Cyber Security News
The Register
407

Image Credit: The Register
Apple tries to contain itself with lightweight Linux VMs for macOS
- Apple introduced an open source containerization framework for creating and running Linux container images on Mac.
- The framework allows developers to run Linux containers on Mac, enabling them to access the environment they code for while using a Mac.
- Apple's containerization framework creates lightweight virtual machines for each container, enhancing security by reducing the attack surface and maintaining speed.
- The framework is optimized for Apple Silicon chips but has some limitations under current macOS versions, with full capabilities expected in future releases.
Read Full Article
14 Likes
Medium
49
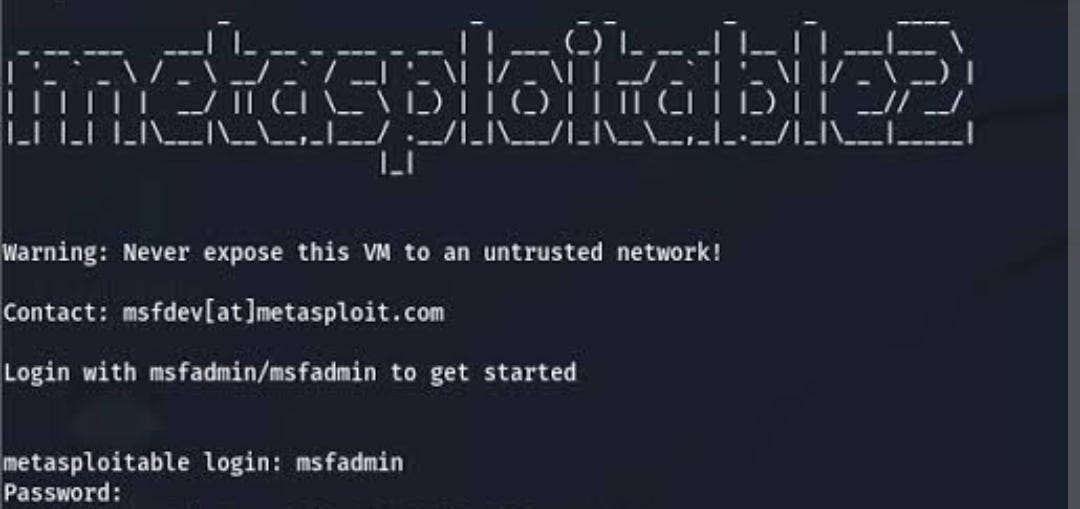
Image Credit: Medium
How To Convert an Old PC/Laptop Into Home Lab.
- Transforming an old computer into a home lab can provide hands-on experience with ethical hacking, crucial for those pursuing a career in Offensive Security.
- Download VirtualBox from the official website, select the appropriate operating system, and install the latest version.
- After installation, set up VirtualBox by launching the program, keeping default settings, selecting location, and finishing the setup.
- Allocate around 10 GB of storage for the VirtualBox setup, and follow the steps to successfully set up Metasploitable2 with credentials: Username - msfadmin, Password - msfadmin.
Read Full Article
2 Likes
Dev
415

Image Credit: Dev
Timing Attacks: Why Your Code Might Be Leaking Secrets
- Side-channel attacks analyze unintended information leakage from the physical implementation of a system during normal operation.
- Timing attacks are a common side-channel attack that targets how code runs to extract sensitive data by measuring response times.
- Researchers demonstrated extracting RSA private keys over a network through timing analysis in 2003, highlighting the real danger of timing attacks for systems.
- Authentication systems with timing leaks can reveal sensitive information through response time differences for valid and invalid inputs.
- Rate limiting systems can become timing attack vectors, allowing attackers to detect rate limits and adjust attack patterns.
- Defending against timing attacks requires constant-time programming, architectural defenses, and monitoring systems to ensure execution time independence from secret data.
- Constant-time comparison functions and architectural defenses like decoupling requests/responses are essential in timing attack defense.
- Monitoring systems help detect timing attack attempts through analysis of request patterns and response times.
- Protecting code against timing attacks involves switching to timing-safe functions, implementing dummy processing for authentication failures, and using libraries with built-in protection.
- Combining defensive layers like constant-time implementations, architectural protections, and monitoring is crucial to resist timing attacks across various applications.
Read Full Article
24 Likes
Damienbod
335

Image Credit: Damienbod
Experimental alternative flow for OAuth First-Party Applications
- A post discusses an experimental alternative flow for implementing native app authentication and authorization using OAuth 2.0 for First-Party Applications draft.
- The approach focuses on authenticated device and user onboarding without gaps in secure channels, with the device responsible for user authentication.
- Advantages include unique authentication of the application/device, enhanced security with 'auth_session' binding, and flexibility in user onboarding.
- Disadvantages entail the need for client assertion adaptation, potential unsecured initial session setup endpoint, and vulnerability to DDoS attacks.
Read Full Article
20 Likes
Siliconangle
268

Image Credit: Siliconangle
Zero trust everywhere: Zscaler’s vision for securing today’s digital world
- Zscaler's 'zero trust everywhere' approach aims to reimagine how companies secure users, workloads, and third-party relationships in today's digital world.
- The company's vision involves treating each branch as a standalone 'café,' where users and IoT devices access permitted destinations only, blocking lateral movement of malware.
- Zscaler's Cloud Zero Trust Gateway helps enterprises segment workloads and enforce precise communication rules between services, reducing security risks as organizations transition to hybrid work environments.
- The 'zero trust everywhere' principle extends to applying one-to-one connections between applications and data sync, ensuring a secure digital infrastructure.
Read Full Article
16 Likes
Medium
196

We’ve all heard the same privacy advice over and over again:
- Privacy education and training programs are usually designed as 'one-size-fits-all' solutions, which may not effectively cater to individuals' unique privacy needs.
- Research suggests that personalized privacy education based on individual traits such as cognitive style and decision fatigue is more effective than generic advice.
- Just-in-time reminders and empowerment strategies are found to be more successful in promoting long-term privacy behavior change compared to fear-based tactics.
- Default privacy settings play a significant role in users' privacy behaviors, emphasizing the importance of designing systems with privacy as the default option.
Read Full Article
11 Likes
Wired
272

Image Credit: Wired
The Dangerous Truth About the ‘Nonlethal’ Weapons Used Against LA Protesters
- The recent protests in Los Angeles against ICE raids led to the arrests of at least 56 individuals, amid a growing intensity of raids by Immigration and Customs Enforcement.
- Use of the National Guard and nonlethal weapons by law enforcement raised concerns over the suppression of dissent and instilling fear, as stated by civil society groups and California governor Gavin Newsom.
- Law enforcement agencies used various 'nonlethal' weapons like PGL-65, 37mm/40mm Sage Deuce Projectile Launchers, tear gas grenades, and rubber ammunition to disperse protesters in Los Angeles.
- Canada bans the use of such 'nonlethal weapons' for protest control, labeling them as prohibited weapons with concerns raised by civil society organizations about their potential dangers.
- Kinetic projectiles like rubber bullets are discouraged under Geneva conventions due to potential severe injuries, such as skull fractures, brain damage, and even death, when fired at protesters.
- The Geneva conventions specify rules for the application of kinetic projectiles, emphasizing not firing in automatic mode, avoiding multiple simultaneous firings, and not targeting the face, neck, or torso.
- Usage of 'less lethal' weapons is widespread, with many countries keeping the specific models confidential, hindering accountability and verification of their illegal use against peaceful civilians.
- Amnesty International has documented abusive use of 'nonlethal' weapons like Penn Arms GL-1 and Defense Technology 1325 in social protests, leading to serious injuries and human rights violations.
- In Chile, police actions during protests resulted in over 440 eye injuries, including cases of eye loss or rupture, highlighting the devastating impact of these 'less lethal' weapons.
- Amnesty International's 2023 report 'My Eye Exploded' calls for the suspension of using 40-mm gas or impact projectiles against peaceful civilians to prevent further harm and human rights violations.
Read Full Article
16 Likes
Lastwatchdog
254

News alert: Seraphic launches BrowserTotal™ — a free AI-powered tool to stress test browser security
- Seraphic Security launches BrowserTotal, a free AI-powered tool to assess browser security posture in real-time.
- BrowserTotal offers CISOs and security teams features such as posture analysis, real-time weakness detection, insights on threats, in-browser LLM for tailored recommendations, and a secure URL sandbox.
- This initiative aims to democratize access to enterprise-grade security analysis and strengthen the collective defense against web-based threats.
- Seraphic Security, known for its innovative solutions, aims to elevate awareness and readiness against sophisticated browser-based attacks through BrowserTotal.
Read Full Article
15 Likes
Semiengineering
420

Image Credit: Semiengineering
Metrics And Methodology for Hardware Security Constructs (NIST)
- NIST published a technical paper titled "Metrics and Methodology for Hardware Security Constructs" outlining a methodology for assessing hardware vulnerabilities and threats.
- The paper addresses design and implementation flaws in hardware that can compromise security and user information, presenting metrics to quantify weaknesses and potential attacks.
- The methodology introduces a threat metric to quantify the number of hardware weaknesses exploitable by an attack and a sensitivity metric to measure distinct attacks targeting specific weaknesses.
- This analysis aims to assist in enhancing hardware security and optimizing the balance between security measures and associated costs.
Read Full Article
25 Likes
Tech Radar
194
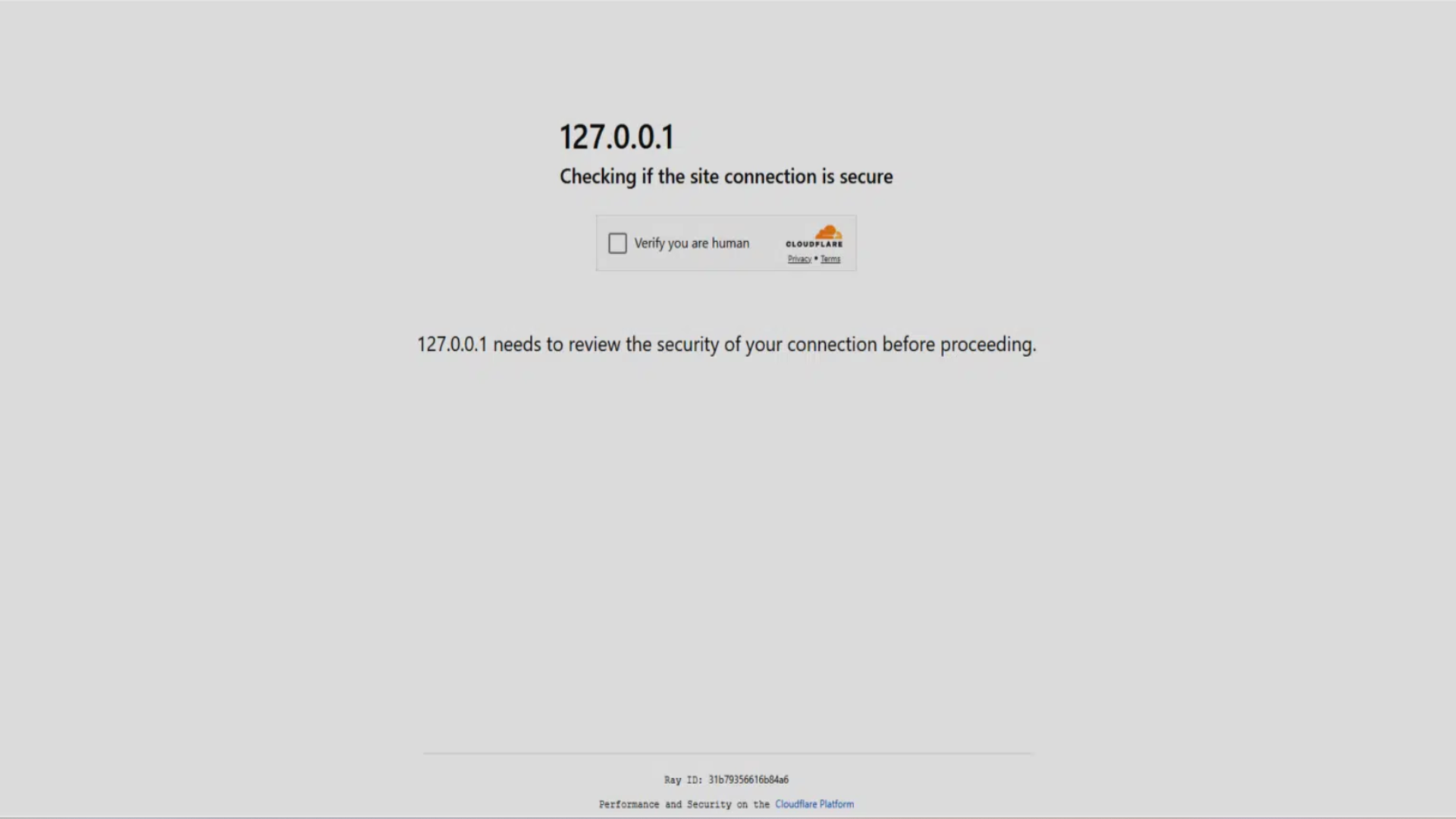
Image Credit: Tech Radar
Fake Cloudflare CAPTCHA page laden with malware uncovered in the wild - here's how to stay secure and safe
- A phishing technique known as ClickFix is circulating, using fake Cloudflare CAPTCHA pages to infect users with malware.
- The deceptive technique presents a counterfeit Cloudflare's Turnstile CAPTCHA page, mimicking the visual layout and technical elements convincingly.
- Users are tricked into executing commands that install malware by clicking 'Verify you are human' and following seemingly harmless instructions.
- ClickFix exploits user trust and habit, evading traditional detection tools by using legitimate Windows utilities for clipboard injections.
Read Full Article
11 Likes
Pymnts
411

Image Credit: Pymnts
Financial Trade Associations Ask Treasury to Limit Data Collection After Cybersecurity Incidents
- Four financial industry trade associations have urged federal agencies to limit data collection to only what is necessary after recent cybersecurity incidents.
- The American Bankers Association, Bank Policy Institute, Managed Funds Association, and Securities Industry and Financial Markets Association recommended stricter security and data protection standards for agencies.
- The groups emphasized the need for agencies to notify affected companies promptly in case of security breaches and avoid centralizing sensitive data.
- The OCC faced a major security incident in April involving unauthorized access to sensitive information, while the Treasury Department's workstations were breached by China-backed hackers in December.
Read Full Article
24 Likes
Hackernoon
192
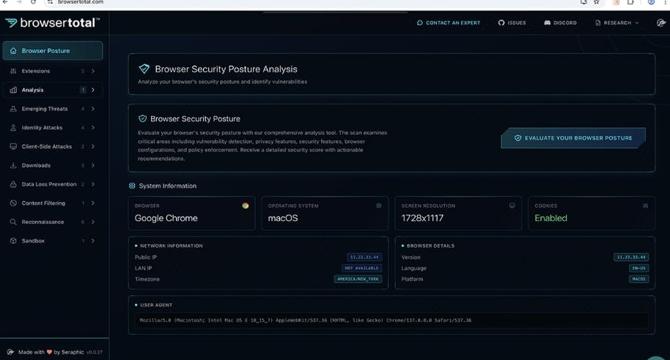
Image Credit: Hackernoon
Seraphic Security Unveils BrowserTotal™ - Free AI-Powered Browser Security Assessment For Enterprise
- Seraphic Security unveiled BrowserTotal™, an AI-powered browser security assessment tool for enterprises, conducting over 120 tests to analyze posture standing, emerging threats, URL analysis, and more.
- BrowserTotal offers CISOs and security teams a comprehensive environment to test browser security defenses against sophisticated threats, with features like posture analysis, real-time weakness detection, insights on emerging threats, and a secure URL sandbox.
- The launch of BrowserTotal coincided with the Gartner Security & Risk Management Summit 2025 where live demos were showcased, allowing security leaders to visualize their organization's browser security risks and access tailored recommendations for remediation.
- Seraphic Security received a $29 million Series A fundraising and aims to democratize access to enterprise-grade security analysis with BrowserTotal, addressing the critical gap in understanding and preparing for browser-based attacks.
Read Full Article
11 Likes
Securityaffairs
192

Image Credit: Securityaffairs
DOJ moves to seize $7.74M in crypto linked to North Korean IT worker scam
- The US Department of Justice (DoJ) has filed a civil forfeiture complaint to seize $7.74 million in crypto connected to North Korean fake IT worker schemes.
- The frozen assets include cryptocurrency, NFTs, and other digital assets tied to the indictment of North Korean Foreign Trade Bank representative Sim Hyon Sop.
- North Korean IT workers obtained illegal employment to amass millions in cryptocurrency, evading US sanctions.
- These workers used fake IDs and deceptive tactics to hide their identities while gaining remote jobs in blockchain firms, paid in stablecoins unknowingly supporting North Korea's revenue stream.
- Illicit gains were laundered through various means and funneled back to the regime, including using US accounts to mask their origins.
- The US authorities unsealed charges against individuals aiding overseas IT workers to defraud US companies, with North Korea dispatching IT workers globally using stolen US identities.
- The operations financed North Korea's illicit nuclear program, highlighting the country's exploitation of global remote IT contracting and cryptocurrency ecosystems to circumvent sanctions.
- Several arrests were made, including Christina Marie Chapman and Oleksandr Didenko, facing charges related to fraud, money laundering, and unlawful employment.
- Additionally, Matthew Isaac Knoot was arrested for aiding North Korean IT workers, hosting company laptops and laundering payments, contributing to North Korea's illicit weapons program.
- Knoot and his associates caused targeted companies over $500,000 in costs. If convicted, Knoot could face a maximum of 20 years in prison.
Read Full Article
11 Likes
TechDigest
184

Image Credit: TechDigest
M&S food sales growth stalls following cyber attack disruption
- Marks & Spencer's food sales growth has been impacted by a cyber attack in April, with a significant slowdown in sales.
- Spending in M&S food halls rose by only 0.8% in the four weeks to May 17 compared to a year earlier, down from 11% growth over the previous 12 months.
- The cyber incident by the group 'Scattered Spider' led to disrupted online orders, food deliveries, and caused a slip in M&S market share to 3.3% from 3.6%.
- M&S has estimated a £300 million profit loss due to the attack, with ongoing IT system restorations expected to continue until July. However, analysts anticipate a bounce back once issues are resolved.
Read Full Article
10 Likes
TechCrunch
321

Image Credit: TechCrunch
Paragon says it canceled contracts with Italy over government’s refusal to investigate spyware attack on journalist
- Spyware maker Paragon canceled contracts with Italy over the government's refusal to investigate a journalist's spyware attack.
- Paragon claims it offered a solution for Italy to determine if its system was used against the journalist but terminated contracts when Italian authorities did not proceed with it.
- The Italian government rebuffed Paragon's remarks, stating the decision to suspend and terminate the contract was mutual, citing concerns over national security and confidentiality.
- The spyware scandal involves Paragon, WhatsApp, and Italian intelligence agencies, with ongoing investigations and disputes regarding targeted individuals and their activities.
Read Full Article
19 Likes
For uninterrupted reading, download the app