to adapt to the changing landscape due to AI, moving towards deeper security skills alongside traditional connectivity roles.
- Zscaler aims to lead in secure AI adoption, emphasizing the urgency for organizations to adapt to the disruptions brought by AI.
- The need for change in security operations and networking is highlighted, with a focus on embracing AI to stay relevant in the evolving landscape.
Read Full Article
Like
Arstechnica
422

Image Credit: Arstechnica
Nintendo warns Switch 2 GameChat users: “Your chat is recorded”
- Nintendo updated its privacy policy to mention that video and audio interactions on the Switch 2 GameChat may be recorded.
- Before using GameChat on Switch 2, users must consent to terms stating that chat content is temporarily recorded and stored on systems.
- Recordings are only shared with Nintendo in case of reported violations of Community Guidelines, with a review option for specific sections.
- Recordings are reportedly only available for viewing within 24 hours of the report, indicating that they are deleted from local storage after a day.
Read Full Article
25 Likes
For uninterrupted reading, download the app